IPv6
Internet Protocol version 6 (IPv6) has become an important factor to consider as the pool of IPv4 addresses becomes exhausted. You must also plan to meet the organizational mandates for compliance with IPv6. This chapter describes how to configure SteelHeads running RiOS 8.5 for optimization of TCP over IPv6 using autodiscovery and fixed-target rules. The benefit of autodiscovery and fixed-target rules is that you can provide both application streamlining for select protocols and transport streamlining, in addition to data streamlining. Packet mode optimization is still an alternative for data streamlining of IPv6 traffic. This chapter includes the following sections:
Overview of IPv6
This section provides an overview of various aspects of IPv6. This section includes the following topics:
IPv6 is the next revision of the Internet Protocol. IPv6 has become a critical enabler as more devices are being connected to the internet. The main purpose of IPv6 is to help service providers and companies manage the exhaustion of IPv4 addresses without relying on other techniques such as network address translation (NAT), which hide and manipulate the source IP address when connecting across organizational boundaries. IPv6 was designed to overcome the limitation in IPv4 by using a 128-bit address instead of a 32-bit address, thereby supporting up to 3.4 x 10^38 addresses; IPv4 supports up to 4.3 billion only.
The use of private IPv4 address space has created challenges for applications, security, and performance because the source and destination addresses can change through the connection. RiOS extended support for IPv6 traffic with packet mode optimization, and RiOS 8.5 or later further enhanced its IPv6 capabilities by supporting autodiscovery and fixed target rules. By using autodiscovery or fixed target rules, RiOS can apply transport and application streamlining techniques (similarly as it does for TCP connections over IPv4) to improve the user experience as the transition to IPv6 continues.
RiOS RFC Compliance and Feature Compatibility
The following RiOS 8.5 features are compatible with IPv6.
RiOS IPv6 Support Includes | RiOS Version | Notes |
Conformance with Request for Comments (RFCs) 1981, 2460, 2464, 2710, 3590, 4007, 4291, 4443, 4861, 4862, 4943, 5095, and 5156. | 8.5 and later | |
TCP IPv6 traffic interception between source and destination, bandwidth optimization. | 8.5 and later | |
Autodiscovery of SteelHeads. | 8.5 and later | TCP inner connections between the peer SteelHeadsSteelHead Management Console User’s Guide is strictly IPv4. |
Ability to automatically discover fixed-target and pass-through in-path rules, along with ability to deny and reject IPv6 TCP traffic as configured in the in-path rules. | 8.5 and later | RiOS doesn’t support the neural framing modes Always, TCP Hints, and Dynamic. RiOS doesn’t support the Oracle forms and Oracle forms over SSL preoptimization policies. |
HTTP and HTTPS latency optimization for IPv6 TCP traffic. | 8.5 and later | |
Ability to configure serial clusters. | 8.5 and later | |
Interception of IPv6 traffic for in-path, virtual in-path, and server-side out-of-path configurations. | 8.5 and later | WCCPv6 support is not available. Virtual in-path support is PBR only. Interceptor is not supported. |
Intercepting and passing through IPv4 and/or IPv6 traffic, depending on the in-path rules. | 8.5 and later | |
Ability to detect asymmetric routes for IPv6 TCP traffic; enables connection forwarding of IPv6 TCP traffic in asymmetric conditions. | 8.5 and later | The connection-forwarding control channel between the neighbors is strictly IPv4. You must configure IPv4 addresses on the SteelHeads when using a connection-forwarding control channel. |
Ability to configure IPv4 and IPv6 addresses on every in-path interface and intercepting and optimizing IPv4 and IPv6 traffic. | 8.5 and later | |
Ability to configure one IPv6 address configuration for every in-path interface. RiOS intercepts and optimizes traffic matching the scope of the IPv6 address configured on the in-path interface. Not applicable for a link-local address configured on the in-path interface. | 8.5 and later | RiOS passes through IPv6 TCP traffic not matching the scope of the IPv6 address configured on the in-path interface. |
Ability to configure IPv6 addresses on any in-path interface. IPv6 TCP inner connections only in fixed-target cases. | 8.5 and later | This IPv6-only mode requires configuring only fixed-target in-path rules. |
Enhanced autodiscovery of SteelHead appliances for IPv6 TCP traffic. | 8.5 and later | TCP inner connections between the peer SteelHead appliances is IPv4 only. |
Simplified routing for IPv6 TCP traffic. | 8.5 and later | |
Connection forwarding for IPv6 traffic in multi-interface mode. | 8.5 and later | The control connection between neighbors is still IPv4 only. When multiple interface support in the Networking > Network Integration: Connection Forwarding page is not enabled, IPv6 traffic is passed through. |
Ability to configure peering rules for IPv6 traffic. | 8.5 | The peer client-side SteelHead IP address is IPv4 only. |
Ability to configure IPv6 addresses in Single Ended Interception (SEI) rules under Optimization > Network Services: Transport Settings. | 8.5 and later | |
Global and automatic kickoff for pass-through TCP IPv6 traffic. | 8.5 and later | |
Ability to configure asymmetric VLANs for IPv6 TCP traffic. | 8.5 and later | |
Latency optimization of signed-SMB, CIFS/SMB1, SMB2, and SMB3 using IPv6 endpoint addressing. | 8.5.2 and later | The authentication stack continues to require IPv4 endpoint addressing. |
Encrypted Outlook Anywhere latency optimization. | 8.6 and later | |
MAPI, eMAPI latency optimization. | 8.6 and later | Authentication is over IPv4. |
Authentication over IPv6. | 8.6 and later | |
Features Not Supported with IPv6
The following features are not IPv6 compatible:
• Management In-Path (MIP) Interface
• Transparency
• NetFlow
• Path selection
• QoS
• Host labels
• IPSec
• Automatic address assignment through DHCPv6
• Multicast listener discovery
• IPv6 stateless address autoconfiguration
• WCCP using anything other than IPv4 outer connections
IPv6 Addressing
IPv6 addresses share many characteristics with their IPv4 counterparts. Each version separates the address into a network identifier and host identifier. Depending on the type of address, IPv6 specifies certain bit ranges for specific purposes.
In many ways, this is similar to how IPv4 uses address classes. It is important to note that IPv6 addresses use hexadecimal digits instead of a dotted-decimal format. Also, an interface on a device has multiple IPv6 addresses (instead of a single IPv4 address) that it uses to communicate. For example, each interface always has a link-local address and can have one or multiple global unicast addresses.
There are several types of IPv6 addresses. Riverbed recommends that you verify with the IPv6 address registry, because new IPv6 transition mechanisms or address blocks are reserved. The types of addresses are as follows:
• Global unicast--2000::/3
– 2002::/16 reserved for 6to4
– 2001:0000::/32 reserved for TEREDO
• ::ffff:0:0/96 reserved for IPv4-mapped address
• Unique local--fc00::/7
• Link local--fe80::/10
• Multicast--ff00::/8
• Loopback--::1/128 reserved for loopback address
• Unspecified--::/128 reserved for unspecified address
Note: The types of IPv6 addresses are subject to change.
RiOS supports a single-system, generated link-local address and a user-assigned IPv6 address for each interface (primary, auxiliary, and in-path). The link-local address is automatically assigned as the network identifier using FE80 in the first 64 bits and a modified EUI-64 identifier for the host bits following RFC 4291. This address is automatically assigned by the system and cannot be changed.
The link-local address is used as part of IPv6 neighbor discovery, which is analogous to address resolution protocol for IPv4. You must manually configure the user-assigned IPv6 address—it cannot be derived from stateless automatic configuration or dynamic host communication protocol for IPv6. There are two address types, depending on whether you need to natively communicate outside of an organizational boundary—in much the same way a public or private IPv4 address is selected. For SteelHeads, choose one of the following IPv6 addresses:
• An aggregatable global unicast address for the SteelHead to communicate with devices not directly connected to the interface.
• A unique local unicast address, which is the updated address range to replace site local addresses.
The intent of a unique local unicast address is for a private IPv6 address range.
The IPv6 gateway is also user assigned, and you can link it to the local address of the router or the address on the same subnet as the manually assigned address. RiOS does not support receiving router advertisements as a means to discover the IPv6 gateway. Configure the link-local address for a virtual router in circumstances in which you use a first hop redundancy protocol: for example, HSRPv6.
Traffic Interception
RiOS 8.5 introduces the ability to intercept TCP-over-IPv6 traffic and perform optimization by performing transport streamlining on the connection instead of performing data reduction on a packet-by-packet basis. The SteelHeads perform their roles in the connection by establishing three separate connections:
• Outer channel from the client to the client-side SteelHead
• Outer channel from the server to the server-side SteelHead
• Inner channel between SteelHeads
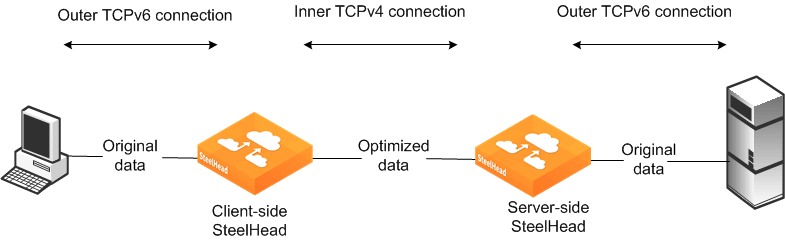
The key difference between packet mode optimization and IPv6-based optimization is that IPv6 supports autodiscovery and fixed-target rules. Packet mode performs data reduction on each packet, and TCP-over-IPv6 supports application, data, and transport streamlining by inserting the SteelHeads into the connection.
Support for WAN visibility modes with autodiscovery of TCP-over-IPv6 traffic is limited to correct addressing. Identical to IPv4 autodiscovery, IPv6 autodiscovery uses the same TCP options present in the TCP header of the connection setup packets to discover a remote SteelHead on the path between the end systems. The SteelHeads set up an inner channel using IPv4 addresses that requires the intervening network to be IPv6- and IPv4-capable or dual-stack.
For more information about packet mode optimization, see
Packet Mode Optimization. For more information about WAN visibility modes and correct addressing, see
WAN Visibility Modes.
Figure: Autodiscovery with IPv6
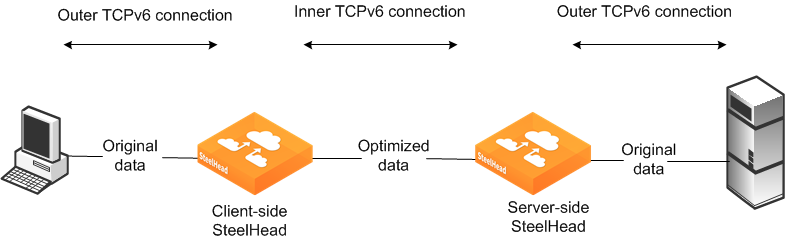
The alternative to using autodiscovery is to use a fixed-target rule. A fixed-target rule enables you to optimize traffic end-to-end using IPv6 addresses. The inner channel between SteelHeads forms a TCP connection using the manually assigned IPv6 address. This method is similar to an IPv4 fixed-target rule, and you configure it the same way. Although you can use IPv6 addresses end-to-end in the connection, the SteelHead in-path interface continues to require an IPv4 address for the optimization service to start.
Figure: Fixed-Target Rule with IPv6
In-Path Rules
The default rule was previously all-IPv4 but is now all-IP. All-IP includes all IPv4 and all IPv6 traffic. The default rule for TCP traffic, either IPv4 or IPv6, attempts autodiscovery with correct addressing as the WAN visibility mode. A fixed-target rule with an IPv6 target appliance address requires the source and destination address type to be an IPv6 address. You must change the use of all-IP to all-IPv6. If you do not change to all-IPv6, use specific source addresses or destination addresses or both.
Deployment Options
You can configure SteelHeads for in-path or virtual in-path deployment for TCP-over-IPv6 traffic. Riverbed also supports server-side out-of-path deployments. This section includes the following topics:
Considerations for the deployment type are the same as the considerations for optimizing of IPv4 connections. Network integration features such as fail-to-wire, link state propagation, parallel deployments, firewalls, and so on continue to be relevant for optimization of TCP-over-IPv6 traffic. IPv4 connections can coexist with TCP-over-IPv6 traffic.
The following list can help you simplify the choice of deployment options:
• Use a fixed-target-rule or packet mode optimization for all IPv6 networks. Use autodiscovery if you have a mix of IPv4 and IPv6. You must always configure an IPv4 address on the SteelHead in-path interface if you are using the interface for optimization. If you do not configure the interface with IPv4 addresses, the service does not start.
• If you have a dual-stack network, use autodiscovery.
• A parallel SteelHead deployment requires IPv4 between the local SteelHead in-path interfaces, for connection forwarding.
• Virtual in-path deployments support policy-based routing. WCCP and SteelHead Interceptor deployments are not supported with TCP over IPv6.
Configuring an In-Path SteelHead IPv6 Deployment
The in-path deployment for optimization of TCP over IPv6 traffic is similar to an in-path deployment for IPv4 connections. You deploy the SteelHead physically in-path using an IPv6 address on the SteelHead in-path interface. Optionally, for IPv6 management, you can configure an IPv6 address on the primary interface.
In addition to using the primary interface, you can also use the auxiliary (AUX) interface for management. The AUX interface must be on a different subnet than the primary interface. The in-path management interface cannot be assigned an IPv6 address to manage the SteelHead.
The in-path interface has its own IPv6 routing table. You can add destinations to the table and select an appropriate next hop. You can also add simplified routing to reduce the burden of administering IPv6 routes.
For information about simplified routing, see
Overview of Simplified Routing.
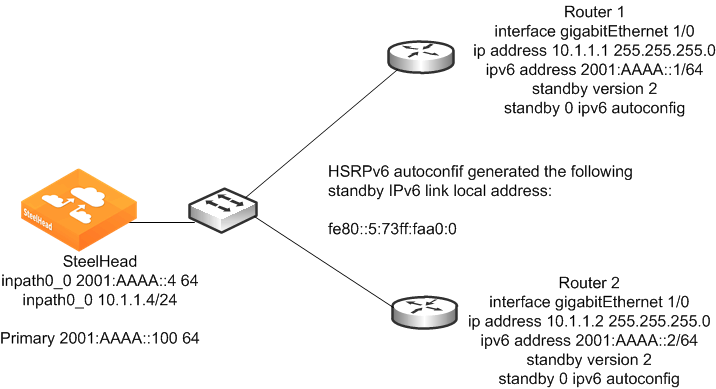
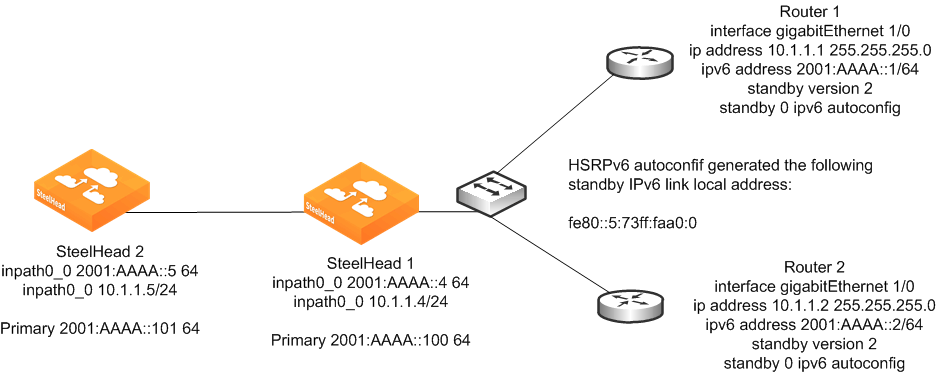
Figure: In-Path SteelHead Configuration Using IPv6 shows an example deployment with IPv6 address from the globally assigned address range manually assigned to the primary and inpath0_0 interface. The primary interface is assigned 2001:aaaa:100 with a prefix length of 64 bits. The inpath0_0 interface is assigned 2001:aaaa::10 with a prefix length of 64 bits. The primary interface has the global unicast address of Router 1 configured as its IPv6 gateway, but you could use a link-local address.
In this example, the link-local address of the HSRPv6 virtual gateway is used as the default route for the in-path interface and the global unicast address is used for the primary interface. Normally, the same default route is used. The in-path interface is configured to use the HSRPv6 virtual gateway link local address for its IPv6 gateway. This link-local address is always on the same network as the SteelHead in-path interface automatically assigned link-local address according to the IPv6 standards.
Figure: In-Path SteelHead Configuration Using IPv6
To configure an in-path SteelHead using IPv6
• Connect to the SteelHead CLI and enter the following commands:
enable
configure terminal
interface primary ipv6 address 2001:aaaa::100 64
ipv6 default-gateway "2001:aaaa::1"
interface inpath0_0 ipv6 address 2001:aaaa::4 64
ipv6 in-path-gateway inpath0_0 fe80::5:73ff:fea0:0
in-path enable
Using autodiscovery requires an IPv4 address
interface inpath0_0 ip address 10.1.1.4 /24
ip in-path-gateway inpath0_0 10.1.1.1
Configuring a SteelHead Serial Cluster IPv6 Deployment
Figure: Serial Cluster SteelHead Configuration Using IPv6 shows an example deployment with an IPv6 addresses in a SteelHead serial cluster deployment. You can deploy SteelHeads in a serial cluster and optimize TCP-over-IPv6 traffic. Set the peering rule to match the peer IPv4 address, because SteelHeads insert the IPv4 address in the autodiscovery probe to identify themselves in the autodiscovery process. Setting the peering rule for serial cluster deployments correctly is important because Riverbed does not recommend that you optimize connections between locally connected SteelHeads.
For information about serial cluster deployments, see
In-Path Redundancy and Clustering Examples.
Figure: Serial Cluster SteelHead Configuration Using IPv6
To configure a SteelHead serial cluster using IPv6
1. On SteelHead A, connect to the CLI and enter the following commands:
enable
configure terminal
interface inpath0_0 ip address 10.1.1.4 /24
ip in-path-gateway inpath0_0 10.1.1.1
interface inpath0_0 ipv6 address 2001:aaaa::4 64
ipv6 in-path-gateway inpath0_0 fe80::5:73ff:fea0:0
in-path enable
in-path peering auto
in-path simplified routing dest-only
in-path peering rule pass peer 10.1.1.5 rulenum end
write memory
restart
2. On SteelHead B, connect to the CLI and enter the following commands:
enable
configure terminal
interface inpath0_0 ip address 10.1.1.5 /24
ip in-path-gateway inpath0_0 10.1.1.1
interface inpath0_0 ipv6 address 2001:aaaa::5 64
ipv6 in-path-gateway inpath0_0 fe80::5:73ff:fea0:0
in-path enable
in-path simplified routing dest-only
in-path peering auto
in-path peering rule pass peer 10.1.1.4 rulenum end
write memory
restart
Configuring a Connection Forwarding and SteelHead IPv6 Deployment
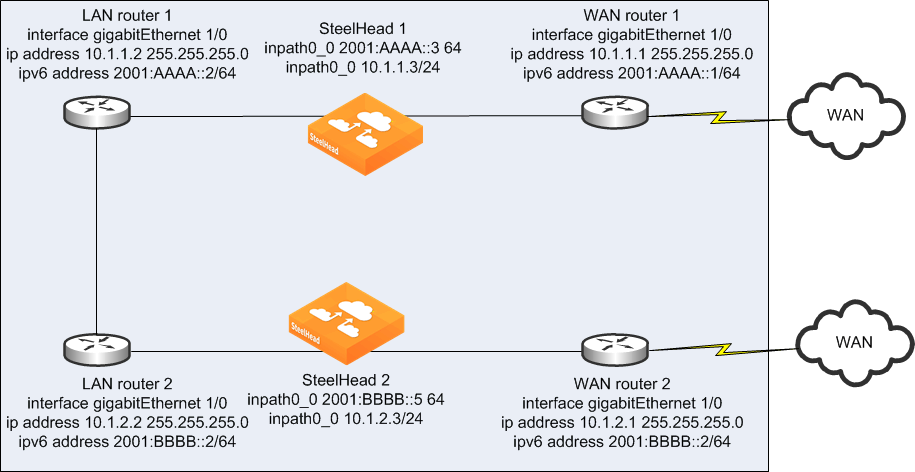
Figure: Connection Forwarding and SteelHead Using IPv6 shows an example deployment of connection forwarding for TCP-over-IPv6 traffic. You can deploy SteelHeads in a parallel topology using connection forwarding to optimize TCP-over-IPv6 traffic. You must use RiOS 8.5 or later and configure your SteelHead to communicate using multi-interface. In addition, each in-path interface requires an IPv4 and an IPv6 address.
Connection forwarding uses the IPv4 addresses (TCP port 7850 connection) and redirects the connection setup packets through GRE encapsulation between the IPv4 addresses. When the connection is established and optimized, asymmetric traffic is redirected through NAT, destined to the peer in-path interface IPv6 address. You can optimize TCP-over-IPv4 and TCP-over-IPv6 traffic concurrently and the NAT entries are resynchronized between peers, even if a peer has its optimization service restarted or is disconnected.
For information about connection forwarding, see
Connection Forwarding.
Figure: Connection Forwarding and SteelHead Using IPv6
To configure connection forwarding and SteelHeads using IPv6
1. On SteelHead A, connect to the CLI and enter the following commands:
in-path enable
interface inpath0_0 ip address 10.1.1.3 /24
interface inpath0_0 ipv6 address 2001:aaaa::3 64
ip in-path-gateway inpath0_0 10.1.1.1
ipv6 in-path-gateway inpath0_0 2001:aaaa::1
ip in-path route inpath0_0 10.1.2.0 255.255.255.0 10.1.1.2
ipv6 in-path route inpath0_0 2001:bbbb::/64 2001:aaaa::2
in-path peering auto
in-path simplified routing dest-only
steelhead communication enable
steelhead communication multi-interface enable
steelhead name SteelheadB main-ip 10.1.2.3
2. On SteelHead B, connect to the CLI and enter the following commands:
in-path enable
interface inpath0_0 ip address 10.1.2.3 /24
interface inpath0_0 ipv6 address 2001:bbbb::3 64
ip in-path-gateway inpath0_0 10.1.2.2
ipv6 in-path-gateway inpath0_0 2001:bbbb::1
ip in-path route inpath0_0 10.1.1.0 255.255.255.0 10.1.2.2
ipv6 in-path route inpath0_0 2001:aaaa::/64 2001:bbbb::2
#--- Enable enhanced auto discovery
in-path peering auto
in-path simplified routing dest-only
steelhead communication enable
steelhead communication multi-interface enable
steelhead name SteelheadA main-ip 10.1.1.3
Configuring a Virtual In-Path SteelHead IPv6 Deployment
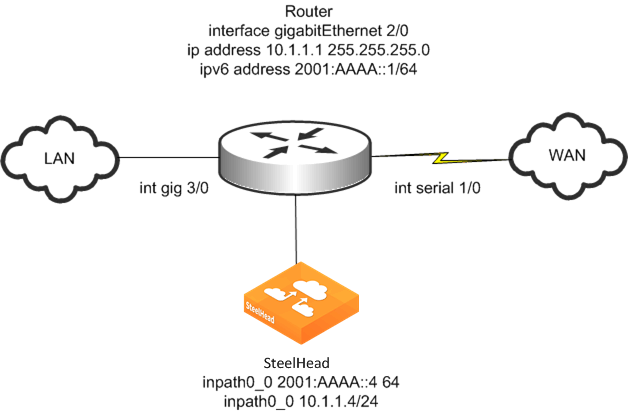
Figure: Virtual In-Path SteelHead Configuration Using IPv6 shows an example deployment of a virtual in-path SteelHead using IPv6. Virtual in-path support for TCP-over-IPv6 traffic is limited to policy-based routing (PBR) in RiOS 8.5 or later. You configure a SteelHead virtually in-path similarly to an IPv4 PBR deployment.
WCCPv6 is not supported. The Layer-3 device redirecting traffic must support PBR for IPv6 traffic. Cisco provides a list of software in which the PBR for IPv6 feature was introduced (12.2(30)S, 12.2(33)SXI4, 12.3(7)T, 12.4, and 12.4(2)T).
Figure: Virtual In-Path SteelHead Configuration Using IPv6
To configure a virtual in-path SteelHead using IPv6
1. Connect to the SteelHead CLI and enter the following commands:
interface inpath0_0 ipv6 address 2001:aaaa::4 64
ipv6 in-path-gateway inpath0_0 2001:aaaa::1
in-path enable
in-path simplified routing "none"
in-path oop enable
You must configure an IPv4 address for autodiscovery of TCP-over-IPv6 traffic if you are using connection forwarding.
2. Configure the Layer-3 device (use Cisco IOS syntax):
ipv6 access-list OPTIMIZEv6
permit tcp any host 2001:DDDD::100
permit tcp host 2001:DDDD::100 any
route-map OPTIMIZEv6 permit 10
match ipv6 address OPTIMIZEv6
set ipv6 next-hop 2001:aaaa::4
interface serial1/0
ipv6 policy route-map OPTIMIZEv6
interface gigabitEthernet3/0
ipv6 policy route-map OPTIMIZEv6
Configuring a Fixed-Target Rule SteelHead IPv6 Deployment
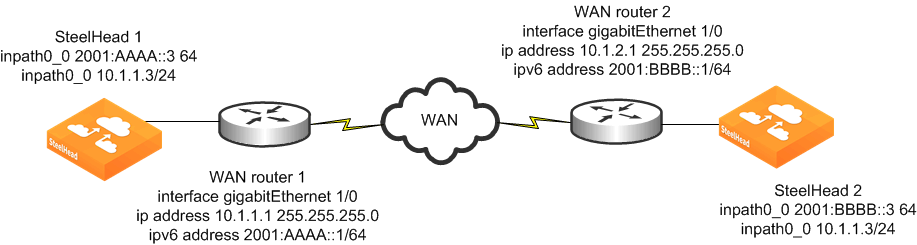
Figure: Fixed-Target Rule SteelHead Configuration Using IPv6 shows an example deployment of a SteelHead using a fixed-target rule in an IPv6 environment. You can use fixed-target rules for end-to-end optimization using an IPv6 address when you have SteelHeads in an all-IPv6 network or when peer SteelHeads communicate using their in-path interface IPv6 addresses.
The fixed-target rule operates similarly to IPv4 traffic, by replacing the IPv4 header and sending a directed connection setup packet to the target appliance IPv6 address. A fixed-target rule also works for server-side out-of-path (SSOOP) deployments. In a SSOOP deployment, the outer channel between the server-side SteelHead and server uses the primary interface IPv6 address in the same way it operates for SSOOP on IPv4 traffic.
For information about SSOOP, see
Out-of-Path Deployments.
Figure: Fixed-Target Rule SteelHead Configuration Using IPv6
To configure a SteelHead using a fixed-target rule and IPv6
• Connect to the SteelHead CLI and enter the following commands:
enable
configure terminal
interface inpath0_0 ip address 10.1.1.3 /24
ip in-path-gateway inpath0_0 10.1.1.1
interface inpath0_0 ipv6 address 2001:aaaa::3 64
ipv6 in-path-gateway inpath0_0 2001:aaaa::1
in-path enable
in-path simplified routing dest-only
in-path peering auto
in-path rule fixed-target target-addr 2001:bbbb::3 target-port 7810 backup-addr :: backup-port 7810 dstaddr all-ipv6 dstport "80" srcaddr all-ipv6 preoptimization "none" optimization "normal" latency-opt "normal" neural-mode "always" wan-visibility "correct" vlan -1 description "" auto-kickoff disable rule-enable true rulenum start
Protocol Support
Optimization for TCP-over-IPv6 traffic supports data reduction for any connection. In addition to data reduction, the following protocols have application streamlining support:
• FTP
• SSL
• HTTP
• MAPI
• Encrypted MAPI
• Outlook Anywhere (RPC over HTTP)
• MAPI over HTTP
• SMB
For more information about protocol support, see the SteelHead Deployment Guide - Protocols and the Riverbed Command-Line Interface Reference Manual.
Verification and Troubleshooting
There are three ways to verify and troubleshoot your IPv6 deployments:
• Utility ping
• Traceroute
• Connection report
Make sure that the SteelHead can reach the end system (client or server). You can use a utility ping at the SteelHead CLI and in the SteelHead Management Console. Using the ping6 utility, you must specify the interface IPv6 address instead of the interface name. The following example shows how to send an ICMPv6 echo request using the IPv6 address of 2001:aaaa::10 to reach 2001:aaaa::2:
VSH # ping6 -I 2001:aaaa::10 2001:aaaa::2
PING 2001:aaaa::2(2001:aaaa::2) from 2001:aaaa::10 : 56 data bytes
64 bytes from 2001:aaaa::2: icmp_seq=1 ttl=64 time=22.0 ms
64 bytes from 2001:aaaa::2: icmp_seq=2 ttl=64 time=31.1 ms
64 bytes from 2001:aaaa::2: icmp_seq=3 ttl=64 time=20.3 ms
Traceroute for IPv6 has also been included for verifying the path from the SteelHead to an IPv6 device or verifying the path between SteelHeads using a fixed-target rule:
VSH # traceroute6 -I 2001:aaaa::10 2001:bbbb::2
traceroute to 2001:aaaa::10 (2001:aaaa::10), 30 hops max, 2001 byte packets
1 2001:aaaa::10 (2001:aaaa::10) 0.328 ms 309.442 ms 309.450 ms
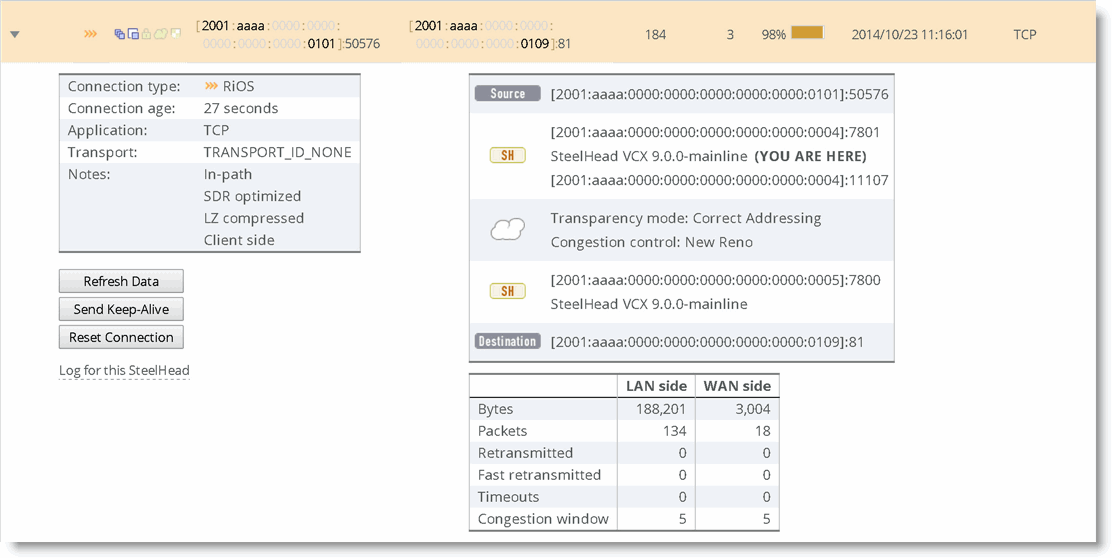
Figure: Connection Report shows a connection report in which the status of an IPv6 connection is optimized by the SteelHead.
Figure: Connection Report