Product Overview
This chapter provides an overview of the SteelCentral Controller for SteelHead (SCC). The SCC enables you to manage, configure, and monitor Riverbed products. The SCC also acts as an enterprise management and reporting tool for Riverbed products enabling greater control for global network deployments. It includes these sections:
This chapter assumes you have installed and performed the initial configuration of the SCC. For details, see the SteelHead Management Console User’s Guide.
This chapter also assumes that you are familiar with the various deployment options available to you. For details, see the SteelHead Deployment Guide and the SteelCentral Controller for SteelHead Deployment Guide.
Riverbed recommends that you do not use the Riverbed CLI to configure the SCC.
Hardware and Software Dependencies
This section provides information about product dependencies and compatibility. It includes these topics:
Hardware and Software Requirements
This tables summarize the hardware and software requirements for the SCC.
SCC Component | Hardware and Software Requirements |
SCC appliance | 19-inch (483-mm) two-post or four-post rack. Model 1000 can be installed on a desktop. |
SCC Management Console | The SCC has been tested with Mozilla Firefox Extended Support Release version 38, and Microsoft Internet Explorer 11. When you upgrade to v9.2, clear the browser cache and cookies to ensure the user interface displays correctly. JavaScript and cookies must be enabled in your web browser. |
SCC Compatibility
This section summarizes SCC support by product and identifies compatible software versions across Riverbed products.
Note: After updating the version of SSH, older releases of SCC cannot connect to newer software on managed appliances. If you plan to upgrade your appliances, upgrade the SCC first to avoid disconnections. See the Knowledge Base article
S27759 for complete details.
SteelHead CX
SCC 9.2 supports configuration and monitoring for SteelHead CX 8.6 and later.
In general, each SCC version can manage the features found in the similarly numbered RiOS version; for optimum compatibility, Riverbed recommends aligning the SCC and SteelHead CX versions.
The SCC can manage features where they occur in a subsequent RiOS version. For example, with SCC 9.0 managing SteelHead CX 9.1 systems, the SCC can manage the 9.0 features that are present in 9.1, but not the features that are new in 9.1. This restriction is referred to as parity in this compatibility table.
This table shows the supported and recommended SCC versions for SteelHead CX releases.
SteelHead RiOS Version | Recommended Version | SCC Appliance 9.1.x | SCC Appliance 9.0.x | SCC Appliance 8.6.x |
SteelHead CX 9.2.0 | SCC 9.2.0 | Full Support | Parity | Parity |
SteelHead CX 9.1.0a | SCC 9.1.0d | Full Support | Parity | Parity |
SteelHead CX 9.0 | SCC 9.0 | Full Support | Full Support | Parity |
SteelHead CX 8.6 | SCC 8.6 | Full Support | Full Support | Parity |
To view how many SteelHeads an SCC can manage, see
knowledge base article S14106. SteelHead EX
SCC 9.2 supports configuration and monitoring for SteelHead EX 3.0 and later.
This table shows the supported and recommended SCC versions for SteelHead EX releases.
EX Version | SteelHead RiOS Version | Recommended SCC Version |
4.2 | 9.2.0 | 9.2.0 |
4.2 | 9.1.1a | 9.1.0d |
4.1 | 9.1 | 9.1 |
3.6 | 9.0 | 9.0 |
3.5.3 | 8.6 | 8.6.0 |
SteelHead Interceptor
SCC 9.2 supports configuration and monitoring for SteelHead Interceptor 3.x and later.
Pushing configurations to appliances is limited to XBridge, system settings, security settings, and in-path and load balancing rules for clusters.
SteelHead Mobile
SCC 9.2 supports monitoring only for SteelHead Mobile 4.0 and later.
SteelFusion Core
SCC supports monitoring only for SteelFusion Core 4.0 and later.
This table shows the supported and recommended SCC versions for SteelFusion Core releases.
SteelFusion Core Version | Recommended SCC Version |
4.3 | 9.1.0d, 9.2 |
4.2 | 9.1.0d |
4.1 | 9.1 |
4.0 | 9.0 |
SteelFusion Edge
SCC supports monitoring and partial configuration for SteelFusion Edge 4.0 and later. SCC enables you to configure and monitor SteelHead (RiOS) features except web proxy. You cannot configure ESXi from the SCC.
This table shows the supported and recommended SCC versions for SteelFusion Edge releases.
SteelFusion Edge Version | Recommended SCC Version |
4.3 | 9.1.0d, 9.2 |
4.2 | 9.1.0d |
4.1 | 9.1 |
4.0 | 9.0 |
Legacy Policy Push Restrictions
This table summarizes the legacy policy push restrictions in SCC 9.0 and later. These restrictions only apply to policies configured with software versions prior to SCC 9.0.
SCC Feature | SteelHead CX Software | SteelHead EX Software | SteelHead Interceptor |
Outbound QoS (Basic) | 8.0.x only supported 9.0 and later not supported | 2.0.x only supported 3.6.x and later not supported | — |
Outbound QoS (Advanced) | 8.0.x only supported 9.0 and later not supported | 2.0.x only supported 3.6.x and later not supported | — |
Outbound QoS Interfaces | 9.0 and later not supported | 3.6.x and later not supported | — |
Inbound QoS | 9.0 and later not supported | 3.6.x and later not supported | — |
Inbound QoS Interfaces | 9.0 and later not supported | 3.6.x and later not supported | — |
Path Selection (legacy) | 8.0.x not supported 9.0 and later not supported | 2.0.x not supported 3.6.x and later not supported | — |
Host Labels | 8.0.x not supported | 2.0.x not supported | — |
SnapMirror | 8.0.x not supported | 2.0.x not supported | — |
REST API Access | 8.0.x not supported | 2.0.x not supported | — |
Management ACL | — | — | 3.x.x not supported |
Firewall Requirements
These ports must be open for the SCC to function properly:
• TCP port 9443 and 443 for HTTPS communication. SCC 9.0.0 and later use port 443 for the REST API SSL key exchange between the SCC and SteelHeads. After the certificate exchange is successful, an OCC channel is established between the SteelHead and the SCC on port 9443; thereafter the SCC uses port 9443 to communicate with the SteelHeads.
• TCP port 22 for CLI communication.
• If the network is public, UDP port 4500 for encryption services.
Because optimization between SteelHeads typically takes place over a secure WAN, it is not necessary to configure company firewalls to support SteelHead-specific ports.
If your SteelHead is behind a firewall, you can configure an SSL authorized port using the CLI to connect and manage these SteelHeads. For detailed information, see
Connecting SteelHeads When the SCC Is Behind a FirewallUpgrading the SCC
You can upgrade the SCC only to the next major version. Do not skip intermediate major versions. Multiversion upgrades and downgrades can result in database incompatibilities, potentially leading to data corruption.
Upgrade Considerations
If you are running SCC 8.6 and earlier, you must perform a multistep upgrade; for example:
5.5.4c > (6.0.1 or 6.1.x) > 6.5.x > (7.0.x or 8.0.x) > 8.5.x > 8.6.0 > (9.0.x or 9.1.0 or 9.2) > 9.2.0
You can upgrade from SCC 8.6 > 9.2, but a multistep upgrade ensures that automigration of statistics occurs correctly. Contact Riverbed Support at https://support.riverbed.com for detailed information about upgrade paths.
Upon upgrading, clear your browser cache and cookies to ensure that the SCC Management Console displays correctly. Also upon upgrading, make sure none of the processes have exited due to an error. All new and existing processes should run as expected. Some processes are dependent on other processes so they might take time to run at start up.
With SCC 9.0 or later, policy push configurations with the SteelHeads running RiOS 8.0 or later (that is, SteelHead CXs running 8.0+ and SteelHead EXs running 3.6 or later) are not supported. Earlier version appliances are still connected and the SCC still manages health and alarms for these appliances. The SCC 9.0 or later does not support policy pushes for SteelHead EX 2.0 and earlier, and SteelHead CXs 8.0 and earlier.
Consider these guidelines before upgrading SCC:
• The SCC must be upgraded to 8.6 before it can be upgraded to 9.0 or later.
• Upgrading from RiOS 8.6.x (or earlier) to 9.0 (and later) does not automatically migrate previous QoS rules to a new configuration. The SCC provides a QoS migration wizard to assist you in migrating your QoS rules.
• You cannot migrate previous path selection rules from SCC 8.6.x (or earlier) to 9.0 or later.
• If you mix RiOS software versions in your network, the releases might not fully support certain features (for example, QoS) and you cannot take full advantage of the SCC features that are not part of the older software versions.
Recommended Upgrade Paths
To find allowed upgrades between software versions and recommended upgrade paths, see Riverbed Support at https://support.riverbed.com. The tool includes the recommended intermediate software versions.
• The SCC must be upgraded to 8.6 before it can be upgraded to 9.1 or later.
• The SCC must be upgraded to 8.5 before it can be upgraded to 8.6.
• The SCC must be upgraded to 8.0 before it can be upgraded to 8.5.
If you are running a version of the SCC prior to 8.0, please contact Riverbed Support regarding acceptable upgrade paths.
Upgrading the SCC Software Version
Perform this task to upgrade your software. These instructions assume you are familiar with the SCC, the CLI, and the SCC Management Console.
To upgrade SCC software
1. Download the software image from Riverbed Support to your desktop.
2. Log in to the SCC using the administrator account (admin).
3. Choose Administration > Maintenance: Software Upgrade to display the Software Upgrade page.
4. Under Install Upgrade, choose one of these options:
– From URL - Type the URL that points to the software image that you want to upgrade to. Use one of these formats:
http://host/path/to/file
https://host/path/to/file
ftp://user:password@host/path/to/file
scp://user:password@host/path/to/file
– From Riverbed Support Site - Before you begin, make sure you have created a support account at https://support.riverbed.com. Select the target release number from the drop-down list to download a delta image directly to the appliance from the Riverbed Support site. The downloaded image includes only the incremental changes. You do not need to download the entire image. The system downloads and installs the new image immediately after you click Install. To download and install the image later, schedule another date or time before you click Install.
– From Local File - Browse to your file system and select the software image.
– Schedule Upgrade for Later - Type the date and time using this format:
YYYY/MM/DD HH:MM:SS.
5. Click Install to upgrade your SCC software.
The software image can be quite large; uploading the image to the system can take a few minutes. Downloading a delta image directly from the Riverbed Support site is faster because the downloaded image includes only the incremental changes and is downloaded directly to the appliance.
As the upgrade progresses, status messages appear.
After the installation is complete, you are reminded to reboot the system to switch to the new version of the software.
6. Choose Administration > Maintenance: Reboot/Shutdown and click Reboot.
The appliance can take a few minutes to reboot. This is normal behavior as the software is configuring the recovery flash device. Do not press Ctrl-C, unplug, or otherwise shut down the system during this first boot. There is no indication displayed during the system boot that the recovery flash device is being configured.
After the reboot, the Dashboard, Software Upgrade, and Help pages in the Management Console display the RiOS version upgrade.
Migration Procedures
For detailed information about SCC migration best practices, see
SCC Best Practices. SteelHead Autoregistration
SteelHeads must be registered with the SCC so that you can monitor and manage them with the SCC.
SteelHeads are designed to send a registration request periodically to the SCC—either to an IP address or hostname you specify when you run the SteelHead configuration wizard, or to a default SCC hostname. For autoregistration with the default hostname to work, you must configure your DNS server to map to the hostname riverbedcmc and the IP address of the SCC either as a CNAME or as an A record.
During autoregistration, the SteelHeads do not send passwords to the SCC. Unless the password value has been modified in the Manage Appliances page, the SCC assumes that the default password is
password. For details, see
Adding Appliances.
After a SteelHead is registered, you can set autoconfiguration to automatically push the current configuration when the SteelHead connects.
HTTPS Communication Channel
Traditionally, appliances communicated with the SCC via an SSH channel. In SCC 9.0 an HTTPS (on TCP port 9443) communication channel was added. This channel is used to push and pull the new hybrid networking features supported in the SCC (for example, path selection, QoS, and secure transport).
For managed appliances (SteelHead 9.0, SteelHead EX 3.6, SteelFusion 4.0, and later) both the SSH and the HTTPS channels must be in a connected state. If either one of these channels is down, then a push from the SCC to the appliance will fail. For instance if the HTTPS connection is down, pushing the hybrid network configuration from the SCC to appliances will fail.
For detailed information about troubleshooting, see
HTTPS Communication Channel.
Connecting SteelHeads When the SCC Is Behind a Firewall
SCC 9.2 provides you with the ability to configure an SSL authentication port for SteelHeads when the SCC is behind a firewall with restricted access to ports 443 and 80. This feature enables SteelHeads to communicate with the SCC. You configure the SSL authentication port using the SCC CLI.
This diagram shows a SteelHead-1 (SH-1) connected to the SCC that is listening on port 443 without a firewall. The SteelHead-2 (SH-2) is connected to the SCC through a firewall that has restricted access to ports 443 and 80. On the SCC for SteelHead-2 (SH-2), you can configure an SSL authentication port (for example, 7443) using a CLI command enabling you to communicate with SH-2.
Figure: SCC with Custom Authorized Port 7443
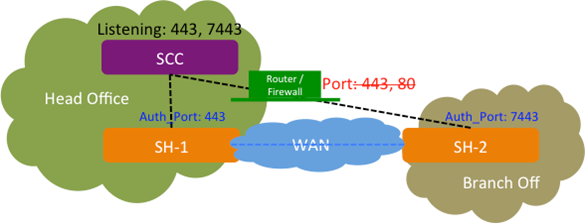
You can configure one additional authentication port in addition to the existing port 443.
The SSL authentication port feature is only available via the CLI; it is not available in the SCC Management Console.
For detailed information about connecting and using the Riverbed CLI, see the Riverbed Command-Line Interface Reference Manual.
To enable communication to SteelHeads with restricted access
1. On the SCC, connect to the CLI in configuration mode. For detailed information about connecting and using the Riverbed CLI, see the Riverbed Command-Line Interface Reference Manual.
2. To configure SSL authentication port access, at the system prompt enter:
amnesiac (config) # ocs authport port <port-number>
where <port-number> is the authentication port number on which you want to establish communication with the SCC.
3. On the SteelHead, connect to the CLI in configuration mode and enter this command at the system prompt:
ocd connection cmc csr_auth auth_port <port number>
where <port-number> is the authorized port number on which you want to establish communication with the SCC. Make sure this is the same port you configured on the SCC.
Troubleshooting
On the SCC:
• The port number should have an appropriate entry when you run the netstat command. On the SCC, via the shell, at the system prompt enter:
netstat -an |grep <port-number>
• The port number should be listed in the Apache /etc/httpd/http.conf file:
Listen <port-number>
If the port number does not appear, restart the http service on the SCC:
pm process httpd restart
On the SteelHead:
• Enter the show ocd connections command. It should list the port number as Auth Port and Status “Connected”.
• To ensure registration is successful, enter these commands:
amnesiac # show scc
amnesiac # show cmc
Connecting to the SCC Management Console
To connect to the Management Console, you must know the host, domain, and administrator password that you assigned in the configuration wizard.
Note: Cookies and JavaScript must be enabled in your web browser.
Note: Before you begin, clear your browser cache and cookies to ensure the user interface displays correctly.
To connect to the SCC Management Console
1. Enter the URL for the SCC in the location box of your browser:
<protocol>://<host>.<domain>
<protocol> is http or https. The secure HTTPS uses the SSL protocol to ensure a secure environment. When you connect using HTTPS, you are prompted to inspect and verify the SSL certificate. This is a self-signed certificate used to provide encrypted web connections to the SCC.
<host> is the IP address or hostname you assigned the SCC during initial configuration. If your DNS server maps the IP address to a name, you can specify the DNS name.
<domain> is the full domain name for the SCC.
The SCC Sign In page appears.
2. In the text box, specify the user login: admin, monitor, a login from a RADIUS or a TACACS+ database, or a previously configured RBM account.
The default login is admin. Users with administrator privileges can configure and administer the SCC. Users with monitor privileges can view SCC reports but they cannot configure the system.
3. In the Password text box, specify the password you assigned in the configuration wizard of the SCC.
The SCC is shipped with password as the default password.
4. Click Log In to log in to display the dashboard.
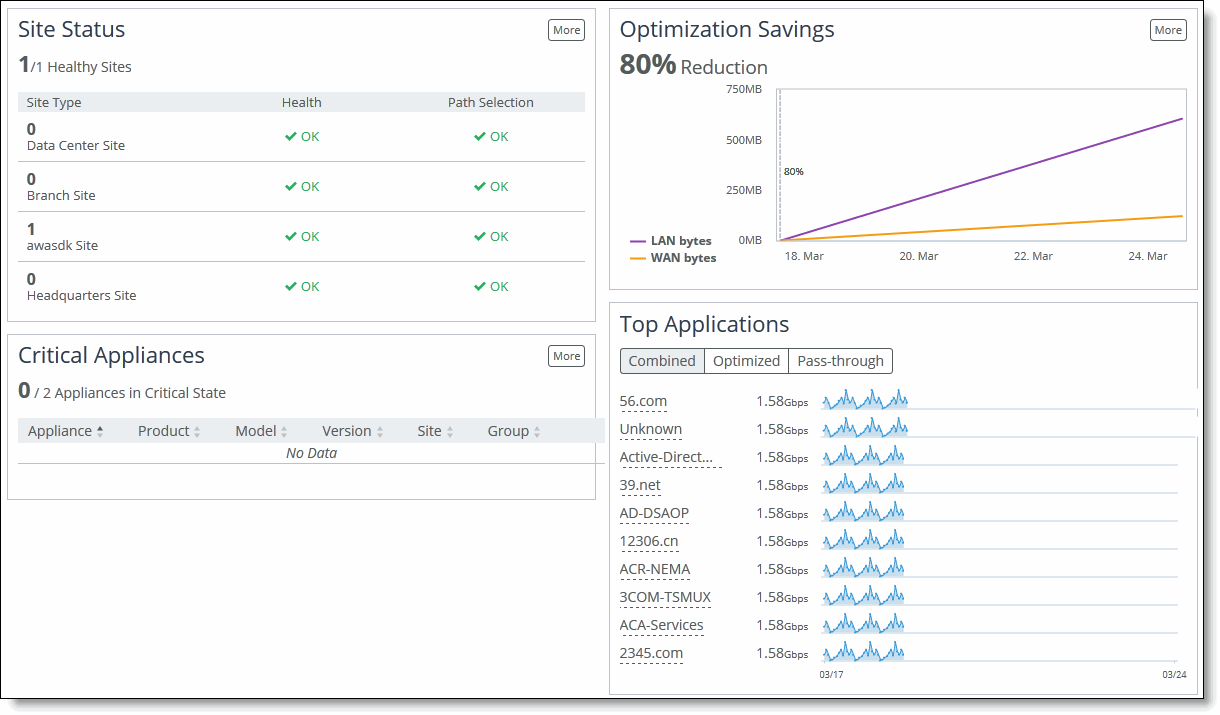
Figure: The Dashboard