Controlling Direct Collection
This section explains how to control direct collection and includes the following topics:
Accessing the Device Manager
1. Log in to the UI as admin.
2. Choose Configure > Device Manager. The Device Manager screen appears.
The maximum number of groups and sites that can be displayed in the left navigation panel of the Device Manager has been increased to 1000 (previously a maximum of 500). Additionally, Device Manager’s right-click menu has been enhanced to include new options to Clear Collected Data, Collect from Device(s), and Collect from Device(s) and Update Model.
Working with device entries
You must have administrative privileges to create and/or modify device entries.
This section includes the following topics:
What is a device entry?
NetIM requires certain information to access a device using SNMP and/or WMI. This access information—plus additional fields that support NetIM functionality—is organized into a device entry.
Device entries are automatically created and populated with needed information when you run the Add/Discover Devices wizard.
Device entries can also be created by importing a device info file or manually created through the user interface. (See
Creating, modifying, and deleting device entries.)
Each separately managed network element must have its own device entry. Because of this, some devices require multiple device entries. For example, a switch may consist of a switching core running CatOS and one or more routing modules running IOS. In this case, each separately managed addressable module must have its own device entry. Interface and port modules do not need to be handled in this fashion.
Device entries are stored in the NetIM database. When a project is removed or the database cleaned, device entries are exported to a device info file before they are removed. Connection statistics, however, are not preserved.
Related topics
Viewing device entries
The Device Manager lists device entries.
Not all components of a device entry are displayed in the Device Manager. The password, privileged password, and community string fields are encrypted and stored in the NetIM database as part of the device entry but are not included in the display.
The Device Driver and Login Script fields define scripts internal to NetIM that are used to connect to a device using the CLI. These fields are required for AppNetwork Path Analysis. These are automatically determined by the Add/Discover Devices wizard. Do not modify unless directed to do so by technical support.
Filtering device entries
The Device Manager supports robust filtering.
You can add entries in the Device table based on Sites, Groups, and Views, using the left side navigation and selection expander.
You can also add and remove columns in the main device listing panel by expanding the Column Filtering on the right side of the page, and selecting the columns you want to display.
You can, for example, choose to view the devices primarily by their sysName or hostname instead of device name and access address or hide columns you are not interested in seeing.
Each column in Device Manager supports sorting, searching, and filtering.
Saving column layout
After you have determined the column layout that best suits your purposes, you can save the layout so that it persists between sessions by clicking the Save icon on the far right of the Device Manager page, which brings up the Save Grid Orientation window.
Every user can make their own column layout and save it.
Click Save to save your layout.
Related topics
Device entry components
The device entry components are listed in the following table.
Device Management View
The following table lists the components of each device entry.
Field | Description |
Active | Determines whether a device is a candidate for metric polling and/or AppNetwork Path Analysis. • When a device entry is inactive it will be skipped. • When active, the appropriate Collect flag determines. |
Device Name | Indicates the hostname of the device. |
Access Address | Specifies the network address used to access the device. |
Polling Profile | Shows the name of the polling profile (configured in the
Using the Polling wizard to create, clone, edit or delete Polling Profiles) to use for the device. |
Alerts | Shows the alerts (configured in the
Configuring an alert) associated with the device. |
Managed By | “Local” indicates that polling of the device is managed by the local system. |
Polling Profile | Specifies the polling profile assigned to the device. A device may have only one polling profile. See
Configuring Metric Polling. |
Alerts | Specifies alerts assigned to the device. A device may have multiple alerts. See
Configuring Metric Alerts. |
SNMP Version | Indicates version of SNMP used to contact the device. |
Device Driver | Specifies the device console “show” commands that will be executed to collect data. The device driver can be imported from a file or NetIM can automatically determine the appropriate device driver when discovering devices. Device drivers are managed using the
Enabling collection of CLI data for a device driver.. |
Login Script | Specifies the initial device prompt and a sequence of commands and expected responses for successful command-line interface (CLI) login to this device. This is automatically determined by the
Add/Discover Devices wizard |
Access Method | Specifies the protocol used for CLI access. (TELNET, SSHv1, SSHv2, or Unknown). |
CLI Username | Specifies the username for CLI login. |
WMI Username | Specifies the username for WMI access. |
WMI Domain | Specifies the domain for WMI access. |
Password | Specifies the password for CLI login. This field does not display in the Device Manager. |
Privileged Password | Specifies the password (if needed) to enter the privileged exec mode during a CLI session. This field does not display in the Device Manager. |
System Name | Specifies the device name. Supports NetIM’s archiving function. Do not modify unless directed to do so by technical support. |
Collect CLI | Do not modify unless directed to do so by technical support. When selected, CLI metrics are being collected. |
Collect WMI | Do not modify unless directed to do so by technical support. When selected, WMI metrics are being collected. |
Collect Metrics | When the
Active flag is enabled for a device, the status of the Collect Metrics flag determines whether the Poller will attempt to collect metrics from the device. To enable/disable polling, adjust the
Active flag for the device. You should not disable the Collect Metrics flag. See
Manually enabling or disabling metric polling to learn more. |
Description | Free-text description. |
Country | Specifies the country, region, and city in which a device is located. See
Setting Geographic Location. |
Region |
City |
Time Zone | Specifies the time zone associated with a device. This value overrides the default time zone setting from Basic Setup. See
Setting Time Zones and Business Hours. |
Business Hours | Identifies the Business Hour profile associated with the device. See
Setting Time Zones and Business Hours. for further information on how to use this wizard. |
Required credentials for CLI (AppNetwork path analysis) and SNMP and/or WMI (metric polling)
Credentials are required to connect to a device using the CLI or SNMP and/or WMI. The following table lists required device entry fields for each.
Display name | CLI | SNMP | WMI |
Device Name | X | X | X |
Access Address | X | X | X |
Username | X | | X |
Password | Xb | | X |
Privileged Password | Xb | | X |
Device Driver | X | | X |
Login Scriptc | X | | X |
Access Methodc | X | | X |
Read Community String | | X | X |
SNMP v3 Credentials | | Xd | X |
1 CLI access is required for Device Config File Collection and AppNetwork Path Analysis.
2 Required fields depend on device login.
3 The Add/Discover Devices wizard automatically determines the appropriate values and sets them in the device entry when you choose an entry mode that uses SNMP discovery.
4 Read community string is required for SNMPv2c and below. SNMP v3 credentials are required for SNMP v3. The following require SNMP access: Device MIB Configuration Import, Device MIB MPLS TE Import, SNMP MIB Poller, and IP Detection Service.
Related topics
Creating, modifying, and deleting device entries
For information on creating, modifying, and deleting device entries, see
Adding Devices to Device Manager and
Advanced Methods for Creating Device Entries.Creating groups and sites, and editing and deleting members
The Device Manager supports group/site creation, group/site member editing, and group/site member deletion.
1. Choose Configure > Device Manager.
2. Select the device entries of interest, and then click the Selected action menu. A pop-up menu appears.
3. Select Grouping, which displays options to:
– Create Site/Group
– Add to Site/Group
– Remove From Site/Group.
4. Select the operation you want to perform.
Note the following:
• Group and Site names and descriptions can also be edited from the group and site pages action menus.
• You can bulk delete all groups or all sites from the Configure > All Settings -> Customize > General Settings page.
Controlling collection using the Active flag and collection settings
Each device in the Device Manager has several flags that control whether NetIM will contact that device for various purposes. For example:
• Active—Specifies whether that device will be contacted for any purpose. If not selected, none of the following will be performed, regardless of their setting.
• Collect SNMP—Specifies whether NetIM will include this device in direct collection (the effort to build a network model) by contacting its SNMP interface.
• Collect WMI—Specifies whether NetIM will include this device in direct collection (the effort to build a network model) by contacting its WMI interface.
• Collect Metrics—Specifies whether NetIM will collect performance metrics from this device’s SNMP interface.
For information on modifying these settings for a device, see
Adding Devices to Device Manager.About streaming telemetry
Streaming Telemetry (or Model-Driven Telemetry) is a rapidly evolving technology for network monitoring. Metric data can be streamed from network devices continuously and at a high granularity thereby providing near real-time access to operational device metrics. NetIM can subscribe to specific data using standards-based YANG data models.
Streaming telemetry topology
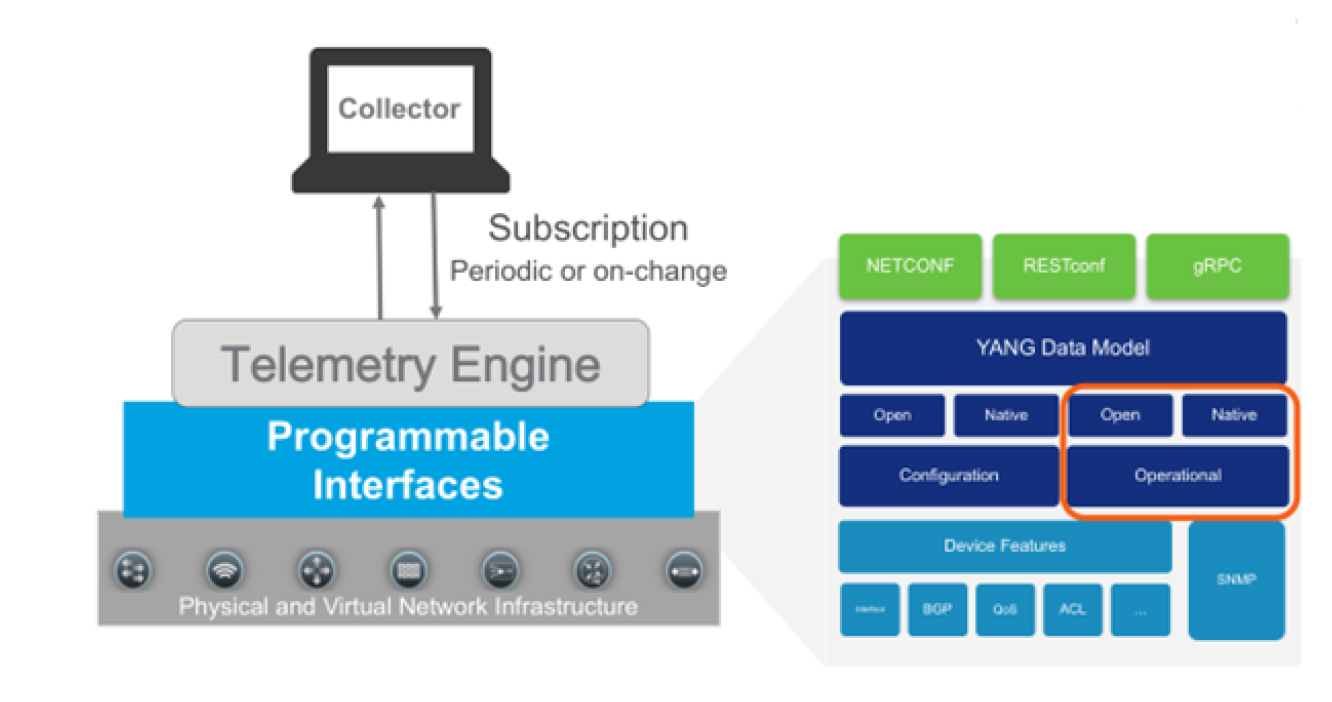
NetIM sets up a subscription to a data set in a YANG model. A subscription is a contract between a subscription service and a subscriber that specifies the type of data to be pushed. Subscription allows clients to subscribe to metric data and the device pushes the data to the collector for the subscribed data. Streaming telemetry data can be sent periodically or on-change.
NetIM currently expects periodic. Streaming telemetry configuration can also be dial-in or dial-out. Streaming telemetry provides device metric data to NetIM at a much higher frequency, more efficiently than classic SNMP is able to do. NetIM’s Streaming Telemetry support populates existing metric classes and is configured per device within the NetIM Device Manager.
Many resources exist for learning about streaming telemetry and vendor implementations. We do not attempt to duplicate the many excellent sources of material that exist for reference. We provide basic information on configuring your network devices for streaming telemetry. You should reference each vendor’s reference and configuration guides for comprehensive information on how to configure vendor devices for streaming telemetry. We will focus on how you configure NetIM to successfully receive the streaming telemetry data.
NetIM’s Model-driven Telemetry Receiver microservice is hosted on the NetIM Core VM. Use the IP address of the core VM as the address to use for configuring streaming telemetry on your network devices (at TCP port 57000 for dial-out). Check with the device vendor regarding which specific models and OS versions support streaming telemetry. In some cases, additional vendor feature licensing may be required for the devices to support streaming telemetry.
For streaming telemetry, configuration is required on NetIM UI, as well as, on the device. You must first ensure that you have an existing device object with interfaces in NetIM. The NetIM device model can be created by using either CLI data or SNMP data. However, you should ensure that SNMP polling is turned off for the devices for which you want the streaming telemetry data. Once the device model is created, configure the actual network device and then NetIM for telemetry collection.
NetIM supports both dial-in and dial-out.
• Dial-in—The network device listens on an established port for the Collector (NetIM) to subscribe (dial-in) to collect the metrics.
• Dial-out—The network device dials-out to the Collector (NetIM’s Telegraf instance) running on the core VM. In dial-out, the network device initiates the connection.
For dial-in, NetIM creates a gNMI subscription template. The NetIM template requests that metric data to be provided at 10-second granularity. The device may abide by the 10-second granularity request or ignore it. The actual metric granularity provided is negotiated with the device with the requested granularity in the template just a suggestion to the device.
Communication between the device and NetIM is encrypted as TLS is enabled by default. TLS can be disabled to support unencrypted communication. Unencrypted communication requires manual configuration. SSL certificate validation can also be enabled.
Basic steps for setting up streaming telemetry in NetIM
1. Configure a device in the Device Manager for CLI or SNMP collection. Make sure that both SNMP polling and WMI polling are turned off for the Device in the Device Manager.
2. Perform a collection from the device and ensure the device model has attributes, interfaces, and interface attributes in NetIM.
3. Configure the device to enable streaming telemetry for dial-in or dial-out.
4. Once your device is configured for streaming telemetry, you can enable streaming telemetry for the device in the Device Manager. Select the Telemetry Option.
– For gNMI Dial-in, provide the IP address, port, and credentials.
– For gNMI dial-out, you select the gNMI Dial Out option and NetIM will be configured to receive the data from the device.
5. To visually confirm you have started to receive streaming telemetry, just check the At a Glance page for the metrics. You should see metrics at the granularity you have configured for streaming telemetry.
We will document some details on how to configure various device types for Streaming Telemetry integration. This documentation is not a replacement for your device vendor configuration guide.
Streaming telemetry for Cisco IOS-XR
Cisco IOS-XR Dial-Out Support
Metric Class | Origin | YANG Model Path |
DEV_STATUS | Device | sensor-path Cisco-IOS-XR-nto-misc-oper:memory-summary/nodes/node/summary |
MEM_USAGE_v2 | Device | sensor-path Cisco-IOS-XR-nto-misc-oper:memory-summary/nodes/node/summary |
CPU_UTIL | Device | sensor-path Cisco-IOS-XR-wdsysmon-fd-oper:system-monitoring/cpu-utilization |
IFC_STATUS | OpenConfig | sensor-path openconfig-interfaces:interfaces/interface/state |
IFC_UTIL | OpenConfig | sensor-path openconfig-interfaces:interfaces/interface/state |
IFC_ERROR | OpenConfig | sensor-path openconfig-interfaces:interfaces/interface/state |
IOS-XR Sample Dial-Out Configlet
telemetry model-driven
destination-group dg-netim
address-family ipv4 11.11.11.11 port 57000
encoding self-describing-gpb
protocol grpc no-tls
!
!
sensor-group sg-netim
sensor-path openconfig-interfaces:interfaces/interface/state
sensor-path Cisco-IOS-XR-wdsysmon-fd-oper:system-monitoring/cpu-utilization
sensor-path Cisco-IOS-XR-nto-misc-oper:memory-summary/nodes/node/summary
!
subscription sub-netim
sensor-group-id sg-netim sample-interval 10000
destination-id dg-netim
!
!
Cisco IOS-XR Dial-In Support
Metric Class | Origin | YANG Model Path |
DEV_STATUS | Device | sensor-path Cisco-IOS-XR-nto-misc-oper:memory-summary/nodes/node/summary |
MEM_USAGE_v2 | Device | sensor-path Cisco-IOS-XR-nto-misc-oper:memory-summary/nodes/node/summary |
CPU_UTIL | Device | sensor-path Cisco-IOS-XR-wdsysmon-fd-oper:system-monitoring/cpu-utilization |
IFC_STATUS | OpenConfig | sensor-path openconfig-interfaces:interfaces/interface/state |
IFC_UTIL | OpenConfig | sensor-path openconfig-interfaces:interfaces/interface/state |
IFC_ERROR | OpenConfig | sensor-path openconfig-interfaces:interfaces/interface/state |
IOS-XR Sample Dial-In Configlet
grpc
port 57000
#TLS is enabled by default
no-tls
address-family ipv4
!
gNMI Config:
[[inputs.cisco_telemetry_gnmi.subscription]]
origin = "openconfig"
path = "/interfaces/interface/state/"
subscription_mode = "sample"
sample_interval = "10s"
[[inputs.cisco_telemetry_gnmi.subscription]]
origin = "Cisco-IOS-XR-nto-misc-oper"
path = "/memory-summary/nodes/node/summary"
subscription_mode = "sample"
sample_interval = "10s"
[[inputs.cisco_telemetry_gnmi.subscription]]
origin = "Cisco-IOS-XR-wdsysmon-fd-oper"
path = "/system-monitoring/cpu-utilization"
subscription_mode = "sample"
sample_interval = "10s"
Streaming telemetry for Cisco NX-OS
Regardless of whether you are doing dial-in or dial-out on the Nexus, you must ensure the following features are enabled on your NX-OS device:
• feature telemetry
• feature grpc
• feature nxapi
• feature Netconf
NX-OS Sample Dial-Out Configlet
# Enable telemetry
telemetry
# Destination group with a unique identifier defines the receiver details
destination-group test-netim
ip address 10.46.250.197 port 57000 protocol gRPC encoding GPB
certificate /bootflash/telegraf.crt telegraf
# Sensor group with unique identifier specifies the data-source and the path to the metrics
sensor-group test-netim
data-source DME
path environment
path interface
path resources
# Subscription with unique identifier binds the destination group and the sensor group
# to the sample refresh internal
subscription 1
dst-grp test-netim
snsr-grp test-netim sample-interval 120000
Cisco NX-OS Dial-Out Support
Metric Class | Origin | YANG Model Path |
MEM_USAGE_v2 | Device | data-source DME path sys/procsys/sysmem/sysmemfree path sys/procsys/sysmem/sysmemusage path sys/procsys/sysmem/sysmemused |
CPU_UTIL | Device | data-source DME path sys/procsys/syscpusummary/syscpu-ALL/total |
IFC_STATUS | OpenConfig | path openconfig-interfaces:interfaces/interface/state path openconfig-interfaces:interfaces/interface/state/counters |
IFC_UTIL | OpenConfig | path openconfig-interfaces:interfaces/interface/state path openconfig-interfaces:interfaces/interface/state/counters |
IFC_ERROR | OpenConfig | path openconfig-interfaces:interfaces/interface/state path openconfig-interfaces:interfaces/interface/state/counters |
NX-OS Dial-In Sample Configlet
Additional configuration is not required for NX-OS dial-in.
Cisco NX-OS Dial-In Support
Metric Class | Origin | YANG Model Path |
DEV_STATUS | Device | /System/ch-items |
MEM_USAGE_v2 | Device | /System/procsys-items /System/procsys-items/sysmem-items/sysmemusage-items /System/procsys-items/sysmem-items/sysmemused-items /System/procsys-items/sysmem-items |
CPU_UTIL | Device | /System/procsys-items /System/procsys-items/syscpusummary-items/syscpu-items/SysCpu-list/total-items |
IFC_STATUS | OpenConfig | /interfaces/interface/state/oper-status /interfaces/interface/state/admin-status |
IFC_UTIL | OpenConfig | /interfaces/interface/state/counters |
IFC_ERROR | OpenConfig | /interfaces/interface/state/counters |
Streaming telemetry for Cisco IOS-XE
Cisco IOS-XE Dial-Out Support
Metric Class | Origin | YANG Model Path |
DEV_STATUS | Device | filter xpath /device-hardware-xe-oper:device-hardware-data/entity-information |
MEM_USAGE_v2 | Device | filter xpath /memory-ios-xe-oper:memory-statistics |
CPU_UTIL | Device | filter xpath /process-cpu-ios-xe-oper:cpu-usage/cpu-utilization |
IFC_STATUS | OpenConfig | filter xpath /oc-if:interfaces/interface/state |
IFC_UTIL | OpenConfig | filter xpath /oc-if:interfaces/interface/state |
IFC_ERROR | OpenConfig | filter xpath /oc-if:interfaces/interface/state |
IOS-XE Example Dial-Out Configlet
telemetry ietf subscription 1
encoding encode-kvgpb
filter xpath /memory-ios-xe-oper:memory-statistics
stream yang-push
update-policy periodic 2000
receiver ip address 11.11.11.11 57000 protocol grpc-tcp
telemetry ietf subscription 2
encoding encode-kvgpb
filter xpath /process-cpu-ios-xe-oper:cpu-usage/cpu-utilization
stream yang-push
update-policy periodic 2000
receiver ip address 11.11.11.11 57000 protocol grpc-tcp
telemetry ietf subscription 3
encoding encode-kvgpb
filter xpath /device-hardware-xe-oper:device-hardware-data/entity-information
stream yang-push
update-policy periodic 2000
receiver ip address 11.11.11.11 57000 protocol grpc-tcp
telemetry ietf subscription 4
encoding encode-kvgpb
filter xpath /oc-if:interfaces/interface/state
stream yang-push
update-policy periodic 2000
receiver ip address 11.11.11.11 57000 protocol grpc-tcp
Streaming telemetry for Arista EOS
Dial-in Sample Configlet
management api gnmi
transport grpc default
provider eos-native
Streaming telemetry support and certificates
You can configure NetIM Streaming Telemetry to use TLS with either CA-signed or self-signed certificates.
CA-signed certificates
When the Model-driven Telemetry microservice’s telegraf instance starts up, required keys and certificates are created in a directory on the NetIM Core VM:
/home/netimadmin/common/core-tenant-stack/1/telemetry-telegraf/cert
The files of interest are:
• telegraf.key (telegraf’s private key)
• telegraf.csr (telegraf’s signing request)
• telegraf.pem (the signed telegraf certificate)
The telegraf instance configuration file points to both the telegraf.key and telegraf.pem file, by default. At the end of the signing process, both of those files need to be used/paired from the signing process and need to be named exactly as shown.
In order to use an external root CA, perform the following steps:
1. Retrieve the telegraf.csr/copy its contents
if you want to create your own .csr you can use the existing telegraf.key as the base
2. Execute a signing request with the root CA, an example command shows this as follows:
Example: openssl x509 -req -in telegraf.csr -CA rootCA.pem -CAkey rootCA.key -CAcreateserial -out telegraf.pem -days 3650 -sha256
This will create the signed certificate in ‘telegraf.pem’
3. Copy the newly signed telegraf.pem file and overwrite the original one at <NetIM core host>/<user home>/telemetry-telegraf/cert
If you want a different telegraf.key with an original telegraf.csr then the .key file must also be copied over
4. Restart the telemetry-telegraf service
5. Copy the rootCA.pem file over to the dial-out enabled streaming telemetry devices and configure accordingly
Self-Signed Certificates
When the streaming telemetry collector service starts up, it will create (if they do not already exist) a new private key for telegraf and a self-signed certificate for devices to use for dial-out. The self-signed certificates will be generated in the form of telegraf.crt and telgraf.pem as well as the private key and signing request in telegraf.key and telegraf.csr, respectively. NetIM stores these files on the NetIM Core VM in the directory: /home/netimadmin/common/core-tenant-stack/1/telemetry-telegraf/cert
If you want to use NetIM-generated self-signed certificates for dial-out workflows, you need to copy the certificate (telegraf.pem) to the respective devices and configure accordingly.


