Type | Description | Asymmetric routing table and log entries |
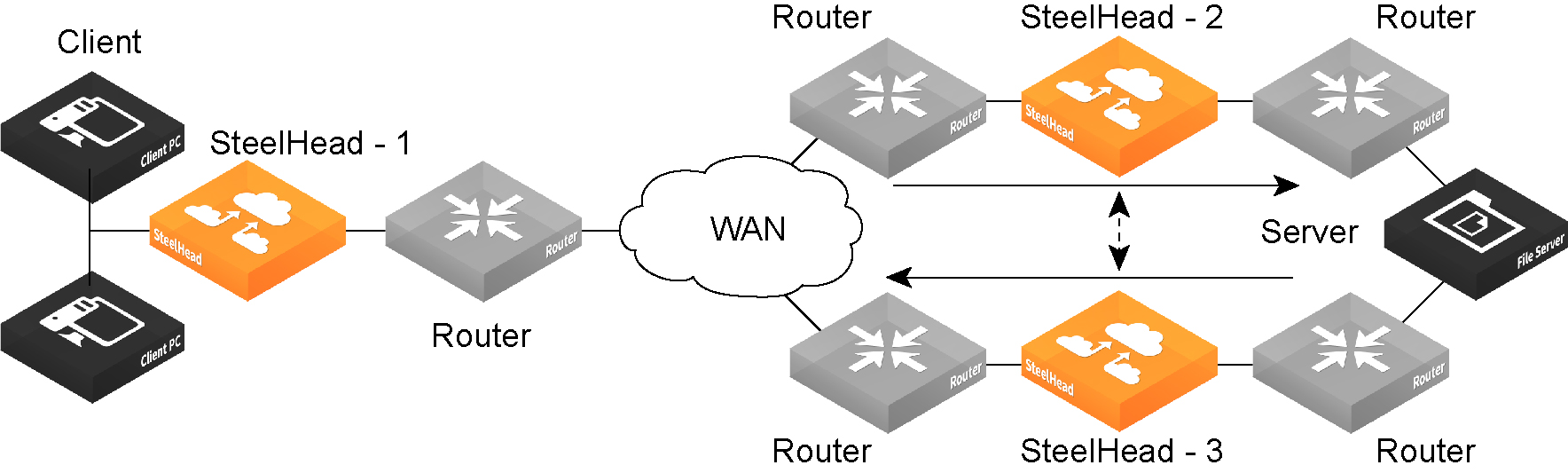
Complete Asymmetry | Packets traverse both SteelHeads going from the client to the server but bypass both SteelHeads on the return path. | •Asymmetric Routing Table: bad RST •Log: Sep 5 11:16:38 gen-sh102 kernel: [intercept.WARN] asymmetric routing between 10.11.111.19 and 10.11.25.23 detected (bad RST) |
Server-Side Asymmetry | Packets traverse both SteelHeads going from the client to the server but bypass the server-side SteelHead on the return path. | •Asymmetric Routing Table: bad SYN/ACK •Log: Sep 7 16:17:25 gen-sh102 kernel: [intercept.WARN] asymmetric routing between 10.11.25.23:5001 and 10.11.111.19:33261 detected (bad SYN/ACK) |
Client-Side Asymmetry | Packets traverse both SteelHeads going from the client to the server but bypass the client-side SteelHead on the return path. | •Asymmetric Routing Table: no SYN/ACK •Log: Sep 7 16:41:45 gen-sh102 kernel: [intercept.WARN] asymmetric routing between 10.11.111.19:33262 and 10.11.25.23:5001 detected (no SYN/ACK) |
multiSYN Retransmit | The types of multi-SYN retransmits are: •Probe-filtered occurs when the client-side SteelHead sends out multiple SYN+ frames and doesn’t get a response. •SYN-remit occurs when the client-side SteelHead receives multiple SYN retransmits from a client and doesn’t see a SYN/ACK packet from the destination server. | •Asymmetric Routing Table: probe-filtered (not-AR) •Log: Sep 13 20:59:16 gen-sh102 kernel: [intercept.WARN] it appears as though probes from 10.11.111.19 to 10.11.25.23 are being filtered. Passing through connections between these two hosts. |
Control | Description |
Enable Asymmetric Routing Detection | Detects asymmetric routes in your network. |
Enable Asymmetric Routing Pass-Through | Enables pass-through traffic if asymmetric routing is detected. If asymmetric routing is detected, the pair of IP addresses, defined by the client and server addresses of this connection, is cached on the SteelHead. Further connections between these hosts are passed through unoptimized until that particular asymmetric routing cache entry times out. Detecting and caching asymmetric routes doesn’t optimize these packets. If you want to optimize asymmetric routed packets you must make sure that the packets going to the WAN always go through a SteelHead either by using a multiport SteelHead, connection forwarding, or using external ways to redirect packets, such as WCCP or PBR. For details, see the SteelHead Deployment Guide. |
Remove Selected | Select the check box next to the name and click Remove Selected. |
Control | Description |
Enable Connection Forwarding | Enables connection forwarding by default on all neighbors added to the peer list. |
Port | Specify the port number to use as the default for the neighbor SteelHead in-path port. The default value is 7850. |
Keep-Alive Interval | Specify the number of seconds to use as the default interval for ping commands between neighbor SteelHeads. The default value is 1 second. |
Keep-Alive Count | Specify the number of tries to use as the default number of failed ping attempts before an appliance terminates a connection with a neighbor. The default value is 3. |
In-Path Neighbor Failure | Uses the neighbor appliance to optimize new connections if the appliance fails. For in-path deployments that use connection forwarding with WCCP, enabling this option ensures that if one appliance fails, the neighbor appliance continues to optimize new connections. For in-path deployments that use connection forwarding without WCCP, enabling this option ensures that a SteelHead attempts to optimize new connections that are symmetrically routed, even after all of the neighbor SteelHeads on another network path failed. New asymmetrically routed connections aren’t optimized but passed through. |
Multiple Interface Support | Enables high availability on SteelHead appliances configured with multiple in-path interfaces and using connection forwarding with another multiport SteelHead. This option makes all neighbor in-path interface IP addresses visible to each peer to ensure proper neighbor communication if the in-path0_0 interface fails. RiOS 6.5 and later require connection forwarding in a WCCP cluster. You must enable multiple interface support for a connection-forwarding neighbor to work with IPv6. |
IPv6 Connection Forwarding | Allows IPv6 addresses to be entered in the Neighbor Table area of this page, in the In-Path IP Address and Additional IP Addresses fields. Selecting this check box disallows the use of IPv4 addresses for neighbors; clearing this box disallows the use of IPv6 addresses for neighbors. |
Control | Description |
Add a New Neighbor | Displays the controls to add a new neighbor. |
Hostname | Specify a hostname. |
In-Path IP Address | Specify the in-path IP address for the neighbor SteelHead. When you define a neighbor, you must specify the appliance in-path IP address, not the primary IP address. You can use connection forwarding with IPv6 addresses if the following conditions are met: •Both SteelHeads must be running RiOS 9.6 or later. •Multiple interface support must be selected. •The IPv6 Connection Forwarding check box must be selected in the Connection Forwarding Settings area of this page. |
Port | Specify the in-path port for the neighbor SteelHead. The default port is 7850. |
Additional IP Addresses | Adds a neighbor SteelHead to the neighbor list. IPv6 addresses are allowed if this SteelHead and the neighbor SteelHeads are running RiOS 9.6 or later and the IPv6 Connection Forwarding check box is selected. |
Add | Adds a new neighbor. |
Remove Selected | Select the check box next to the name and click Remove Selected. |
Control | Description |
Enable Authentication and Encryption | Enables authentication between SteelHeads. By default, this option is disabled. |
Enable Perfect Forward Secrecy | Enables additional security by renegotiating keys at specified intervals. If one key is compromised, subsequent keys are secure because they’re not derived from previous keys. By default, this option is enabled. |
Encryption Policy | Select one of these encryption methods from the drop-down list: •DES - Encrypts data using the Data Encryption Standard algorithm. DES is the default value. •NULL - Specifies the null encryption algorithm. •None - Doesn’t apply an encryption policy. •3DES - Appears when a valid Enhanced Cryptography License Key is installed on the appliance. Encrypts data using the Triple Digital Encryption Standard with a 168-bit key length. This standard is supported for environments where AES has not been approved, but is both slower and less secure than AES. •AES - Appears when a valid Enhanced Cryptography License Key is installed on the appliance. Encrypts data using the Advanced Encryption Standard (AES) cryptographic key length of 128 bits. •AES256 - Appears when a valid Enhanced Cryptography License Key is installed. Encrypts data using the Advanced Encryption Standard (AES) cryptographic key length of 256 bits. Provides the highest security. Optionally, select an algorithm from the method 2, 3, 4, or 5 drop-down lists to create a prioritized list of encryption policies for negotiating between peers. Note: Peer SteelHeads must both have a valid Enhanced Cryptography License Key installed to use 3DES, AES, or AES256. When a SteelHead has the valid Enhanced Cryptography License Key installed and an IPSec encryption level is set to 3DES or AES, and a peer SteelHead doesn’t have a valid Enhanced Cryptography License Key installed, the appliances uses the highest encryption level set on the appliance without the key. |
Authentication Policy | Select one of these authentication methods from the drop-down list: •MD5 - Specifies the Message-Digest 5 algorithm, a widely used cryptographic hash function with a 128-bit hash value. This is the default value. •SHA-1 - Specifies the Secure Hash Algorithm, a set of related cryptographic hash functions. SHA-1 is considered to be the successor to MD5. Optionally, select an algorithm from the method 2 drop-down list to create a secondary policy for negotiating the authentication method to use between peers. If the first authentication policy negotiation fails, the peer SteelHeads use the secondary policy to negotiate authentication. |
Time Between Key Renegotiations | Specify the number of minutes between quick-mode renegotiation of keys using the Internet Key Exchange (IKE) protocol. IKE uses public key cryptography to provide the secure transmission of a secret key to a recipient so that the encrypted data can be decrypted at the other end. The default value is 240 minutes. |
Enter the Shared Secret/Confirm the Shared Secret | Specify and confirm the shared secret. All the SteelHeads in a network for which you want to use IPSec must have the same shared secret. |
Add a New Secure Peer | Displays the controls to add a new secure peer. •Peer IP Address - Specify the IP address for the peer SteelHead (in-path interface) for which you want to make a secure connection. |
Add | Adds the peer specified in the Peer IP Address text box. If a connection has not been established between the two SteelHeads that are configured to use IPSec security, the peers list doesn’t display the peer SteelHead status as mature. Note: Adding a peer causes a short service disruption (3 to 4 seconds) to the peer that is configured to use IPSec security. |
Remove Selected | Select the check box next to the name and click Remove Selected. |
Control | Description |
Add a Subnet Side Rule | Displays the controls to create a subnet side rule. |
Insert Rule At | Select Start, End, or a rule number from the drop-down list. SteelHeads evaluate rules in numerical order starting with rule 1. If the conditions set in the rule match, then the rule is applied, and the system moves on to the next packet. If the conditions set in the rule don’t match, the system consults the next rule. For example, if the conditions of rule 1 don’t match, rule 2 is consulted. If rule 2 matches the conditions, it is applied, and no further rules are consulted. |
Subnet | Specify the subnet. The subnet can be either an IPv4 or an IPv6 address. Use the following format: <ip address>/<subnet mask> xxx.xxx.xxx.xxx/xx (IPv4) x:x:x:x/xxx (IPv6) |
Subnet is on the LAN side of this appliance | In virtual in-path configurations, all traffic is flowing in and out of one physical interface. Select to specify that the subnet is on the LAN side of the device. |
Subnet is on the WAN side of this appliance | In virtual in-path configurations, all traffic is flowing in and out of one physical interface. Select to specify that the subnet is on the WAN side of the device. |
Add | Adds the rule to the subnet map table. The Management Console redisplays the subnet map table and applies your changes to the running configuration, which is stored in memory. |
Remove Subnet Rules | Select the check box next to the name and click Remove Subnet Rules. |
Move Subnet Rules | Moves the selected rules. Click the arrow next to the desired rule position; the rule moves to the new position. |
Control | Description |
Enable Application Visibility | Continuously collects detailed application-level statistics for both pass-through and optimized traffic. The Application Visibility and Application Statistics reports display these statistics. This statistic collection is disabled by default. To view the reports, choose Reports > Networking: Application Statistics or Application Visibility. Enabling application visibility also improves connection reporting on the Current Connections report. For example, HTTP-SharePoint is displayed as the WebDAV or FPSE protocols and Office 365 appears as MS-Office-365 instead of HTTP. |
Enable WAN Throughput Statistics | Continuously collects WAN throughput statistics, which the WAN Throughput report displays. This statistic collection is enabled by default; however, you can disable the collection to save processing power. To view the WAN throughput statistics, choose Reports > Networking: WAN Throughput. |
Enable Top Talkers | Continuously collects statistics for the most active traffic flows. A traffic flow consists of data sent and received from a single source IP address and port number to a single destination IP address and port number over the same protocol. The most active, heaviest users of WAN bandwidth are called the Top Talkers. A flow collector identifies the top consumers of the available WAN capacity (the top 50 by default) and displays them in the Top Talkers report. Collecting statistics on the Top Talkers provides visibility into WAN traffic without applying an in-path rule to enable a WAN visibility mode. You can analyze the Top Talkers for accounting, security, troubleshooting, and capacity planning purposes. You can also export the complete list in CSV format. The collector gathers statistics on the Top Talkers based on the proportion of WAN bandwidth consumed by the top hosts, applications, and host and application pair conversations. The statistics track pass-through or optimized traffic, or both. Data includes TCP or UDP traffic, or both (configurable in the Top Talkers report page). A NetFlow collector is not required for this feature. Optionally, select a time period to adjust the collection interval: •24-hour Report Period - For a five-minute granularity (the default setting). •48-hour Report Period - For a ten-minute granularity. The system also uses the time period to collect SNMP Top Talker statistics. For top talkers displayed in the Top Talker report and SNMP Top Talker statistics, the system updates the Top Talker data ranks either every 300 seconds (for a 24- hour reporting period), or 600 seconds (for a 48-hour reporting period). The system saves a maximum of 300 Top Talker data snapshots, and aggregates these to calculate the top talkers for the 24-hour or 48-hour reporting period. The system never clears top talker data at the time of polling; however, every 300 or 600 seconds, it replaces the oldest Top Talker data snapshot of the 300 with the new data snapshot. After you change the reporting period, it takes the system one day to update the Top Talker rankings to reflect the new reporting period. In the interim, the data used to calculate the Top Talkers still includes data snapshots from the original reporting period. This delay applies to Top Talker report queries and SNMP Top Talker statistics. |
Control | Description |
Enable Flow Export | Enables the SteelHead to export network statistics about the individual flows that it sees as they traverse the network. By default, this setting is disabled. |
Export QoS and Application Statistics to CascadeFlow Collectors | Sends application-level statistics from all sites to a SteelCentral collector on a SteelCentral appliance. SteelCentral appliances provide central reporting capabilities. The collector aggregates QoS and application statistics to provide visibility using detailed records specific to flows traversing the SteelHead. The SteelHead sends SteelCentral an enhanced version of NetFlow called CascadeFlow. CascadeFlow includes: •NetFlow v9 extensions for round-trip time measurements that enable you to understand volumes of traffic across your WAN and end-to-end response time. •extensions that enable a SteelCentral NetExpress to properly measure and report on the benefits of optimization. After the statistics are aggregated on a Cascade appliance, you can use its central reporting capabilities to: •analyze overall WAN use, such as traffic generated by application, most active sites, and so on. •troubleshoot a particular application by viewing how much bandwidth it received, checking for any retransmissions, interference from other applications, and so on. •compare actual application use against your outbound QoS policy configuration to analyze whether your policies are effective. For example, if your QoS policy determines that Citrix should get a minimum of 10 percent of the link, and the application statistics reveal that Citrix performance is unreliable and always stuck at 10 percent, you might want to increase that minimum guarantee. You must enable outbound QoS on the SteelHead, add a CascadeFlow collector, and enable REST API access before sending QoS configuration statistics to an SteelCentral NetProfiler. To enable QoS, choose Networking > Network Services: Outbound QoS. You can’t export statistics for inbound QoS. The collectors appear in the Flow Collector list at the bottom of the Configure > Networking: Flow Statistics page. To enable REST API access, choose Administration > Security: REST API Access. The CascadeFlow collector collects read-only statistics on both pass-through and optimized traffic. When you use CascadeFlow, the SteelHead sends four flow records for each optimized TCP session: ingress and egress for the inner-channel connection, and ingress and egress for the outer-channel connection. A pass-through connection still sends four flow records, even though there are no separate inner- and outer-channel connections. In either case, the SteelCentral NetExpress merges these flow records together with flow data collected for the same flow from other devices. For details, see the SteelCentral Network Performance Management Deployment Guide. |
Enable IPv6 | Enables support for IPv6 addresses for flow exports. |
Active Flow Timeout | Optionally, specify the amount of time, in seconds, the collector retains the list of active traffic flows. The default value is 1800 seconds. You can set the time-out period even if the Top Talkers option is enabled. |
Inactive Flow Timeout | Optionally, specify the amount of time, in seconds, the collector retains the list of inactive traffic flows. The default value is 15 seconds. |
Control | Description |
Add a New Flow Collector | Displays the controls to add a Flow collector. |
Collector Hostname or IP Address | Specify the IP address or (in RiOS 9.7 and later) a hostname for the Flow collector. |
Port | Specify the UDP port the Flow collector is listening on. The default value is 2055. |
Version | Select one of these versions from the drop-down list: •CascadeFlow - Use with Cascade Profiler 8.4 or later. •CascadeFlow-compatible - Use with Cascade Profiler 8.3.2 or earlier, and select the LAN Address check box. •NetFlow v9 - Enables both ingress and egress flow records. •NetFlow v5 - Enables ingress flow records. For details on using NetFlow records with Cascade, see the SteelCentral Network Performance Management Deployment Guide. CascadeFlow and CascadeFlow-compatible are enhanced versions of flow export to the SteelCentral. These versions allow automatic discovery and interface grouping for SteelHeads in a Riverbed SteelCentral NetProfiler or a SteelCentral Flow Gateway and support WAN and optimization reports in SteelCentral. For details, see the SteelCentral NetProfiler and NetExpress User Guide and the SteelCentral Flow Gateway User Guide. |
Packet Source Interface | Select the interface to use as the source IP address of the flow packets (Primary, Aux, or MIP) from the drop-down list. NetFlow records sent from the SteelHead appear to be sent from the IP address of the selected interface. |
LAN Address | Causes the TCP/IP addresses and ports reported for optimized flows to contain the original client and server IP addresses and not those of the SteelHead. The default setting displays the IP addresses of the original client and server without the IP address of the SteelHeads. This setting is unavailable with NetFlow v9, because the optimized flows are always sent out with both the original client server IP addresses and the IP addresses used by the SteelHead. |
Capture Interface/Type | Specify the traffic type to export to the flow collector. Select one of these types from the drop-down list: •All - Exports both optimized and nonoptimized traffic. •Optimized - Exports optimized traffic. •Optimized - Exports optimized LAN or WAN traffic when WCCP is enabled. •Passthrough - Exports pass-through traffic. •None - Disables traffic flow export. The default is All for LAN and WAN interfaces, for all four collectors. The default for the other interfaces (Primary, rios_lan, and rios_wan) is None. You can’t select a MIP interface. |
Enable Filter | (CascadeFlow and NetFlow v9 only) Filter flow reports by IP and subnets or IP:ports included in the Filter list. When disabled, reports include all IP addresses and subnets. |
Filter | (CascadeFlow and NetFlow v9 only) Specify the IP and subnet or IP:port to include in the report, one entry per line, up to 25 filters maximum. This field supports both IPv4 and IPv6 subnets. |
Add | Adds the collector to the Collector list. |
Remove Selected | Select the check box next to the name and click Remove Selected. |
Control | Description |
Workgroup Name | Specify a local workgroup name. If you configure in local workgroup mode, the SteelHead doesn’t need to join a domain. Local workgroup accounts are used by clients when they connect to the SteelHead. Starting with RiOS 9.5, this name is not case sensitive. |
Add a New User | Displays the controls to add a new user to the local workgroup. |
User | Specify the login to create a local workgroup account so that users can connect to the SteelHead. |
Password/Password Confirm | Specify and confirm the user account password. |
Add | Adds users to the local workgroup. |
Remove Selected | Removes the selected names. |
Protocol | Port |
SMB1, SMB2/3 | TCP 139 (legacy Windows implementations) 445 (more recent Windows implementations) |
LDAP | TCP/UDP 389 |
Kerberos | TCP/UDP 88 |
DNS | UDP 53 |
SMB1-Named-Pipes, SMB2/3-Named-Pipes | TCP 445 |
EPM/RPC | TCP 135 |
Control | Description |
Active Directory Domain Name/Realm | Specify the domain in which to make the SteelHead a member. Typically, this is your company domain name. RiOS supports Windows 2000 or later domains. RiOS doesn’t support nondomain accounts other than administrator accounts. If you create Local mode shares on a nonadministrator account, your security permissions for the share aren’t preserved on the origin-file server. |
Primary DNS IP Address | By default, this field displays the primary DNS IP set in the DNS Settings page. To modify this entry, click the IP address. |
Join Account Type | Specifies which account type the server-side SteelHead uses to join the domain controller. You can optimize the traffic to and from hosted Exchange servers. You must configure the server-side SteelHead in the Active Directory integrated mode for Windows 2003 or Windows 2008. This allows the SteelHead to use authentication on the Exchange servers that provide Microsoft Exchange online services. The domain that the server-side SteelHead joins must be either the same as the client user or any domain that trusts the domain of the client user. Be aware that when you integrate the server-side SteelHead in the Active Directory, it doesn’t provide any Windows domain controller functionality to any other machines in the domain and doesn’t advertise itself as a domain controller or register any SRV records (service records). In addition, the SteelHead doesn’t perform any replication nor hold any Active Directory objects. The server-side SteelHead has just enough privileges so that it can have a legitimate conversation with the domain controller and then use transparent mode for NTLM authentication. The Active Directory integration provides a way to optimize NTLM authentication from Windows 7/2008 R2 and newer clients when using transparent mode. This scenario is only successful for servers and clients that can make use of NTLM authentication. The server-side SteelHead joins a domain with DC privileges and then uses NTLM pass-through authentication to perform the authentication. Using transparent mode simplifies the configuration. Select one of these options from the drop‑down list: •Active Directory integrated (Windows 2008 and later) - Configures the server-side SteelHead to integrate with the Active Directory domain. This option supports Windows 2008 DCs and higher, supports authentication across domains, and is the default setting for RiOS 9.6 and later. If the network contains any domain controllers running Windows 2003 or older operating system versions, you must explicitly specify a list of Windows 2008 DCs in the Domain Controller Names field; see the instructions under “Domain Controller Name(s)” in this table for details. •Workstation - Joins the server-side SteelHead to the domain with workstation privilege. You can join the domain to this account type using any ordinary user account that has the permission to join a machine to the domain. This is the default setting for RiOS releases earlier than 9.6. •Active Directory integrated (Windows 2003) - Configures the server-side SteelHead to integrate with the Active Directory domain. If the account for the server-side SteelHead was not already present, it’s created in organizational unit (OU) domain controllers. If the account existed previously as a domain computer then its location doesn’t change. You can move the account to a different OU later. When you select Active Directory integrated (Windows 2003), you must specify one or more domain controller name(s), separated by commas. You must have Administrator privileges to join the domain with active directory integration. Active Directory integration doesn’t support cross-domain authentication where the user is from a domain trusted by the domain to which the server-side SteelHead is joined. |
You must have Administrator privileges. Additionally, if the user account is in a domain that is different from the domain to which the join is being performed, specify the user account in the format domain\username. Do not specify the user account in the format username@realmname. In this case, domain is the short domain name of the domain to which the user belongs. Even though the SteelHead is integrated with Active Directory, it doesn’t provide any Windows domain controller functionality to any other machines in the domain. | |
Domain Login | Specify the login name, which must have domain join privileges. Domain administrator credentials aren’t strictly required, except when you join the domain as an Active Directory integration. RiOS deletes domain administrator credentials after the join. |
Password | Specify the password. This control is case sensitive. |
Domain Controller Name(s) | Specify the hosts that provide user login service in the domain, separated by commas. (Typically, with Windows 2000 Active Directory Service domains, given a domain name, the system automatically retrieves the DC name.) Specifying domain controller names is required if you are joining the domain in Active Directory integrated mode 2008 and higher, and the network contains domain controllers running Windows 2003 or older operating system versions. We recommend specifying the domain controller names in environments where there’s varying latency between the SteelHead and the domain controllers. |
Short Domain Name | Specify the short domain (NetBIOS) name if it doesn’t match the first portion of the Active Directory domain name. Case matters; NBTTECH is not the same as nbttech. |
Join/Leave | Joins the domain or leaves the domain. Note: If you are in domain mode and have joined a domain, you can’t change to local workgroup mode until you leave the domain. |
Rejoin | Rejoins the domain. |
Cancel | Cancels any current domain action that is in progress, such as joining or leaving a domain. |
Control | Description |
Collect Mappings From | Select one of these options from the drop‑down list: •None - Does not collect mappings. •Destination Only - Collects mappings from destination IP, destination MAC, and VLAN tag (when deployed on 802.1q trunk). We recommend that you use this setting for most deployments with multiple in-paths or connection forwarding SteelHeads. SteelHeads do not usually learn incorrect mappings unless the network devices themselves are routing incorrectly. This is the default setting. •Destination and Source - Collects mappings from destination and source IP, destination and source MAC, and VLAN tag (when deployed on 802.1q trunk). •All - Collects mappings for destination, source, and inner MAC data. Also collect data for connections that are un-NATted (that is, connections that aren’t translated using NAT). |
Enable simplified routing for GRE-tunneled pass-through packets | Enables simplified routing for GRE tunnel pass-through traffic. Enabling this setting avoids packet ricochet between the server-side SteelHead and the server-side SteelHead gateway for pass-through packets from GRE tunnels. This setting applies to TCP and UDP packets. |
Control | Description |
Enable WCCP v2 Support | Enables WCCPv2 support on all groups added to the Service Group list. |
Multicast TTL | Specify the TTL boundary for the WCCP protocol packets. The default value is 16. |
Control | Description |
Add a New Service Group | Displays the controls for adding a new service group. |
Interface | Select a SteelHead interface to participate in a WCCP service group. In virtual in-path configurations, all traffic flows in and out of one physical interface, and the default subnet side rule causes all traffic to appear to originate from the WAN side of the device. RiOS allows multiple SteelHead interfaces to participate in WCCP on one or more routers for redundancy (RiOS 6.0 and earlier allows a single SteelHead interface). If one of the links goes down, the router can still send traffic to the other active links for optimization. You must include an interface with the service group ID. More than one SteelHead in-path interface can participate in the same service group. For WCCP configuration examples, see the SteelHead Deployment Guide. If multiple SteelHeads are used in the topology, they must be configured as neighbors. RiOS 6.5 and later require connection forwarding in a WCCP cluster. |
Service Group ID | Enables WCCPv2 support on all groups added to the Service Group list. Specify a number from 0 to 255 to identify the service group on the router. A value of 0 specifies the standard HTTP service group. We recommend that you use WCCP service groups 61 and 62. Note: The service group ID is local to the site where WCCP is used. Note: The service group number is not sent across the WAN. |
Protocol | Select a traffic protocol from the drop-down list: TCP, UDP, or ICMP. The default value is TCP. |
Password/Password Confirm | Optionally, assign a password to the SteelHead interface. This password must be the same password that is on the router. WCCP requires that all routers in a service group have the same password. Passwords are limited to eight characters. |
Priority | Specify the WCCP priority for traffic redirection. If a connection matches multiple service groups on a router, the router chooses the service group with the highest priority. The range is 0 to 255. The default value is 200. The priority value must be consistent across all SteelHeads within a particular service group. |
Weight | Specify the percentage of connections that are redirected to a particular SteelHead interface, which is useful for traffic load balancing and failover support. The number of TCP, UDP, or ICMP connections a SteelHead supports determines its weight. The more connections a SteelHead model supports, the heavier the weight of that model. In RiOS 6.1 and later, you can modify the weight for each in-path interface to manually tune the proportion of traffic a SteelHead interface receives. A higher weight redirects more traffic to that SteelHead interface. The ratio of traffic redirected to a SteelHead interface is equal to its weight divided by the sum of the weights of all the SteelHead interfaces in the same service group. For example, if there are two SteelHeads in a service group and one has a weight of 100 and the other has a weight of 200, the one with the weight 100 receives 1/3 of the traffic and the other receives 2/3 of the traffic. However, since it’s generally undesirable for a SteelHead with two WCCP in-path interfaces to receive twice the proportion of traffic, for SteelHeads with multiple in-paths connected, each of the in-path weights is divided by the number of that SteelHead's interfaces participating in the service group. As an example, if there are two SteelHeads in a service group and one has a single interface with weight 100 and the other has two interfaces each with weight 200, the total weight will still equal 300 (100 + 200/2 + 200/2). The one with the weight 100 receives 1/3 of the traffic and each of the other's in-path interfaces receives 1/3 of the traffic. The range is 0 to 65535. The default value corresponds to the number of TCP connections your SteelHead supports. Failover Support To enable single in-path failover support with WCCP groups, define the service group weight to be 0 on the backup SteelHead. If one SteelHead has a weight 0, but another one has a nonzero weight, the SteelHead with weight 0 doesn’t receive any redirected traffic. If all the SteelHeads have a weight 0, the traffic is redirected equally among them. The best way to achieve multiple in-path failover support with WCCP groups is to use the same weight on all interfaces from a given SteelHead for a given service group. For example, suppose you have SteelHead A and SteelHead B with two in-path interfaces each. When you configure SteelHead A with weight 100 from both inpath0_0 and inpath0_1 and SteelHead B with weight 200 from both inpath0_0 and inpath0_1, RiOS distributes traffic to SteelHead A and SteelHead B in the ratio of 1:2 as long as at least one interface is up on both SteelHeads. In a service group, if an interface with a nonzero weight fails, its weight transfers over to the weight 0 interface of the same service group. For details on using the weight parameter to balance traffic loads and provide failover support in WCCP, see the SteelHead Deployment Guide. |
Encapsulation Scheme | Specifies the method for transmitting packets between a router or a switch and a SteelHead interface. Select one of these encapsulation schemes from the drop-down list: •Either - Use Layer 2 first; if Layer 2 is not supported, GRE is used. This is the default value. •GRE - Generic Routing Encapsulation. The GRE encapsulation method appends a GRE header to a packet before it’s forwarded. This method can cause fragmentation and imposes a performance penalty on the router and switch, especially during the GRE packet deencapsulation process. This performance penalty can be too great for production deployments. •L2 - Layer-2 redirection. The L2 method is generally preferred from a performance standpoint because it requires fewer resources from the router or switch than the GRE does. The L2 method modifies only the destination Ethernet address. However, not all combinations of Cisco hardware and IOS revisions support the L2 method. Also, the L2 method requires the absence of L3 hops between the router or switch and the SteelHead. |
Assignment Scheme | Determines which SteelHead interface in a WCCP service group the router or switch selects to redirect traffic to for each connection. The assignment scheme also determines whether the SteelHead interface or the router processes the first traffic packet. The optimal assignment scheme achieves both load balancing and failover support. Select one of these schemes from the drop-down list: •Either - Uses Hash assignment unless the router doesn’t support it. When the router doesn’t support Hash, it uses Mask. This is the default setting. •Hash - Redirects traffic based on a hashing scheme and the Weight of the SteelHead interface, providing load balancing and failover support. This scheme uses the CPU to process the first packet of each connection, resulting in slightly lower performance. However, this method generally achieves better load distribution. We recommend Hash assignment for most SteelHeads if the router supports it. The Cisco switches that don’t support Hash assignment are the 3750, 4000, and 4500 series, among others. Your hashing scheme can be a combination of the source IP address, destination IP address, source port, or destination port. •Mask - Redirects traffic operations to the SteelHeads, significantly reducing the load on the redirecting router. Mask assignment processes the first packet in the router hardware, using less CPU cycles and resulting in better performance. Mask assignment supports load-balancing across multiple active SteelHead interfaces in the same service group. The default mask scheme uses an IP address mask of 0x1741, which is applicable in most situations. However, you can change the IP mask by clicking the service group ID and changing the service group settings and flags. In multiple SteelHead environments, it’s often desirable to send all users in a subnet range to the same SteelHead. Using mask provides a basic ability to leverage a branch subnet and SteelHead to the same SteelHead in a WCCP cluster. For details and best practices for using assignment schemes, see the SteelHead Deployment Guide. Note: If you use mask assignment you must ensure that packets on every connection and in both directions (client-to-server and server-to-client), are redirected to the same SteelHead. For details, see the SteelHead Deployment Guide. |
Source | •IP Mask - Specify the service group source IP mask. The default value is 0x1741. •Port Mask - Specify the service group source port mask. •IP Hash - Specify that the router hash the source IP address to determine traffic to redirect. •Port Hash - Specify that the router hash the source port to determine traffic to redirect. |
Destination | •IP Mask - Specify the service group destination IP mask. •Port Mask - Specify the service group destination port mask. •IP Hash - Specify that the router hash the destination IP address to determine traffic to redirect. •Port Hash - Specify that the router hash the destination port to determine traffic to redirect. |
Ports Mode | Select one of these modes from the drop-down list: •Ports Disabled - Select to disable the ports. •Use Source Ports - The router determines traffic to redirect based on source ports. •Use Destination Ports - The router determines traffic to redirect based on destination ports. |
Ports | Specify a comma-separated list of up to seven ports that the router will redirect. Use this option only after selecting either the Use Source Ports or the Use Destination Ports mode. |
Router IP Address(es) | Specify a multicast group IP address or a unicast router IP address. You can specify up to 32 routers. |
Add | Adds the service group. |
Remove Selected Groups | Select the check box next to the name and click Remove Selected Groups. |
Control | Description |
Add a New Rule | Displays the controls for adding a new rule. |
Type | Select a rule type: •Accept - Accepts rules matching the Subnet A or Subnet B IP address and mask pattern for the optimized connection. •Pass-Through - Identifies traffic to be passed through the network unoptimized. |
Insert Rule At | Determines the order in which the system evaluates the rule. Select Start, End, or a rule number from the drop-down list. The system evaluates rules in numerical order starting with rule 1. If the conditions set in the rule match, then the rule is applied and the system moves on to the next rule: for example, if the conditions of rule 1 don’t match, rule 2 is consulted. If rule 2 matches the conditions, it is applied, and no further rules are consulted. In general, filter traffic that is to be unoptimized, discarded, or denied before processing rules for traffic that is to be optimized. |
Subnet A | Specify an IP address and mask for the subnet that can be both source and destination together with Subnet B. Use this format: xxx.xxx.xxx.xxx/xx Note: You can specify all or 0.0.0.0/0 as the wildcard for all traffic. |
Subnet B | Specify an IP address and mask for the subnet that can be both source and destination together with Subnet A. Use this format: xxx.xxx.xxx.xxx/xx Note: You can specify all or 0.0.0.0/0 as the wildcard for all traffic. |
VLAN Tag ID | Optionally, specify a numeric VLAN tag identification number. Select all to specify the rule applies to all VLANs. Select untagged to specify the rule applies to nontagged connections. Note: Pass-through traffic maintains any preexisting VLAN tagging between the LAN and WAN interfaces. Note: To complete the implementation of VLAN tagging, you must set the VLAN tag IDs for the in-path interfaces that the SteelHead uses to communicate with other SteelHeads. For details about configuring the in-path interface for the SteelHead, see Configuring in-path rules. |
Description | Optionally, include a description of the rule. |
Add | Adds the new hardware-assist rule to the list. You can add up to a maximum number of 50 rules. •RiOS applies the same rule to both LAN and WAN interfaces. •Every 10G card has the same rule set. The SteelHead refreshes the hardware-assist rules table and applies your modifications to the running configuration, which is stored in memory. |
Remove Selected Rules | Select the check box next to the name and click Remove Selected Rules. |
Move Selected Rules | Moves the selected rules. Click the arrow next to the desired rule position; the rule moves to the new position. |