Peering Rules page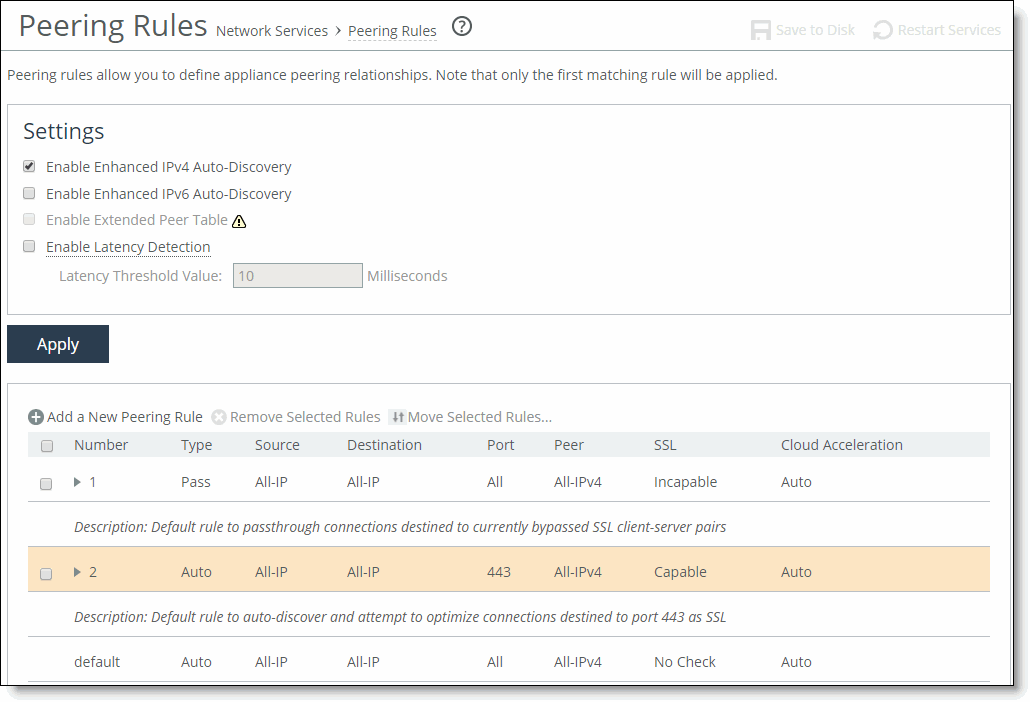

Deployment type | Description |
Serial Cascade Deployments | Cascade configurations enable optimal multisite deployments where connections between the client and the server might pass through intermediate SteelHeads to reach their final destination. Enhanced autodiscovery for cascading SteelHeads detects when more than two SteelHeads are present between the client and the server and automatically chooses the two outside SteelHeads, optimizing all traffic in between. |
Serial Cluster Deployments | You can provide increased optimization by deploying two or more SteelHeads back-to-back in an in-path configuration to create a serial cluster. Appliances in a serial cluster process the peering rules you specify in a spill-over fashion. When the maximum number of TCP connections for a SteelHead is reached, that appliance stops intercepting new connections. This behavior allows the next SteelHead in the cluster the opportunity to intercept the new connection, if it has not reached its maximum number of connections. The in-path peering rules and in-path rules tell the SteelHead in a cluster not to intercept connections between themselves. You configure peering rules that define what to do when a SteelHead receives an autodiscovery probe from another SteelHead. You can deploy serial clusters on the client-side or server-side of the network. Supported models Two-appliance serial clusters are supported for all SteelHead and xx55 models, except the 255 models. The SteelHeads must be the same model. The CX 570 through GX 10000SteelHead models support serial clusters. These models can reach their specifications even while potentially passing through the LAN-side traffic for optimized connections for the other SteelHead in the cluster. For environments that want to optimize MAPI or FTP traffic which require all connections from a client to be optimized by one SteelHead, we strongly recommend using the master and backup redundancy configuration instead of a serial cluster. For larger environments that require multiappliance scalability and high availability, we recommend using the Interceptor to build multiappliance clusters. For details, see the SteelHead Interceptor Deployment Guide and the SteelHead Interceptor User Guide. A serial cluster has the same bandwidth specification as the SteelHead model deployed in the cluster. The bandwidth capability doesn’t increase because the cluster contains multiple SteelHeads. For example, a serial cluster that is made up of two SteelHead 570-M models with a bandwidth specification of 20 Mbps has a bandwidth specification of 20 Mbps If the active SteelHead in the cluster enters a degraded state because the CPU load is too high, it continues to accept new connections. |

Control | Description |
Enable Enhanced IPv4 Auto-Discovery | Enables enhanced autodiscovery for IPv4 and mixed (dual-stack) IPv4 and IPv6 networks. With enhanced autodiscovery, the SteelHead automatically finds the furthest SteelHead along the connection path of the TCP connection, and optimization occurs there: for example, in a deployment with four SteelHeads (A, B, C, D), where D represents the appliance that is furthest from A, the SteelHead automatically finds D. This feature simplifies configuration and makes your deployment more scalable. By default, enhanced autodiscovery peering is enabled. Without enhanced autodiscovery, the SteelHead uses regular autodiscovery. With regular auto-discovery, the SteelHead finds the first remote SteelHead along the connection path of the TCP connection, and optimization occurs there: for example, if you had a deployment with four SteelHeads (A, B, C, D), where D represents the appliance that is furthest from A, the SteelHead automatically finds B, then C, and finally D, and optimization takes place in each. This option uses an IPv4 channel to the peer SteelHead over a TCP connection, and your network connection must support IPv4 for the inner channels between the SteelHead and the Client Accelerator Controller. If you have an all-IPv6 (single-stack IPv6) network, select the Enable Enhanced IPv6 Auto-Discovery option. For detailed information about deployments that require enhanced autodiscovery peering, see the SteelHead Deployment Guide. |
Enable Enhanced IPv6 Auto-Discovery | Enables enhanced autodiscovery for single-stack IPv6 networks. |
Enable Extended Peer Table | Enables support for up to 20,000 peers on high-end server-side SteelHeads to accommodate large SteelHead client deployments. The RiOS data store maintains the peers in groups of 1,024 in the global peer table. We recommend enabling the extended peer table if you have more than 4,000 peers. By default, this option is disabled and it’s unavailable on SteelHead models that don’t support it. Before enabling this feature, you must have a thorough understanding of performance and scaling issues. When deciding whether to use extended peer table support, you should compare it with a serial cluster deployment. For details on serial clusters, see the SteelHead Deployment Guide. After enabling this option, you must clear the RiOS data store and stop and restart the service. |
Enable Latency Detection | Enables peer appliances to pass through traffic without optimizing it when the latency between the peers is below the configured threshold. The latency threshold is in milliseconds and the default is 10 ms. The client-side SteelHead calculates the latency. When latency between peers is low enough, simply passing through unoptimized traffic can be faster than transmitting optimized traffic. When enabled, you can specify the Ignore Latency Detection flag in peer in-path rules, as needed. |
Control | Description |
Add a New Peering Rule | Displays the controls for adding a new peering rule. |
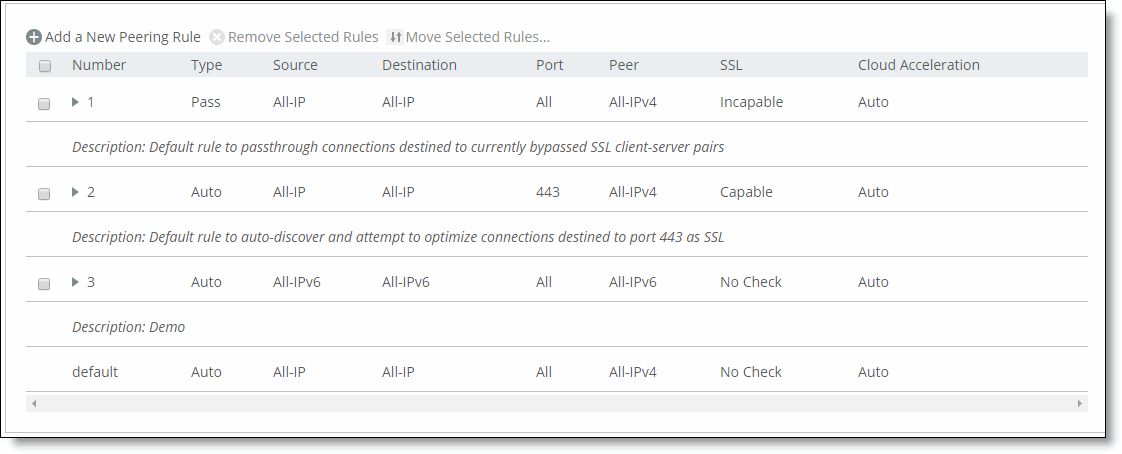
Rule Type | Determines which action the SteelHead takes on the connection. Select one of these rule types from the drop-down list: • Auto—Allows built-in functionality to determine the response for peering requests (performs the best peering possible). If the receiving SteelHead is not using automatic autodiscovery, this has the same effect as the Accept peering rule action. If automatic autodiscovery is enabled, the SteelHead only becomes the optimization peer if it’s the last SteelHead in the path to the server. • Accept—Accepts peering requests that match the source-destination-port pattern. The receiving SteelHead responds to the probing SteelHead and becomes the remote-side SteelHead (that is, the peer SteelHead) for the optimized connection. • Passthrough—Allows pass-through peering requests that match the source and destination port pattern. The receiving SteelHead doesn’t respond to the probing SteelHead, and allows the SYN+probe packet to continue through the network. |
Insert Rule At | Determines the order in which the system evaluates the rule. Select Start, End, or a rule number from the drop-down list. The system evaluates rules in numerical order starting with rule 1. If the conditions set in the rule match, then the rule is applied and the system moves on to the next rule: for example, if the conditions of rule 1 don’t match, rule 2 is consulted. If rule 2 matches the conditions, it’s applied, and no further rules are consulted. The Rule Type of a matching rule determines which action the SteelHead takes on the connection. |
Source Subnet | Specify an IP address and mask for the traffic source. You can also specify wildcards: • All-IPv4 is the wildcard for single-stack IPv4 networks. • All-IPv6 is the wildcard for single-stack IPv6 networks. • All-IP is the wildcard for all IPv4 and IPv6 networks. Use these formats: xxx.xxx.xxx.xxx/xx (IPv4) x:x:x::x/xxx (IPv6) |
Destination Subnet | Specify an IP address and mask pattern for the traffic destination. You can also specify wildcards: • All-IPv4 is the wildcard for single-stack IPv4 networks. • All-IPv6 is the wildcard for single-stack IPv6 networks. • All-IP is the wildcard for all IPv4 and IPv6 networks. Use these formats: xxx.xxx.xxx.xxx/xx (IPv4) x:x:x::x/xxx (IPv6) Port—Specify the destination port number, port label, or all. |
Peer IP Address | Specify the in-path IP address of the probing SteelHead. If more than one in-path interface is present on the probing SteelHead, apply multiple peering rules, one for each in-path interface. You can also specify wildcards: • All-IPv4 is the wildcard for single-stack IPv4 networks. • All-IPv6 is the wildcard for single-stack IPv6 networks. • All-IP is the wildcard for all IPv4 and IPv6 networks. |
SSL Capability | Enables an SSL capability flag, which specifies criteria for matching an incoming connection with one of the rules in the peering rules table. This flag is typically set on a server-side SteelHead. Select one of these options from the drop-down list to determine how to process attempts to create secure SSL connections: • No Check—The peering rule doesn’t determine whether the server SteelHead is present for the particular destination IP address and port combination. • Capable—The peering rule determines that the connection is SSL-capable if the destination port is 443 (irrespective of the destination port value on the rule), and the destination IP and port don’t appear on the bypassed servers list. The SteelHead accepts the condition and, assuming all other proper configurations and that the peering rule is the best match for the incoming connection, optimizes SSL. • Incapable—The peering rule determines that the connection is SSL-incapable if the destination IP and port appear in the bypassed servers list. The service adds a server to the bypassed servers list when there’s no SSL certificate for the server or for any other SSL handshake failure. The SteelHead passes the connection through unoptimized without affecting connection counts. We recommend that you use in-path rules to optimize SSL connections on non-443 destination port configurations. |
Cloud Acceleration | Use cloud acceleration in peering rules on a server-side SteelHead in a back-hauled deployment to configure which connections coming from a client-side SteelHead (with the SteelHead SaaS enabled but with redirect disabled) should be optimized with the SteelHead SaaS. Select one of these rule types from the drop-down list: • Auto—The server-side SteelHead redirects to the cloud connections when the client-side SteelHead tries to optimize with the SteelHead SaaS. • Pass Through—The server-side SteelHead doesn’t redirect to the cloud connections when the client-side SteelHead tries to optimize with the SteelHead SaaS. If the client-side SteelHead doesn’t have the SteelHead SaaS enabled, or if it’s not trying to optimize the SteelHead SaaS connection, the value of this field is irrelevant on the server-side SteelHead. |
Description | Specify a description to help you identify the peering relationship. |
Add | Adds a peering rule to the list. The Management Console redisplays the Peering Rules table and applies your modifications to the running configuration, which is stored in memory. |
Remove Selected Rules | Select the check box next to the name and click Remove Selected Rules. |
Move Selected Rules | Select the check box next to the rule and click Move Selected Rules. Click the arrow next to the desired rule position; the rule moves to the new position. |