Managing Secure Transport
You configure secure transport in the Secure Transport page. This section includes these topics:
Overview of Secure Transport
Secure transport enables group encryption for path selection deployments. Secure transport allows you to protect data transmitted between SteelHead over private, public, and hybrid network links with standards-based encryption for added security and regulatory compliance. Secure transport uses security based on AES-256 and SHA-2 to secure traffic over a path.
With broader adoption of public WAN services to supplant private resources, hybrid networks are becoming more common as they combine the strengths of the highly reliable MPLS with the lower-cost Internet infrastructure. A hybrid network, when controlled by path selection, combine the private WAN and public Internet to increase available bandwidth, application performance, and network reliability at the lowest cost possible. Secure transport data protection and path selection allow organizations to have the benefits of a hybrid network without the underlying complexity.
Direct-to-net public access requires a higher degree of security at the branch than a private WAN. Unlike traffic sent across a private WAN to access data center resources, public Internet transport requires all traffic to be encrypted and protected. Encryption of data over private WAN connections is also beneficial for ensuring that traffic is secure end-to-end (that is, protected as it traverses the last mile over various service provider networks). While managed service providers can offer secure VPN services, the cost of service and trust concerns make customer managed solutions preferred. With secure transport you can retain control over confidentiality of data.
Consider these guidelines when you configure secure transport:
• Secure transport requires an SSL license. Due to export control of encryption, each SteelHead is required to have an SSL license before in can join the secure transport group. For detailed information about verifying SteelHead licenses, see the SteelHead Management Console User’s Guide. If you do not have a valid enhanced cryptography license key file, go to https://sslcert.riverbed.com and follow the procedures documented there.
• You must configure networks and sites before you begin configuring secure transport. When you define networks, you specify which networks are secure. For details, see
Defining Networks.
• You must configure application policies before you begin configuring secure transport. For details, see
Defining Applications.
• Traffic is double encrypted only when both secure transport and SSL secure peering are enabled.
• Only physical in-path deployments are supported; virtual in-path deployments are not supported.
• In RiOS 9.0 or later, IPSec secure peering and the secure transport service are mutually exclusive.
• The secure transport service is enabled by default on SteelHeads. Before you enable IPSec secure peering on the SteelHead, you must disable the secure transport service on the SteelHead.
• Flow statistic collectors, such as NetFlow, cannot collect Encapsulating Security Payload (ESP) packet data flow information.
• SteelHeads must be present on both endpoints of the path.
Common Network Deployment Models for Secure Transport
Secure transport is designed to provide security to any uplink: for example, internet facing links. This is achieved through leveraging path selection. Path selection provides you with the ability to control the paths on which their applications flow. Secure transport defines encryption as an attribute to the path defined in path selection. By doing so, any application that chooses a secure path is encrypted. Secure transport provides encryption services to both WAN optimized traffic and all other traffic matched by the path selection services policy.
Figure: Secured Transport
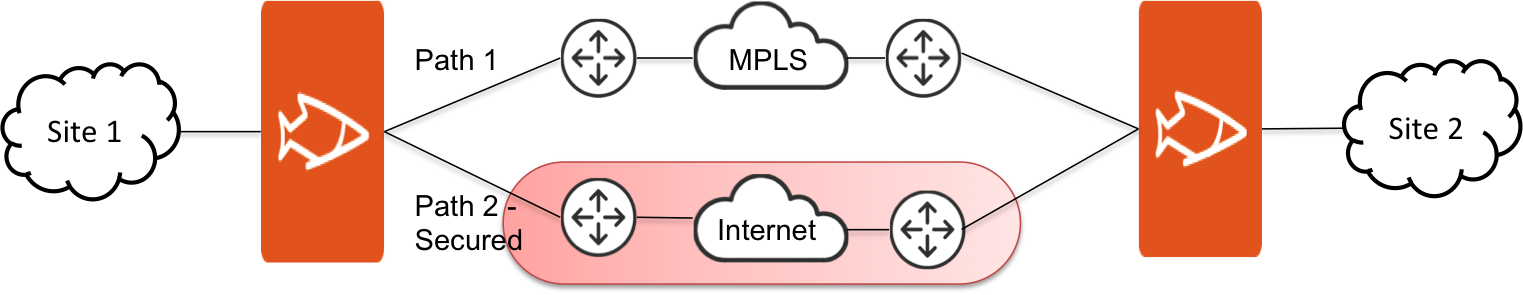
With secure transport, the most common network deployment models are:
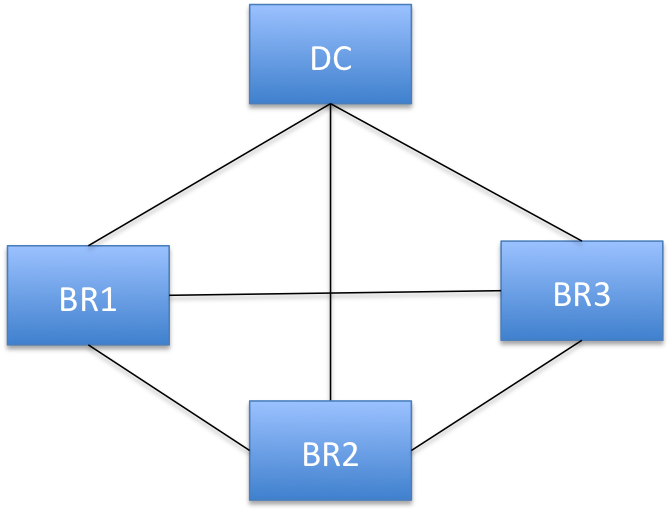
• Full mesh - The mesh model is one in which branches are connected with many redundant interconnecting circuits between them. In a mesh model if any circuit or node fails, there are many other ways for two branches to communicate. In a full mesh model every branch has a circuit connecting it to every other branch in a network. A mesh connected network is preferred by latency sensitive peer to peer applications, such as UCC (unified communication and collaboration). Peer-to-peer as well as peer-to-branch communication models are fully supported by secure transport. Each peer is allowed to securely exchange traffic with any other peer without having to go through the data center peer (hub).
Figure: Full Mesh
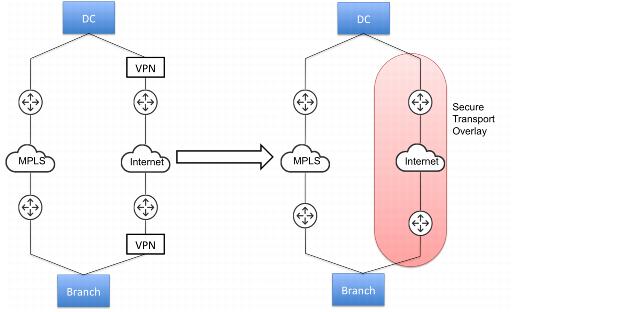
• Hybrid-Backhaul-Existing - Here you already have two circuits between the data center and the branch. A third-party dedicated MPLS link with no security enabled on it, and other is an Internet link. There is probably an third party VPN device after the SteelHead on the Internet path to provide reachability and security on that link. Now, you can remove this VPN device and enable secure transport on internet paths defined in path selection. This way the SteelHead can select the path based on policies for application and apply security to the traffic traversing the internet link.
Figure: Hybrid-Backhaul-Existing
Typical Workflow for Configuring Secure Transport
These steps represent a typical workflow for configuring secure transport.
1. Due to export control of encryption, each SteelHead is required to have an SSL license before in can join the secure transport group. For detailed information about verifying SteelHead licenses, see the SteelHead Management Console User’s Guide. If you do not have a valid enhanced cryptography license key file, go to https://sslcert.riverbed.com and follow the procedures documented there.
2. Define sites, networks, and uplinks. Make sure you specify which networks are securable using secure transport. For details, see
Managing Path Selection.
3. Define application policies. Based on your defined application policies, the SCC enables you to prioritize, secure, and deliver critical applications over the faster networks. For details, see
Defining Applications.
6. Add appliances to the secure transport group. All appliances that have a securable uplink are added automatically to a secure transport group. For details, see
Managing Path Selection.
Configuring the Secure Transport Controller on the SteelHead
A secure transport controller is a centralized service deployed on a reachable SteelHead. The SteelHead typically resides in the data center and manages the control channel and operations required for secure transport between SteelHead peers. The control channel between the SteelHeads uses SSL to secure the connection between the peer SteelHead and the SteelHead secure transport controller.
The secure transport controller controls and manages secure transport key generation, distribution of local site subnets and rekeying between secure transport peers, and uses a centralized portal for configuring and reporting.
The secure transport controller must be reachable by other SteelHead peers. You must enable secure transport client on all the SteelHead peers in which you want secure transport to encrypt data. On the SCC, all appliances that have a securable uplink are added to a secure transport group.
You can have only one active secure transport controller in your deployment. You can view secure transport properties for a SteelHead configured as a secure transport peer in the Secure Transports report on the SteelHead. For detailed information about the Secure Transports report, see the SteelHead Management Console User’s Guide for SteelHead CX.
Disconnected Mode
When connectivity is lost between the secure transport controller and its peers, the peers go into disconnected mode. The last known keys and subnet information are used during the Disconnected mode Timeout period.
An alarm is raised on the SteelHead peer when it enters disconnected mode. For detailed information about the secure transport alarm on SteelHeads, see the Alarm Status report on the SteelHead in the SteelHead Management Console User’s Guide for SteelHead CX. Possible causes for a disconnected mode timeout are:
• Connection with Controller Lost - Indicates that the peer SteelHead is no longer connected to the SteelHead secure transport controller for one of these reasons:
– The connectivity between the peer SteelHead and the SteelHead secure transport controller is lost.
– The SSL for the connection is not configured correctly.
• Registration with Controller Unsuccessful - Indicates that the peer SteelHead is not registered with the SteelHead secure transport controller, and the controller does not recognize it as a member of the secure transport group.
After a disconnected mode timeout (which can be configured through the SCC), all secure transport tunnels are brought down.
To configure the secure transport controller on the SteelHead
1. Log in to the CLI on the SteelHead that you want to configure as the secure transport controller. For detailed information about connecting to the CLI, see the Riverbed Command-Line Interface Reference Manual.
2. Enter configuration mode and run these CLI commands:
sh2 (config) # stp-controller address private-ip <private-ip-address> public-ip <public-ip-address> port <port-number>
sh2 (config) # stp-controller enable
sh2 (config) # show stp-controller status
Secure Transport Controller status: Enabled
sh2 (config) # show stp-controller address
Controller Properties:
Private address: 10.0.0.1
Public address: 10.0.0.2
private-ip <private-ip-address> | Specifies an IP address that is bound to the management interface of the SteelHead that you have chosen to be the secure transport controller. The secure transport controller IP address can be bound to an in-path address if management over the in-path interface is enabled (that is, the SteelHead is managed via the in-path address). |
public-ip <public-ip-address> port <port-number> | Optionally, specifies a publicly reachable IP address and port that is NATted to the management interface on the SteelHead running the secure transport controller. |
Activating the Secure Transport Controller on the SCC
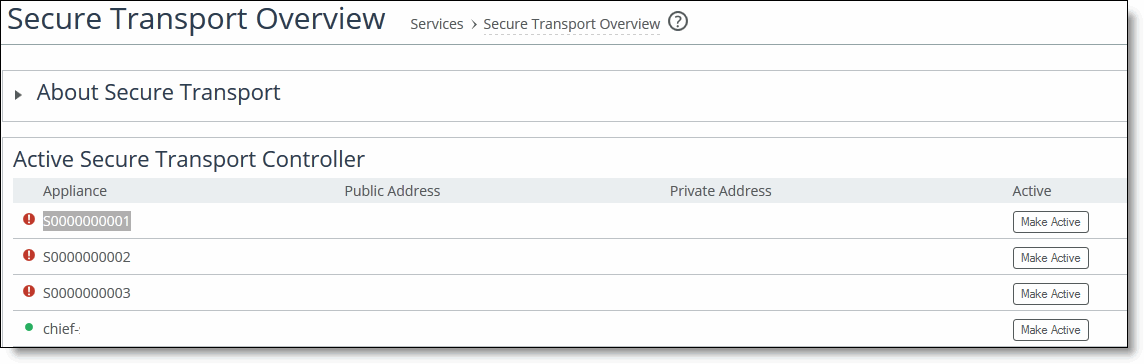
You activate the secure transport controller on the SCC in the Secure Transport page.
To activate the secure transport controller on the SCC
2. Choose > Manage > Services: Secure Transport to display the Secure Transport page.
3. Under Active Secure Transport Controller, select the name of the secure transport controller you want to activate and click Make Active.
Figure: Activating a Secure Transport Controller
Adding Appliances to the Secure Transport Group
The secure transport group is a set of SteelHeads that share the same cryptographic keys and have connectivity to each other. Any member of the secure transport group can create a secure path to any other member of the same group instantaneously, without delay. The traffic does not incur any added latency waiting for the secure paths to establish, as is common with traditional IPSec VPNs.
All appliances that have a securable uplink are automatically added to a secure transport group.
To ensure your network is secure for use with secure transport:
• Select
Securable using Secure Transport when you add networks to your topology. For details, see
Defining Networks. If the network represents the Internet, select
Public Network; public networks are UDP encapsulated.
• If the secure network is newly created, then all appliances belonging to the sites that use the securable uplink going forward will be added to the secure transport group. If the network already exists, you can edit it to make it secure, then all appliances belonging to existing sites using that uplink will be added to the secure transport group.
• Associating a secure uplink to the site makes all appliances of that site a part of secure transport mesh.
• All uplinks and thereby all paths derived from a secure network are handled by secure transport.
• The path selection rules table can be configured on application basis to be transported over secure uplinks. For details, see
Configuring Path Selection Rules.
To ensure that appliances are part of the secure transport group
1. Choose Manage > Topology: Sites & Networks to display the Sites & Networks page.
2. Click + Add a Network to display the New Network pop-up window.
Figure: Adding a Network
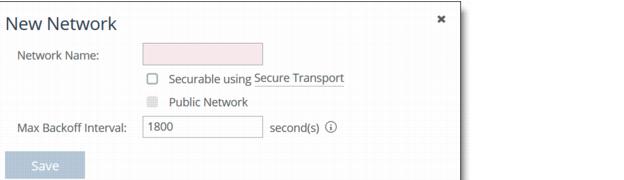
3. Specify a network name: for example doctest, select Securable using Secure Transport to ensure that the network is part of the secure transport group, and click Save.
4. Under Sites, select the site you want to associate with the secure network and click Edit Site to display the Edit a Site pop-up window. To associate a new site click + Add a Site to display the Edit a Site pop-up window and specify the site name, type, and region.
5. Under Uplinks, click
+ Add a New Uplink and select the secured network from the Network drop-down list. Define the remaining parameters for the uplink. For details, see
Defining Uplinks.
Figure: Associating the Secure Network to an Uplink
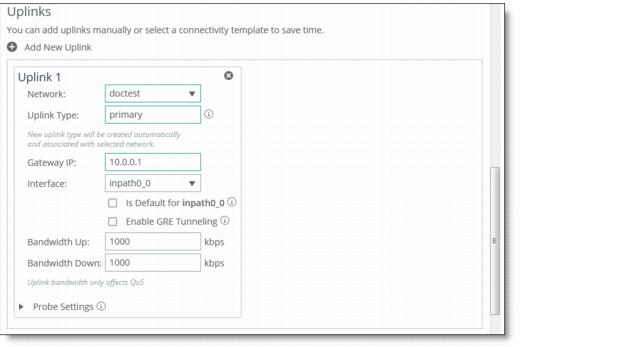
6. Click Save to save your settings.
Configuring Secure Transport Group Settings
All appliances that require a secure uplink are added to a secure transport group automatically. You can secure traffic flowing between any two appliances in the group by directing it to a secured uplink using path selection service rules. All appliances that have a secure uplink are added to a secure transport group during site and network creation.
You configure the secure transport group settings in the Secure Transport page.
To configure secure transport group settings
1. Choose > Manage > Services: Secure Transport to display the Secure Transport page.
Figure: Configuring Secure Transport Group Settings
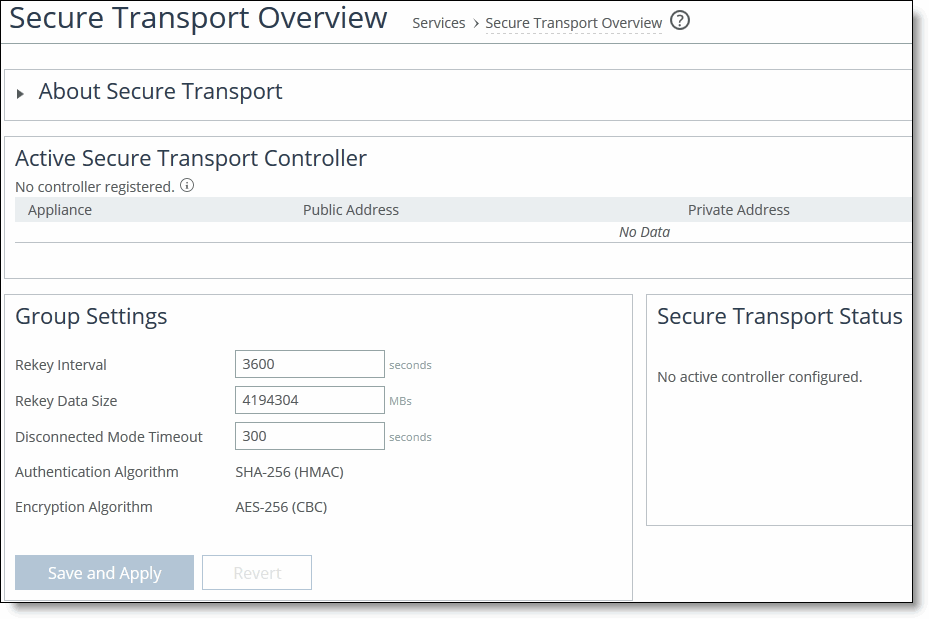
2. Under Group Settings, complete the configuration as described in this table.
Control | Description |
Rekey Interval | Specify the time in seconds to rekey the group. This is the number of seconds after which the secure transport controller will generate new security keys and push them out to the secure transport members. The secure transport members will then start using the new keys for encrypting the traffic. The default value is 3600. |
Rekey Data Size | Specify the rekey data size in megabytes. The rekey data size is the total data size encrypted by all peers using a certain security key after which the secure transport controller should generate a new key and push it to the secure transport members. The default value is 4194304. |
Disconnected Mode Timeout | Specify the amount of time in seconds the secure transport members can operate while disconnected from the secure transport controller. The default value is 300. After a disconnected mode timeout, all secure transport paths are brought down. Make sure you allow enough time for the group to recover from a disconnected state. |
Authentication Algorithm | Displays the authentication algorithm is displayed for informational purposes. |
Encryption Algorithm | Displays the encryption algorithm is displayed for informational purposes. |
Save and Apply/Revert | Click Save and Apply to save and apply your settings; click Revert to undo your changes. |
Viewing Active Secure Transport Status
You can view the current status of active secure transport controller in the Secure Transport page.
To view the current status of the active secure transport controller
1. Choose > Manage > Services: Secure Transport to display the Secure Transport page.
2. Under Active Secure Transport Status, to view the current status of the active secure transport controller.
Figure: Viewing Active Secure Transport Controller Status
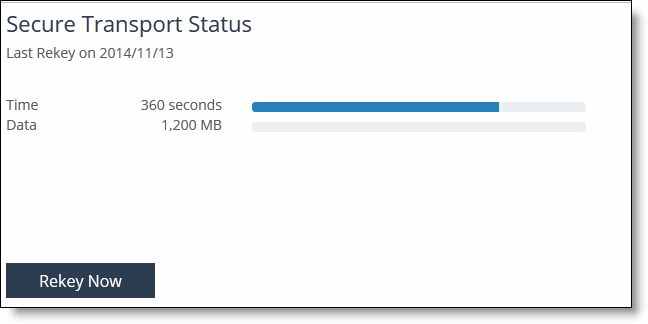
3. Click Rekey Now to rekey all SteelHead peers in the group.
Viewing Group Traffic Information
You can view group traffic information in the Secure Transport page.
To view group traffic information
1. Choose > Manage > Services: Secure Transport to display the Secure Transport page.
2. Under Traffic Information for Default_Group, view group traffic information.
Figure: Viewing Group Traffic Information
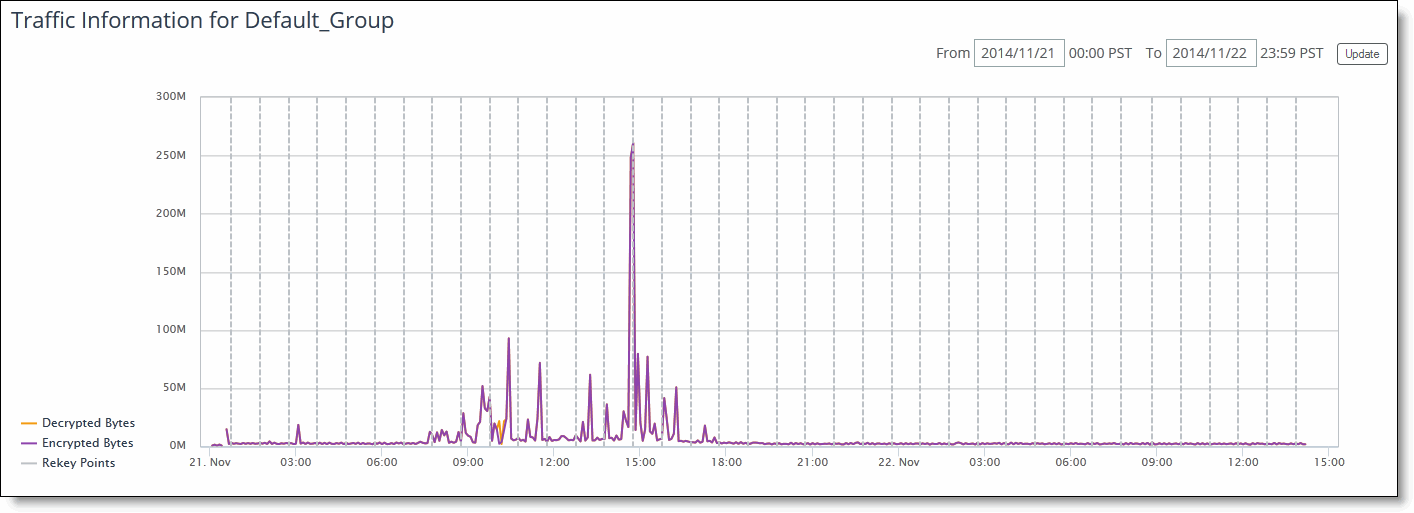
3. Click the From and To text boxes to display a calendar to set the time to begin and end the traffic information to be displayed.
4. Click Update to update the traffic information.
Viewing Secure Group Members
You can view the members of the secure transport group in the Secure Transport page.
To view members of the secure transport group
1. Choose > Manage > Services: Secure Transport to display the Secure Transport page.
Under Secure Members, view the members of the group. A green dot next to the member name indicates a connected secure transport controller; a red dot next to the member name indicates a disconnected secure transport controller.
Figure: Viewing Members of the Secure Transport Group
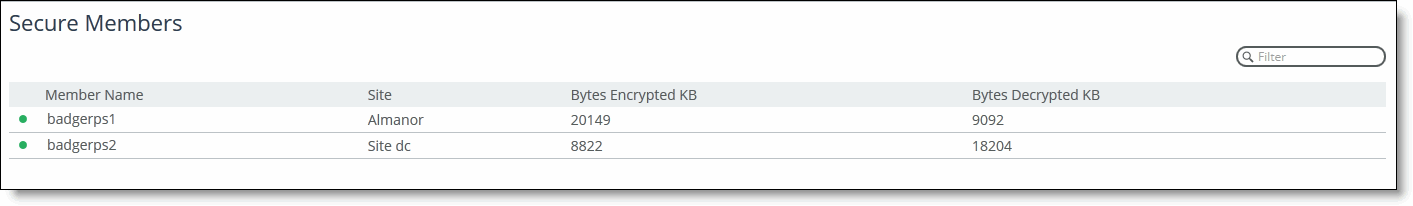
2. Optionally, in the Filter text box type a set of criteria by which to filter the displayed members.











