Figure: Editing Port Labels Page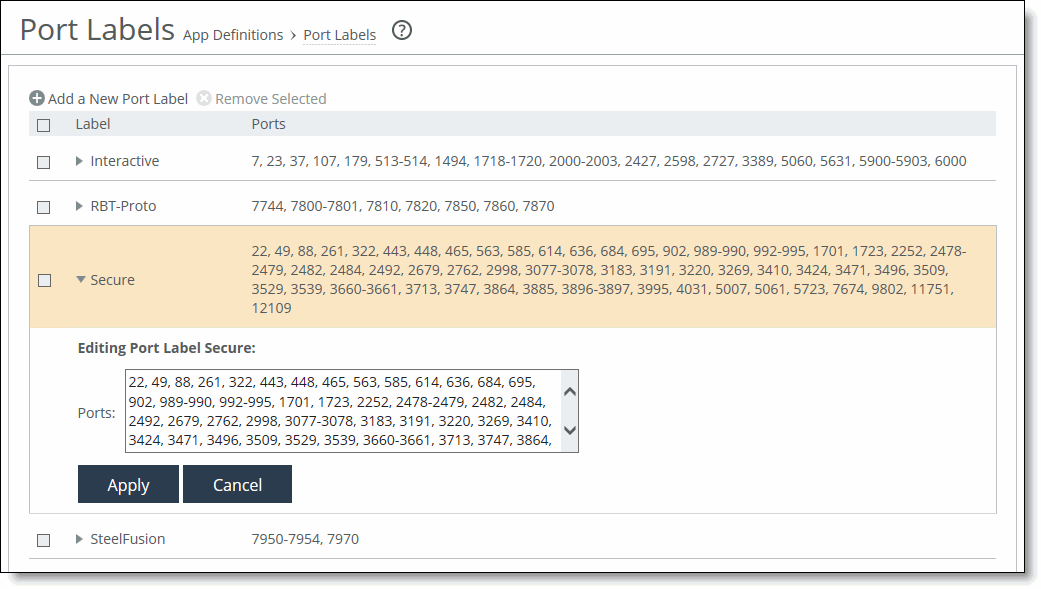


Control | Description |
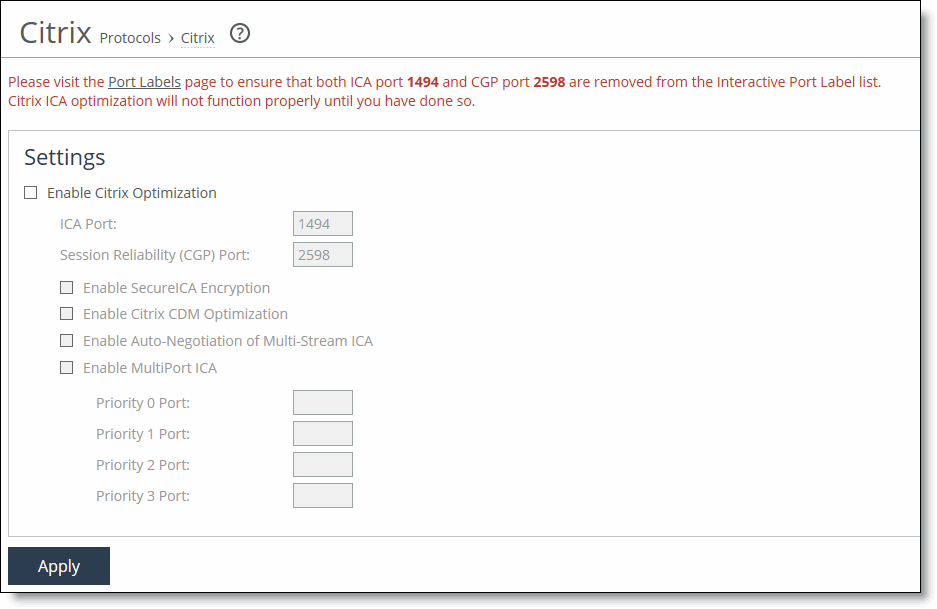
Enable Citrix Optimization | Optimizes the native Citrix traffic bandwidth. By default, Citrix optimization is disabled. Enabling Citrix optimization requires an optimization service restart. |
ICA Port | Specify the port on the Presentation Server for inbound traffic. The default port is 1494. |
Session Reliability (CGP) Port | Specify the port number for Common Gateway Protocol (CGP) connections. CGP uses the session reliability port to keep the session window open even if there’s an interruption on the network connection to the server. The default port is 2598. |
Enable SecureICA Encryption | Enables SDR and Citrix optimizations, while securing communication sent between a MetaFrame Presentation Server and a client. RiOS supports optimization of Citrix ICA sessions with SecureICA set to RC5 40-bit, 56-bit, and 128-bit encryption. By default, RiOS can optimize Citrix ICA traffic with SecureICA set to basic ICA protocol encryption. You must enable SecureICA encryption to allow RiOS to optimize ICA sessions with SecureICA encryption set to RC5 on the client-side SteelHeads. |
Enable Citrix CDM Optimization | Enable this control on the client-side and server-side SteelHeads to provide latency optimization for file transfers that use client drive mapping (CDM) between the Citrix client and server. CDM allows a remote application running on the server to access disk drives attached to the local client machine. The applications and system resources appear to the user at the client machine as if they’re running locally during the session. For example, in the remote session, C: is the C drive of the remote machine and the C drive of the local thin client appears as H:. Bidirectional file transfers between the local and remote drives use one of many virtual channels within the ICA protocol. The individual data streams that form the communication in each virtual channel are all multiplexed onto a single ICA data stream. This feature provides latency optimization for file transfers in both directions. You can use CDM optimization with or without secure ICA encryption. Both the client-side and server-side SteelHeads must be running RiOS 7.0 or later. By default, CDM optimization is disabled. Enabling CDM optimization requires an optimization service restart. CDM optimization doesn’t include support for CGP (port 2598). |
Enable Auto-Negotiation of Multi-Stream ICA | Enable this control on the client-side SteelHead to automatically negotiate ICA to use Multi-Stream ICA and carry the ICA traffic over four TCP connections instead of one. The ICA traffic within a Citrix session comprises many categories of traffic called virtual channels. A virtual channel provides a specific function of Citrix ICA remote computing architecture, such as print, CDM, audio, video, and so on. The ICA traffic within a Citrix session is also categorized by priority, in which virtual channels carrying real-time traffic, such as audio and video, are flagged with higher priority than virtual channels carrying bulk transfer traffic such as print and CDM. When enabled, the SteelHead splits traffic on virtual channels into a separate TCP stream (by ICA priorities) so that QoS can be applied to each individual stream. This feature is applicable for both CGP and ICA connections. This allows finer QoS shaping and marking of Citrix traffic. You can also use this feature with path selection to select and prioritize four separate TCP connections. You can use this feature with both inbound and outbound QoS. Both SteelHeads must be running RiOS 9.1 or later. To view the multistream connections, choose Reports > Networking: Current Connections. When the connection is classified by QoS on the SteelHead, the Application column lists the connection as Citrix-Multi-Stream-ICA along with its priority. You can also choose Reports > Networking: Inbound QoS and Outbound QoS to view the connection classifications. Four applications are available by default under Networking > App Definitions: Applications > Business VDI for QoS classification: Citrix-Multi-Stream-ICA-Priority-0 Citrix-Multi-Stream-ICA-Priority-1 Citrix-Multi-Stream-ICA-Priority-2 Citrix-Multi-Stream-ICA-Priority-3 No configuration is required on the server-side SteelHead. The Citrix deployment must support Multi-Stream ICA: the clients must be running Citrix Receiver 3.0 or later. The servers must be running XenApp 6.5 or later or XenDesktop 5.5 or later. Enabling this feature doesn’t require an optimization service restart. |
Enable MultiPort ICA | Enable this control on the client-side SteelHead to provide multiport ICA support. For thin-client applications, Citrix has a protocol that segregates the network traffic between a client and a server. Typically, all of the traffic is routed through the same port on the server. Enabling multiport ICA lets you group the traffic into multiple CGP ports using priorities based on data type (mouse clicks, window updates, print traffic, and so on). After you enable multiport ICA, you can assign a port number to each of the configurable priorities. You can’t assign the same port number to more than one priority. You can also leave a priority port blank and route that traffic through some other means—which doesn’t have to be a SteelHead. Perform these steps: 1. From the Citrix server, enable and configure the multiport policy for the computer configuration policy in the Group Policy Editor or Citrix AppCenter. By default, port 2598 has high priority (value 1) and is not configurable. You can configure port values 0, 2, and 3. Use these application priorities for multiport ICA: Very high = 0, for audio High = 1, for ThinWire/DX command remoting, seamless, MSFT TS licensing, SmartCard redirection, control virtual channel, mouse events, window updates, end-user experience monitoring. Medium = 2, for MediaStream (Windows media and Flash), USB redirection, clipboard, and client drive mapping. Low = 3, for printing, client COM port mapping, LPT port mapping, and legacy OEM virtual channels. 2. Restart the Citrix server. You can then go to Reports > Networking: Current Connections to view the TCP connections in the ICA session. 3. On the client-side SteelHead, specify the same CGP ports configured on the Citrix server in the Priority Port fields. You can then return to Reports > Networking: Current Connections to view the four unique TCP connections in the ICA session. If you have a port label to represent all ICA traffic over ports 1494 and 2598, you must add the new CGP ports to support multiport ICA. Make sure that any ports you configure on the Citrix server don’t conflict with the ports used on the preconfigured port labels on the SteelHead. The port labels use default pass-through rules to automatically forward traffic. To view the default port labels, choose Networking > App Definitions: Port Labels. You can resolve a port conflict as follows: • To configure a standard port that is associated with the RBT-Proto, Secure, or Interactive port labels and can’t be removed, use a different port number on the Citrix server configuration. • Otherwise, remove the port from the port label. |
Client-side SteelHead Traffic Type Setting | Server-side SteelHead Traffic Type Setting | Client-side SteelHead Fallback Setting | Server-side SteelHead Fallback Setting | Traffic-Flow Type, if SSL Secure Inner Channel Setup Fails |
SSL and secure protocols | SSL and secure protocols | Lenient. Fallback to No Encryption is enabled, allowing fallback. | Lenient. Fallback to No Encryption is enabled, allowing fallback. | Optimized without encryption |
SSL and secure protocols | SSL and secure protocols | Lenient. Fallback to No Encryption is enabled, allowing fallback. | Strict. Fallback to No Encryption is disabled. | Passed through |
SSL and secure protocols | SSL and secure protocols | Strict. Fallback to No Encryption is disabled. | Lenient. Fallback to No Encryption is enabled, allowing fallback. | Passed through |
SSL and secure protocols | SSL and secure protocols | Strict. Fallback to No Encryption is disabled. | Strict. Fallback to No Encryption is disabled. | Passed through |
SSL and secure protocols | All | Lenient. Fallback to No Encryption is enabled, allowing fallback. | Lenient. Fallback to No Encryption is enabled, allowing fallback. | Optimized without encryption |
SSL and secure protocols | All | Lenient. Fallback to No Encryption is enabled, allowing fallback. | Strict. Fallback to No Encryption is disabled. | Passed through |
SSL and secure protocols | All | Strict. Fallback to No Encryption is disabled. | Lenient. Fallback to No Encryption is enabled, allowing fallback. | Passed through |
SSL and secure protocols | All | Strict. Fallback to No Encryption is disabled. | Strict. Fallback to No Encryption is disabled. | Passed through |
Client-side SteelHead Running RiOS Version | Server-side SteelHead Running RiOS Version | SteelHead Fallback Setting | ICA or CGP | Citrix Traffic-Flow Type, if SSL Secure Inner Channel Setup Fails |
7.0 with traffic type SSL and secure protocols | 7.0 with traffic type SSL and secure protocols | Lenient. Fallback to No Encryption is enabled, allowing fallback. | Both | Optimized with a warning |
7.0 with traffic type SSL and secure protocols | 7.0 with traffic type SSL and secure protocols | Strict. Fallback to No Encryption is disabled. | Both | Passed through |
6.5.x and earlier | 7.0 with traffic type SSL and secure protocols | Lenient. Fallback to No Encryption is enabled, allowing fallback. | Both | Optimized without a secure inner channel |
6.5.x and earlier | 7.0 with traffic type SSL and secure protocols | Strict. Fallback to No Encryption is disabled. | Both | Optimized without a secure inner channel, with a warning that traffic on the WAN is unencrypted |
7.0 with traffic type SSL and secure protocols | 6.5.x and earlier | Lenient. Fallback to No Encryption is enabled, allowing fallback. | Both | Optimized without a secure inner channel |
7.0 with traffic type SSL and secure protocols | 6.5.x and earlier | Strict. Fallback to No Encryption is disabled. | ICA | Optimized without a secure inner channel |
7.0 with traffic type SSL and secure protocols | 6.5.x and earlier | Strict. Fallback to No Encryption is disabled. | CGP | Passed through on the WAN unencrypted |