Overview of Client Accelerator
This chapter provides an overview of Client Accelerator. It includes these sections:
When using this guide, if you’re not familiar with the installation, configuration, and management of networks with deployed SteelHeads, consult the documents listed below:
• SteelHead Installation and Configuration Guide
• SteelHead User Guide
• SteelHead Deployment Guide
Before you begin the installation and configuration process for the Client Accelerator, you must select a network deployment. For specific Client Accelerator deployment options, see the SteelHead Deployment Guide.
Overview of the Client Accelerator solution
The Client Accelerator solution enables you to optimize application protocols such as HTTP and MAPI and to reduce bandwidth for other protocols, providing LAN-like performance to remote users who are accessing your computer network using any type of remote access (dial-up, broadband, wireless, and so forth). Managed by a Client Accelerator, remote users employ client software to exchange optimized data with a SteelHead. The controller can be either a Client Accelerator appliance or a Client Accelerator-v.
The Client Accelerator solution enables you to optimize traffic for these types of users:
• Mobile users - Mobile users are employees who connect to the WAN from various locations and also connect to the LAN locally.
• Home users - Home users are employees who use computers that connect to the corporate network.
• Small branch office users - Small branch office users are located at offices with fewer than ten employees that connect to the WAN but don’t require a standard SteelHead.
Definition of terms
The following terms are used to describe features, attributes, and processes in the Client Accelerator.
Term | Definition |
Endpoint | An endpoint is a client computing device, such as a personal computer. |
Client install package | A client install package installs Client Accelerator software onto each of your endpoints. A package created on a Client Accelerator contains complete endpoint settings, including the fully qualified domain name (FQDN) of the Client Accelerator and a certificate that secures communication between the client and the controller. The default package that ships with the Client Accelerator contains the default (initial) policy, with complete endpoint settings. The default package is designed to be suitable for most network environments. Typically, you install and deploy Client Accelerator clients without modifying the default policy. Consider deploying the Client Accelerator client software to your endpoints using the policy defaults and modifying them only as necessary. For detailed information about the default policy settings, see the Client Accelerator User Guide. |
Policy | A policy specifies computer-specific software settings for acceleration (such as protocol and SSL settings) and endpoints (such as data store size and Client Accelerator to connect to). A policy is required for optimization to occur. |
Assignment | An assignment occurs when a policy is matched to a group ID. |
Group ID | A group ID (GID) governs which policies and packages the Client Accelerator provides to endpoints. The GID enables you to assign policies to groups of endpoints. When you create the package, you can assign a GID to it. The GID is associated with the endpoint upon installation. The Client Accelerator subsequently uses the GID to identify the endpoint and provide assigned policies and updates. Group ID was called Deployment ID in Client Accelerator 2.x and earlier. |
Demilitarized Zone | A demilitarized zone (DMZ) is a computer or small subnetwork that sits between a trusted internal network, such as a corporate private LAN, and an untrusted external network, such as the public internet. Typically, the DMZ contains devices accessible to internet traffic, such as web (HTTP) servers, FTP servers, SMTP (email) servers, and DNS servers. |
Client Accelerator Controller components
A Client Accelerator Controller deployment consists of these components:
• Client Accelerator Controller - The Client Accelerator Controller acts as a gateway for remote users and is installed at a data center or at the server side of the WAN, where it is accessible to users. The Client Accelerator Controller features a web-based GUI, the Management Console, that you use to centrally manage endpoints. You can also use the Management Console for endpoint software upgrades, licensing, reporting, and monitoring.
• Client Accelerator Client - The Client Accelerator client enables endpoint PCs and Macs to optimize data when connected to a Client Accelerator Controller. You distribute Client Accelerator software to endpoints using packages. You create packages using the Management Console, and you deploy them to your endpoints using the deployment tool of your choice. You can use a commercial deployment tool (for example, Microsoft SMS, Active Directory, or Altiris) to deploy packages, or you can email the link to your remote users. For detailed information about deployment options for packages, see the Client Accelerator User Guide.
• SteelHead - SteelHeads deployed throughout the network optimize data generated and accessed by end users. The Client Accelerator Controller allows Client Accelerator clients to exchange optimized data with the SteelHead. For details on the SteelHead, see the SteelHead Deployment Guide and the SteelHead User Guide.
When you start the Client Accelerator client, it accesses the specified Client Accelerator Controller to obtain a license and a policy. After the endpoint retrieves a license and a policy from the Client Accelerator Controller, traffic can be optimized between the Client Accelerator client and the server-side SteelHead. The Client Accelerator client performs data optimization using the same mechanisms as a client-side SteelHead. The endpoint maintains a connection with the Client Accelerator to download new policies from the Client Accelerator. This connection also enables the Client Accelerator to monitor your endpoints and to upload logs from them.
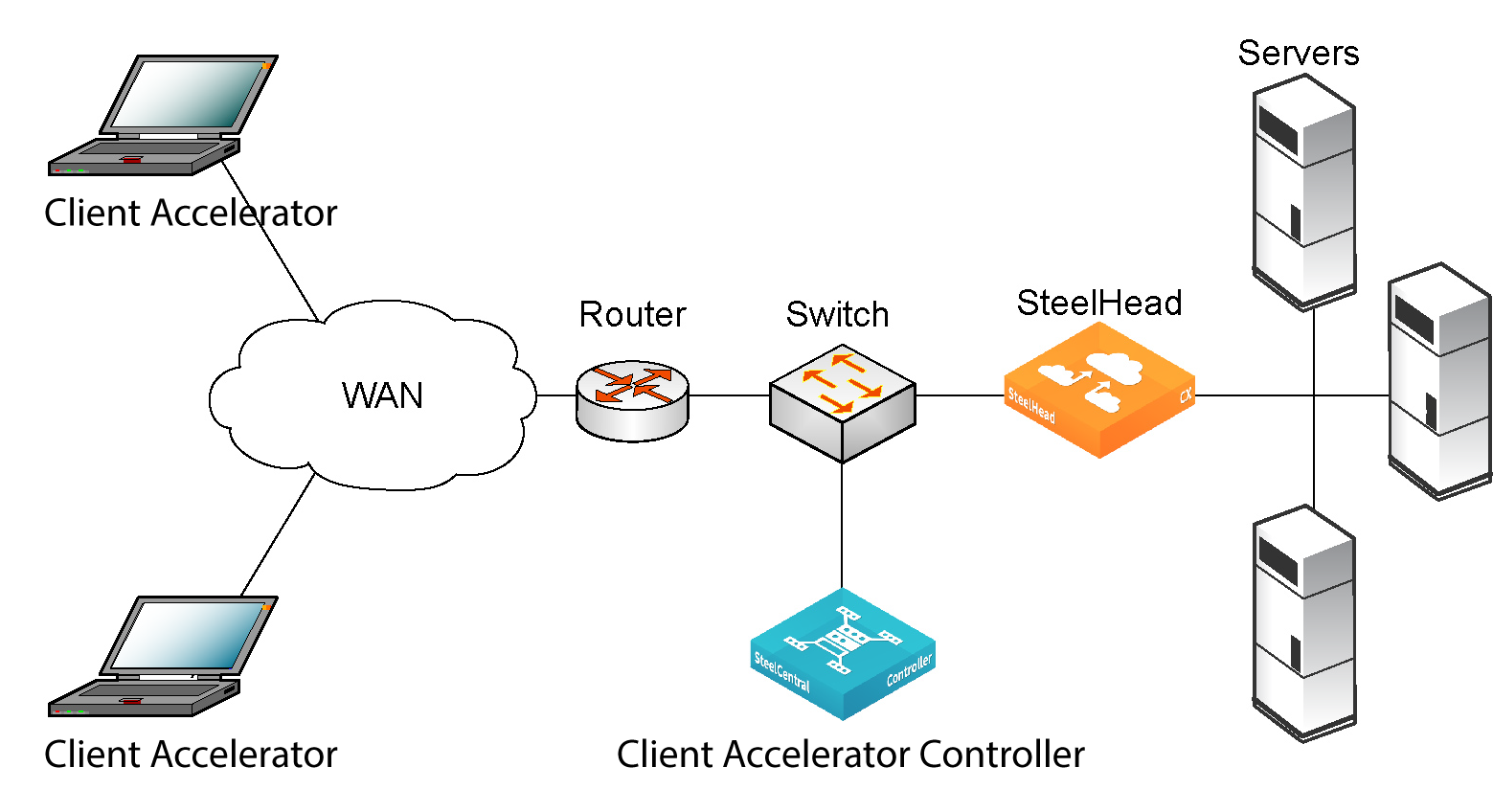
Figure: Typical Client Accelerator deployment shows a typical Client Accelerator deployment. The Client Accelerator is located at the main data center. Client Accelerator clients communicate with the Client Accelerator for management and reporting purposes. Client Accelerator clients are optimized by SteelHeads at the data center.
Figure 1‑1. Typical Client Accelerator deployment
Software and configuration requirements
This section provides information about product dependencies and compatibility.
Client Accelerator
This table summarizes the software and configuration requirements for deploying the Client Accelerator.
Component | Software and configuration requirements |
Client Accelerator Console | A Client Accelerator console is any computer (including Microsoft Surface Pro tablets) that supports a web browser with a color image display. The Client Accelerator console has been tested Mozilla Firefox 78.0.2, Microsoft Internet Explorer 11 and Google Chrome 84.0.4147.89. JavaScript and cookies must be enabled in your web browser. If you want to encrypt your communication, you must have an SSL-capable browser. No particular operating system is required. |
Client Accelerator-v for ESXi
Client Accelerator-v for ESXi is supported on VMware ESXi 5.0, 5.1, 5.5, 6.0, 6.5, and 6.7. Install and configure Client Accelerator-v for ESXi using VMware Virtual Infrastructure (VI) client or the VMware vSphere Client.
Virtual machine snapshots are not supported by Client Accelerator-v for ESXi.
For detailed information about Client Accelerator-v for ESXi, see
Chapter: Installing Client Accelerator-v for ESXi.Client Accelerator-v for Hyper-v
Client Accelerator-v for Hyper-v is supported on Hyper-v version 10.0.14393.0.
Client Accelerator-v for Azure
Client Accelerator-v for Azure is supported on Azure. Client Accelerator-v can be installed and run in Azure.
Supported operating systems for Client Accelerator
This table lists the supported operating systems for Client Accelerator.
Operating system | Supported versions |
Windows | • Windows 8.1 (64 bit) • Windows 10 (32 bit) • Windows 10 (64 bit) • Windows Server 2012 R2 (64 bit) |
Mac | • macOS 10.14 • macOS 10.15 |
Firewall requirements
This section lists the required firewall settings for Client Accelerator deployments.
Port requirements:
• Ports 80 and 443 must be open for the server-side firewall management connection to the Client Accelerator. Port 22 must be open for access to the command-line interface (CLI).
• Either port 80 or port 443 and port 7870 must be open for the connection to the Client Accelerator clients.
• For out-of-path deployments, port 7810 must be open.
• For in-path deployments, port 7800 must be open.
If you’re using application control, you must allow these processes:
• For Windows - rbtdebug.exe, rbtmon.exe, rbtsport.exe, and shmobile.exe
• For Mac OS X - rbtsport, rbtmond, rbtuseragentd, and rbtdebug
Antivirus compatibility
Client Accelerator 6.0 and later has been tested with these antivirus software with no impact on performance:
For Windows systems
• McAfee Internet Security Suite 10.7
• Microsoft Windows Firewall (allow rbtsport)
• Symantec Endpoint Protection 14.2
For Mac systems
• IP Firewall (IPFW)
• Mac OS X Application Firewall
• McAfee Internet Security
• Symantec for Mac
Earlier releases
• CA Anti-Virus 2009
• CA eTrust Anti-Virus r8.x
• Cisco Security Agent 5.2
• McAfee VirusScan 10.0
• McAfee VirusScan Professional 9.0
• McAfee VirusScan Plus 2009
• McAfee Internet Security Suite 2009
• McAfee Internet Security Suite 2007
• McAfee Internet Security Suite 2006
• McAfee Internet Security Suite 2005
• McAfee Internet Security Suite 2004
• Norton AntiVirus 2010 with Antispyware
• Norton AntiVirus 2009
• Norton AntiVirus 2008
• Norton Internet Security 2010
• Symantec AntiVirus Corporate Edition 10.2
• Symantec AntiVirus Corporate Edition 10.1
• Symantec Internet Security Suite 2009
• Symantec Internet Security Suite 2008
• Symantec Endpoint Protection 11.0
• Trend Micro PC-Cillin 2009 Internet Security (including firewall)
• Trend Micro PC-Cillin 2008 Internet Security (including firewall)
• ZoneAlarm Internet Security Suite 3U
VPN requirements
When deploying the Client Accelerator software, make sure that the VPN tunnel is not optimized. If the VPN tunnel uses TCP for transport, when you configure a policy, you must add a pass-through rule for the VPN port number connected to the client. Depending on your deployment scenario, this rule might be the first rule in the list. If the port uses UDP, no rule is required.
For details about configuring policies, see the Client Accelerator User Guide.
VPN software products that use IPsec as the transport protocol don’t need a pass-through rule because IPsec is its own non-TCP/IP protocol and, by default, the SteelHeads don’t optimize it.
For Cisco SSL VPN AnyConnect for use on both Windows and Macintosh platforms, you must configure a fixed-target rule or configure the Cisco ASA to allow TCP options if you plan to use in-path rules. For details, go to Knowledge Base article
S15292 The Cisco ASA 5500 Series (used only on the Windows platform) requires additional configuration to be compatible with the Client Accelerator. You can either configure an in-path, fixed-target rule for the Client Accelerator policy, or you can make configuration changes on the Cisco ASA. For details about configuring in-path, fixed-target rules for acceleration policies, see the
Client Accelerator User Guide. For details about configuring the Cisco ASA, go to Knowledge Base article
S15292.
Client Accelerator 6.0 and later has been tested with the VPN software listed below. For specific versions supported, go to Knowledge Base article
S14999.
Supported VPNs for Windows
• SonicWALL Connect Tunnel V-1.0.3.634
• Cisco Anyconnect V- 4.9.00086
• Palo Alto Global Protect V-5.0.9-15
• WatchGuard
Supported VPNs for Mac
• SonicWALL Connect Tunnel V-5.06 (5040)
• Cisco Anyconnect V- 4.9.00086
• Palo Alto Global Protect V-5.0.9-15
Safety guidelines
Follow the safety precautions outlined in the Safety and Compliance Guide when installing and setting up your equipment.
Failure to follow these safety guidelines can result in injury or damage to the equipment. Mishandling of the equipment voids all warranties. Please read and follow safety guidelines and installation instructions carefully.
Many countries require the safety information to be presented in their national languages. If this requirement applies to your country, consult the Safety and Compliance Guide. The guide contains the safety information in your national language. Before you install, operate, or service the Riverbed products, you must be familiar with the safety information. Refer to the guide if you don’t clearly understand the safety information provided in the documentation.
Upgrading to Client Accelerator
This section describes how to upgrade your Client Accelerator appliance to Client Accelerator. These instructions assume that you’re familiar with the Riverbed CLI and Management Console.
To upgrade your software
1. Log in to the Management Console using the administrator account (admin).
2. Choose Administration > Maintenance > Software Upgrade page and select one of these options:
– From URL - Type the URL that points to the software image. Use one of these formats:
http://host/path/to/file
https://host/path/to/file
ftp://user:password@host/path/to/file
scp://user:password@host/path/to/file
– From Riverbed Support Site - Select the target release number from the drop-down list to download a delta image directly to the appliance from the Riverbed Support site. The downloaded image includes only the incremental changes. You don’t need to download the entire image. The system downloads and installs the new image immediately after you click Install. To download and install the image later, schedule another date or time before you click Install.
– From Local File - Browse your file system and select the software image.
– Schedule Upgrade for Later - Select this check box to schedule an upgrade for a later time. Type the date and time in the Date and Time text boxes using these formats:
yyyy/mm/dd and hh:mm:ss.
3. Click Install to immediately upload and install the software upgrade on your system, unless you schedule it for later.
The software image can be quite large; uploading the image to the system can take a few minutes. Downloading a delta image directly from the Riverbed Support site is faster because the downloaded image includes only the incremental changes and is downloaded directly to the appliance.
As the upgrade progresses, status messages appear. After the installation is complete, you’re reminded to reboot the system to switch to the new version of the software.
4. Choose Administration > Maintenance > Reboot/Shut Down and click Reboot.
The appliance can take a few minutes to reboot. This behavior is normal because the software is configuring the recovery flash device. Don’t press Ctrl+C, unplug, or otherwise shut down the system during this first boot. There is no indication displayed during the system boot that the recovery flash device is being configured.
After the reboot, the Home page, the Software Upgrade page, and the Support page of the Management Console display the version upgrade.


