Multiple WAN Router Deployments
Typically, multiple WAN routers are used at locations where redundancy or high availability is important. With multiple routers, the loss of a single WAN link, or a single WAN router, does not prevent hosts at the locations from reaching WAN resources. SteelHeads can be deployed and configured to maintain the high availability for network access. Additionally, multiple SteelHeads can be deployed and configured so that a SteelHead failure allows new connections to be optimized.
This section covers the following sections:
Configuring Multiple WAN Router Deployments Without Connection ForwardingConfiguring Multiple WAN Router Deployments with Connection ForwardingIf one or more SteelHeads are deployed to cover all the links between the LAN switches and the WAN connecting routers, connection forwarding is not required. These deployments are referred to as
serial deployments, and they can use multiple SteelHeads (in a
Primary and Backup Deployments or
Serial Cluster Deployments) to achieve optimization high availability.
If it is impossible or impractical to have all the WAN links covered by a single SteelHead, multiple SteelHeads are used. They must have connection forwarding configured. These deployments are known as parallel deployments. High availability for optimization is achieved by using either the connection forwarding fail-to-block configuration, or by using primary and backup, or serial clustering on each of the parallel links to the WAN.
For more information about connection forwarding, see
Connection Forwarding. For more information about fail-to-block mode, see
Fail-to-Block Mode.
Riverbed recommends that you use designs that do not require connection forwarding (that is, serial designs) whenever possible. Serial designs require less configuration, and are easier to troubleshoot, than parallel designs. If you need a parallel design, a deployment using the SteelHead Interceptor might have several advantages, including policy-based load-balancing and failover handling.
Using the WAN- or LAN-side HSRP IP address improves the likelihood that optimized connections survive a network outage. To plan this you must understand how the SteelHead learns and reacts to changes in the network. Keep in mind that there are many different network design possibilities, and it is not possible to explain all the caveats here.
By default, the SteelHead uses simplified routing, which learns the association between IP addresses and MAC addresses, and Address Resolution Protocol (ARP), which learns associations between IP addresses and MAC addresses on the same subnet as the in-path interface and MAC addresses.
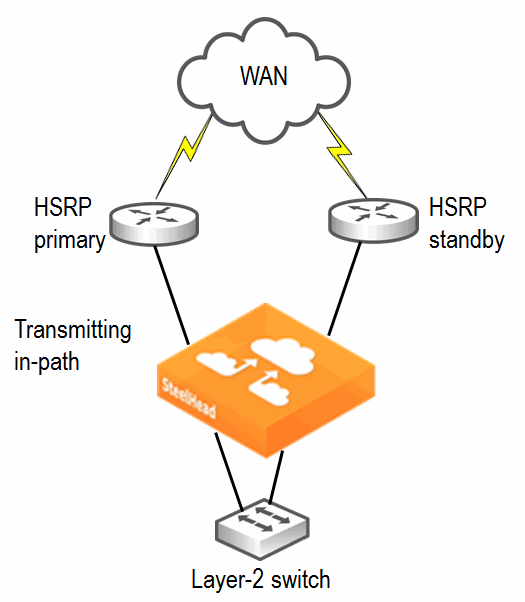
The SteelHead also builds a table of MAC addresses to the LAN or WAN interface, based on the Ethernet frames that cross through the SteelHead in-path interface. Using these tables, the SteelHead learns which destination MAC address to use for packets the SteelHead originates and the corresponding interface on which to transmit the packet. For example, if local hosts are on the same subnet as the SteelHead in-path interfaces and the WAN routers are using HSRP, the transmitting in-path interface learns all local IP addresses on the same subnet to MAC address, through ARP, through the LAN interface. The SteelHead learns remote IP address-to-MAC address relationships from simplified routing = destination-only through the WAN interface. If the SteelHead has not learned the IP address-to-MAC address relationship through simplified routing or ARP, it follows its default gateway.
When the network experiences an outage, the SteelHead in-path interface that transmits for the connection does not react to the change in the network until there has been a change in the flow of traffic through the transmitting in-path interface. After the flow of traffic changes, the SteelHead in-path interface can learn that the destination is available through the opposite interface (WAN now goes to LAN). For example, using the default simplified routing setting, a SteelHead learns that a remote IP address is associated with the MAC address of the primary WAN router that owns the HSRP virtual MAC. When the primary router WAN circuit fails, the primary router can decrement its HSRP priority and the standby router can preempt the primary router to assume control of the HSRP virtual MAC. When this happens, the transmitting interface learns the HSRP MAC through the LAN interface and can continue transmitting traffic across the WAN for optimized connections.
On the other hand, if the transmitting interface learned the remote IP-to-MAC relationship as the physical interface of the primary router then it needs to detect a packet ricochet to learn that the path across the WAN is actually through the LAN interface. Also, you might need to consider any TCP connections that the SteelHead originates, such as the OOB splice. You can use the protocol connection lan on-oob-timeout drop command.
In certain scenarios, existing optimized connections do not survive: for example, if there is a failure between the SteelHead and a directly connected device, such as the cable is damaged or a device lost power. When a directly connected device fails, the first-hop redundancy protocol such as HSRP detects the failure and a standby device can assume the primary role. However, some features on the SteelHead, such as link state propagation, can also detect the failure and stop connectivity in the associated interface (if the failure affects LAN0_0 then WAN0_0 also stops connectivity). The result is that all paths from the in-path interface that transmit for the optimized connection are in a down state and the optimized connections do not continue. Most applications restart new connections. Link state propagation provides feedback to other devices of the failure, and network protocols can more quickly detect the failure.
The choice of a default gateway is very important in locations with multiple WAN routers. In addition to choosing a default gateway (and simplified routing) that minimizes packet ricochet, HSRP or similar protocols can be used to ensure the loss of a single WAN router does not prevent the SteelHead from transmitting packets over the WAN. Most WAN devices that support HSRP or similar protocols have a link tracking option that allows them to relinquish the HSRP virtual IP address if a WAN link fails; this option should be used when possible.
In a high-availability environment, there are often multiple gateways or next hops to choose from. To minimize the disruption to any existing optimized connections when a network device fails, it is important that the correct settings are configured on the SteelHeads.
Figure 9‑10. HRSP Diagram
Configuring Multiple WAN Router Deployments Without Connection Forwarding
The following section describes best practices for serial SteelHead deployments at locations with multiple routers. Each of the following scenarios can be modified to use multiple SteelHeads, either in primary and backup or serial cluster configurations. This section covers the following scenarios:
Configuring a Single SteelHead and Single Layer-2 Switch DeploymentConfiguring a Single SteelHead and Dual Layer-2 Switches DeploymentConfiguring a Single SteelHead and Single Layer-3 Switch DeploymentConfiguring Single SteelHead and Dual Layer-3 Switches DeploymentConfiguring a Single SteelHead and Single Layer-2 Switch Deployment
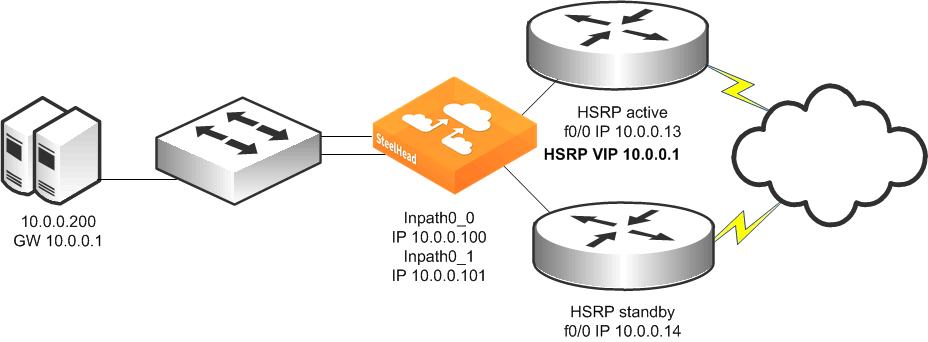
Figure 9‑11 shows a topology consisting of two routers, a single Layer-2 switch, and one SteelHead with a 4-port card. The client and the SteelHead are in the same subnet. The client uses the HSRP virtual IP as its default gateway (10.0.0.1).
In this environment, the in-path gateway for both the inpath0_0 and inpath0_1 interfaces must point to the HSRP virtual IP (10.0.0.1). You do not need to enable simplified routing as the client is on the same subnet as the SteelHead.
Figure 9‑11. Single SteelHead, Single Layer-2 Switch, Dual Router Deployment
To configure a SteelHead, single Layer-2 switch, and dual routers
Connect to the CLI and enter the following commands:in-path enable
in-path interface inpath0_1 enable
interface inpath0_0 ip address 10.0.0.100 /24
interface inpath0_1 ip address 10.0.0.101 /24
ip in-path-gateway inpath0_0 "10.0.0.1"
ip in-path-gateway inpath0_1 "10.0.0.1"
in-path peering auto
in-path simplified routing dest-only
Configuring a Single SteelHead and Dual Layer-2 Switches Deployment
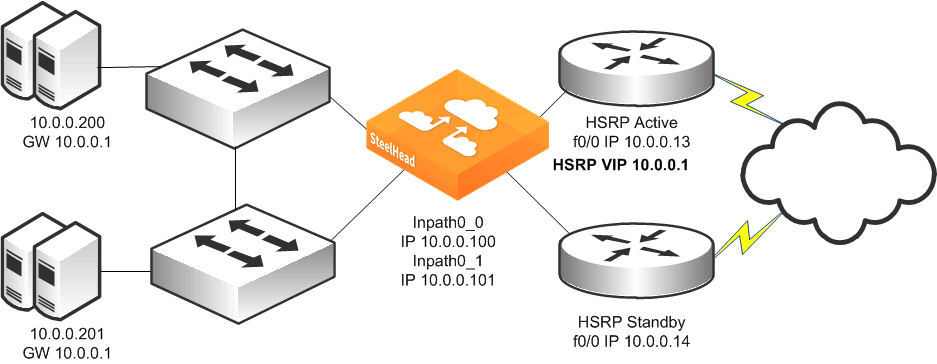
Figure 9‑12 shows a topology in which there are two routers, two Layer-2 switches, and one SteelHead with a 4-port card. The client and the SteelHead are in the same subnet. The client uses the HSRP virtual IP as its default gateway (10.0.0.1).
In this environment, the in-path gateway for both the inpath0_0 and inpath0_1 interfaces must point to the HSRP virtual IP (10.0.0.1). You do not need to enable simplified routing because the clients are on the same subnet as the SteelHead.
Figure 9‑12. Single SteelHead, Dual Layer-2 Switches, Dual Router Deployment
To configure a SteelHead, dual Layer-2 switches, and dual routers
Connect to the CLI and enter the following commands:in-path enable
in-path interface inpath0_1 enable
interface inpath0_0 ip address 10.0.0.100 /24
interface inpath0_1 ip address 10.0.0.101 /24
ip in-path-gateway inpath0_0 "10.0.0.1"
ip in-path-gateway inpath0_1 "10.0.0.1"
in-path peering auto
in-path simplified routing dest-only
Configuring a Single SteelHead and Single Layer-3 Switch Deployment
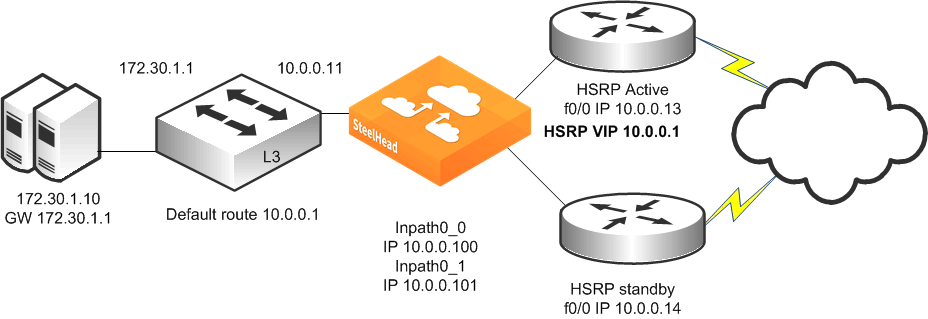
Figure 9‑13 shows a topology in which there are two routers, a single Layer-3 switch, and a single SteelHead with a 4-port card. The client and the SteelHead are in different subnets. The client is using the Layer-3 switch as its default gateway. The Layer-3 switch does not having any routing protocols configured and relies on the default route to reach other subnets. The default route uses the HSRP IP address as the next hop.
In this environment, the in-path gateway on the inpath0_0 and inpath0_1 interface must use the Layer-3 switch as its default gateway (10.0.0.11) while configuring simplified routing to populate its table based on destination MAC address (CLI command: in-path simplified routing dest-only).
Figure 9‑13. Single SteelHead, Single Layer-3 Switch, Static Routing, Dual Router Deployment
To configure a SteelHead, single Layer-3 switch, static routing, and dual routers
Connect to the CLI and enter the following commands:in-path enable
in-path interface inpath0_1 enable
interface inpath0_0 ip address 10.0.0.100 /24
interface inpath0_1 ip address 10.0.0.101 /24
ip in-path-gateway inpath0_0 "10.0.0.11"
ip in-path-gateway inpath0_1 "10.0.0.11"
in-path peering auto
in-path simplified routing dest-only
Configuring Single SteelHead and Dual Layer-3 Switches Deployment
Figure 9‑14 shows a topology in which there are two routers, two Layer-3 switches, and a single SteelHead with a 4-port card. The clients and the SteelHead are in different subnets. The clients are using the Layer-3 switches as their default gateways. The Layer-3 switches do not have any routing protocols configured and relies on the default route to reach other subnets. The default route uses the HSRP IP address as the next hop.
In this environment, the in-path gateway on the inpath0_0 and inpath0_1 interface must use the HSRP address of the Layer-3 switches as its default gateway (10.0.0.254) while configuring simplified routing to populate its table based on destination MAC address (CLI command: in-path simplified routing dest-only).
Figure 9‑14. Single SteelHead, Dual Layer-3 Switches, Dual HSRP, Static Routing, Dual Router Deployment
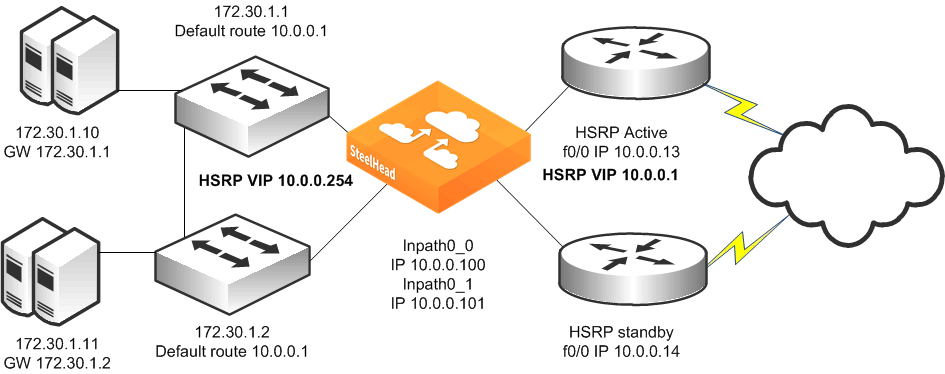
To configure a SteelHead, dual Layer-3 switches, dual HSRP, static routing, and dual routers
Connect to the CLI and enter the following commands:
in-path enable
in-path interface inpath0_1 enable
interface inpath0_0 ip address 10.0.0.100 /24
interface inpath0_1 ip address 10.0.0.101 /24
ip in-path-gateway inpath0_0 "10.0.0.254"
ip in-path-gateway inpath0_1 "10.0.0.254"
in-path peering auto
in-path simplified routing dest-only
Configuring Multiple WAN Router Deployments with Connection Forwarding
The following section describes best practices for parallel SteelHead deployments at locations with multiple routers. Each of the scenarios that follow can be modified to use additional SteelHeads for each path to the WAN, using either the primary and backup or serial cluster configurations. If you are using multiple SteelHeads on each path, every SteelHead at the location must be configured as a connection-forwarding neighbor for every other SteelHead at the location. This section covers the following scenarios:
Configuring Basic Connection ForwardingConfiguring Connection Forwarding with Allow-Failure and Fail-to-BlockConfiguring a Dual SteelHead and Dual Layer-2 Switches DeploymentConfiguring a Dual SteelHead and Dual Layer-3 Switches DeploymentConfiguring a Dual SteelHead with Multiple In-Path DeploymentConfiguring Basic Connection Forwarding
This example requires you to have configured your cabling and duplex according to the recommendations described in
Cabling and Duplex.
Figure 9‑15. Physical In-Path Deployment with Connection Forwarding
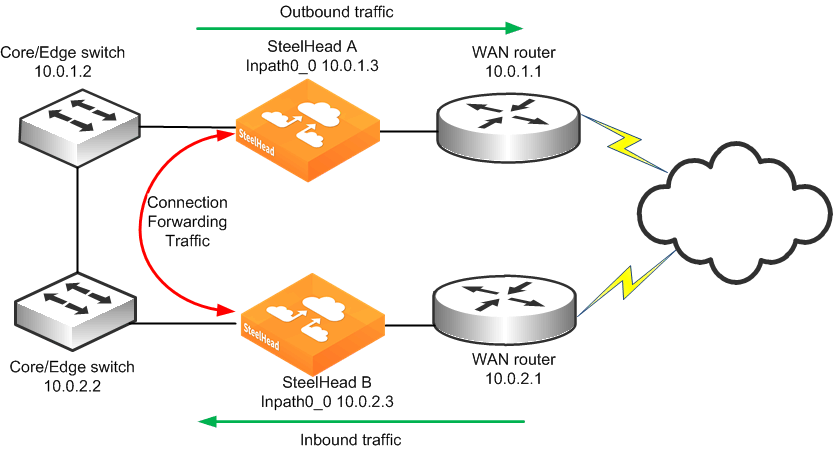
This example makes the following assumptions:
Connection forwarding is enabled by configuring the in-path0_0 IP address of the two SteelHeads as neighbors.When one of the SteelHeads fails, the neighbor SteelHead stops attempting to optimize new connections until the down SteelHead recovers or is replaced. Simplified routing removes any packet ricochet that might occur when the SteelHead sends traffic to remote SteelHeads.To configure connection-forwarding multiple WAN routers
On SteelHead A, connect to the CLI and enter the following commands:
in-path enable
interface inpath0_0 ip address 10.0.1.3 /24
ip in-path-gateway inpath0_0 10.0.1.2
in-path peering auto
in-path simplified routing dest-only
steelhead communication enable
steelhead name SteelHeadB main-ip 10.0.2.3
On SteelHead B, connect to the CLI and enter the following commands:
in-path enable
interface inpath0_0 ip address 10.0.2.3 /24
ip in-path-gateway inpath0_0 10.0.2.2
in-path peering auto
in-path simplified routing dest-only
steelhead communication enable
steelhead name SteelHeadA main-ip 10.0.1.3
These steps do not include the configuration of features such as duplex, alarms, and DNS.
For information about connection forwarding, see
Connection Forwarding.
Configuring Connection Forwarding with Allow-Failure and Fail-to-Block
This example requires you to have configured your cabling and duplex according to the recommendations described in
Cabling and Duplex.
The following example represents the minimum steps required to configure a SteelHead deployment in which connection forwarding is configured, and both fail-to-block and allow-failure are enabled. This example does not include configuration instruction for features such as the management interface, DNS, and SNMP.
This example makes the following assumptions:
Connection forwarding is enabled by configuring the in-path0_0 IP address of the two SteelHeads as neighbors. Fail-to-block option is enabled. (This is not supported with all in-path hardware and SteelHead models.)The allow-failure CLI command is enabled. This specifies that a SteelHead B continues to optimize new connections, if SteelHead A down. Simplified routing removes any packet ricochet that might occur when the SteelHead sends traffic to remote SteelHeads.To configure connection forwarding with multiple WAN routers, allow-failure, and fail-to-block
On SteelHead A, connect to the CLI and enter the following commands:
in-path enable
interface inpath0_0 ip address 10.0.1.3 /24
ip in-path-gateway inpath0_0 10.0.1.2
in-path peering auto
in-path simplified routing dest-only
steelhead communication enable
steelhead name SteelHeadB main-ip 10.0.2.3
steelhead communication allow-failure
no interface inpath0_0 fail-to-bypass enable
On SteelHead B, connect to the CLI and enter the following commands:
in-path enable
interface inpath0_0 ip address 10.0.2.3 /24
ip in-path-gateway inpath0_0 10.0.2.2
in-path peering auto
in-path simplified routing dest-only
steelhead communication enable
steelhead name SteelHeadA main-ip 10.0.1.3
steelhead communication allow-failure
no interface inpath0_0 fail-to-bypass enable
These steps do not include the configuration of features such as duplex, alarms, and DNS.
For information about connection forwarding, see
Connection Forwarding.
Configuring a Dual SteelHead and Dual Layer-2 Switches Deployment
Figure 9‑16 shows a topology in which there are two routers, two Layer-2 switches, and two SteelHeads at the remote location. The client and the SteelHeads are all in the same subnet. The client uses the HSRP virtual IP as its default gateway (10.0.0.1).
In this environment, the in-path gateway on both SteelHeads must point to the HSRP virtual IP (10.0.0.1). You do not need to enable simplified routing because the client is on the same subnet as the SteelHead. You must configure connection forwarding between the two SteelHeads. The connection forwarding path must use the LAN interface of the SteelHeads.
Figure 9‑16. Dual SteelHeads, Dual Layer-2 Switches, Dual Router Deployment
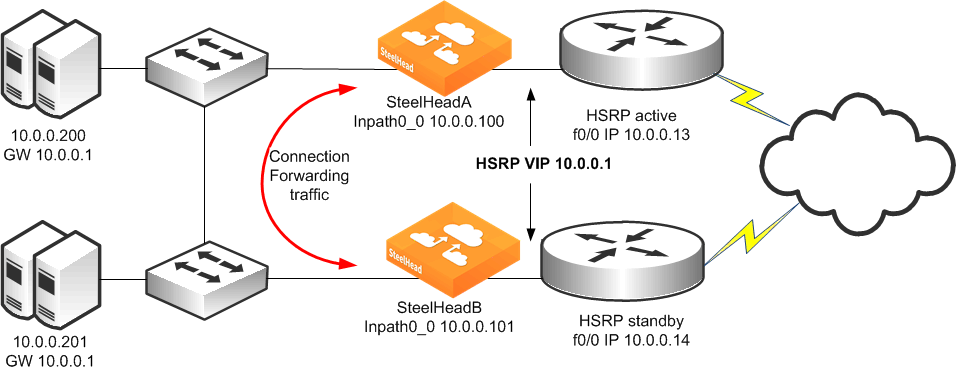
To configure dual SteelHeads, dual Layer-2 switches, and dual routers
On SteelHead A, connect to the CLI and enter the following commands:
in-path enable
interface inpath0_0 ip address 10.0.0.100 /24
ip in-path-gateway inpath0_0 10.0.0.1
in-path peering auto
in-path simplified routing dest-only
steelhead communication enable
steelhead name SteelHeadB main-ip 10.0.0.101
steelhead communication allow-failure
no interface inpath0_0 fail-to-bypass enable
On SteelHead B, connect to the CLI and enter the following commands:
in-path enable
interface inpath0_0 ip address 10.0.0.101 /24
ip in-path-gateway inpath0_0 10.0.0.1
in-path peering auto
in-path simplified routing dest-only
steelhead communication enable
steelhead name SteelHeadA main-ip 10.0.0.100
steelhead communication allow-failure
no interface inpath0_0 fail-to-bypass enable
Configuring a Dual SteelHead and Dual Layer-3 Switches Deployment
Figure 9‑17 shows a topology in which there are two routers, two Layer-3 switches, and two SteelHeads at the remote location. The clients and the SteelHeads are in different subnets. The clients use the Layer-3 switch as the default gateway. The Layer-3 switch does not having any routing protocols configured and relies on the default route to reach other subnets. The default route uses the HSRP IP address as the next hop.
In this environment, the in-path gateway on both SteelHeads must use the HSRP address of the Layer-3 switches as its default gateway (10.0.0.254) while configuring simplified routing to populate its table based on destination MAC address (CLI command: in-path simplified routing dest-only). You must configure connection forwarding between the two SteelHeads. The connection forwarding path must use the LAN interface of the SteelHeads.
Figure 9‑17. Dual SteelHeads, Dual Layer-3 Switches, Static Routing, Dual Router Deployment
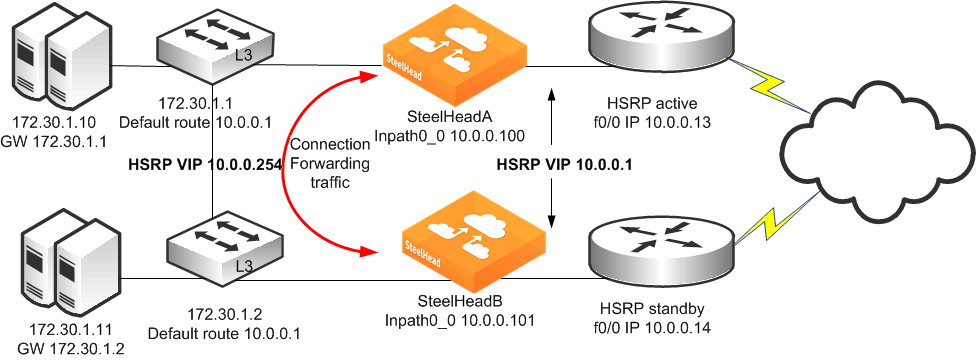
To configure dual SteelHeads, dual Layer-3 switches, static routing, and dual routers
On SteelHead A, connect to the CLI and enter the following commands:
in-path enable
interface inpath0_0 ip address 10.0.0.100 /24
ip in-path-gateway inpath0_0 10.0.0.254
in-path peering auto
in-path simplified routing dest-only
steelhead communication enable
steelhead name SteelHeadB main-ip 10.0.0.101
steelhead communication allow-failure
no interface inpath0_0 fail-to-bypass enable
On SteelHead B, connect to the CLI and enter the following commands:
in-path enable
interface inpath0_0 ip address 10.0.0.101 /24
ip in-path-gateway inpath0_0 10.0.0.254
in-path peering auto
in-path simplified routing dest-only
steelhead communication enable
steelhead name SteelHeadA main-ip 10.0.0.100
steelhead communication allow-failure
no interface inpath0_0 fail-to-bypass enable
Configuring a Dual SteelHead with Multiple In-Path Deployment
Figure 9‑18 shows a topology similar to
Figure 9‑17, but each router has two links going back to the Layer 3 switches totaling four links. Each link between the router and switch are independent /29 bit networks. You can configure dynamic routing protocols so that traffic can flow inbound or outbound. You can use this network design to prevent the loss of a single Layer-3 switch from cutting connectivity to the attached router. To ensure traffic is routed to the partner SteelHead during a failure, you can use the two in-path interfaces and deploy the SteelHeads in parallel, (requires larger model than 150, 250 or 550), with connection forwarding, and fail-to-block.
The clients and the SteelHeads are in different subnets and simplified routing is enabled (in-path simplified routing dest-only). To ensure connection forwarding traffic is sent to the LAN side, Riverbed recommends that you configure each in-path interface default gateway to point to the LAN side, the Layer 3 switch.
Figure 9‑18. Dual SteelHeads with Multiple In-Path Deployment
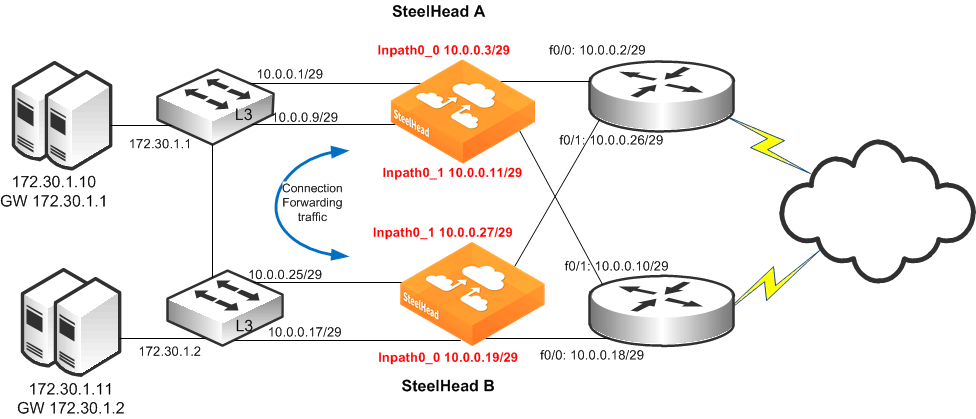
To configure dual SteelHeads with multiple in-path interfaces
On SteelHead A, connect to the CLI and enter the following commands:
in-path enable
in-path interface inpath0_0 enable
interface inpath0_0 ip address 10.0.0.3 /29
in-path interface inpath0_1 enable
interface inpath0_1 ip address 10.0.0.11 /29
ip in-path-gateway inpath0_0 10.0.0.1
ip in-path gateway inpath0_1 10.0.0.9
SteelHead
in-path peering auto
in-path simplified routing dest-only
SteelHead
SteelHead
steelhead communication enable
steelhead communication multi-interface enable
steelhead name SteelHeadB main-ip 10.0.0.19
steelhead name SteelHeadB additional-ip 10.0.0.27
steelhead communication allow-failure
no interface inpath0_0 fail-to-bypass enable
no interface inpath0_1 fail-to-bypass enable
On SteelHead B, connect to the CLI and enter the following commands:
in-path enable
in-path interface inpath0_0 enable
interface inpath0_0 ip address 10.0.0.19 /29
in-path interface inpath0_1 enable
interface inpath0_1 ip address 10.0.0.27 /29
ip in-path-gateway inpath0_0 10.0.0.17
ip in-path gateway inpath0_1 10.0.0.25
SteelHead
in-path peering auto
in-path simplified routing dest-only
SteelHead
SteelHead
steelhead communication enable
steelhead communication multi-interface enable
steelhead name SteelHeadA main-ip 10.0.0.3
steelhead name SteelHeadA additional-ip 10.0.0.11
steelhead communication allow-failure
no interface inpath0_0 fail-to-bypass enable
no interface inpath0_1 fail-to-bypass enable
You can configure and deploy routers in an endless number of variations, for example:
The links between Layer-3 switches and routers can be Layer-2 instead of separate Layer-3 networks. Layer-3 switches that are WAN distribution switches connected to a pair of core switches, then connected to other distribution switches before connecting to the end hosts. Instead of two routers, you can use four routers connecting to various WAN providers for a total of eight connections to the Layer-3 switches. You can use static routes, or any number of routing protocols, to balance traffic across multiple paths. Regardless of the variations, the same deployment logic applies. The SteelHeads must cover all the desired paths of traffic to be optimized. You can use up to 10 supported in-path interfaces on the larger SteelHeads. If you have parallel SteelHeads, follow the same simplified routing and connection forwarding guidelines in this section. For information about serial clusters, see
Serial Cluster Deployments.










