Fixed-Target In-Path Rules
A fixed-target in-path rule enables you to manually specify a remote SteelHead for optimization. As with all in-path rules, fixed-target in-path rules are executed only for SYN packets, and therefore are configured on the initiating or client-side SteelHead. This section includes the following topics:
Configuring a Fixed-Target In-Path Rule for an In-Path DeploymentFixed-Target In-Path Rule for an Out-of-Path DeploymentFor information about in-path rules, see
In-Path Rules.
You can use fixed-target in-path rules in environments where the auto-discovery process cannot work. SteelHead DX does not peer with other SteelHead models with neither auto-discovery nor if explicitly configured by in-path rules.
A fixed-target rule requires the input of at least one target SteelHead; you can also specify an optional backup SteelHead.
Fixed-target in-path rules have several disadvantages compared to auto-discovery:
You cannot easily determine which subnets to include in the fixed-target rule.Ongoing modifications to rules are needed as new subnets or SteelHeads are added to the network.Currently, you can specify two remote SteelHeads. All traffic is directed to the first SteelHead until it reaches capacity, or until it stops responding to requests to connect. Traffic is then directed to the second SteelHead (until it reaches capacity, or until it stops responding to requests to connect).Because of these disadvantages, fixed-target in-path rules are not as desirable as auto-discovery. In general, use fixed-target rules only when you cannot use auto-discovery.
LAN data flow has a significant difference depending on whether the fixed-target (or backup) IP address specified in the fixed-target in-path rule is for a SteelHead primary interface or its in-path interface.
Configuring a Fixed-Target In-Path Rule for an In-Path Deployment
In environments where the auto-discovery process does not work, use fixed-target in-path rules to target a remote in-path (physical or virtual) SteelHead. Configure the fixed-target in-path rule to target the remote SteelHead in-path interface.
Examples of environments where the auto-discovery process does not work are as follows:
Traffic traversing the WAN passes through a satellite or other device that strips off TCP options, including those used by auto-discovery.Traffic traversing the WAN goes through a device that proxies TCP connections and uses its own TCP connection to transport the traffic. For example, some satellite-based WANs use built-in TCP proxies in their satellite uplinks.When the target IP address of a fixed-target in-path rule is a SteelHead in-path interface, the traffic between the server-side SteelHead and the server looks like client-to-server traffic; that is, the server detects connections coming from the client IP address. This process is the same as when auto-discovery is used.
Figure 1‑13 shows how to use a fixed-target in-path rule to the SteelHead in-path interface. This example uses a fixed-target in-path rule to resolve an issue with a satellite. The satellite gear strips the TCP option from the packet, which means the SteelHead does not detect the TCP option, and the connection cannot be optimized.
To enable the SteelHead to detect the TCP option, you configure a fixed-target in-path rule on the initiating SteelHead (SteelHead A) that targets the terminating SteelHead (SteelHead B) in-path interface.
Figure 1‑13. Fixed-Target In-Path Rule to the SteelHead In-Path Interface
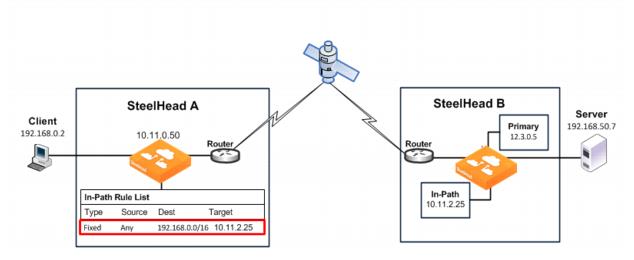
The fixed-target in-path rule specifies that only SYN packets destined for 192.168.0.0/16, SteelHead B subnets, are allowed through to the Site B SteelHead. All other packets are passed through the SteelHead.
You can configure in-path rules using the CLI.
To configure fixed-target in-path rule to an in-path address
On SteelHead A, connect to the CLI and enter the following commands:enable
configure terminal
in-path rule fixed-target target-addr 10.11.2.25 dstaddr 192.168.0.0/16 rulenum end
Fixed-Target In-Path Rule for an Out-of-Path Deployment
When you enable the remote SteelHead for out-of-path deployment, use fixed-target in-path rules to target the primary IP address. The most important caveat to this deployment method is that traffic to the remote server no longer uses the client IP address. Instead, the server detects connections coming to it from the out-of-path SteelHead primary IP address.
For deployment examples, see
Out-of-Path Deployments.


