Controlling Optimization
You can configure what traffic a SteelHead optimizes and what other actions it performs, using the following:
In-path rules - In-path rules determine the action a SteelHead takes when a connection is initiated, usually by a client.Peering rules - Peering rules determine how a SteelHead reacts when it detects a probe query.This section includes the following topics:
In-Path RulesDefault In-Path RulesPeering RulesKickoff and Automatic Kickoff FeaturesIn-Path Rules
In-path rules are used only when a connection is initiated. Because connections are typically initiated by clients, in-path rules are configured for the initiating, or client-side, SteelHead. In-path rules determine SteelHead behavior with SYN packets.
In-path rules are an ordered list of fields that a SteelHead attempts to match with SYN packet fields (for example, source or destination subnet, IP address, VLAN, or TCP port). Each in-path rule has an action field. When a SteelHead finds a matching in-path rule for a SYN packet, the SteelHead treats the packet according to the action specified in the in-path rule.
The in-path rule actions, each with different configuration possibilities, are as follows:
Auto - Uses the auto-discovery process to determine if a remote SteelHead is able to optimize the connection that this SYN packet.Pass - Allows the SYN packet to pass through the SteelHead. No optimization is performed on the TCP connection initiated by this SYN packet is trying to initiate.Fixed-Target - Omits the auto-discovery process and instead uses a specified remote SteelHead as an optimization peer. Fixed-target rules require the input of at least one remote target SteelHead; you can specify an optional backup SteelHead. Deny - Drops the SYN packet and sends a message back to its source.Discard - Drops the SYN packet silently.Only use in-path rules in the following scenarios:
TCP SYN packet arrives on the LAN interface of physical in-path deployments. TCP SYN packet arrives on the WAN interface of virtual in-path deployments. Again, both of these scenarios are associated with the first, or initiating, SYN packet of the connection. In-path rules are applicable to only the client-side SteelHead. In-path rules have no effect on connections that are already established, regardless of whether the connections are being optimized.
In-path rule configurations differ depending on the action. For example, both the fixed-target and the auto-discovery actions allow you to choose configurations such as what type of optimization is applied, what type of data reduction is used, and what type of latency optimization is applied.
For an example of how in-path rules are used, see
Configuring High-Bandwidth, Low-Latency Environment.
Default In-Path Rules
The SteelHead ships with three default in-path rules. Default rules pass through certain types of traffic unoptimized because these protocols (telnet, SSH, HTTPS) are typically used when you deploy and configure your SteelHeads. The default in-path rules can be removed or overwritten by altering or adding other rules to the in-path rule list, or by changing the port groups that are used. The default rules allow the following traffic to pass through the SteelHead without attempting optimization:
Encrypted Traffic - Includes HTTPS, SSH, and others.Interactive Traffic - Includes telnet, ICA, and others. Riverbed Protocols - Includes the TCP ports used by Riverbed products (that is, the SteelHead, the SteelHead Interceptor, and the Mobile Controller).Peering Rules
Peering rules control SteelHead behavior when the appliance detects probe queries.
Peering rules (displayed using the show in-path peering rules CLI command) are an ordered list of fields that a SteelHead uses to match with incoming SYN packet fields (for example, source or destination subnet, IP address, VLAN, or TCP port) and with the in-path IP address of the probing SteelHead. If more than one in-path interface exists on the probing SteelHead, apply one peering rule for each in-path interface. Peering rules are especially useful in complex networks.
Peering rule actions are as follows:
Pass - The receiving SteelHead does not respond to the probing SteelHead, and allows the SYN+probe packet to continue through the network.Accept - The receiving SteelHead responds to the probing SteelHead and becomes the remote-side SteelHead (that is, the peer SteelHead) for the optimized connection.Auto - If the receiving SteelHead is not using enhanced auto-discovery, this has the same effect as the Accept peering rule action. If enhanced auto-discovery is enabled, the SteelHead becomes the optimization peer only if it is the last SteelHead in the path to the server. If a packet does not match any peering rule in the list, the default rule applies.
Kickoff and Automatic Kickoff Features
The kickoff feature provides you with a simple way to ensure that unoptimized active TCP connections passing through the SteelHead can be reset. When a connection is reset, it tries to reestablish itself using the SYN, SYN-ACK, ACK handshake. The SteelHead uses its in-path rule table to determine if the connection should be optimized.
For more information about in-path rules, see
In-Path Rules.
Connections can pass through a SteelHead unoptimized when they are set up and active before the SteelHead optimization service is running. By default, the SteelHead does not reset legacy connections and reports them as preexisting.
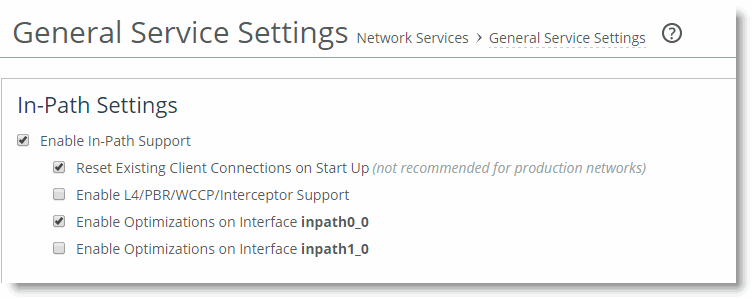
The main difference between the auto kickoff feature and the kickoff feature is that kickoff has a global setting that can affect all existing connections passing through a SteelHead. The global setting sends a reset to all connections, regardless of whether they need one. The global setting is not recommended for production networks, but you can use it in lab test scenarios. By default, this setting is not enabled. You can enable this setting in the Management Console, or with the CLI command in-path kickoff.
The automatic kickoff feature is included in RiOS v6.1 or later.
Figure 1‑5. The Automatic Kickoff Feature Global Setting
You can reset individual connections manually on the SteelHead. This forces an existing connection from optimized to pass-through, or visa-versa, when you test a new rule in the SteelHead's in-path rule table. You can also use manual reset for diagnostic purposes. You can set this feature on the Current Connections page in the Management Console, or with the tcp connection send pass-reset commands.
If you configure the automatic kickoff feature, when a SteelHead comes out of bypass mode, it automatically resets (by sending RST to the client and server) only the preexisting TCP connections that match in-path rules for which automatic kickoff is enabled.
If automatic kickoff and the global kickoff feature are both enabled on the same SteelHead, the global kickoff setting takes precedence.
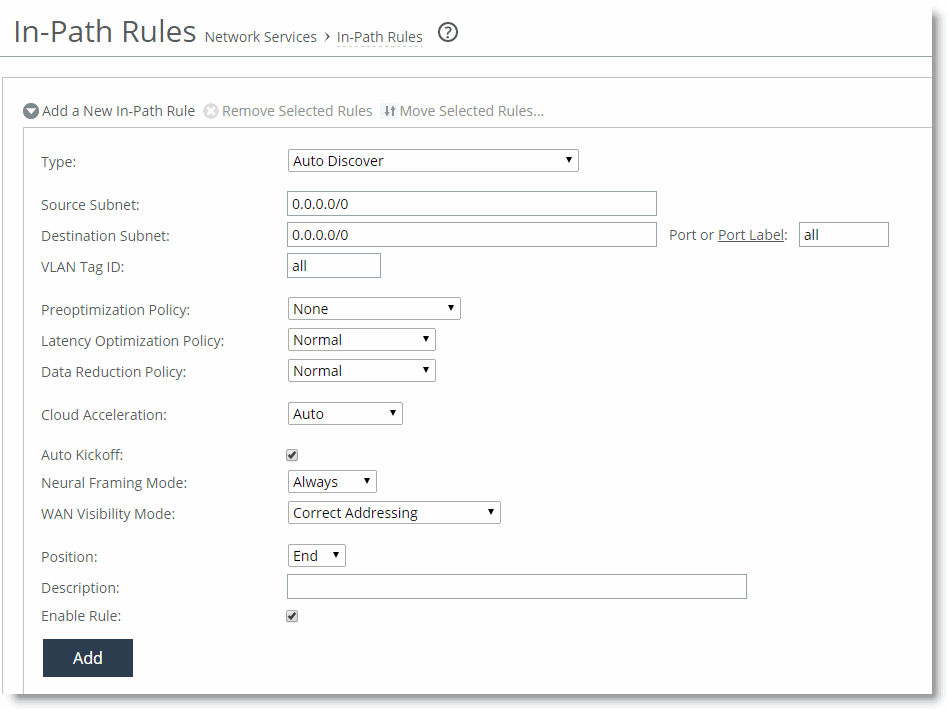
One of the reasons to use the automatic kickoff feature instead of the kickoff feature is that you can enable it as part of an in-path rule for optimization (
Figure 1‑6). Automatic kickoff is only available for auto-discovery and fixed-target rules. When you enable automatic kickoff as part of an in-path rule, and the rule matches packet flow for a preexisting connection, the individual connection is reset automatically. Connections that are preexisting and do not match an in-path rule with automatic kickoff enabled are unaffected. If you add a new rule with automatic kickoff, any preexisting connection that matches the new rule is not affected until the next service restart.
Figure 1‑6. Enable Automatic Kickoff
You use automatic kickoff primarily when you deploy SteelHeads in data protection environments. In data protection deployments, connections carrying the data replication traffic between the two storage arrays are often long-lived. This poses a problem if the connections are established as unoptimized or pass-through (for example, if the SteelHead is offline during connection setup), because the connections can remain unoptimized for a long time. Without the automatic kickoff on a SteelHead, you must manually intervene to reset the connections carrying data replication traffic on one of the storage arrays.
For more information about data protection deployment, see
Data Protection Deployments.
Although you can use automatic kickoff for any type of optimizable connection, the majority of connections for office applications—Web, email, and so on—are comparatively short-lived and begin to be optimized after a brief period of time without any need for a reset.
When using the automatic kickoff feature, be aware of the following:
Automatic kickoff does not have a timer. A preexisting connection that remains inactive for a period of time is reset as soon as there is packet flow and it matches an in-path rule that has auto kickoff enabled. After the connection has been reset, an internal flag is set to prevent further kick offs for the connection unless the optimization service is restarted.
Take note when you enable automatic kickoff to make sure you do not cause undesired behavior.For example, in a design in which there is network asymmetry, if one or more SteelHead neighbors are configured and an in-path rule with automatic kickoff matches the connection, then the connection is kicked off even after detecting only one side of the handshake conversation.
For information about configuring the automatic kickoff feature, see the Riverbed Command-Line Interface Reference Manual and SteelHead Management Console User’s Guide.



