Application Flow Engine
This section includes the following topics:
Overview of Application Flow EngineAFE and Microsoft Lync 2010 and 2013Overview of Application Flow Engine
The Riverbed Application Flow Engine (AFE), QoS can identify applications accurately using a variety of technologies. It is a powerful engine that you can use to automatically detect applications on the network. You can also use AFE in QoS and path selection rules, in application definitions, and the application visibility reporting. In RiOS v9.1 and later, AFE can identify over 1300 applications and protocols.
Examples of technologies the AFE uses are:
Application signature/Pattern matchingMatch well-known byte patterns in a flow and across multiple packetsMatch the URL within HTTPProtocol dissection/Protocol awarenessLayer-7 fluency to following the conversationBehavioral classification/Heuristic classificationAnalyses packet size, packet inter-arrival time, packet rate, data rate, and calculates entropy (randomness) to detect an application (for example, Skype)Dynamic decodeUndoing obfuscation techniques (for example, base64)If the AFE fails to identify the application based on the above technologies, it falls back to a TCP/UDP port-based classification.
To view a completed global application list, see the SteelHead Management Console User’s Guide.
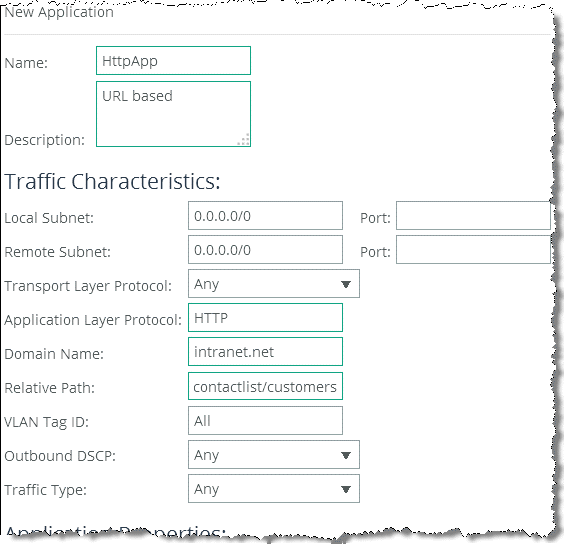
In addition to the AFE supporting many well-known applications, you can add rules to identify custom applications. For example, you can identify a new HTTP application based on specific domain name or relative path (
Figure 5‑7).
Figure 5‑7. Rules to Identify Applications
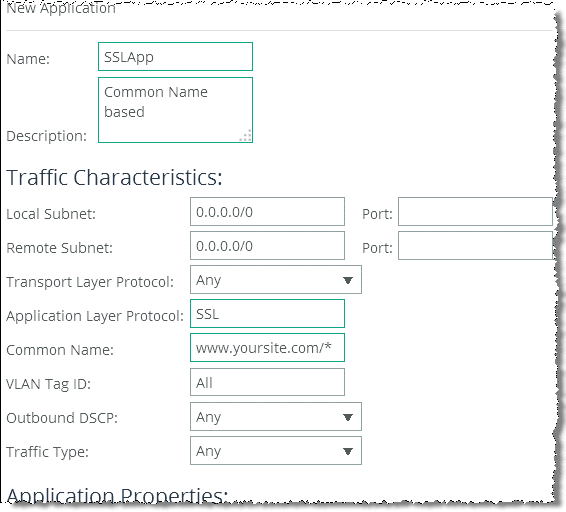
With RiOS v8.6 or later, you can use the AFE to classify unoptimized SSL traffic based on the TLS/SSL server common name in the server certificate. To do this, add an application, type SSL in the Application Layer Protocol text box, and type the common name of the server certificate (for example, www.yoursite.com/*) in the Common Name field. To make the configuration easier, you can use wildcards in the name (
Figure 5‑8).
Figure 5‑8. SSL Common Name Matching Configuration
You cannot classify SSL optimized traffic using the common name control. For optimized or decrypted SSL traffic, the AFE uses the same techniques as nonencrypted traffic to classify the traffic.
For information about defining an application using the AFE, see
Applications. For more information about SSL, see the
SteelHead Deployment Guide - Protocols.
AFE and Microsoft Lync 2010 and 2013
RiOS v9.1 and later enhances support for Microsoft Lync. Lync is a multiple-feature communication suite that carries traffic over an extensive selection of protocols. The AFE classification of Lync traffic covers the majority of traffic generated between Lync clients and Lync servers.
The following table summarizes the types of traffic Lync generates and the classification the AFE provides for them:
Workload | Classified As |
Client login | LYNC, LYNCCTRL |
Chat message | LYNC, LYNCCTRL |
File transfer | LYNC, LYNCSHRE |
Group voice chat | LYNC, LYNCMDIA |
Video call | LYNC, LYNCMDIA |
Application screen sharing | LYNC, LYNCSHRE |
Desktop sharing | LYNC, LYNCSHRE |
Voice call | LYNC, LYNCMDIA |
Presentation sharing | SSL, SIP |
White-board session | SSL, SIP |
A Lync server uses the default SIP port of TCP 5061. You can use this information to build a custom rule to classify Lync SIP traffic.



