Configuring a management ACL
You can secure access to a SteelHead using an internal management access control list (ACL) in the Security: Management ACL page.
SteelHeads are subject to the network policies defined by a corporate security policy, particularly in large networks. Using an internal management ACL, you can:
• restrict access to certain interfaces or protocols of a SteelHead.
• restrict inbound IP access to a SteelHead, protecting it from access by hosts that don’t have permission without using a separate device (such as a router or firewall).
• specify which hosts or groups of hosts can access and manage a SteelHead by IP address, simplifying the integration of SteelHeads into your network.
The management ACL provides these safeguards to prevent accidental disconnection from the SteelHead and the SCC:
• It detects the IP address you are connecting from and displays a warning if you add a rule that denies connections to that address.
• It always allows the default SteelHead ports 7800, 7801, 7810, 7820, and 7850.
• It always allows a previously connected SCC to connect and tracks any changes to the IP address of the SCC to prevent disconnection.
• It converts well-known port and protocol combinations such as SSH, Telnet, HTTP, HTTPS, SNMP, and SOAP into their default management service and protects these services from disconnection. For example, if you specify protocol 6 (TCP) and port 22, the management ACL converts this port and protocol combination into SSH and protects it from denial.
• It tracks changes to default service ports and automatically updates any references to changed ports in the access rules.
To set up a management ACL
1. Choose Administration > Security: Management ACL to display the Management ACL page.
Management ACL page
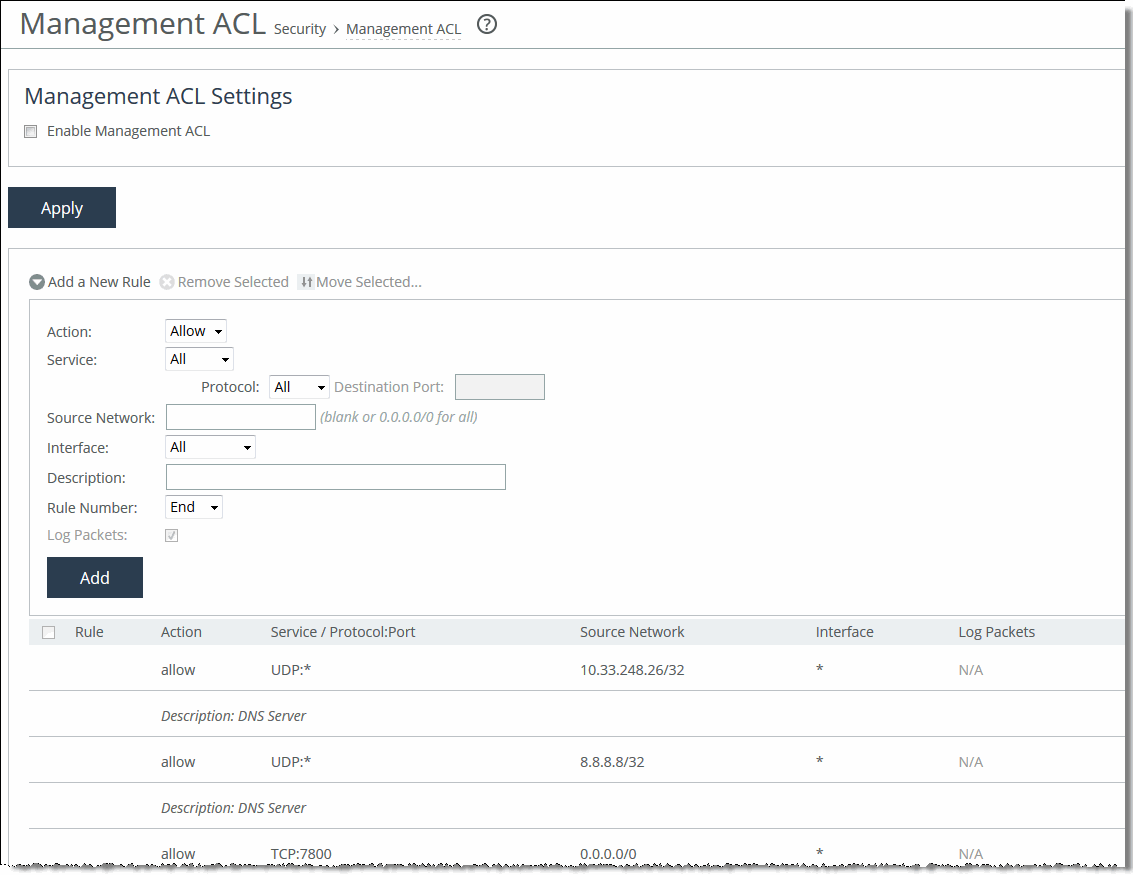
2. Under Management ACL Settings, complete the configuration as described in this table.
Control | Description |
Enable Management ACL | Secures access to a SteelHead using a management ACL. |
3. Click Apply to apply your changes to the running configuration.
4. Click Save to Disk to save your settings permanently.
If you add, delete, edit, or move a rule that could disconnect connections to the SteelHead, a warning message appears. Click Confirm to override the warning and allow the rule definition. Use caution when overriding a disconnect warning.
ACL management rules
The management ACL contains rules that define a match condition for an inbound IP packet. You set a rule to allow or deny access to a matching inbound IP packet. When you add a rule on a SteelHead, the destination specifies the SteelHead itself, and the source specifies a remote host.
The ACL rules list contains default rules that allow you to use the management ACL with DNS caching. These default rules allow access to certain ports required by this feature. The list also includes default rules that allow access to the SCC. If you delete a default ACL rule and need to restore it, see
To restore the default ACL management rule for DNS caching.
To add an ACL management rule
1. Under Management ACL Settings, complete the configuration as described in this table.
Control | Description |
Add a New Rule | Displays the controls for adding a new rule. |
Action | Select one of these rule types from the drop-down list: • Allow—Allows a matching packet access to the SteelHead. This is the default action. • Deny—Denies access to any matching packets. |
Service | Optionally, select Specify Protocol, or HTTP, HTTPS, SOAP, SNMP, SSH, Telnet. When specified, the Destination Port is dimmed. |
Protocol | (Appears only when Service is set to Specify Protocol.) Optionally, select All, TCP, UDP, or ICMP from the drop-down list. The default setting is All. When set to All or ICMP, the Service and Destination Ports are dimmed. |
Source Network | Optionally, specify the source subnet of the inbound packet: for example, 1.2.3.0/24. |
Destination Port | Optionally, specify the destination port of the inbound packet, either a single port value or a port range of port1-port2, where port1 must be less than port2. Leave it blank to specify all ports. |
Interface | Optionally, select an interface name from the drop-down list. Select All to specify all interfaces. |
Description | Optionally, describe the rule to facilitate administration. |
Rule Number | Optionally, select a rule number from the drop-down list. By default, the rule goes to the end of the table (just above the default rule). SteelHeads evaluate rules in numerical order starting with rule 1. If the conditions set in the rule match, then the rule is applied, and the system moves on to the next packet. If the conditions set in the rule don’t match, the system consults the next rule. For example, if the conditions of rule 1 don’t match, rule 2 is consulted. If rule 2 matches the conditions, it’s applied, and no further rules are consulted. The default rule, Allow, which allows all remaining traffic from everywhere that has not been selected by another rule, can’t be removed and is always listed last. |
Log Packets | Tracks denied packets in the log. By default, packet logging is enabled. |
Add | Adds the rule to the list. The Management Console redisplays the Rules table and applies your modifications to the running configuration, which is stored in memory. |
Remove Selected | Select the check box next to the name and click Remove Selected. |
Move Selected | Moves the selected rules. Click the arrow next to the desired rule position; the rule moves to the new position. |
2. Click Save to Disk to save your settings permanently.
Usage notes
• When you change the default port of services such as SSH, HTTP, HTTPS, on either the client-side or server-side SteelHead and create a management ACL rule denying that service, the rule will not work as expected. The SteelHead on the other end (either server or client) of an in-path deployment doesn’t know that the default service port has changed, and consequently optimizes the packets to that service port. To work around this problem, add a pass-through rule to the client-side SteelHead for the management interfaces. The pass-through rule prevents the traffic from coming from the local host when optimized.
• A management ACL rule that denies access from port 20 on the server-side SteelHead in an out-of-path deployment prevents data transfer using active FTP. In this deployment, the FTP server and client can’t establish a data connection because the FTP server initiates the SYN packet and the management rule on the server-side SteelHead blocks the SYN packet. To work around this problem:
—or—
– add a rule to either allow source port 20 on the server-side SteelHead or allow the IP address of the FTP server.
To restore the default ACL management rule for DNS caching
1. Under Management ACL Settings, add a DNS Caching ACL rule with these properties.
Property | Value |
Type | Allow |
Protocol | UDP |
Destination Port | 53 |
Rule Number | 1 |
Description | DNS Caching |
2. Click Add.


