Configuring SaaS Acceleration
You configure SaaS acceleration through the SaaS Accelerator Manager (SAM) as well as the client-side appliance. After you configure the environment, you configure applications for SaaS acceleration. SAM version 1.1.0 and later together with client-side applications running RiOS 9.9.2 and later simplifies the process of configuring applications for acceleration by grouping related applications such as those in Microsoft Office 365 into bundles. You configure one in-path rule for the bundle and it applies to all applications in the bundle.
This chapter includes these sections:
Before you begin
Before you begin, ensure you have a license for the SaaS Accelerator and your environment meets these requirements:
•SteelHeads require version 9.8.1a software or later.
•SteelFusion Edges require version 6.0.2 or later.
•SAM requires version 1.1.0 or later.
•SteelCentral Controller for SteelHead Mobile (Mobile Controller) requires version 6.1.1a or later.
•SteelCentral Controller for SteelHead (SCC) requires version 9.9.1 or later.
Licensing SaaS Accelerator Manager for SaaS Accelerator
When you purchase SaaS Accelerator, Riverbed emails you a license token that you need to redeem through SaaS Accelerator Manager (SAM).
To install your licenses for SaaS acceleration
1. Sign in to the SAM that will manage the SaaS acceleration.
2. Choose Configure > Licenses and click Redeem Token.
The Redeem Token dialog box appears.
Redeem Token dialog box
3. Enter the token and click Submit.
The SaaS Accelerator pages are now available, and you can review your license details on the Configure > Licenses page. Click the license serial number to show the details.
License details
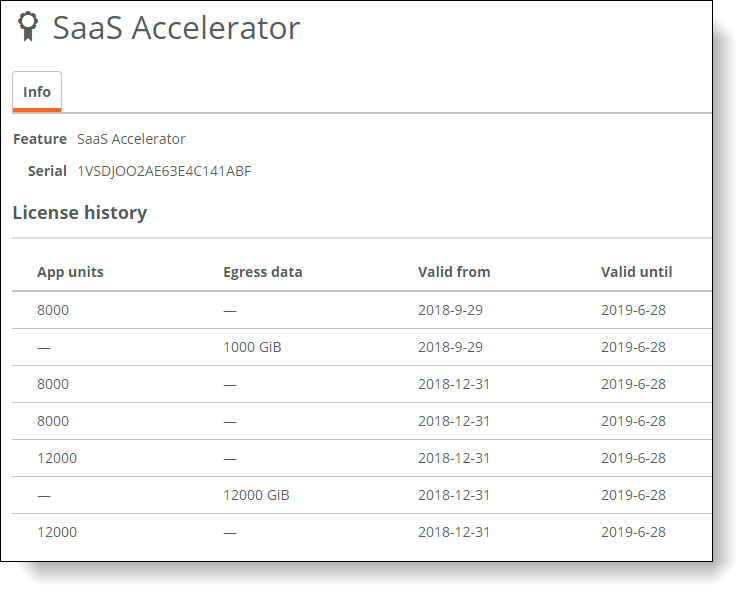
Configuring SSL optimization
SSL optimization is required for SaaS acceleration, and you need to generate a root CA (RCA) certificate—or an intermediate CA (ICA) certificate if you plan to use your organization’s CA—before you can configure SaaS acceleration. In the default configuration, Riverbed manages the RCA, but you must generate an RCA certificate and deploy that certificate into the Trusted Root Certificate Authority certificate store on your clients. The RCA then automatically generates trusted certificates to sign optimized TLS/SSL traffic. When you choose to use your organization’s CA, you must generate a certificate signing request (CSR) for an ICA certificate, which is signed by your organization’s CA that is already trusted by your clients. You upload the signed ICA certificate to SAM.
SAM uses the RCA, or ICA, certificate to sign proxy certificates, which it pushes to the SaaS service cluster. You also need to install this certificate from SAM on each client system. The SaaS service cluster and the client-side appliance use their peering certificates to form a trust relationship.
When a client-side appliance is moved to the SAM whitelist, SAM pushes the peering certificate signed by the CA to the client-side appliance and the client-side appliance uploads its peering certificate to SAM, which SAM pushes to the service cluster, completing the trust relationship between the client-side appliance and the SaaS service cluster.
SSL optimization with peering certificates
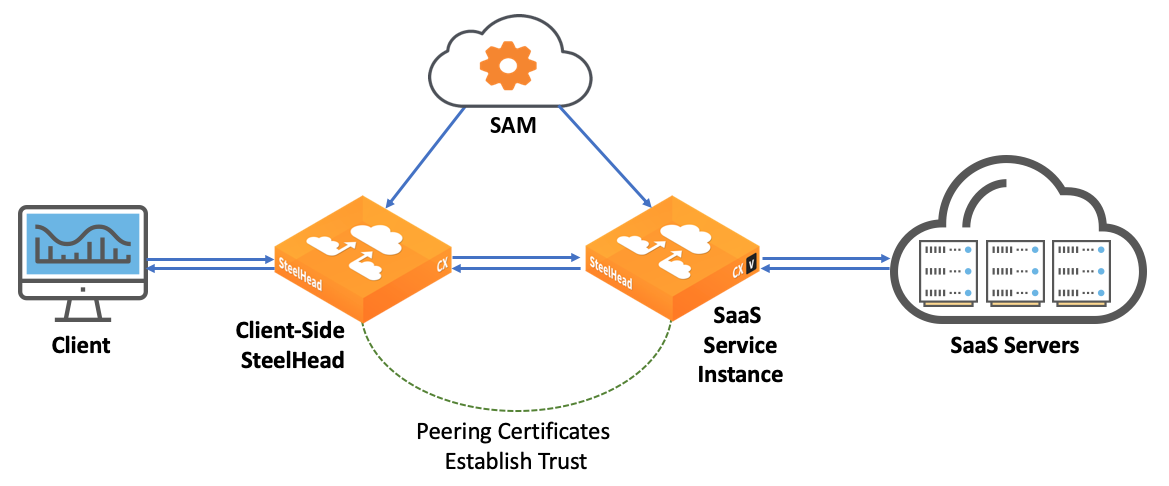
If there are any changes to the CA certificate, SAM automatically updates the client-side appliance and the SaaS service cluster to maintain the trust relationship.
SAM users with read-only permissions are not allowed to generate certificates or configure SaaS acceleration.
To enable automatic signing and generate either an RCA certificate or CSR
1. In SAM, choose Configure > SSL Optimization and select the Certificate Authority tab.
2. Do one of these actions:
–Select the Riverbed Managed tab and then click Generate Root CA Certificate.
–Select the Customer Managed tab and then click Generate CSR.
The Generate Root CA Certificate, or Generate CSR, dialog box appears.
Generate Root CA Certificate dialog box
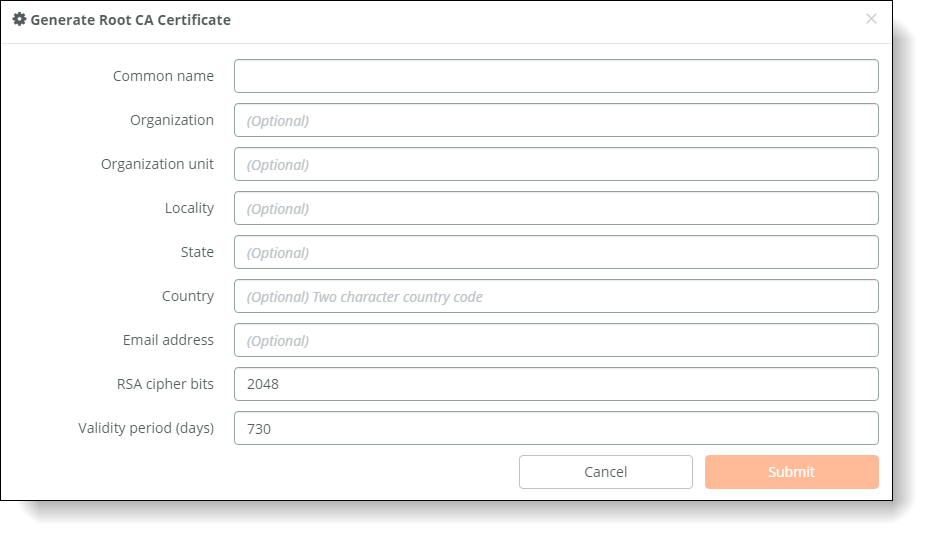
3. Provide the following information.
The Generate Root CA Certificate has an extra field where you must specify how many days the certificate is valid.
Field | Description |
Common name | Specify the common name of the root CA certificate. |
Organization | Optionally, specify the organization name (for example, the company). |
Organization unit | Optionally, specify the organization unit name (for example, the section or department). |
Locality | Optionally, specify the city. |
State | Optionally, specify the state. |
Country | Optionally, specify the country (2-letter code only). |
Email address | Optionally, specify the email address of the contact person. |
RSA cipher bits | Select the key length from the drop-down list. The default value is 2048. |
Validity period (days) Riverbed Managed only | Specify how many days the root CA certificate is valid. The default value is 730 days (two years). |
4. Click Submit.
SAM creates the root CA certificate or the CSR depending on your chosen configuration.
5. A CA certificate automatically becomes active when you are using an RCA, or ICA, only. If an RCA is currently active and you want to switch to an ICA, you must manually activate the ICA after you upload the signed CSR. To manually activate the ICA, choose Configure > SSL Optimization and select the Certificate Authority tab and then the Customer Managed tab and click On under Status for the ICA you want to use.
6. Copy or download the root CA certificate or the signed CSR from SAM and install it in end-user client systems.
Copy or download the root CA certificate
An active Root Certificate Authority (CA) enables clients to accelerate SaaS traffic when SaaS applications are configured on the SaaS Accelerator page. The root CA certificate needs to be deployed into the Trusted Root Certification Authority certificate store on your clients and then your clients can automatically use certificates issued by this trusted root CA to accelerate encrypted SaaS traffic.
To delete the certificate
1. In SAM, choose Configure > SSL Optimization.
2. Select the certificate or CSR and select Actions > Delete Root CA Certificate/CSR.
You are prompted to confirm this action.
3. Click Confirm.
The root CA certificate or CSR is removed from the system and new SaaS connections will not be accelerated.
Configuring SaaS applications for acceleration
After you have licensed the SaaS Accelerator and configured SSL optimization, you can set up acceleration for SaaS applications.
To configure SaaS applications for acceleration
1. In SAM, choose Configure > SaaS Accelerator and click Accelerate Application.
The Accelerate Application pane appears.
Configuring applications for SaaS acceleration
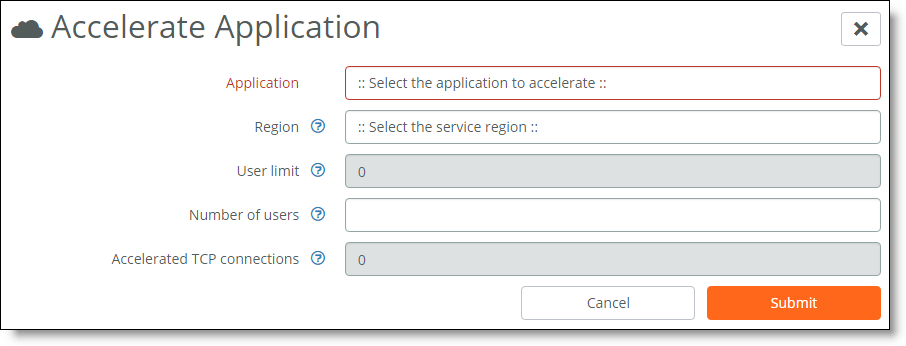
2. Select the application from the drop-down list.
3. Select the region from the drop-down list.
For best performance, select the region closest to the data for the SaaS application. Once you deploy to a specific region, you cannot change it unless you delete the deployed application and set it up again with a different region.
4. Enter the number of Active Users.
Each application has a minimum and maximum number of users. SAM provides guidelines for the limits as you type numbers in the field.
SAM uses the number of users to calculate the capacity of service instances in the SaaS service cluster based on the type of application.
SAM calculates the user limit based on the number of users, the application, and the available AppUnits.
We recommend that you carefully select the number of users for your business needs. Once deployed, you can change the number of users; however, when you change the number of users, the acceleration feature is unavailable for up to 30 minutes while the service cluster updates.
5. Click Submit.
This creates the SaaS service cluster dedicated to accelerating traffic for this application.
Deployment can take up to 20 minutes, and you cannot edit the configuration while the configuration is in process.
When deployed, you see the SaaS application, the service endpoint, and service status. The service status appears as a green check mark when deployed and ready for optimization.
Status for deployed application
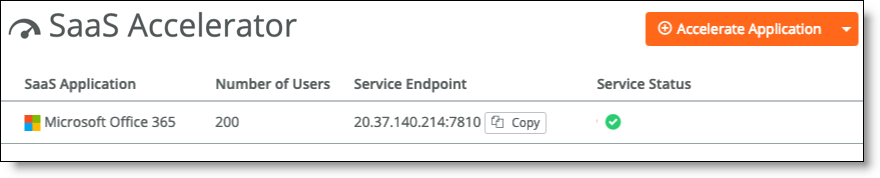
6. As needed, open port 7810 for the service endpoint IP address on your firewall.
The SaaS service cluster and client-side appliances need to be able to connect to this location.
To stop SaaS acceleration for an application
1. Choose Configure > SaaS Accelerator and click the application to stop accelerating.
2. From the Actions drop-down list, select Terminate SaaS acceleration.
3. When prompted, click Confirm.
When you terminate SaaS acceleration for an application, you remove the SaaS service cluster that was deployed in the cloud to support the acceleration.
Configuring SaaS acceleration on the client-side appliance
When you have configured SAM for SaaS acceleration, you can configure client-side appliances.
To configure a client-side appliance for acceleration
1. In SAM, choose Configure > SaaS Client Appliances and copy the registration token.
2. On the appliance, choose Optimization > SaaS: SaaS Accelerator and add these values:
–SaaS Accelerator Manager Hostname.
–SaaS Accelerator Manager Port. The client-side appliance uses port 3900 from the primary interface to communicate with SAM and the port needs to be open on the branch firewall. The field for the port number is editable but we recommend not changing the value.
–Registration Token. Paste the registration token you copied in
Step 1 into this field.
3. Click Register.
When the registration process completes, the registration details and a helpful list of remaining configuration tasks appear on the page. Completed tasks are prefaced by a check mark.
A new SaaS Acceleration section appears on the page, and you can view the current status and monitor acceleration status.
4. Enable SSL optimization on the appliance.
Choose Optimization > SSL Main Settings, and in the General SSL Settings area select Enable SSL Optimization and click Apply.
5. In SAM, move this appliance to the whitelist.
Newly added appliances always appear on the graylist in the Access List column. You need to move their status to the whitelist to allow acceleration.
Choose Configure > Client Appliances and select the appliance serial number to display the details pane.
Under Access List, select Whitelist from the Access list drop-down list and click
Submit. For more information, see
Controlling appliance access.
6. Enable SaaS acceleration on this client-side appliance. Choose Optimization > SaaS: SaaS Accelerator, select Enable Acceleration, and click Apply.
7. Add an in-path rule to accelerate SaaS applications.
The in-path rule is application, or application bundle, based and lets the client-side appliance connect to the service endpoint of the SaaS service cluster deployed for the selected application.
Choose Optimization > Network Services: In-Path Rules and click Add a New In-Path Rule. For the Source subnet, select All IPv4. For the Destination Subnet, select SaaS Application. A second menu appears to the right. In the second menu, select a SaaS application, or application bundle, for acceleration. (Note: Only applications, and application bundles set up for SaaS acceleration on SAM appear in the list.) Click Add.
SaaS in-path rule
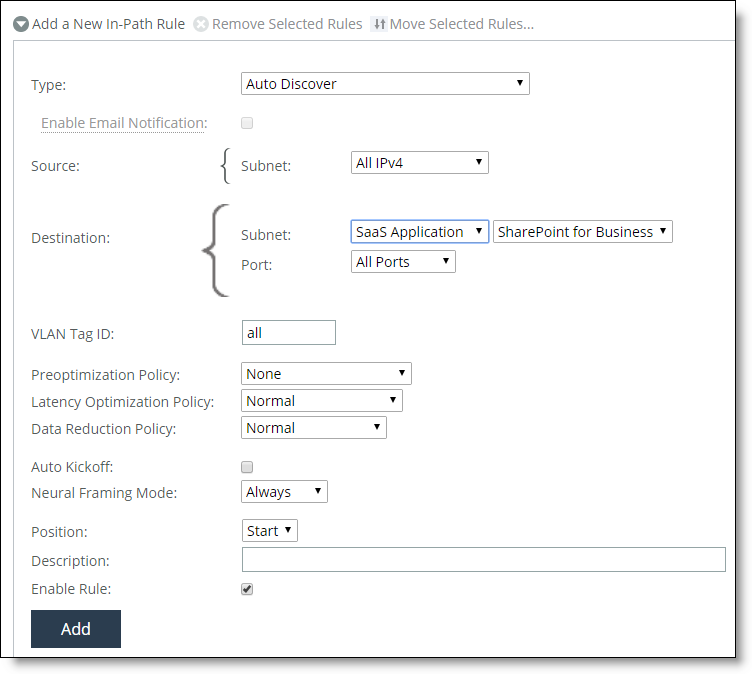
For more information about in-path rules, see the SteelHead User Guide.
8. Click Save to Disk to save your settings permanently.
Pausing and Canceling SaaS acceleration on client-side appliances
Canceling SaaS acceleration for an appliance entails deregistering the appliance from SAM, which removes appliance-related peering certificates and in-path rules. Pausing acceleration does not remove configuration settings, so you can easily restore the service when you want.
To pause SaaS acceleration on client-side appliances
1. On the appliance, choose Optimization > SaaS: SaaS Accelerator.
2. Clear the Enable Acceleration check box and click Apply.
When paused, all related in-path rules are ignored.
To cancel SaaS acceleration on client-side appliances
1. On the appliance, choose Optimization > SaaS: SaaS Accelerator.
2. Click Deregister.
SaaS acceleration is canceled for this appliance and acceleration-related settings, including in-path rules, are removed.
As another option, you can move the appliance to the blacklist on SAM. When you move an appliance to the blacklist, SAM removes the peering CA that it uploaded from the appliance and stops acceleration. For details, see
“Controlling appliance access” on page 33.Configuring SaaS acceleration on multiple appliances using SCC
In SCC 9.9.1 and later, you can configure SaaS acceleration on managed appliances. SaaS Accelerator requires a license, which is installed on SAM.
We strongly recommend that you configure and push SaaS acceleration policies from an SCC to the managed appliances, particularly in large-scale deployments and production networks with multiple appliances.
To accelerate SaaS application traffic using your managed appliances, register your SCC with an SAM that is set up for SaaS acceleration. After registering the SCC with SAM, register selected appliances or a group of appliances with SAM.
To configure multiple appliances for SaaS acceleration using SCC
1. On SAM, choose Configure > Client Appliances and copy the registration token.
2. On the SCC, choose Administration > SaaS: SaaS Accelerator Manager Registration and add these values:
–SaaS Accelerator Manager Hostname.
–SaaS Accelerator Manager Port. The SCC uses port 3900 to communicate with SAM, and the port needs to be open on the firewall. The field for the port number is editable but we do not recommend changing the value.
–Registration Token. Paste t he registration token you copied in
Step 1 to this field.
3. Click Register.
When the registration process completes, the registration details appear on the page.
A new SaaS Acceleration Status section also appears on the page where you can view the current access list status and a list of applications set up for SaaS acceleration on SAM.
4. On SAM, move this SCC to the whitelist.
Newly added appliances always appear on the graylist in the Access List column. You need to change their status to the whitelist to allow acceleration.
You can safely ignore the No certificates uploaded error message appearing in the Peering Certificates Status column for the SCC appliance. To accelerate SaaS application traffic, only peering certificates for managed appliances are uploaded to SAM when the appliances register with SAM. Peering certificates allow a client-side appliance to establish trust relationship and peer with a SaaS service cluster to accelerate the SaaS traffic.
To move their status to the whitelist:
–Choose Configure > Client Appliances and click the appliance serial number to display the details panel.
–Under Access List, select Whitelist from the Access List drop-down menu and click Submit.
Without moving the SCC to the whitelist on SAM, you cannot push a policy with in-path rules for SaaS applications from the SCC to the managed appliances. For more details about the access lists, see Controlling appliance access.
Moving an appliance to the whitelist on SAM
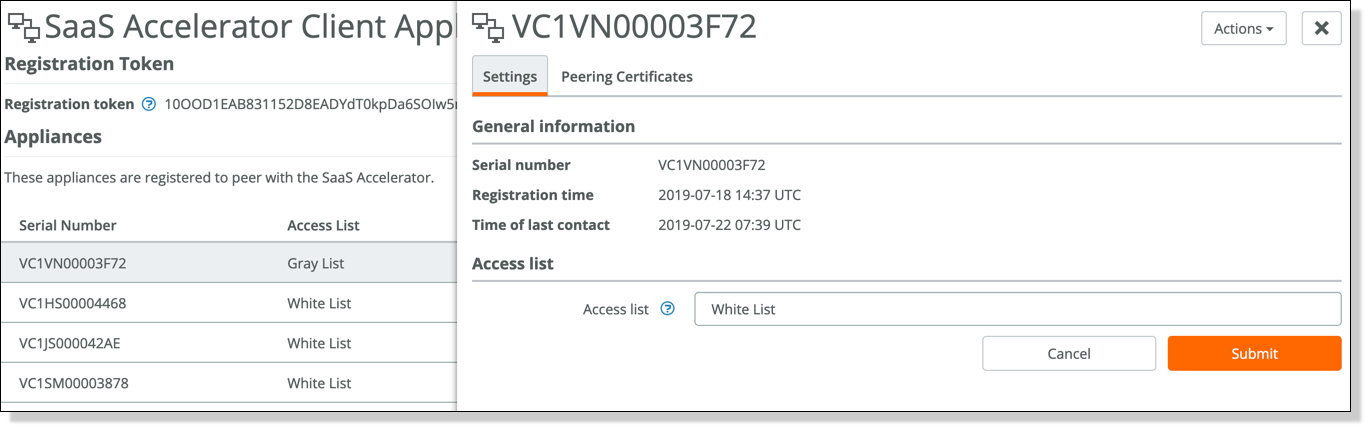
5. On the SCC, choose Administration > SaaS: SaaS Accelerator Manager Registration and click Refresh Data under the SaaS Acceleration Status section. Make sure the access list status of the SCC is Whitelist. You can also view a list of applications set up for SaaS acceleration on SAM and their respective service endpoints.
If you set up new applications for SaaS acceleration on SAM, perform Step 5 on the SCC to view the latest list of SaaS applications set up for acceleration. 6. Register appliances with SAM.
If you plan to use SCC policies to accelerate SaaS application traffic, make sure the SCC and the managed appliances are registered with the same SAM. After registering the SCC with SAM, register the selected appliances or a group of appliances with SAM.
To register client-side appliances with SAM:
–Choose Manage > Topology: Appliances and select appliances, or a group of appliances, you plan to register with SAM.
–Click Appliance Operations, and select SaaS Accelerator Manager Registration from the Choose an operation to perform on the selected groups and appliances drop-down list.
–Select Register, make sure you have the latest registration token from SAM in the Registration Token text field and click Apply.
The client-side appliances use port 3900 to communicate with SAM and the port needs to be open on the branch firewall. The field for the port number is editable but we do not recommend changing the value.
For more details about registering appliances with SAM using SCC, see the SteelCentral Controller for SteelHead User Guide.
7. Move the appliances to the whitelist on SAM.
Newly added appliances always appear on the graylist in the Access List column. You need to change their status to the whitelist to allow acceleration. For details about moving an appliance to the whitelist, see
Step 4. For more information about the access lists, see
Controlling appliance access.
8. Enable SSL optimization in the SCC policies that include SaaS acceleration.
To enable SSL optimization:
–Choose Manage > Services: Policies, open the policy, and click + Add/Remove Pages.
–Under Optimization, select SSL Main Settings and click Apply.
–In the Editing Policy page, click SSL Main Settings, click Include to include the policy, select Enable SSL optimization, and click Apply.
For more details, see the SteelCentral Controller for SteelHead User Guide.
9. Enable SaaS acceleration in the SCC policies to configure SaaS acceleration for groups of appliances.
To enable SaaS acceleration:
–Choose Manage > Services: Policies, open the policy, and click + Add/Remove Pages.
–Under Optimization, select SaaS Accelerator and click Apply.
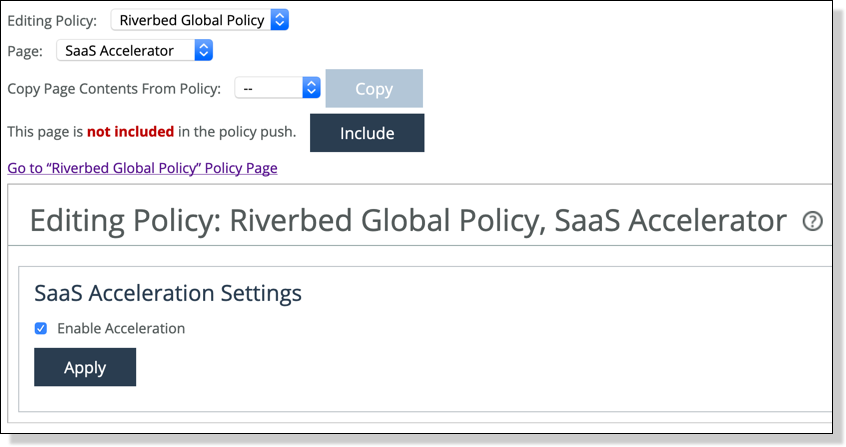
–In the Editing Policy page, click SaaS Accelerator, click Include to include the policy, select Enable Acceleration, and click Apply.
Enabling SaaS acceleration in SCC policy
10. Add an in-path rule to each policy for which you want SaaS acceleration enabled.
In RiOS 9.9.1, you need to configure a unique in-path rule for each application. In RiOS 9.9.2 and later, related applications are grouped into application bundles and you configure just one in-path rule for the bundle.
The in-path rule associates the IP address of the SaaS service cluster in the cloud (supplied by SAM) with the accelerated application or application bundle.
To enable SaaS acceleration:
–Choose Manage > Services: Policies, open the policy, and click + Add/Remove Pages.
–Under Optimization, select In-Path Rules and click Apply.
–In the Editing Policy page, click In-Path Rules, click Include to include the policy, and click Add a New In-Path Rule to expand the page.
–For the Source Subnet, select IPv4 or All IPv4.
–For the Destination Subnet, select SaaS Application.
–A second drop-down list appears to the right. In the second drop-down list, select a SaaS application for acceleration and click Add.
Only applications set up for SaaS acceleration on SAM appear in the list.
For more details, see the SteelCentral Controller for SteelHead User Guide.
SaaS in-path rule

11. Click Save to Disk to save your settings permanently.
Pausing and Canceling SaaS acceleration on SCC
Canceling SaaS acceleration for an appliance entails deregistering the appliance from SAM, which removes appliance-related peering certificates and in-path rules. Pausing acceleration does not remove configuration settings, so you can easily restore the service when you want.
To pause SaaS acceleration on managed appliances on SCC
1. On the SCC, choose Manage > Services: Policies and open the policy.
2. In the Editing Policy page, click SaaS Accelerator, clear the Enable Acceleration check box, and click Apply.
3. Apply the updated policy to the respective appliances.
When paused, all related in-path rules are ignored.
To cancel SaaS acceleration on selected appliances on SCC
1. On the SCC, choose Manage > Topology: Appliances and select appliances, or a group of appliances, you plan to deregister with SAM.
2. Click Appliance Operations, and select SaaS Accelerator Manager Registration from the Choose an operation to perform on the selected groups and appliances drop-down list.
3. Click Deregister.
SaaS acceleration is canceled for the selected appliances and acceleration-related settings, including in-path rules, are removed.
As another option, you can move the appliances to the blacklist on SAM. When you move an appliance to the blacklist, SAM removes the peering CA that it uploaded from the appliance and stops acceleration. For details, see
“Controlling appliance access” on page 33.Configuring SaaS acceleration on SteelHead Mobile
When you have configured SAM for SaaS acceleration, you can configure the Mobile Controller and create a client policy to accelerate SteelHead Mobile client SaaS traffic.
To configure the Mobile Controller for SaaS acceleration
1. In SAM, choose Configure > Client Appliances and copy the registration token.
2. On the Mobile Controller, choose Configure > SaaS Accelerator and add these values:
–SaaS Accelerator Manager Hostname or IP Address.
–SaaS Accelerator Manager Port. The Mobile Controller uses port 3900 from the primary interface to communicate with SAM, and the port needs to be open on the branch firewall. The field for the port number is editable but we do not recommended changing the value.
–Registration Token. Paste the registration token you copied in Step 1 into this field.
3. Click Register.
4. In SAM, move this Mobile Controller to the whitelist.
Newly added appliances appear on the graylist in the Access List column.
Moving an appliance to the whitelist
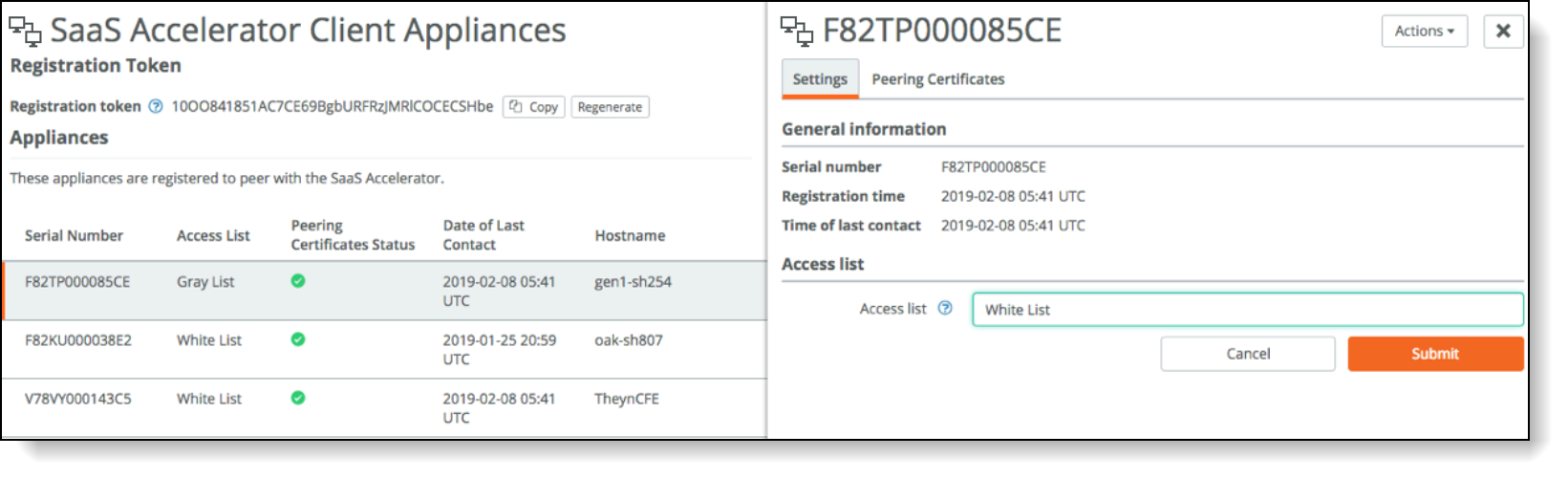
To move their status to the whitelist:
–Choose Configure > Client Appliances and click the serial number of the Mobile Controller to display the details pane.
–Under Access List, select Whitelist from the Access list drop-down list and click Submit.
You cannot enable SaaS acceleration without moving the Mobile Controller to the whitelist. In SAM, if a Mobile Controller is moved from the whitelist to the blacklist, SaaS acceleration stops working. For more information about the access lists, see
Controlling appliance access.
5. Enable SaaS acceleration on the Mobile Controller. Choose Configure > SaaS Accelerator and in the Configure SaaS Acceleration section, select Enable Acceleration and click Apply.
When you click Apply, be patient. It can take several minutes to start acceleration.
6. Enable SSL optimization on the Mobile Controller policies that include SaaS acceleration.
Choose Manage > Policies and open the policy and select the SSL tab. Then select Enable SSL Optimization.
You cannot enable SaaS acceleration without enabling SSL. If SSL was disabled after SaaS acceleration was enabled, SaaS acceleration will stop working.
For details, see the SteelCentral Controller for SteelHead Mobile User Guide.
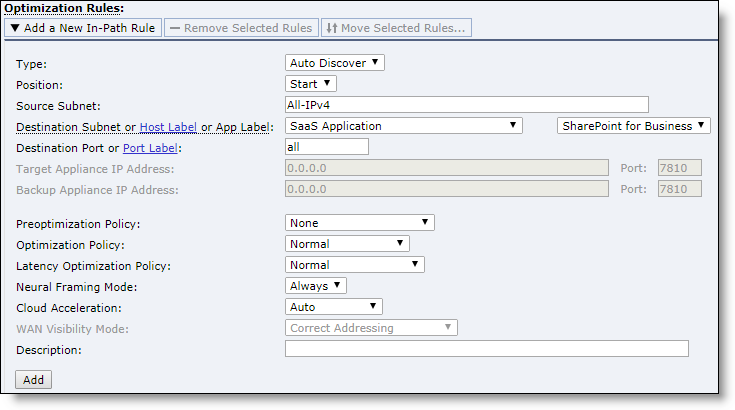
7. On the Mobile Controller, add an in-path rule to each policy for which you want SaaS acceleration enabled.
The in-path rule is application based and lets the Mobile Controller connect to the service endpoint of the SaaS service cluster deployed for the selected application.
–Choose Manage > Policies and select the In-Path Rules tab and click Add a New In-Path Rule.
–For the Destination Subnet, select SaaS Application.
–A second menu appears to the right. In the second menu, select a SaaS application for acceleration. Only applications set up for SaaS acceleration on SAM appear in the list.
–Click Add.
See the SteelCentral Controller for SteelHead Mobile User Guide for more information.
SaaS in-path rule
8. Enable SaaS acceleration in a policy to configure SaaS acceleration for groups of SteelHead Mobile clients. Choose Manage > Policies and open a policy to configure and select the SaaS Acceleration tab.
A helpful list of remaining configuration tasks appears on the page. Completed tasks are prefaced by a check mark.
Enabling SaaS acceleration for a policy
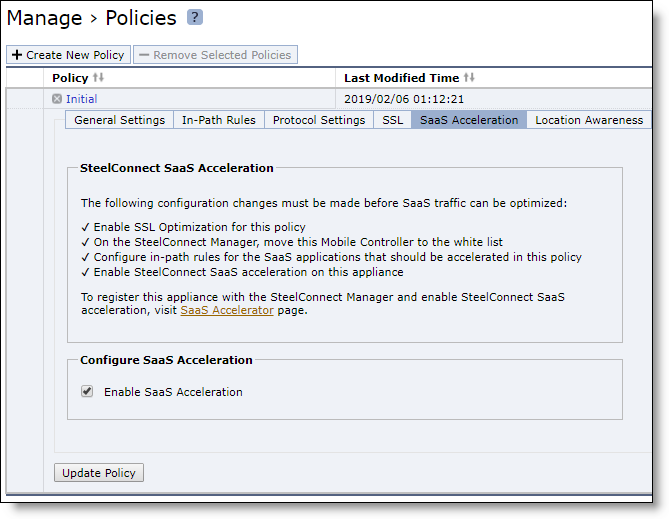
Select Enable SaaS Acceleration and click Update Policy.
You cannot enable SaaS acceleration in a policy without enabling SaaS acceleration in the Mobile Controller.
9. Click Save to Disk to save your settings permanently.
Pausing and Canceling SaaS acceleration on Mobile Controller
Canceling SaaS acceleration on endpoints on Mobile Controller entails deregistering the Mobile Controller from SAM, which removes Mobile Controller-related peering certificates and in-path rules. Pausing acceleration does not remove configuration settings, so you can easily restore the service when you want.
To pause acceleration on managed endpoints on Mobile Controller
1. On the Mobile Controller, choose Configure > SaaS Accelerator.
2. Clear the Enable Acceleration check box and click Apply.
When cleared, all related in-path rules are ignored.
To cancel acceleration on managed endpoints on Mobile Controller
1. On the Mobile Controller, choose Configure > SaaS Accelerator.
2. Click Deregister. This deregisters the appliance from SAM and removes all related in-path rules.
SaaS acceleration is canceled and acceleration-related settings, including in-path rules, are removed.
As another option, you can move the Mobile Controller to the blacklist on SAM. When you move an appliance to the blacklist, SAM removes the peering CA that it uploaded from the appliance and stops acceleration. For details, see
“Controlling appliance access” on page 33.Controlling appliance access
When a client-side appliance registers with SAM, the appliance is added to the access list on the SaaS Accelerator Client Appliances page. An entry appears in the peering list with the appliance serial number, access list status, peering certificate status, date of last contact, and notes. The access lists are designated by these categories:
•Graylist - Indicates an appliance of unknown status. This list serves as a temporary holding place for all registered appliances that are attempting to establish SaaS acceleration. You can move these appliances to the whitelist or blacklist, but you cannot move appliances to the graylist.
•Whitelist - Indicates a trusted appliance. When you move an appliance to the whitelist, the appliance’s peering certificate is copied to the SaaS service cluster and other peer appliances. Once an appliance has been whitelisted, subsequent peering CA uploads automatically replace the older peering CA and changes are pushed out to the SaaS service cluster and SAM managed appliances.
•Blacklist - Indicates untrusted appliances. When you select blacklist for a peer in a whitelist or graylist, SAM removes the peering CA that it uploaded from the appliance and stops acceleration. You can move appliances between the whitelist and the blacklist. (Note: Connections are expected to fail for approximately an hour when moved from the blacklist to the whitelist.)
When you have configured appliances to use the SaaS acceleration service, you need to move those systems to the whitelist on SAM to indicate trust and allow acceleration.
To change the access list status for an appliance
1. In SAM, choose Configure > Client Appliances.
2. Select the row for the appliance to change.
The appliance settings pane appears.
Changing access list status
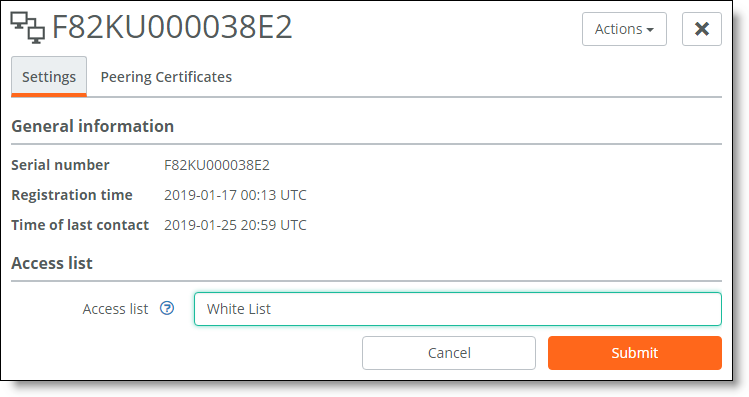
3. From the Access list drop-down list, select the type of list for the appliance.
4. Click Submit.
Resizing a SaaS service cluster
You can resize a SaaS service cluster from SAM.
To resize a SaaS service cluster
1. Choose Configure > SaaS Accelerator and select the application row.
The application settings pane appears.
2. In the application settings, change the number of users.
This adjusts the capacity of the cluster without changing the service endpoint. This operation can take up to 30 minutes.
When you resize a service cluster, the cache is cleared (all traffic will be cold) and proxy and peer certificates will be auto-signed again.
Deleting appliances from SAM
If you no longer want an appliance to be part of your SaaS acceleration service, you can permanently remove an appliance from the SAM configuration. This is a permanent alternative to blacklisting.
The preferred method is to deregister from the client appliance. When you do this, SAM automatically removes the appliance and updates its configuration.
To delete an appliance from SAM
1. Choose Configure > Client Appliances and select the appliance row.
The appliance pane appears.
2. From the Actions drop-down list, select Delete this appliance.
3. When prompted, click Confirm.
You should also deregister this appliance (using the client’s web interface) after deleting the appliance from SAM.
Configuration through the CLI
You can configure SaaS acceleration through the CLI as well as the web interface. These are the primary commands:
•show service saas-accel
•show service saas-accel applications
•service saas-accel acs
Configure App Control Server options
–cache-size <entries>
Configure the maximum number of entries for the app cache (1000-100000)
–cache-timeout <hours>
Configure the duration in hours entries are held in the app cache (1-24)
–syn
Classify connections on syn packet
•service saas-accel acs syn enable
Enable classification based on syn packet
•service saas-accel enable
Enable SaaS acceleration
•service saas-accel register
Register SaaS Accelerator
–sam <sam-domain-name>
–token <token-value>
•service saas-accel sam
Configure SaaS Accelerator Manager access
•service saas-accel sam refresh
•in-path rule auto-discover dst-app <app-name> rulenum start
•no service saas-accel register
Examples:
•service saas-accel acs syn enable <cr>
•service saas-accel acs cache-size <num> (1000 - 100000)
•service saas-accel acs cache-timeout <hours> (1-24)
The Mobile Controller supports these additional commands:
•policy id <id> in-path rule auto-discover dst-app <app-name>
•policy id <id> ssl enable
•policy id <id> saas-accel enable
For more information, see the Riverbed Command-Line Interface Reference Manual.
















