About IPsec encryption settings
These settings are under Optimization > SSL: Secure Peering IPsec.
IPsec secure peering settings
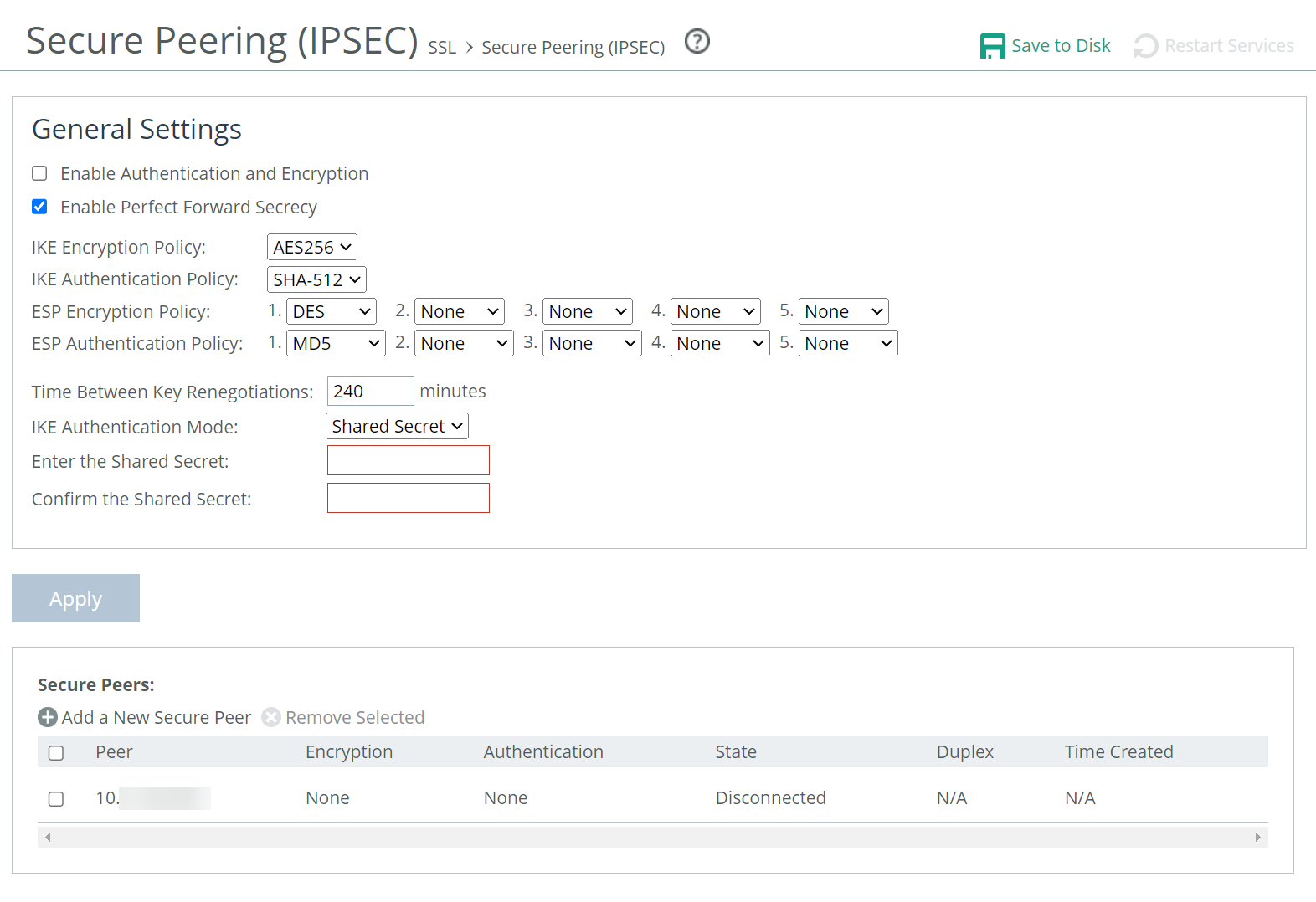
Enable Authentication and Encryption
Enables authentication between SteelHeads. By default, this option is disabled.
Enable Perfect Forward Secrecy
Enables additional security by renegotiating keys at specified intervals. If one key is compromised, subsequent keys are secure because they’re not derived from previous keys. By default, this option is enabled.
IKE Encryption Policy
Specifies the Internet Key Exchange (IKE) encryption policy:
• DES specifies the Data Encryption Standard. This is the default value.
• 3DES specifies the Triple DES encryption algorithm.
• AES specifies the AES 128-bit encryption algorithm.
• AES256 specifies the AES 256-bit encryption algorithm.
Internet Key Exchange (IKE) is the protocol that ensures a secure, authenticated communications channel between two peers.
IKE Authentication Policy
Specifies the IKE authentication policy:
• MD5 enables MD5 security protocol.
• SHA-1 enables SHA security protocol.
• SHA-256 enables the SHA-256 cryptographic hash function.
• SHA-384 enables the SHA-384 cryptographic hash function.
• SHA-512 enables the SHA-512 cryptographic hash function.
ESP Encryption Policy
Selects one of these Encapsulating Security Payload (ESP) encryption methods from the drop-down list:
• DES encrypts data using the Data Encryption Standard algorithm. DES is the default value.
• NULL specifies the null encryption algorithm.
• None doesn’t apply an encryption policy.
• 3DES appears when a valid Enhanced Cryptography License Key is installed on the appliance. Encrypts data using the Triple Digital Encryption Standard with a 168-bit key length. This standard is supported for environments where AES hasn’t been approved, but is both slower and less secure than AES.
• AES appears when a valid Enhanced Cryptography License Key is installed on the appliance. Encrypts data using the Advanced Encryption Standard (AES) cryptographic key length of 128 bits.
• AES256 appears when a valid Enhanced Cryptography License Key is installed. Encrypts data using the Advanced Encryption Standard (AES) cryptographic key length of 256 bits. Provides the highest security.
Optionally, select an algorithm from the method 2, 3, 4, or 5 drop-down lists to create a prioritized list of encryption policies for negotiating between peers.
Peer appliances must both have a valid Enhanced Cryptography License Key installed to use 3DES, AES, or AES256. When an appliance has the valid Enhanced Cryptography License Key installed and an IPsec encryption level is set to 3DES or AES, and a peer SCC doesn’t have a valid Enhanced Cryptography License Key installed, the appliances uses the highest encryption level set on the appliance without the key.
ESP Authentication Policy
Enables you to select one of these ESP authentication methods from the drop-down list:
• MD5 specifies the Message-Digest 5 algorithm, a widely-used cryptographic hash function with a 128-bit hash value. This is the default value.
• SHA-1 specifies the Secure Hash Algorithm, a set of related cryptographic hash functions. SHA-1 is considered to be the successor to MD5.
• SHA-256 enables the SHA-256 cryptographic hash function.
• SHA-384 enables the SHA-384 cryptographic hash function.
• SHA-512 enables the SHA-512 cryptographic hash function.
Optionally, select an algorithm from the method 2 drop-down list to create a secondary policy for negotiating the authentication method to use between peers. If the first authentication policy negotiation fails, the peer appliances use the secondary policy to negotiate authentication.
Time Between Key Renegotiations
Specifies the number of minutes between quick-mode renegotiation of keys using the Internet Key Exchange (IKE) protocol. IKE uses public key cryptography to provide the secure transmission of a secret key to a recipient so that the encrypted data can be decrypted at the other end. The default value is 240 minutes.
Enter the Shared Secret/Confirm the Shared Secret
Specifies and confirms the shared secret. All the SteelHeads in a network for which you want to use IPsec must have the same shared secret.
Add a New Secure Peer
Displays the controls to add a new secure peer.
Peer IP Address
Specifies the IP address for the peer SteelHead (in-path interface) for which you want to make a secure connection.
Add
Adds the peer specified in the Peer IP Address text box. If a connection has not been established between the two SteelHeads that are configured to use IPsec security, the peers list doesn’t display the peer SteelHead status as mature. Adding a peer causes a short service disruption (3 to 4 seconds) to the peer that is configured to use IPsec security.
If you have changed an IPsec encryption setting, you must restart the optimization service. For details, see
Starting, stopping, and restarting the optimization service.
The peered SteelHeads don’t establish the IPsec channel until they’re optimizing traffic.
About the Secure Peers list
The Secure Peers list displays the peers with the encryption and authentication policies and one of these states:
• Mature indicates the IPsec connection is established and usable.
• Larval indicates the IPsec connection is being established.
• Disconnected indicates the IPsec connection isn’t yet established or isn’t usable.


