Configuring password policy
You can change the password policy and strength in the Password Policy page.
Selecting a password policy
You can choose one of these password policy templates under Administration > Security: Password Policy, depending on your security requirements:
• Strong—Sets the password policy to more stringent enforcement settings. Selecting this template automatically prepopulates the password policy with stricter settings commonly required by higher security standards such as for the Department of Defense.
• Basic—Reverts the password policy to its predefined settings so you can customize your policy.
Setting a password policy
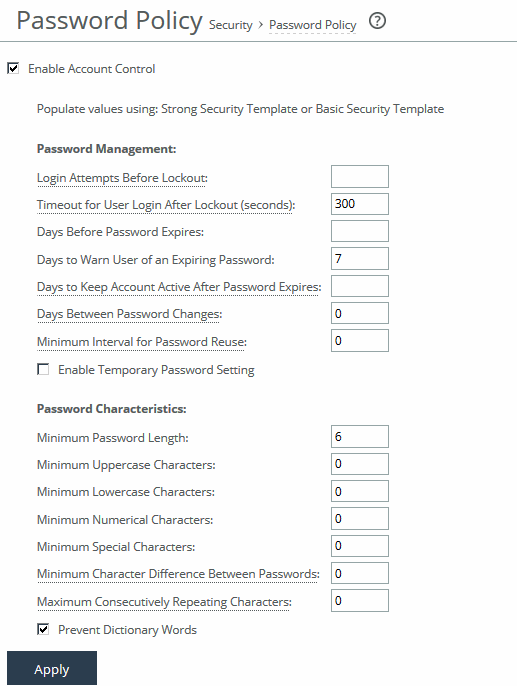
To enforce password policies, select the Enable Account Control check box. This makes password use mandatory and immediately expires all existing passwords, requiring users to create new ones that meet the defined password policy. From that point on, all passwords are governed by the policy settings.
Passwords will also expire after the number of days specified by the administrator on the Password Policy page. When a user tries to log in with an expired password, the system shows an Expired Password page prompting them to create a new password. After doing so, they are automatically logged in to the Management Console. Empty passwords are not allowed when account control is enabled.
You can choose between Basic or Strong password policy templates. Selecting a template automatically fills in secure settings. Under the Basic template, the system prompts users to change their password every 60 days, and locks them out after 300 days without a password change. Once locked out, only an administrator can unlock the account. For details, see
Unlocking an account.These configuration options are available under Password Management:
Login Attempts Before Lockout
Specifies the maximum number of unsuccessful login attempts before temporarily blocking user access to the SteelHead appliance. The user is prevented from further login attempts when the number is exceeded. The default for the strong security template is 3. The lockout expires after the amount of time specified in Timeout for User Login After Lockout elapses.
Timeout for User Login After Lockout
Specifies the amount of time, in seconds, that must elapse before a user can attempt to log in after an account lockout due to unsuccessful login attempts. The default for the strong security template is 300.
Days Before Password Expires
Specifies the number of days the current password remains in effect. The default for the strong security template is 60. To set the password expiration to 24 hours, specify 0. To set the password expiration to 48 hours, specify 1. Leave blank to turn off password expiration.
Days to Warn User of an Expiring Password
Specifies the number of days the user is warned before the password expires. The default for the strong security template is 7.
Days to Keep Account Active After Password Expires
Specifies the number of days the account remains active after the password expires. The default for the strong security template is 305. When the time elapses, RiOS locks the account permanently, preventing any further logins.
Days Between Password Changes
Specifies the minimum number of days before which passwords can’t be changed.
Minimum Interval for Password Reuse
Specifies the number of password changes allowed before a password can be reused. The default for the strong security template is 5.
Enable Temporary Password Setting
Specifies a temporary password to meet security best practices and DISA requirements. This option is only available if Account Control is enabled. When a temporary password is used, the password set by an Admin or System Admin will expire upon the user’s first login. The user will see a Password Expired page and be required to create a new password.
This applies both to new users and to existing users whose passwords have been reset by an Admin or System Admin. In both cases, the temporary password will expire immediately after the first login, prompting the user to change it.
These configuration options are available under Password Characteristics:
Minimum Password Length
Specifies the minimum password length. The default for the strong security template is 14 alphanumeric characters.
Minimum Uppercase Characters
Specifies the minimum number of uppercase characters required in a password. The default for the strong security template is 1.
Minimum Lowercase Characters
Specifies the minimum number of lowercase characters required in a password. The default for the strong security template is 1.
Minimum Numerical Characters
Specifies the minimum number of numerical characters required in a password. The default for the strong security template is 1.
Minimum Special Characters
Specifies the minimum number of special characters required in a password. The default for the strong security template is 1.
Minimum Character Differences Between Passwords
Specifies the minimum number of characters that must be changed between the old and new password. The default for the strong security template is 4.
Maximum Consecutively Repeating Characters
Specifies the maximum number of times a character can occur consecutively.
Prevent Dictionary Words
Prevents the use of any word that’s found in a dictionary as a password. By default, this control is enabled.
Unlocking an account
RiOS temporarily locks out an account after a user exceeds the configured number of login attempts.
Account lockout information appears on the User Permissions page.
When an account is locked out, the lockout ends after one of these events:
• The configured lockout time elapses.
• The administrator unlocks the account. RiOS never locks out administrator accounts.
To unlock an account log in as an administrator (admin).
Under Administration > Security: User Permissions, click Clear Login Failure Details.
When the user logs in to their account successfully, RiOS resets the login failure count.
Resetting an expired password
RiOS temporarily locks out an account when its password expires. Passwords expire for one of these reasons:
• An administrator enables Account Control.
• The expiration time for a password elapses.
• An administrator disables a user account and then enables it.
• An administrator uses a CLI command to encrypt a password.
After a user password expires, the user must update their password within the number of days specified in Days to Keep Account Active After Password Expires. The default value is 305 days. After the time elapses, RiOS locks the account permanently, preventing any further logins.
To reset the password and unlock the account, log in as an administrator (admin). Under Administration > Security: User Permissions, click Clear Login Failure Details. Type and confirm the new password and click Change Password.


