Figure: Setting Capability-Based Accounts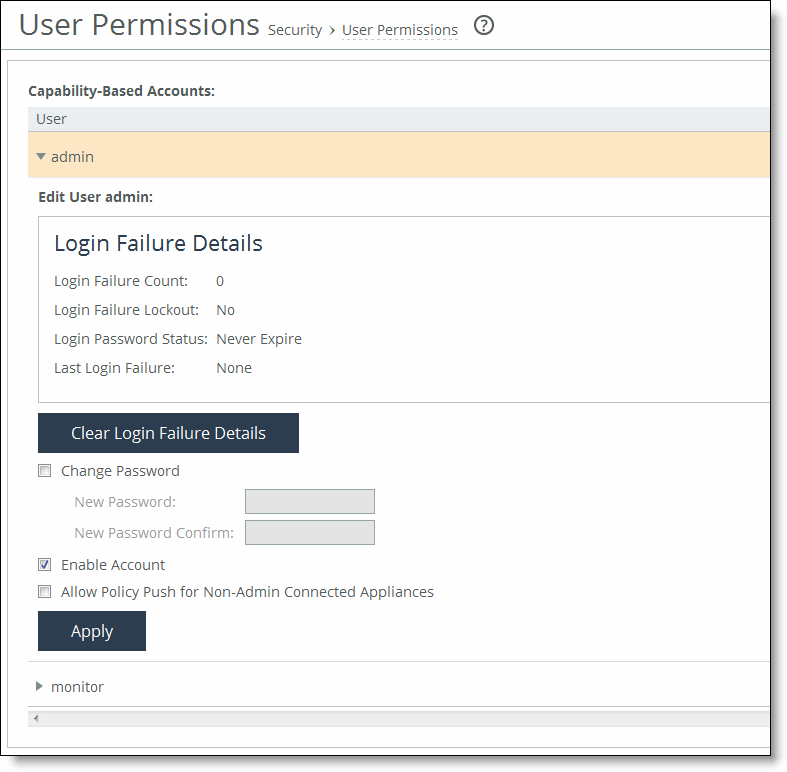

Management Console Page | Feature (To Configure or Change This Feature) | Required Settings for Read Permission | Required Settings for Read/Write Permission |
Manage > Topology: Sites & Networks | Networks | Network Settings Read-Only | Network Settings Read/Write Policy Push Read/Write |
Sites | Network Settings Read-Only QoS/Path Selection Read-Only | Network Settings Read/Write Policy Push Read/Write QoS/Path Selection Read/Write | |
Manage > Applications: App Definitions | Applications | Network Settings Read-Only | Network Settings Read/Write Policy Push Read/Write |
Manage > Services: Quality of Service | Enable QoS | Network Settings Read-Only | Network Settings Read/Write QoS/Path Selection Read/Write Policy Push Read/Write |
Manage QoS Per Interface | Network Settings Read-Only | Network Settings Read/Write QoS/Path Selection Read/Write Policy Push Read/Write | |
QoS Profile | QoS/Path Selection Read-Only | QoS/Path Selection Read/Write Policy Push Read/Write | |
Manage > Services: QoS Profile Details | QoS Profile Name | QoS/Path Selection Read-Only | QoS/Path Selection Read/Write Policy Push Read/Write |
QoS Classes | QoS/Path Selection Read-Only | QoS/Path Selection Read/Write Policy Push Read/Write | |
QoS Rules | QoS/Path Selection Read-Only | Network Settings Read/Write QoS/Path Selection Read/Write Policy Push Read/Write | |
Manage > Services: Path Selection | Enable Path Selection | Network Settings Read-Only | Network Settings Read/Write Policy Push Read/Write |
Path Selection Rules | Network Settings Read-Only QoS/Path Selection Read-Only | Network Settings Read/Write QoS/Path Selection Read/Write Policy Push Read/Write | |
Uplink Status | Network Settings Read-Only QoS/Path Selection Read-Only Reports Read/Write | N/A | |
Manage > Topology: Interceptor Clusters | Interceptor Clusters | Network Settings Read-Only | Interceptor/Cluster Settings Read/Write Policy Push Read/Write |
Page | Description |
SCC Settings | Manages the SCC features: for example, host settings, network settings and reports. |
AAA Configurations | Authenticates and authorizes SCC users. |
Page | Description |
Global | Configures Global group settings. |
<group> | Configures the <group> settings. |

Control | Description |
admin/monitor | Click the right arrow to modify the admin and monitor accounts. |
Clear Login Failure Details | Clears the account log in failure details and closes the fields for changing the password. |
Change Password | Enables password protection. Password protection is an account control feature that allows you to select a password policy for more security. When you enable account control on the Administration > Security: Password Policy page, a user must use a password. When a user has a null password to start with, the administrator can still set the user password with account control enabled. However, once the user or administrator changes the password, it cannot be reset to null as long as account control is enabled. • Password - Specify a password in the text box. • Password Confirm - Retype the new administrator password. |
Enable Account | Activates the account. Clear the check box to disable the administrator or monitor account. When enabled, you may make the account the default user for RADIUS and TACACS+ authorization. You may only designate one account as the default user. Once enabled, the default user account may not be disabled or removed. The Accounts table displays the account as permanent. |
Allow Policy Push for Non-Admin Connected Appliances | Enables administrator users to perform configuration pushes to appliances connected with nonadministrator role-based management users, provided the nonadministrator role-based management users have read/write privileges on the appliance. |
Apply | Applies your changes to the running configuration. |
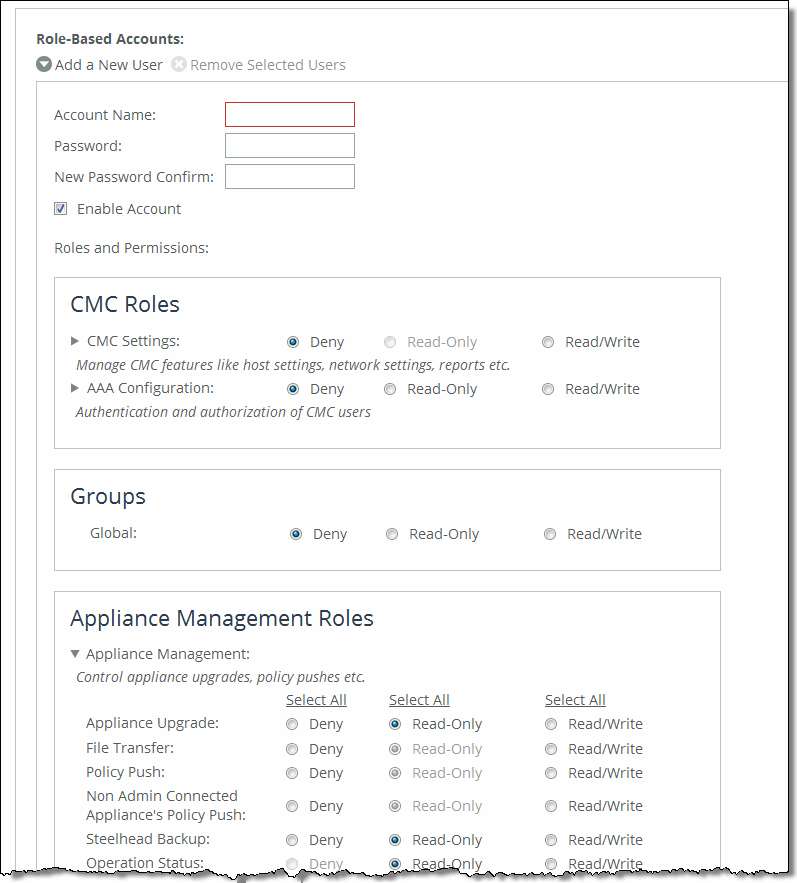
Control | Description |
Add a New User | Displays the controls for adding a new user. |
Account Name | Specify a name for the role-based account. |
Password | Specify a password in the text box, and then retype the password for confirmation. |
Enable Account | Select the check box to enable the new account. |
CMC (SCC) Roles | |
CMC (SCC) Settings | Manages the SCC features: for example, host settings, network settings and reports. |
AAA Configurations | Authenticates and authorizes SCC users. |
Groups | |
Global | Configures Global group settings. |
Appliance Management | Controls appliance upgrades, policy pushes, and so forth. |
Appliance Upgrade | Configures appliance upgrade settings. |
File Transfer | Enables file transfers on managed appliances. |
Policy Push | Enables policy pushes for SCC features, such as hybrid networking features. |
Non Admin Connected Appliance's Policy Push | Enables administrator users to perform configuration pushes to appliances connected with nonadministrator role-based management users, provided the nonadministrator role-based management users have read/write privileges on the appliance. If the push fails, verify if the nonadministrator role-based management user has the required permissions to modify the page that is being pushed on the appliance and on SCC: for example, to push QoS changes the user must also have Read/Write permissions for Role Based Accounts > Appliance Management Roles > Optimization Settings > Qos/Path Selection. |
SteelHead Backup | Configures SteelHead backups on managed appliances. |
Operation Status | Enables operation status on managed appliances. |
CLI Commands | Enables CLI commands to managed appliances. |
Appliance Settings | Manage appliance features like Cluster configuration, host settings, network settings, and so forth. |
Interceptor/Cluster Settings | Configures Interceptor clusters. You must also include the Policy Push role. |
Network Settings | Configures these features: • Topology definitions • Site and network definitions • Application definitions • Host interface settings • Network interface settings • DNS cache settings • Hardware assist rules • Host labels • Port labels You must include this role for users configuring path selection or enforcing QoS policies in addition to the QoS and Path Selection roles. |
Reports | Sets system report parameters. |
Basic Diagnostics | Customizes system diagnostic logs, including system and user log settings, but does not include TCP dumps. |
SteelFusion Branch Storage Service | Configures branch storage services on SteelFusion Edge appliances (the branch storage services are only available on a SteelHead EX or SteelFusion Edge). |
TCP Dumps | Customizes TCP dump settings and allows use of the Shark function for detailed packet analysis through Cascade Pilot. |
Appliance AAA Configuration | Appliance security set up. |
Security Settings | Configures security settings, including RADIUS and TACACS authentication settings and the secure vault password. |
Optimization Settings | |
SteelHead In-Path Rules | Configures TCP traffic for optimization and how to optimize traffic by setting in-path rules. This role includes WAN visibility to preserve TCP/IP address or port information. For details about WAN visibility, see the SteelHead Deployment Guide. |
QoS/Path Selection | Enforces QoS policies. You must also include the Network Settings role. Configures path selection. You must also include the Network Settings role. |
Application Optimization Policies | Configure optimization policies for different applications. |
Optimization Service | Configures alarms, performance features, SkipWare, HS-TCP, and TCP optimization. |
CIFS Optimization | Configures CIFS optimization settings (including SMB signing) and Overlapping Open optimization. |
HTTP Optimization | Configures enhanced HTTP optimization settings: URL learning, Parse and Prefetch, Object Prefetch Table, keepalive, insert cookie, file extensions to prefetch, and the ability to set up HTTP optimization for a specific server subnet. |
Oracle Forms Optimization | Optimizes Oracle E-business application content and forms applications. |
MAPI Optimization | Optimizes MAPI and sets Exchange and NSPI ports. |
NFS Optimization | Configures NFS optimization. |
Notes Optimization | Configures Lotus Notes optimization. |
Citrix Optimization | Configures Citrix optimization. |
SSL Optimization | Configures SSL support and the secure inner channel. |
Replication Optimization | Configures the SRDF/A, FCIP, and SnapMirror storage optimization modules. |
Domain Authentication | Allows joining a Windows domain and configuring Windows domain authentication. |
Branch Services | Branch services set up, such as PFS, RSP, and VSP. |
Proxy File Service (PFS) | Configures functionality into a virtualized environment on the client SteelHead. The functionality can include third-party packages such as a firewall security package, a streaming video server, or a package that provides core networking services (for example, DNS and DHCP). This role includes permission to install VMware tools and add subnet side rules. For details, see the RSP User’s Guide. |
RSP/VSP | Configures Riverbed Services Platform (RSP) and Virtual Services Platform (VSP) |
Add | Adds your settings to the system. |
Remove Selected Accounts | Select the check box next to the name and click Remove Selected. |