About WinSec Controller
Riverbed WinSec Controller is a standalone, dedicated tier-0 appliance for security-specific functions. WinSec Controller provides a highly secure method for performing security functions for server-side SteelHead appliances without compromising Microsoft-recommended security best practices. WinSec Controller appliances are purpose-built to operate in highly secure environments and offer these key features:
• Internet Protocol Security (IPsec) encrypted connections between WinSec Controllers and server-side SteelHeads with user-selectable Internet Key Exchange (IKE) authentication methods.
• Configuration and administration by domain administrators through a web application.
• Secure vault protection.
• Secure peering using IKE shared secrets or self-signed certificates.
• Replication user accounts, server key replication, and control over key fetch scope and password replication policies.
• High availability and fault tolerance with active monitoring for enterprise-class uptime (requires multiple appliances).
• Support for domain trust relationships.
• Secure software upgrades.
Within an enterprise access model topology, a WinSec Controller appliance resides inside the boundaries of the control plane (tier 0) and maintains encrypted connections with configured server-side SteelHead appliances (tier 1), proxying requests and responses between those SteelHead appliances and domain controllers, such as Active Directory.
WinSec Controller supports only Kerberos traffic. New Technology LAN Manager (NTLM) traffic is not supported. If you have NTLM traffic in your environment, we strongly recommend that you configure SteelHead peers to bypass that traffic. If the SteelHead is not configured to bypass NTLM traffic, the traffic could be blackholed (that is, dropped without notification) in the event a domain controller is not reachable or no domain controllers are configured to peer with WinSec Controller. For details, see
Configuring WinSec Controller Peers.WinSec Controller topology
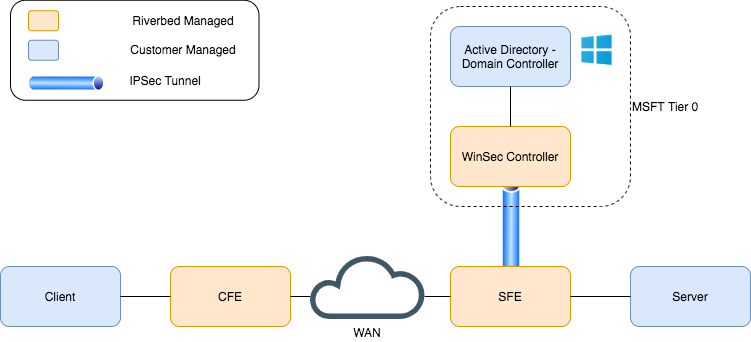
In order to optimize SMB/CIFS and Encrypted MAPI (E-MAPI) traffic, traditional SteelHead deployments placed security functions, such as server key replication, with the SteelHead. Now, using WinSec Controller to host the replication user account and manage server key replication, you can optimize SMB/CIFS and E-MAPI traffic while maintaining strict security best practices. If you are not currently optimizing SMB/CIFS and E-MAPI traffic across your enterprise due to security concerns, WinSec Controller offers a highly secure option for doing so, unlocking more value from your optimization products.
About the WinSec Controller ecosystem
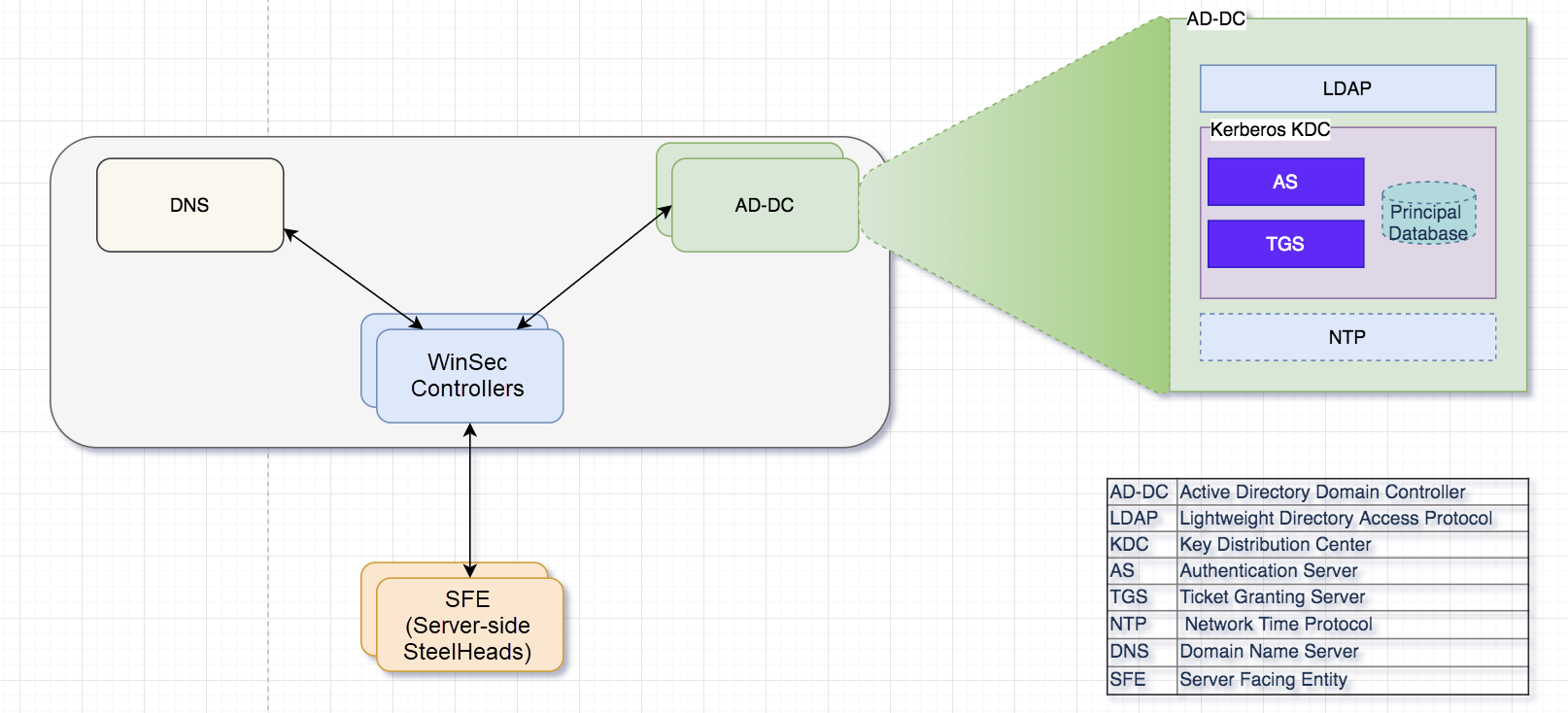
The WinSec Controller is deployed within the control plane (tier-0) perimeter and uses DNS to discover domain controllers. SteelHead appliances are deployed in lower security tiers, such as the management plane, and are configured to use the WinSec Controller.
WinSec Controller deployed with configured server-side SteelHeads
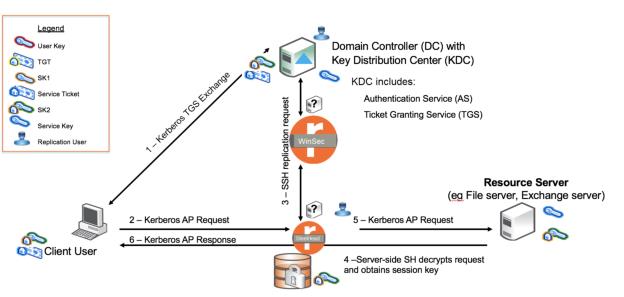
A client device sends a request for a ticket-granting ticket (TGT) to the domain controller. The domain controller forwards the request to its key distribution center (KDC) component, which returns a ticket to the client. Before the client connects to the server, the client shares the TGT with the ticket-granting service (TGS) and requests the server ticket. The TGS authenticates the client, ensuring that the client is authorized to access the server. The TGS then provides a server ticket that includes the session key to the client.
Time synchronization between WinSec Controllers and domain controllers must be within a five-minute tolerance. If the time synchronization is off by more than five minutes, server key fetch operations may fail. When WinSec Controller fails to provide a server key to the server-side SteelHead, the authentication protocol negotiation falls back from Kerberos to NT LAN Manager (NTLM) protocols.
The client sends a Kerberos request to the server that includes the server ticket and an encrypted session key. The client-side SteelHead intercepts the request and forwards it to the server-side SteelHead. The server-side SteelHead communicates with the WinSec Controller through a secure tunnel to obtain the replicated server key, and then decrypts the client’s Kerberos request, obtaining the session key. The server-side SteelHead uses the session key to decrypt the traffic, and then the optimization of application traffic between the client-side SteelHead and server-side SteelHead begins.
Client Kerberos request intercepted and decrypted by server-side SteelHead
About WinSec Controller IPsec peering connections
The WinSec Controller communicates with server-side SteelHeads through an encrypted peering connection using IPsec. The WinSec Controller and the SteelHead peer with each other through their primary interfaces. Authentication of the peering session secret and keys is handled by Internet Key Exchange (IKE) protocols. To enable peering between WinSec Controller and SteelHead, you’ll need to configure these settings:
• SSL certificate exists. SteelHead appliances are supplied with a self-signed certificate during manufacturing. If a new or different certificate is needed, the factory certificate can be replaced. Ensure you validate each certificate.
• Primary interface is configured. The primary interface on both appliances is used for the peering connection.
• Secure transport is disabled. SteelHead only. Secure transport must be disabled because SteelHead appliances do not allow the secure transport feature and the secure peering feature to be enabled at the same time.
• IPsec is enabled on the primary interface. Secure peering occurs through the primary interface on both appliances and requires IPsec to be enabled.
• IKE authentication mode is configured. IKE is the protocol used to set up a security association (SA) in the IPsec protocol suite and establish the secure session secret and cryptographic keys. These two IKE options are available:
– Shared secret—Uses a secret shared between peers to authenticate the session secret and keys.
– Certificate—Uses self-signed certificates on the appliances to authenticate the session secret and keys.
• Peer IP addresses are configured. You’ll need to add peer IP addresses to the peering list on both appliances.
By design, after you configure those settings the appliances do not automatically connect. You’ll need to manually initiate the first-time traffic between them to activate the connection.
For details about how to configure the WinSec Controller, see
Configuring WinSec Controller. For details about how to configure SteelHead appliances, see the
SteelHead User Guide.
About WinSec Controller high availability
On the SteelHead appliance, you can configure primary and secondary WinSec Controller appliances for high-availability (HA) deployments. We recommend you deploy WinSec Controller appliances in an HA deployment to ensure that traffic to and from the domain controller is not disrupted.
The health status of the primary WinSec Controller appliance is always maintained by the SteelHead appliance. If the primary WinSec Controller appliance is not available, the SteelHead appliance switches to the secondary WinSec Controller appliance and forwards the next set of requests. Within a site, you can have multiple server-side SteelHead appliances and WinSec Controller appliances.
The server-side SteelHead appliance maintains the IPsec tunnel to both the primary and secondary WinSec Controller appliances at all times. The primary and secondary WinSec Controller appliances are independent and do not engage in any configuration or state synchronization. It takes approximately eight seconds for the secondary WinSec Controller appliance to respond when the primary WinSec Controller appliance is unreachable.
Accessing the WinSec Controller Management Console
WinSec Controller is managed through the Management Console, a secure, web-based graphical user interface (GUI). There is no command-line interface. For troubleshooting support, Secure Shell (SSH) access will be provided after completing a challenge-response authentication step.
WinSec Controllers cannot be managed through SteelCentral Controller for SteelHead.
The Management Console uses session cookies to communicate with its back-end server. The first time you log in, you’ll see a notice regarding these cookies and are prompted to either accept the use of them or log out. Session cookies are renewed every 30 minutes as long as you are actively using the console. After five minutes of no use, you will be automatically logged out. Session cookies expire after you log out and close your browser.
You can use a FireFox browser to access the Management Console, but you’ll need to add a security exception to your browser for the console. For details, go to Knowledge Base article
S34857.
To log in to and out of the Management Console
1. Go to https://<hostname>.
2. Enter your login credentials.
3. If this is your first time logging in, click Accept & Proceed.
The WinSec Dashboard is displayed.
To log out, click the user icon in the upper right area of the console and select Log out.
Accessing user settings
Click the user icon in the upper right area of the console to access user settings or log out. These settings are available:
• Set theme—Enables you to toggle between light and dark themes.
• Change password—Enables you to change your password.
• About—Enables you to edit your username, enter your full name, enter your email address, and provide a short description for your account.
Upgrading and viewing WinSec Controller software versions
You can upgrade WinSec Controller software and view the current and backup software versions.
To upgrade the WinSec Controller software or view software versions
1. Choose Administration > Upgrade.
2. In the Install Upgrade section, enter the URL to the upgrade image file, or browse to or drag and drop the image file from your local system.
3. Click Submit.
The image is downloaded and installed in a backup partition.
4. Click Switch to backup version.
The system exchanges primary and backup partitions and restarts, loading the new software.
The current and backup software versions are displayed in the Software Upgrade section. To revert to a previous version of the software, simply select the backup version of the software and click Revert.
Shutting down, restarting, and factory resetting the WinSec Controller
You can shut down, restart, and factory reset the WinSec Controller, and restart its GUI services in the Actions page.
You will be logged out and won’t be able to reach the WinSec Controller through the Management Console while performing any of those actions. If you need to access it and are having problems, contact your WinSec Controller administrator.
To shut down, restart, or factory reset the WinSec Controller
1. Choose Administration > Actions.
2. Shut down, reboot, factory reset the WinSec Controller, or restart the GUI services.
Accessing WinSec Controller diagnostic and troubleshooting information
Use the tools available in the Diagnostics section of the Management Console to obtain useful information for troubleshooting problems. There you’ll find tools to test things like Kerberos replication, the ability of the DNS to autodiscover domain controllers, and the ability for the WinSec Controller to contact the SteelHead (tests host reachability using the Internet Control Message Protocol, or ICMP).
You can also generate system dump files, which are helpful when troubleshooting issues together with your Riverbed Support representative.
If you want to clear all fields in a test form, click Reset.
The Kerberos replication and Parallel Redundancy Protocol (PRP) tests in the Diagnostics section are the same as the troubleshooting tests available in the Configuration > Replication Users > Troubleshooting section. For details, see
Testing WinSec Controller key and account replication.To test DNS domain controller discovery
1. Choose Diagnostics > DNS Test.
2. Enter the domain.
3. Click Submit.
To test host reachability
1. Choose Diagnostics > Network Health Checkup.
2. Enter the domain.
3. Click Submit.
To generate, download, or delete system dump files
1. Choose Diagnostics > Sysdump.
2. Do any of these actions
– Click Submit to generate a system dump file. Optionally, you can enter a descriptive case number. Any alphanumeric characters are accepted.
– Click Download for the system dump file you want to download.
– Click Delete for the system dump file you want to remove.




