Configuring SSL Main Settings
You can configure SSL optimization in the Optimization > SSL: SSL Main Settings page. Enabling SSL allows you to accelerate encrypted traffic (for example, HTTPS).
The SteelHead securely decrypts, optimizes, and then reencrypts SSL traffic. To configure SSL support, you don’t need to make configuration changes on the client and the server—clients continue connecting to the same server name or IP address.
To enable SSL
1. Choose Optimization > SSL: SSL Main Settings to display the SSL Main Settings page.
Figure: SSL Main Settings Page
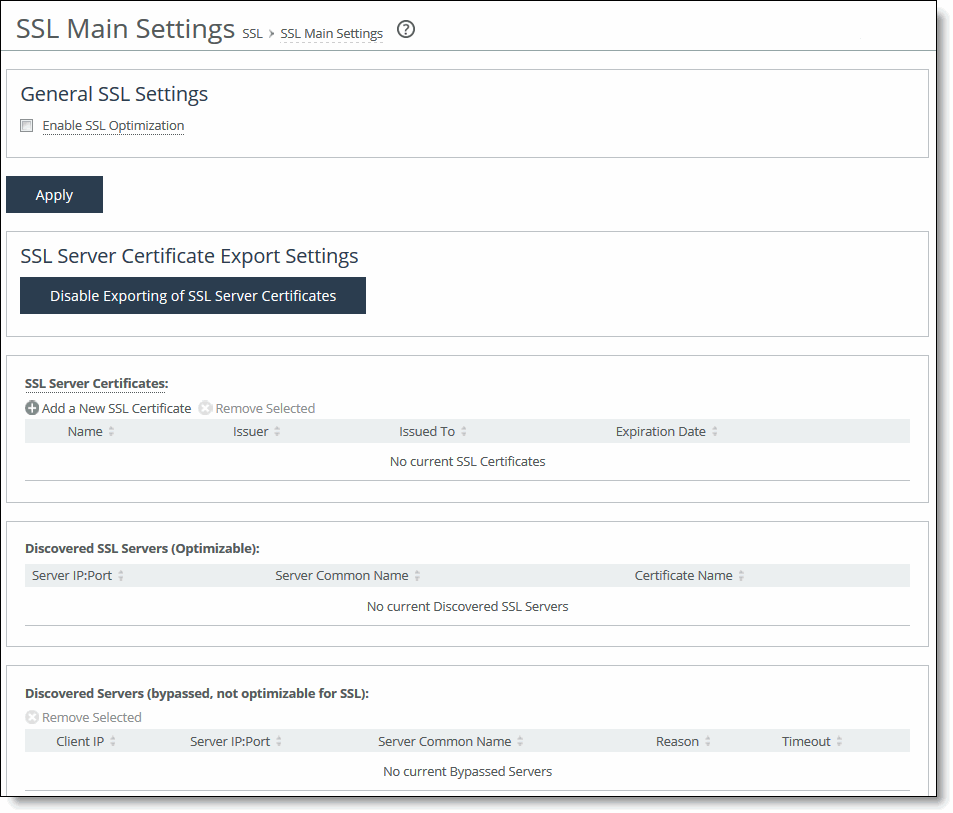
2. Under General SSL Settings, complete the configuration on both the client-side and server-side SteelHeads as described in this table.
Control | Description |
Enable SSL Optimization | Enables SSL optimization, which accelerates applications that use SSL to encrypt traffic. By default, this option is disabled. You can choose to enable SSL optimization only on certain sessions (based on source and destination addresses, subnets, and ports), or on all SSL sessions, or on no SSL sessions at all. An SSL session that is not optimized simply passes through the SteelHead unmodified. |
3. Click Apply to apply your settings.
4. Click Save to Disk to save your settings permanently.
Configuring SSL Server Certificates
You configure an SSL server certificate in the Optimization > SSL: SSL Main Settings page.
The SteelHead doesn’t require you to add each server certificate individually. You need only add unique certificates to a certificate pool on the server-side SteelHead. When a client initiates an SSL connection with a server, the SteelHead matches the common name of the server’s certificate with one in its certificate pool. If it finds a match, it adds the server name to the list of discovered servers that are optimizable and all subsequent connections to that server are optimized.
If it doesn’t find a match, it adds the server IP and port and client IP address (or wildcard) to the list of bypassed servers and all subsequent connections to that client-server pair aren’t optimized. The Discovered and Bypassed Server lists appear in the SSL Main Settings page.
The SteelHead supports RSA private keys for peers and SSL servers.
Note: Optimization doesn’t occur for a particular server IP address and port unless a suitable proxy server certificate is configured on the server-side SteelHead.
When you configure the back-end server proxy certificate and key on the server-side SteelHead, if you choose not to use the actual certificate for the back-end server and key, you can use a self-signed certificate and key or another CA-signed certificate and key. If you have a CA-signed certificate and key, import it.
If you don’t have a CA-signed certificate and key, you can add the proxy server configuration with a self-signed certificate and key, back up the private key, generate a CSR, have it signed by a CA, and import the newly CA-signed certificate and the backed up private key.
Note: To back up a single pair of certificate and key (that is, the peering certificate and key pair and a single certificate and key for the server), use the Export (in PEM format only) option. Make sure you check Include Private Key and enter the encryption password. Save the exported file that contains the certificate and the encrypted private key. For details, see
Configuring Secure Peers.
You can also simply use the generated self-signed certificate and key, but it might be undesirable because the clients by default don’t trust it, requiring action from the end users.
To add an SSL server certificate
1. Choose Optimization > SSL: SSL Main Settings to display the SSL Main Settings page.
Figure: SSL Main Settings Page

2. On the server-side SteelHead, under SSL Server Certificates, complete the configuration as described in this table.
Control | Description |
Add a New SSL Certificate | Displays the controls to add a new server certificate. |
Name | Specify a name for the proxy certificate (required when generating a certificate, leave blank when importing a certificate). |
Import Certificate and Private Key | Imports the certificate and key. The page displays controls for browsing to and uploading the certificate and key files. Or, you can use the text box to copy and paste a PEM file. The private key is required regardless of whether you are adding or updating the certificate. |
Certificate | Upload - Browse to the local file in PKCS-12, PEM, or DER formats. Paste it here (PEM) - Copy and then paste the contents of a PEM file. |
Private Key | Select the private key origin. • The Private Key is in a separate file (see below) - You can either upload it or copy and paste it. • This file includes the Certificate and Private Key |
Separate Private Key | Upload (PEM or DER formats) - Browse to the local file in PEM or DER formats. Paste it here (PEM only) - Paste the contents of a PEM file. Decryption Password - Specify the decryption password, if necessary. Passwords are required for PKCS-12 files, optional for PEM files, and never needed for DER files. Exportable - (Appears only when global exporting of SSL server certificates is enabled.) Allows the certificate and server key to be exported. This is the default setting. Disable this setting to make sure the private key doesn’t leave the SteelHead. |
Generate Self-Signed Certificate and New Private Key | Select this option to generate a new private key and self-signed public certificate. The page displays controls to identify and generate the new certificate and key. Common Name - Specify the common name of a certificate. To facilitate configuration, you can use wildcards in the name: for example, *.nbttech.com. If you have three origin servers using different certificates such as webmail.nbttech.com, internal.nbttech.com, and marketingweb.nbttech.com, on the server-side SteelHeads, all three server configurations can use the same certificate name *.nbttech.com. Organization Name - Specify the organization name (for example, the company). Organization Unit Name - Specify the organization unit name (for example, the section or department). Locality - Specify the city. State (no abbreviations) - Specify the state. Country (2-letter code) - Specify the country (2-letter code only). Email Address - Specify the email address of the contact person. Validity Period (Days) - Specify how many days the certificate is valid. |
Private Key | Cipher Bits - Select the key length from the drop-down list. The default is 2048. |
Add | Paste it here (PEM) - Paste the contents of a PEM file. |
Remove Selected | Select the check box next to the name and click Remove Selected. |
Preventing the Export of SSL Server Certificates and Private Keys
The bulk export feature on the Optimization > SSL: Advanced Settings page allows you to export SSL server certificates and private keys. You can also select SSL server certificates for export individually on the Optimization > SSL: SSL Main Settings page. These features are useful to back up SSL configurations or move them to another SteelHead; however, security-conscious organizations might want to make SSL configurations nonexportable. In RiOS 7.0.1 and later you can ensure a secure SSL deployment by preventing your SSL server certificates and private keys from leaving the SteelHead.
Consider making SSL server certificates and private keys nonexportable with your particular security goals in mind. Before doing so, you must have a thorough understanding of its impact. Use caution and consider the following before making SSL configurations nonexportable:
• After disabling export on a new SteelHead appliance running 7.0.1, you can’t reenable it unless you perform a factory reset on the SteelHead appliance (losing the configuration) or clear the secure vault.
• After upgrading a SteelHead to RiOS 7.0.1 and disabling export, you can’t export any preexisting or newly added server certificates and private keys to another SteelHead.
• After disabling export, any newly added server certificates and keys are marked as nonexportable.
• After disabling export and then downgrading a SteelHead to a previous RiOS version, you can’t export any of the existing server certificates and private keys. You can export any newly added server certificates and private keys.
• Disabling export prevents the copy of the secure vault content.
To prevent exporting of SSL server certificates and private keys
1. Choose Optimization > SSL: SSL Main Settings to display the SSL Main Settings page.
2. Under SSL Server Certificate Export Settings, click Disable Exporting of SSL Server Certificates.
The system reminds you that disabling export can’t be undone.
3. Click Disable Export.
4. Click Apply to apply your settings.
5. Click Save to Disk to save your settings permanently.



