** Requires IIS patch
Changing the authentication scheme
You can change the authentication by using the adsutil.vbs script.
To modify the server so that it only supports NTLM authentication
• From the command prompt on the Windows server, enter the following command:
cscript adsutil.vbs set w3svc/$WebsiteID$/root/NTAuthenticationProviders "NTLM"
You can configure the server to attempt Kerberos authentication first before NTLM by changing the last parameter to Negotiate, NTLM.
Remember to restart the IIS server after the changes have been made.
Changing the per-connection/per-request NTLM authentication mode
By default, NTLM uses per-connection authentication.
To change per-connection NTLM to per-request NTLM
• From the command prompt on the Windows server, enter the following command:
cscript adsutil.vbs set w3svc/$WebsiteID$/root/AuthPersistSingleRequest TRUE
To change NTLM back to its default, replace the word TRUE with FALSE and restart the IIS server.
Note: When you use NTLM, the HTTP optimization module works best when per-connection authentication is set.
Changing the per-connection/per-request Kerberos authentication mode
By default, Kerberos uses per-request authentication. There are several ways to configure Kerberos to use per-connection authentication. For details, see
Per-connection or per-request Kerberos authentication.
HTTP authentication settings
The following table shows some of the recommended configurations for the HTTP Authentication optimization. In this instance, assume that it is not possible to make any modifications on the IIS server.
For example, if the authentication setting on the IIS server is per-request Kerberos, enabling Force NTLM forces the client to use NTLM and in turn, the HTTP optimization module can provide better optimization by using the URL learning and parse-and-prefetch features. If NTLM authentication is not an option, then the only possibility is to enable gratuitous 401.
If you modify the settings on the IIS server, then Force NTLM might not be necessary. In this case, only the first row of the following table is applicable.
The HTTP optimization module expects the default authentication behavior for both NTLM and Kerberos (in other words, per-connection authentication for NTLM and per-request authentication for Kerberos). Continuing with the example earlier, if the IIS server is configured to use the nonstandard authentication scheme by using per-request Kerberos and per-request NTLM, then using Force NTLM does not help as it changes from per-request Kerberos to per-request NTLM. In this case, URL learning and parse-and-prefetch is not effective.
IIS authentication | Recommended configurations | Notes |
per-connection NTLM | Reuse Auth. + Strip Auth. Header + Grat. 401 | |
Reuse Auth. + Strip Auth. Header | |
per-request Kerberos | Reuse Auth. +Force NTLM + Strip Auth. Header + Grat. 401 | N/A if NTLM is not an option |
Reuse Auth. +Force NTLM + Strip Auth. Header + Grat. 401 | N/A if NTLM is not an option |
Grat. 401 | |
per-request NTLM | Grat. 401 | |
per -connection Kerberos | Reuse Auth. + Force NTLM + Strip Auth. Header | N/A if NTLM is not an option |
Reuse Auth. | |
Change to per-request Kerberos and turn on | |
Grat. 401 | |
Don’t know | Reuse Auth. + Strip Auth. Header + Grat. 401 | |
Reuse Auth. + Strip Auth. Header | |
HTTP optimization module and proxy servers
Some network deployments might involve HTTP proxy servers to speed up resource retrieval, apply access control policies, or audit and filter contents. In general, the SteelHeads provide full optimization benefits even with proxy servers in place. Optimized connections can be limited or even hindered in the following circumstances:
• Proxy authentication - If the proxy server uses authentication, prefetching performance can be affected. Similar to web server authentication, proxy authentication can limit the prefetching capability of the connection where prefetched resources are served when the proxy server uses per-connection authentication. In the case of the per-request mode, prefetching is not possible as every single request requires user authentication. HTTP authentication optimization features apply to both web server and proxy authentication.
• Proxy caching - A proxy server can maintain its own local cache to accelerate access to resources. Generally, proxy caching does not thwart HTTP optimization. If it caches objects for an excessively long time, object prefetch table (OPT) might not provide full benefits as the retrieved resource might not be sufficiently fresh.
• Selective proxying - If the same web server is accessed directly by a client and through a proxy server, URL learning might not work properly. URL learning builds a prefetch tree by observing ongoing requests. This is based on the assumption that the same URL is requested by the client if the same base page is requested again.
When a prefetch tree is created without a proxy, the observed partial URLs comprise the tree. If another client asks for the same page but through a proxy, the proxy fails to forward the prefetched responses because it expects full URLs to be able to send the responses back to the client. Thus URL learning might not work well when proxy is selectively employed for the same host. This only happens with URL learning. Other prefetching schemes, such as parse-and-prefetch and object prefetch table, are not subjected to this issue.
• Fat Client - Not all applications accessed through a web browser use the HTTP protocol. This is especially true for fat clients that run inside a web browser that might use proprietary protocols to communicate with a server. HTTP optimization does not improve performance in such cases.
Determining the effectiveness of the HTTP optimization module
Figure: Response header contained in the line X-RBT-Prefetched-By shows that when an object is optimized by the HTTP optimization module, the response header contains the line X-RBT-Prefetched-By. The X-RBT-Prefetched-By line also contains the name of the SteelHead, the version of system, and the method of optimization. The different methods of optimization are:
• UL - URL learning.
• PP - parse-and-prefetch.
• MC - metadata response (pre-RiOS 6.0)
• PT - object prefetch table (RiOS 6.0 and later)
• AC - gratuitous 401
Figure: Response header contained in the line X-RBT-Prefetched-By
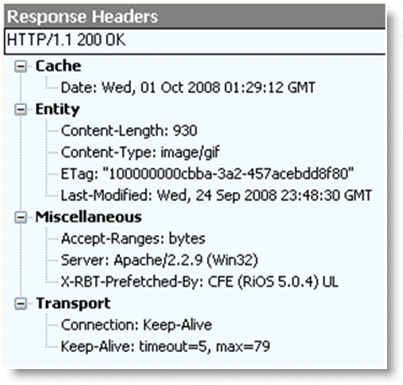
The response header can be captured by using tcpdump, HTTPWatch, Fiddler, or similar tools. Because the HTTP optimization module is a client-side driven feature, the capture must be done on the client itself.
Info-level logging
You can look at the client-side SteelHead log messages to determine whether or not the HTTP optimization module is functioning. The logging level on the SteelHead must be set at info level logging for the messages to appear in the log. If the HTTP optimization module is prefetching objects, a message similar to the following appears in the logs:
Sep 25 12:28:57 CSH sport[29969]: [http/client.INFO] 2354 {10.32.74.144:1051 10.32.74.143:80} Starting 40 Prefetches for Key->abs_path="/" host="10.32.74.143" port="65535" cookie="rbt-http=2354"
This only applies to the URL learning and parse-and-prefetch. No log messages are displayed for metadata response or object prefetch table.
The key specified in the log message is not necessarily the object that triggered the prefetch operation. In RiOS 6.0 and later, the log message includes the object that triggered the prefetch operation.
Use case
While automatic configuration is typically the preferred method of configuration, you have the option of manual configuration. The following use case shows a manual configuration.
A customer has a 1.5 Mbps link with 100 ms latency between the branch office and the data center. The PCs in the remote office are running Microsoft Windows XP with Internet Explorer 7. Users in the remote offices are complaining of slow access for SAP Netweaver and Microsoft SharePoint. The SAP Netweaver server has an IP address of 172.30.1.10 and the Microsoft SharePoint server has an IP address of 172.16.2.20.
Because both SAP Netweaver and Microsoft SharePoint are well-known applications, the customer configured the following on the client-side SteelHead.
Figure: Two subnet server settings showing the new recommended SharePoint settings
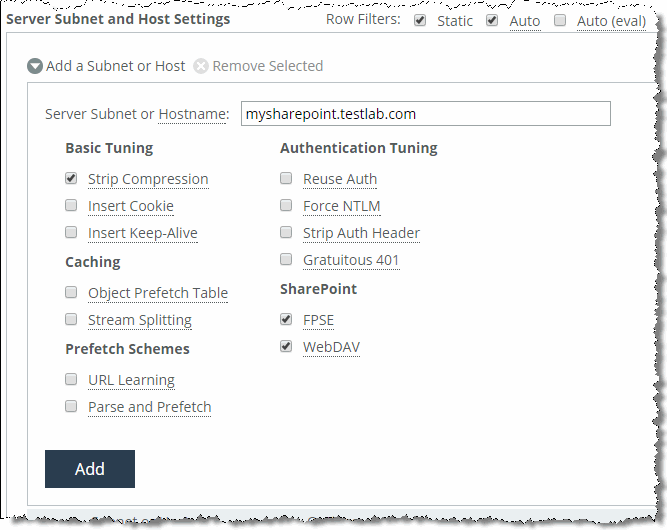
After configuring the settings above, the customer noticed a significant improvement in response time for SAP Netweaver but no changes for Microsoft SharePoint—even though the connections are optimized with good data reduction. One of the users mentioned that the Microsoft SharePoint portal required authentication, which might be the reason why parse-and-prefetch did not work. Unfortunately, the system administrator in charge of the SharePoint portal cannot be reached at this moment and you cannot check the authentication setting on the server.
Instead of checking the authentication on the server, you can capture tcpdump traces and check for the authentication scheme in use.
Figure: TCP dump trace confirming Kerberos enabled shows the server has Kerberos enabled and hence the client attempts to authenticate using Kerberos first.
Figure: TCP dump trace confirming Kerberos enabled
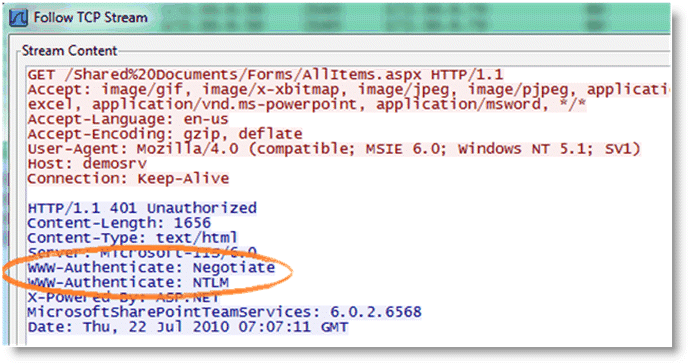
Figure: TCP dump trace showing per-request Kerberos confirms that by scrolling through the trace, the per-request Kerberos is configured on the server.
Figure: TCP dump trace showing per-request Kerberos
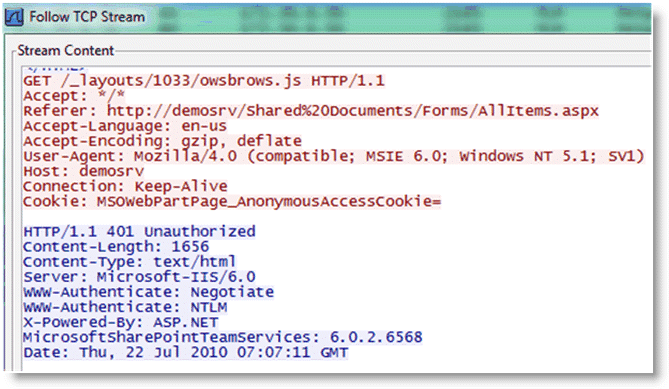
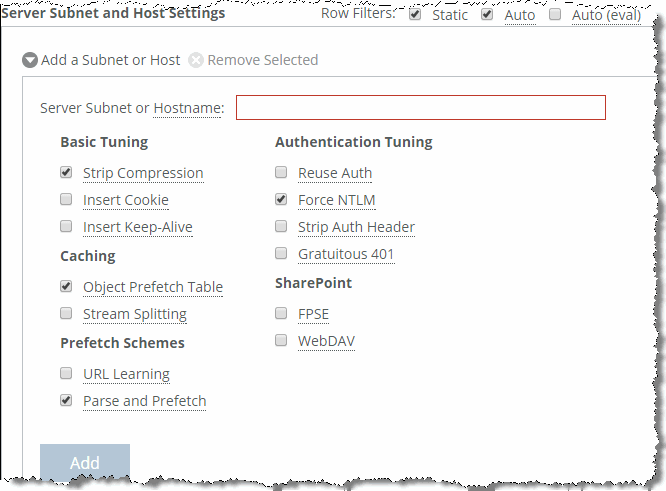
Figure: Enable force NTLM shows that given this information, the best option is to enable
Force NTLM for the SharePoint server.
Figure: Enable force NTLM
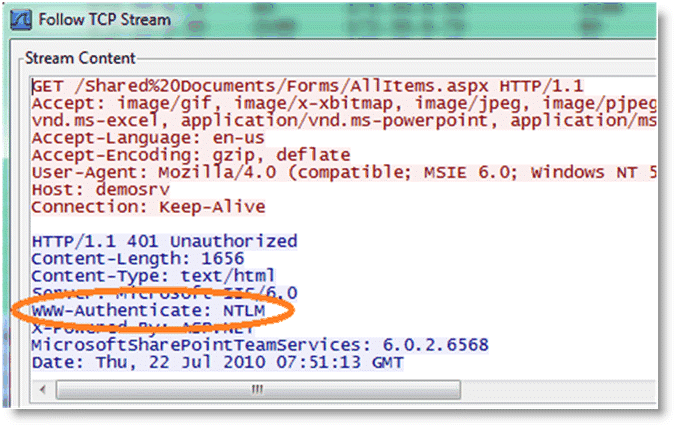
Taking another trace on the client-side SteelHead confirms that the only authentication option available is NTLM. Because there is no other authentication option but NTLM, the client is forced to authenticate via NTLM and parse-and-prefetch and prefetches can once again function as before.
Figure: Trace stream showing NTLM as the only authentication available
In this instance, it is not necessary to enable the other features, as the entire transaction took place over a single connection. If the client uses multiple TCP connections, then it might be necessary to enable reuse auth, strip auth header, and gratuitous 401. Enabling the rest of the features does not provide any benefit in this instance, but it does not cause any problems either.







