SteelConnect with Office 365
This topic describes how to integrate Microsoft Office 365 with SteelConnect to improve the end-user experience across office locations. It includes these sections:
Office 365 networking partner overview
In SteelConnect 2.13, Riverbed SD-WAN is designated as a qualified networking solution and certified as “Works with Office 365” to provide an optimal end-user experience (certification is in progress and is expected in September 2019). Riverbed partners with Microsoft to provide full support that complies with its Office 365
connectivity principles.
The client components of Office 365 such as Outlook, Skype for Business, and SharePoint run on user computers at branch locations and connect to other components of Office 365 running in Microsoft data centers. Office 365 performance is determined by several factors, including network reliability, sufficient bandwidth, and how latency affects application performance between the Office 365 clients and the Office 365 service front-door endpoints, or edge nodes, in the Microsoft global network.
To optimize the end-user experience for Office 365 traffic, Microsoft recommends steering Office 365 traffic using direct-to-net or Direct Internet Access (DIA), avoiding any backhauling of traffic to a central proxy. Because Office 365 traffic such as Outlook, Word, and Skype are sensitive to latency, backhauling this traffic can introduce additional latency. You can define SteelConnect traffic rules to customize the path preferences and default routing.
In SteelConnect 2.13, Office 365 acceleration is supported on SDI-2030 gateways and SteelHead SD appliances. It is not supported on SDI-130, SDI-330, and SDI-1030 gateways.
Office 365 service
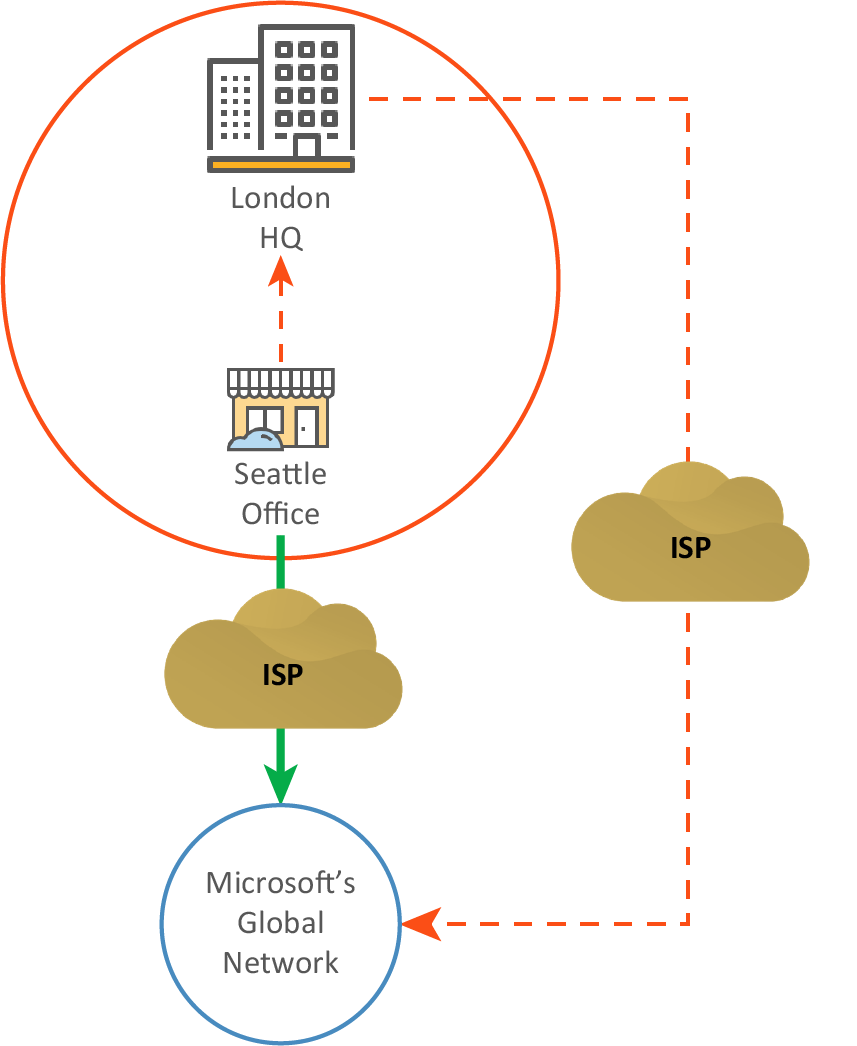
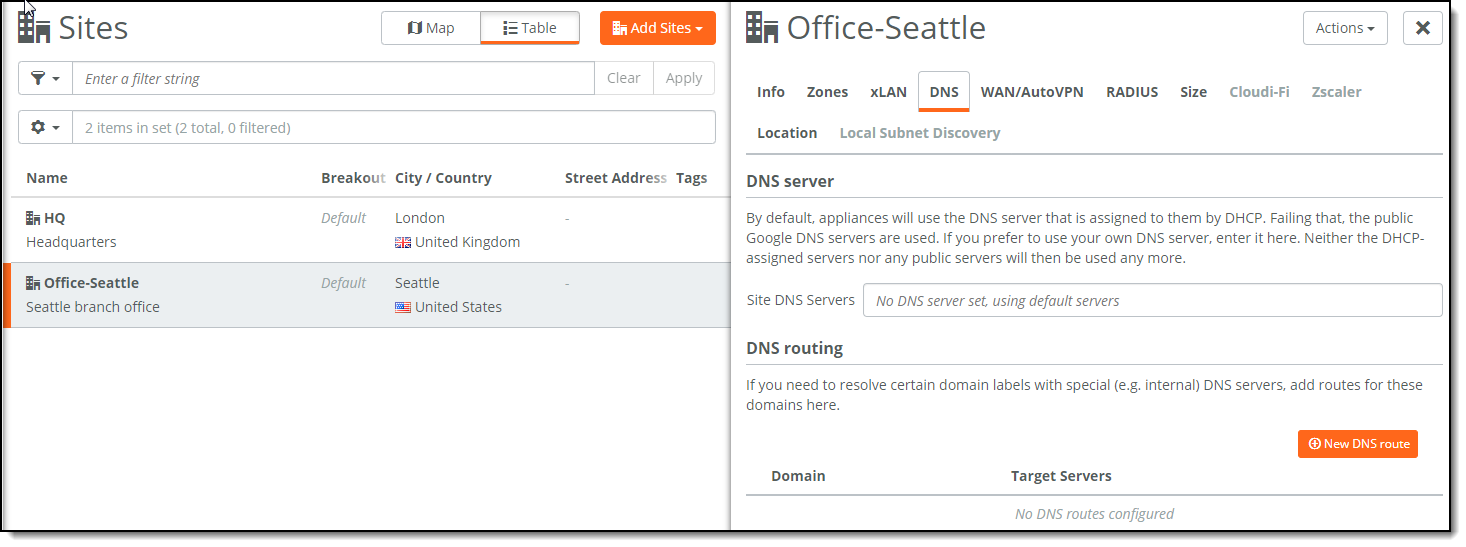
To minimize name resolution latency, Microsoft recommends provisioning local DNS servers in branch sites to provide local name resolution for Office 365 endpoints.
Provide a local DNS server for each site in SCM
SteelConnect integration
The SteelConnect Application Control Server (ACS) supports the Microsoft Office 365 REST APIs that catalog and return up-to-date information about the front-door endpoints. SteelConnect uses the endpoint data to enable direct routing of the internet traffic from the branch to the closest front-door endpoints.
SteelConnect provides methods to steer Office 365 traffic directly to the closest internet either by using the Microsoft default settings or by customizing the path preferences to accommodate regional egress points and centralized routing.
We recommend the single-click configuration using the Microsoft default settings.
Security considerations
Microsoft provides Office 365 native security to reduce network security risks, including bypassing proxy servers and device inspection proxies. Office 365 traffic is already encrypted using secure protocols such as HTTP and SRTP.
To maintain security without sacrificing the end-user experience, SteelConnect offers integration with the Riverbed SaaS Accelerator, or direct-to-net routing via the Zscaler proxy. All available WANs are options to send Office 365, including Zscaler and Saas Accelerator. For example, you can set your path preference to a Zscaler path to steer your Office 365 and internet traffic through the Zscaler service to the Microsoft cloud while maintaining a high level of security.
For details on the Riverbed SaaS Accelerator, see
About SaaS Accelerator.
How SteelConnect steers Office 365 traffic
To identify Office 365 traffic, Microsoft uses endpoint signatures, which are essentially a list of URLs and IP addresses. Microsoft updates the endpoint signatures as needed. The SteelConnect appliance polls the Office 365 Endpoints web service at regular intervals to get the latest endpoint signatures. The appliance downloads any new or updated signatures and stores them in a SteelConnect database, so you don't have to worry about accommodating any URL changes in the Office 365 applications.
When a request for an Office 365 application arrives on a SteelConnect appliance, the application classifier does a first-packet classifier lookup to identify and mark the Office 365 traffic. After classifying the traffic, automatically generated or custom traffic rules take effect and route the traffic over the best path.
Optimizing Office 365 traffic with SteelConnect
The most common ways to optimize Office 365 traffic using SteelConnect are:
1. A single-click deployment that uses the Microsoft endpoint signatures to identify and steer traffic to the closest internet using the best practices. This is the recommended deployment.
2. Disabling the Microsoft default settings and customizing the path preferences and default routing.
Integration using the Microsoft default settings (recommended)
We recommend the single-click deployment method, which uses the Microsoft default settings and the SteelConnect application classifier to:
• identify and differentiate the Office 365 traffic from the generic internet-bound traffic.
• automatically configure traffic rules that group the Office 365 traffic.
• determine the best path according to the traffic endpoint signature.
• route the traffic to the Microsoft front doors located closest to the branch. After the traffic reaches a front door, it travels through the Microsoft network to reach its destination.
• enable the least restrictive access between the clients and the closest Office 365 service front doors.
Steering traffic using endpoint classification
Office 365 endpoints are a set of network addresses and subnets. Endpoints are segregated into these categories:
• Optimize - This group contains a small number of endpoints (approximately 8) that provide connectivity to every Office 365 feature and service. These endpoints require an optimized path and are very sensitive to latency and unimpeded connectivity using Microsoft hosted IP addresses and URLs. All of the endpoints in this group are hosted in Microsoft data centers. The URLs in this group must bypass proxy servers, packet inspection devices, and WAN or VPN network hairpin turns. Although the Optimize group contains a small number of endpoints, it consists of over 75 percent of all Office 365 bandwidth, data volume, and connections.
• Allow - This group includes a larger number of endpoints (approximately 100) that require low latency and unimpeded connectivity. The endpoints in this group bypass SSL break and device inspection. Good connectivity to these URLs is required for Office 365 to operate normally.
• Default - For traffic that doesn’t need an optimized path, this group includes all endpoints that don’t fall into the Optimize or Allow groups. The Default group steers the traffic as typical internet traffic, similar to the default paths used for web browsing. For example, the Default group directs the traffic to the default internet egress location for the organization’s WAN. The standard internet latency is acceptable for this group because the traffic isn’t susceptible to latency variations.
Enabling Office 365 optimization automatically creates three read-only traffic rules: O365 Optimize, O365 Allow, and O365 Default. If you have already configured rules with these names, they will be overwritten, so be sure to rename any rules that you want to keep before enabling Office 365 optimization.
To enable O365 traffic optimization using the Microsoft default settings
1. In SCM, choose Network Design > Office 365.
2. After Office 365, click On.
By default, the default option for all categories is direct internet access (DIA) and rule fall through.
When rule fall through is enabled, if the rule matches but all selected paths are unavailable, the traffic flow falls through to the next traffic rule, other available uplinks, or the default routing. When rule fall through is disabled, the packets are dropped.
3. Click Submit.
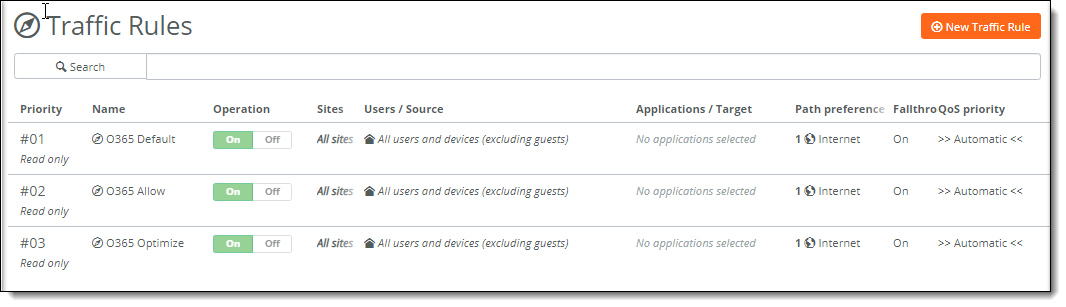
After you enable Office 365 using the Microsoft default settings, SteelConnect automatically adds these read-only traffic rules to the Rules > Traffic Rules page to group the Office 365 traffic. The rules are positioned at the bottom of the traffic rule list when other traffic rules exist. The rules correspond with the Microsoft endpoint classification:
• O365 Allow: Includes Lync Allow, Outlook Allow, SharePoint Allow, and so on.
• O365 Default: Includes Lync Default, Outlook Default, SharePoint Default, and so on.
• O365 Optimize: Includes Lync Optimize, Outlook Optimize, SharePoint Optimize, and so on.
SteelConnect uses these traffic rules to steer the traffic to the closest front door.
You can change the position of the automatically created traffic rules, but you cannot edit or delete them. The rules are deleted after you disable Office 365 optimization.
Read-only traffic rules for O365 traffic
Integration using custom path preferences
To steer O365 traffic using custom path preferences for the groups
1. In SCM, choose Network Design > Office 365.
2. After Office 365, click On.
3. After Microsoft Defaults, click Off.
4. Click the search selector next to Optimize and select the first path preference for the endpoints that fall into the Optimize group.
Add more path preferences as needed.
5. Click the search selector next to Allow and select the first path preference for the endpoints that fall into the Allow group.
Add more path preferences as needed.
6. Click the search selector next to Default and select the first path preference for the endpoints that fall into the Default group.
Add more path preferences as needed.
Use the up and down arrows to reprioritize the path preferences.
7. After Rule fall through, click On to send the traffic flow through to the next traffic rule or the default routing if the rule matches but all selected paths are unavailable.
Click Off to drop the packets if the rule matches but all selected paths are unavailable.
8. Click Submit.




