SteelConnect and Network Security
Providing secure internet access, while preventing malicious content from entering an organization, is critical to maintaining employee productivity and defending the network against threats.
The SteelConnect gateway provides these security capabilities:
•Perimeter firewall - Easy-to-configure inbound/outbound firewall rules build a secure wall to control access into and out of the different segments of the internet edge. This functionality (along with a suite of other services, such as network address translation (NAT) and policy-based network zoning) provides effective controls to mitigate the next step of a network intrusion and limits further movement across the network or propagation of a threat. SteelConnect logging capabilities support troubleshooting and policy-compliance auditing.
•VPN concentrator - SteelConnect automatically forms secure IPsec VPN tunnels with AES-256 encryption between your sites. IPsec VPN is configurable in full-mesh or hub-and-spoke modes from the centralized SteelConnect Manager.
This topic describes how SteelConnect can act as a robust perimeter firewall for your organization and addresses some common security use cases in the enterprise, including how to enforce firewall policies at branches for access control to zones and the internet.
SteelConnect as a perimeter firewall
Defending the network edge is an essential component for detecting and protecting the network from unwanted traffic, potentially malicious content, and intrusion attempts, and a perimeter firewall is the primary defense in a private network. The perimeter firewall identifies and logs these threats for the network administrator.
The perimeter firewall also blocks incoming network traffic from accessing internal networks and hosts and blocks outgoing traffic from accessing undesirable external networks and hosts. For example, organizations might block access to gaming sites or other social media sites. As such, a perimeter firewall can be considered as having an internal and external interface.
With SteelConnect’s networking and security integration, organizations can use internet connections while mitigating security risks. Also, with a centralized cloud-based console, business-intent policies are easy to configure and enforce for your entire organization.
SteelConnect security features
Most enterprises backhaul data from their branch locations to their data centers for thorough inspection of the data going to and from the internet. Alternatively, steering software as a service (SaaS) traffic directly to the internet enables enterprises to offload their WAN network at a lower cost and reduced latency than backhauling traffic to the remote data center. Both backhaul and direct-to-net architectures require a network security stack to protect against malware, phishing, and other security threats. They also provide the ability to apply consistent security policies for all users, no matter where they connect.
Riverbed works with companies that develop specialized security functions to provide a holistic defense. Riverbed has partnered with Palo Alto Networks, Zscaler, and others to provide additional advanced security functions to organizations ensuring a stringent security posture at the branch offices as well as the data centers.
The following table summarizes SteelConnect firewall capabilities in addition to the advanced features provided by partnering with other security vendors.
| Feature | SteelConnect only | SteelConnect + security partner |
Perimeter firewall | Application-based stateful firewall | | |
Granular allow/deny filtering rules | | |
Robust/hardened gateway | | |
VPN capabilities | | |
NAT capabilities | | |
Logging | | |
Advanced security functions | Intrusion detection/prevention | | |
Content scrubbing/malware detection | | |
Acceptable use policy enforcement | | |
Other InfoSec compliance requirements | | |
Application-defined security with granular filtering rules
Application definitions are a way to attach a business relevancy to all traffic that goes through your network. The Riverbed Deep Packet Inspection (DPI) engine can identify and classify business-critical and nonessential network traffic beginning with the first packet of the traffic flow.
With SteelConnect, you can build a secure firewall policy that regulates who has access and to what resources. Security policies can apply to the entire network, such as a single security policy to turn zone access on and off. You can also make the policy more granular to accommodate specific security needs. For example, you can create firewalled zones that require specific user permission to use specific applications. You can also enable access control and data protection for registered and unregistered mobile phones, tablets, and laptops.
The outbound and internal rules specify a source, a target, and an action. The source can be either a special catch-all selection (such as all registered users) or a custom selection of user groups, device groups, individual users, individual devices, or policy tags. We recommend that you base the outbound and internal rules on user groups and device groups, and then make exceptions using policy tags.
Policy controls are built on two types of rules:
•Allow/deny firewall rules - Define the policy for internal users and devices accessing internal or external applications.
•Inbound access control rules - Define the policy for external (internet) access to internal applications. Inbound rules offer optional support for NAT, port translations, and an external host whitelist.
You can easily create, review, enable, and disable these policy controls for the whole organization using SCM as opposed to creating tedious access-control lists and mapping them to interfaces on individual routers at each site.
Policy controls
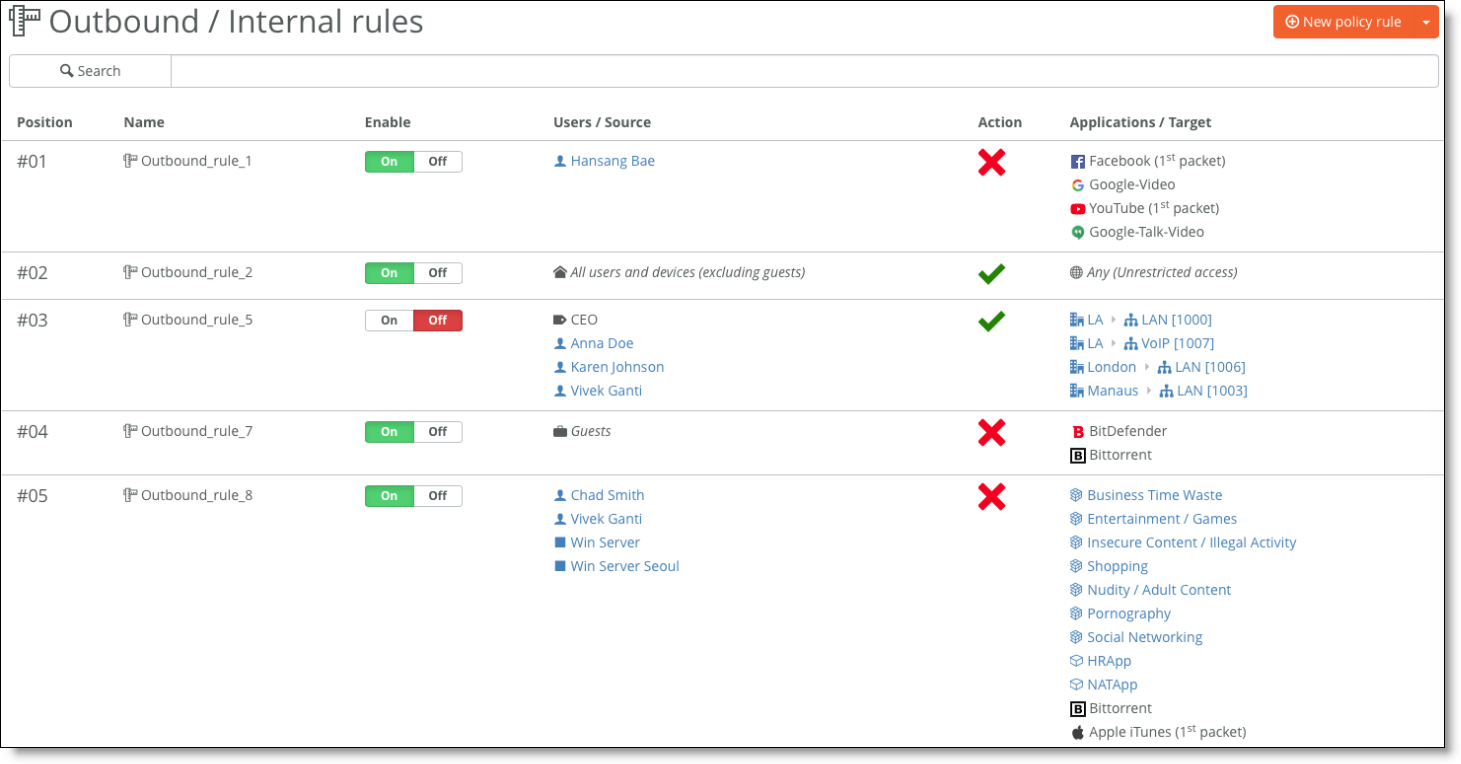
For more details, see “Enabling Security Using Rules” in the SteelConnect Manager User Guide.
WAN hardening and network zoning
Network hardening is a process to address network security vulnerabilities by implementing software patches, introducing new security systems, and adopting better configuration and operation policies.
You can deploy SteelConnect gateways at the internet edge to harden the enterprise network at branches. No unauthorized outside traffic is allowed to enter the branch unless the administrator permits it by configuring granular inbound and outbound firewall rules.
By default, internet uplinks are hardened and all traffic is denied.
You can create inbound rules to allow only specific traffic on specific TCP/ UDP ports to or from specific servers both inside and outside the local branch network. Secure IPsec VPN tunnels allow for data to be encrypted and only secure data can transfer between branches over the internet.
SteelConnect zones help segment the network, and they help maintain control and organization of traffic. The use of zones within NAT rules gives an organization more flexibility and simplicity with its firewall management. In a world where Internet of Things (IoT) devices such as HVAC systems are used as a platform of attack to steal critical customer data, many organizations are taking steps toward network segmentation, such as building multiple subnetworks (overlays) within a shared network (underlay).
SteelConnect makes WAN segmentation radically simpler. You simply need to define a policy describing the underlying network. The policy is then distributed across the nodes in the SD-WAN network, which creates the multipoint (IPsec) tunnels linking these nodes defined in the policy. SteelConnect’s built-in software-defined intelligence also allows for automatic firmware updates to gateways that keep security patches and hotfixes current.
As of version 2.10, SteelConnect does not support Layer 3 segmentation and isolation through virtual routing and forwarding (VRF).
VPN capabilities
AutoVPN
AutoVPN is a SteelConnect feature that automatically connects multiple sites with IPsec VPNs, without tedious manual configuration providing a fast way to create a secure and resilient VPN backbone between all your sites.
AutoVPN can be split into two general operating modes:
•RouteVPN - A Layer 3 IPsec VPN between internal networks across physical sites.
•SwitchVPN - A bridged Layer 2 IPsec VPN that extends zones across multiple sites.
For more details about AutoVPN, see “Secure overlay tunnels” in the SteelConnect Manager User Guide.
IPsec VPN with third-party vendor
Some deployments require a SteelConnect gateway connection to an IPsec VPN built by a third-party vendor. You can connect to a third-party VPN using classic VPN. Classic VPN creates a manual VPN tunnel using the standard IPsec IKEv1 or IKEv2 protocol.
Classic VPN configurations can classify traffic based on TCP/UDP port numbers, providing a more granular approach to traffic steering. Classic VPN is an easy and flexible method to use when:
•connecting to a third-party IPsec VPN gateway, such as a firewall or a Unified Threat Management (UTM) appliance.
•migrating from an existing VPN solution to SteelConnect RouteVPN. You can even use the IP subnets of the remote networks and rules.
•integrating sites with overlapping IPv4 addresses, using one-to-one NAT configuration. When connecting networks through VPN that use the same IP addresses on both sides, it’s impossible to create a simple IPsec tunnel, as routing through the tunnel doesn’t work. Classic VPN uses an integrated NAT layer, in which you can map an overlapping network one-to-one into a virtual network. This means that you can communicate with the remote location using the virtual NAT network and prior to entering the tunnel, the system transparently replaces IPv4 addresses with the matching address from the remote side, allowing both networks to remain unchanged.
For more details about building IPsec tunnels with a third-party vendor, see “Connecting to a third-party VPN” in the SteelConnect Manager User Guide.
By default, the outbound rules for a firewall let users and guests access the internet only. Communication between sites is disallowed by default through an explicit “deny” rule.
Default firewall rules with guest access to the internet shows the default firewall rules with guest access to the internet.
Default firewall rules with guest access to the internet
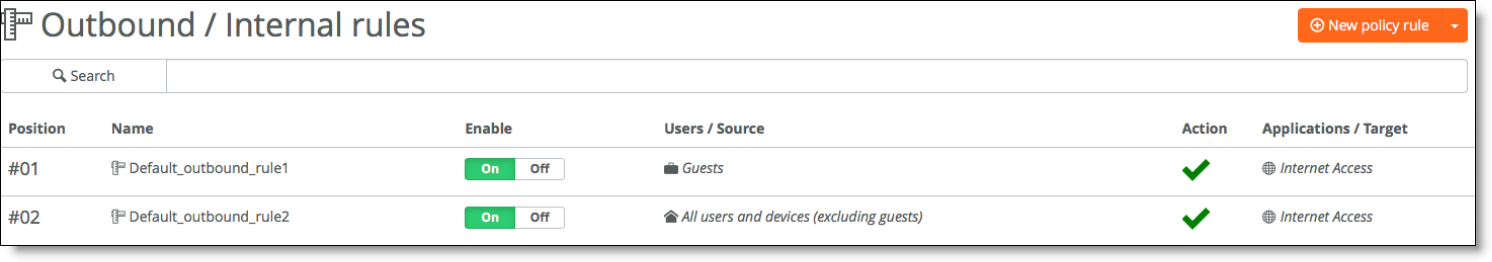
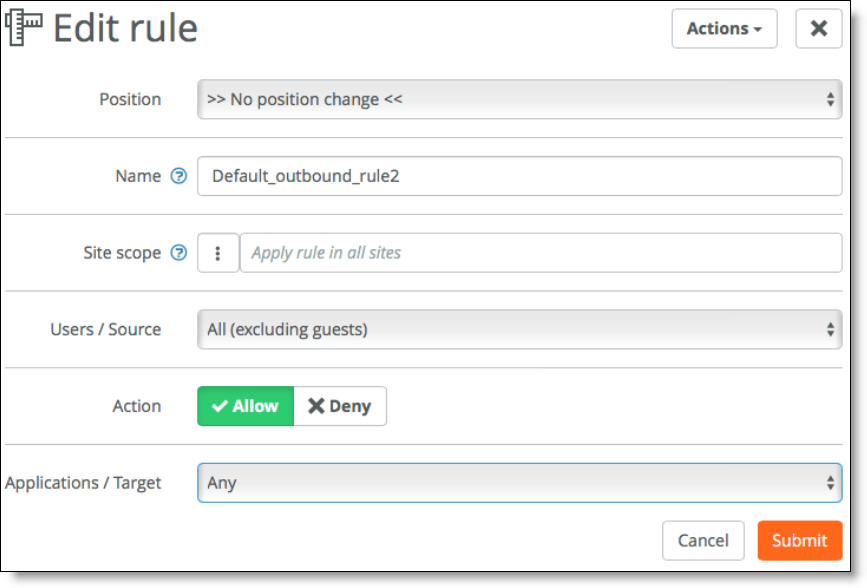
To set up access between sites, you can update the second default rule and allow users (excluding guests) to access all sites.
Allowing guest access to sites
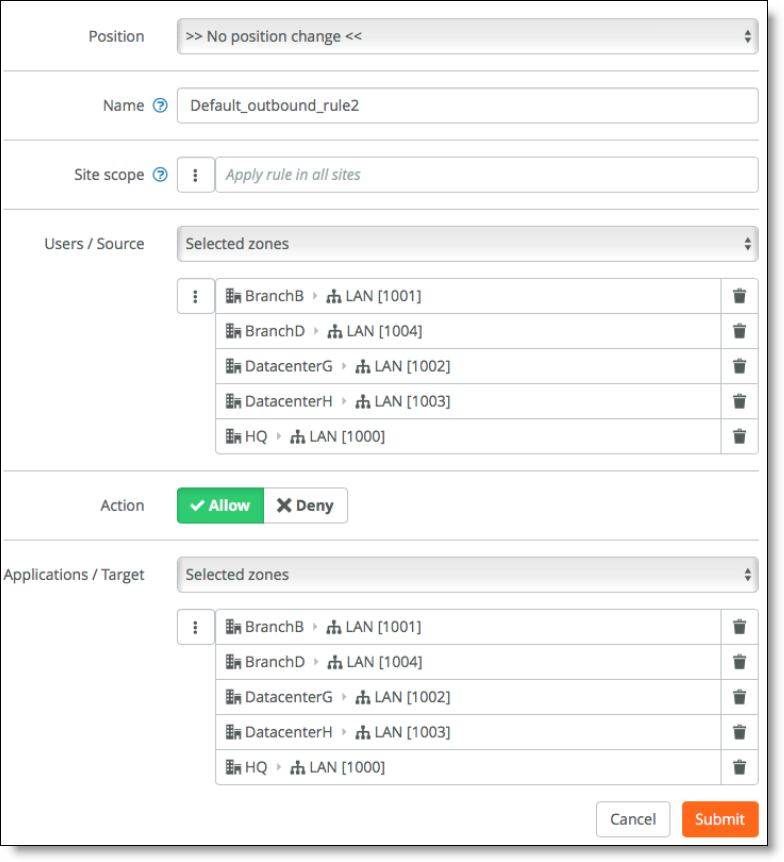
You can also define more granular rules depending on security constraints.
Defining access details
Inbound NAT capabilities
Network address translation (NAT) is the mapping network address to alternate and secure addressing. NAT helps improve security and decrease the number of IP addresses an organization needs.
SteelConnect gateway offers two inbound NAT modes:
•Dynamic NAT (DNAT) - Translates the source address for all outbound connections from the private address of the source host to a public address (typically the gateway public IP). This mode replaces the target address. It requires the target system to use the SteelConnect gateway as its default gateway.
•Full NAT - Replaces the source address of the incoming connection with the internal gateway address. This mode makes sure the return traffic is sent back to the SteelConnect gateway, even if the system uses a different default gateway.
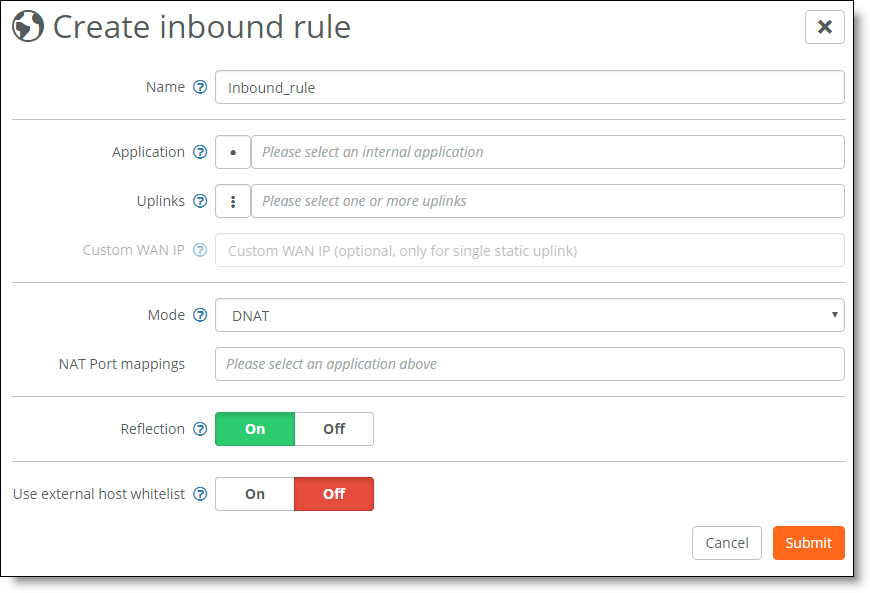
You can create inbound rules to allow only specific connections to reach your internal NAT servers. While doing so, you are given the option of configuring No NAT, DNAT, or Full NAT as shown in the Mode field.
NAT modes
Visibility and logging
Visibility is crucial to security. You can’t protect what you don’t know about.
With SteelConnect Manager, you have a centrally managed system of products designed from the ground up to work together and you have total visibility into your network. You can use the Visibility page to read logs, view a history of the DHCP server IP address assignments, see if and where traffic was blocked, and generate user reports. You can export logs to syslog servers.
SteelCentral Insights for SteelConnect (Insights) also provides visibility into your SD-WAN network. Insights collects data from SteelConnect Manager securely using SteelFlow (a Riverbed-specific form of NetFlow) and REST APIs. Insights uses this data to provide visibility into usage and availability about your overall network, specific sites, servers, applications, and users. With this information, you can make informed policy and deployment decisions, monitor and troubleshoot performance issues, and plan for changes.
For more information see the SteelConnect Manager User Guide.






