Traffic Redirection
This chapter describes the redirection protocol and the redirection controls, and it provides general recommendations for redirection in Interceptor deployments.
Interceptors control traffic redirection to SteelHeads and SteelHead acceleration targets for different types of traffic using the following techniques:
• In-path rules—Control whether locally initiated connections are redirected.
• Hardware-assisted pass-through (HAP) rules—Control what traffic is passed through in hardware on supported network bypass cards.
• Load-balancing rules—Control what traffic is redirected and how traffic is distributed to the SteelHead cluster.
The three types of redirection control rules control what traffic is redirected and potentially accelerated by a SteelHead.
Figure: Redirection packet process overview shows how the control rules are used when a packet arrives on the LAN or WAN interfaces of the Interceptor.
Redirection packet process overview
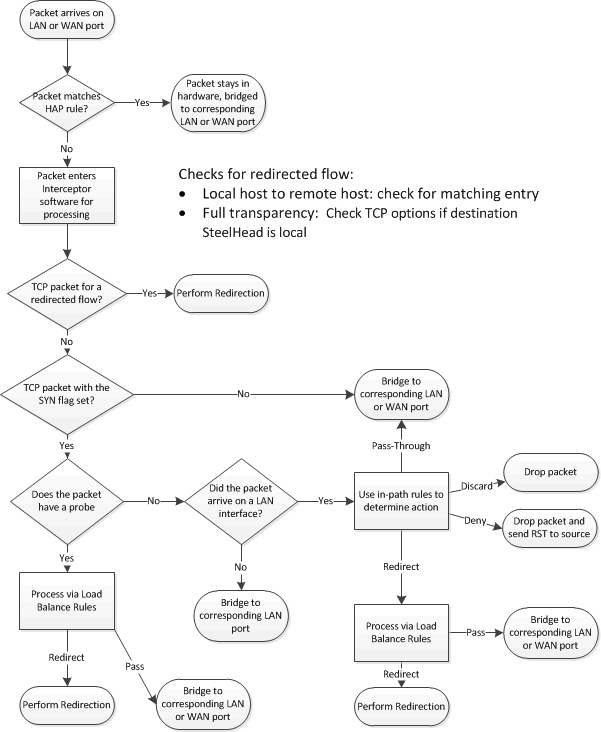
First the Interceptor checks whether the packets arriving on a LAN or WAN port match an HAP rule. If they match, the Interceptor bridges the packet in the hardware corresponding to the port. If not, the Interceptor checks whether the packet belongs to the flow that is redirected. If the packet doesn’t belong to that flow, it could be because the flow is going through autodiscovery or because the flow previously went through autodiscovery and started acceleration.
You can’t use HAP rules for traffic when autodiscovery must decide whether to accelerate or not. HAP rules are only useful for traffic you know you never want redirected or accelerated. HAP can be applied on optimized traffic,whichctakes 300 seconds for new rule to take effect.
If the packet doesn’t correspond to a redirected flow, in-path and load-balancing rules determine the next action. TCP SYN packets from a LAN interface are processed with the in-path rules and can be either dropped, passed-through, or proceed for further processing with the load-balancing rules. Interceptor in-path rules aren’t checked for packets with an automatic discovery probe, such as WAN-side or LAN-side SYN+ packets.
Typically in an Interceptor cluster, all Interceptors have the same control rule set. You aren’t required to have the same control set, but differences in rules can lead to surprising behavior. For example, as shown in
Figure: Redirection packet process overview, HAP rules are checked in hardware before a redirect flow entry is checked in software. This order results in wrong behavior if one Interceptor in a cluster begins redirecting packets when another clustered Interceptor has a HAP-pass rule that matches the connection.
Situations in which different rules are useful include deployments in which Interceptors and SteelHeads in the same cluster are in locations that have some small, but significant, latency separating them. For details on deploying Interceptor clusters across distances, see
Intra-cluster latency.


