Using Amazon Virtual Private Cloud
This chapter describes the Amazon Virtual Private Cloud (VPC). It includes these sections:
About Amazon VPC
Amazon VPC enables you to create a virtual topology (including subnets and route tables) for your Amazon Elastic Compute Cloud (EC2) resources. It enables you to create an isolated portion of the AWS cloud (a VPC) and launch Amazon EC2 instances that have private (RFC 1918) addresses in the range of your choice (for example, 10.0.0.0/16).
Amazon VPC provides various levels of security. At the highest level, the VPC enables you to connect to a private network through a VPN tunnel. You can also access the private subnet through an Internet gateway that enables traffic to flow between the Internet and all the instances in your VPC.
You can also configure a VPC to be in-between, with both a VPN gateway and an Internet gateway to enable some instances to receive Internet traffic (for example, web servers), whereas others could remain unexposed (for example, database servers).
This section describes how to deploy a SteelHead-c virtual appliance using different levels of security and includes configuration caveats.
Using a VPC with a VPN connection to the data center
When you connect to the Amazon VPC through a VPN tunnel using either a software or hardware IPsec gateway, you use the highest level of security. In this scenario, the SteelHead-c has a single IP address from the pool of private VPC addresses. Therefore, there is no special configuration required to deploy the SteelHead-c. As long as you connect the SteelHead-c to the Riverbed Cloud Portal, both autodiscovery and auto-reconfiguration (that is, when instances change their IP addresses, the portal automatically detects it) works.
Using Amazon VPC through a VPN tunnel (without NAT) shows how to deploy SteelHead-c and servers in Amazon VPC with a VPN connection to the data center.
Using Amazon VPC through a VPN tunnel (without NAT)
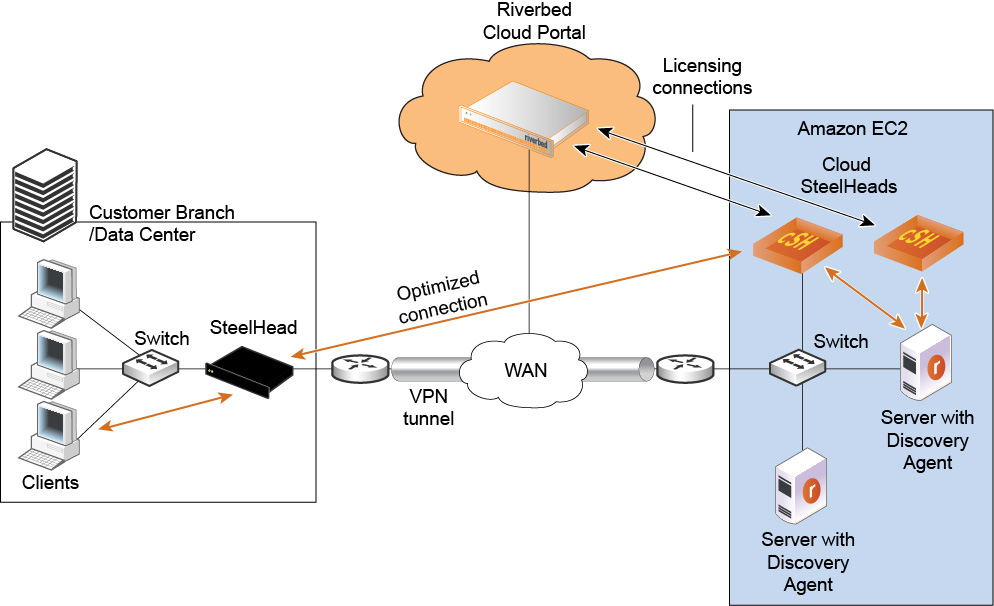
In the network shown in
Using Amazon VPC through a VPN tunnel (without NAT), servers in Amazon use private IP addresses. The VPC with VPN tunnel provides an extension of your intranet into AWS.
Using a VPC without a VPN connection to the data center
When you use a VPC without a VPN connection to the customer data center, you access the Amazon VPC through the Amazon Internet gateway that translates the private IP addresses in the VPC to public IP addresses. In this scenario, the Riverbed Cloud Portal detects the private IP address of the
SteelHead-c and Discovery Agent servers. It also detects the elastic IP address that you manually configure using the AWS console. Ensure that you configure the ACL and security groups in the AWS console so that the SteelHead-c can communicate with the Riverbed Cloud Portal.
Using Amazon VPC through the internet (with NAT) shows how to deploy the SteelHead-c and server in Amazon VPC using a VPC without a VPN connection to the customer data center.
Using Amazon VPC through the internet (with NAT)
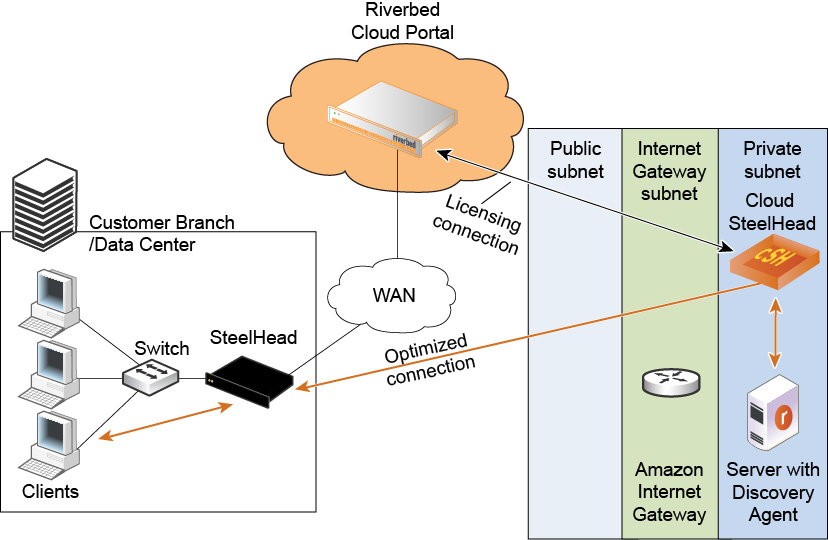
Configuring security groups
This section describes how to configure security groups when you connect to the VPC through the VPN (without NAT) and when you connect to the VPC through the Internet (with NAT).
Connecting to the VPC through the VPN (without NAT)
Configure a VPC through the VPN by modifying the security group of the AWS EC2 instances running the Discovery Agent:
1. Add the private IP address of the remote server for the ports used by the application to optimize.
2. Add the security group of the SteelHead-c (enable access to all ports).
3. On the SteelHead-c security group, add the public IP address of the remote SteelHead and enable it to access port 7800 and port 7810.
Connecting to a VPC through the internet (with NAT)
Configure a VPC without IPsec tunnel by modifying the security group of the AWS EC2 instances running the Discovery Agent:
1. Add the public IP address of the machines that access the server from outside the VPC, such as the virtual appliances in the customer data center.
2. Add the security group of the SteelHead-c (enable access to all ports).
3. On the SteelHead-c security group, configure these settings:
–Add the public IP address of the machines that access the server from outside the VPC, such as the virtual appliances in the customer data center.
–Enable access to port 7800 and port 7810 for TCP.
–Add the private IP addresses of all local AWS instances running the Discovery Agent, allowing access to all ports for TCP and UDP.



