Secure Transport
Secure transport enables you to integrate and configure encryption services with path selection. Secure transport enables simple, secure, and manageable group encryption for inter-SteelHead communication for path selection deployments. Secure transport requires:
• SteelHeads deployed physically in-path and in the natural flow of traffic
• SteelHeads at each end of the path to be secured
• SSL license
• Configured path selection policies
• Secured paths
A key feature for the hybrid enterprise is to leverage multiple paths between sites. This feature enables diversity across a variety of networks for resiliency. More importantly this feature enables you to more efficiently select the network delivery mechanism for an application.
However, not all network paths are equal in terms of exposure to security risks. A common technique to secure traffic is to encrypt traffic at the IP layer with IPsec, which prevents disclosure if traffic is intercepted in transit. This type of encryption also prevents replay attacks from an attacker in the middle of the chain.
Secure transport is integrated with path selection and provides a method to configure and enable encryption services for traffic over a path. Secure transport provides security services at the IP layer for path selection—you can add security for an application, application groups, or custom applications based on the path the traffic travels. By integrating encryption services into the SteelHead, the secure transport feature delivers a secure path between peers over a private WAN, public internet, or a hybrid network.
One key capability of secure transport with path selection managed by the SCC is that each peer automatically joins a security group with other SteelHeads whenever you mark a network as securable and assign the network to the site the peers belong to. This capability has benefits over other forms of encryption services that require configuration at both ends and policies to select the traffic that’s encrypted.
One benefit is that automatically joining a security group requires minimal configuration because it is easier to implement the network design changes when you want to include new sites or new networks that require encryption. Additionally, configuration is done centrally on the SCC, which minimizes the potential for configuration errors as opposed to configuring encryption separately on each device. Also, other virtual private network (VPN) technologies require traffic to match a policy, which then triggers negotiation between devices performing encryption before the encryption is actually performed. With secure transport, encryption is applied packet-by-packet using IPsec tunnel mode.
Secure transport uses a group model for encryption services. In a group model each appliance registers with a controller to learn network-reachability information, policies, and important material to use for encrypting traffic. Each appliance also performs reachability tests to ensure the path is available.
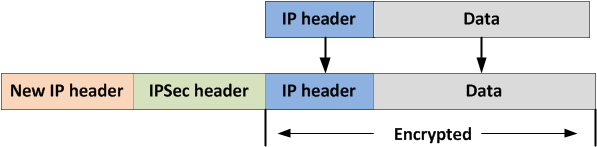
Secure transport uses standards-based IPsec using AES-256 and SHA-2 to secure traffic over a path. Secure transport uses IPsec tunnel mode of which the original IP addresses are part of the encrypted payload (
Figure: Tunnel mode).
Tunnel mode
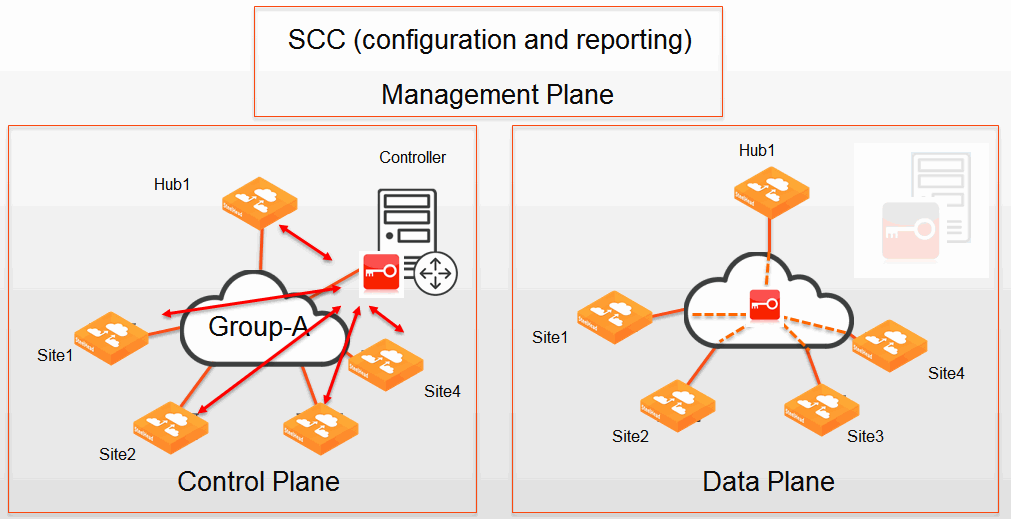
You manage the encryption services centrally through the SCC. Functionality of secure transport is separated into the:
• management plane (
here).
Figure: Secure transport functionality shows how the functionality of secure transport performs at a high level. The SCC works with the management plane for configuration and reporting, a SteelHead in the group acting as the controller manages the control plane actions (such as distributing network-reachability information and encryption key information), and the SteelHeads in the group encrypt traffic for the data plane.
Secure transport functionality