SSL with SteelCentral Controller for SteelHead Mobile
SSL is a cryptographic protocol that provides secure communications between two parties over the Internet. This section includes the following topics:
Traditional SSL OptimizationAdvanced High-Security SSL OptimizationConfiguring SteelCentral Controller for SteelHead Mobile and SSLSupported TLS Versions with SteelHead MobileMultiple Mobile Controllers and SSLTypically in a Web-based application, the client authenticates the server. You install an SSL certificate on a Web server for the client to check the credentials of the certificate to make sure it is valid and signed by a trusted third party. Trusted third parties that sign SSL certificates are called CA certificates.
SteelHead Mobile v2.0 or later supports both traditional SteelHead SSL optimization and advanced high-security SSL optimization. Riverbed recommends that you use advanced high-security SSL optimization to protect your system. You must have RiOS v5.5 or later installed on your SteelHead to use advanced high-security SSL.
For more information about traditional SteelHead SSL optimization, see the SteelHead Deployment Guide - Protocols.
Traditional SSL Optimization
In traditional SteelHead SSL optimization with a SteelHead Mobile, a client-side SteelHead and the SteelHead Mobile can optimize traffic from any client. The traditional SSL security mode enables clients to optimize SSL traffic to all SteelHeads before RiOS v5.5. RiOS v5.5 or later can run in mixed deployments where one SteelHead is running RiOS v5.5 and another SteelHead in the network is running an earlier RiOS version.
In traditional SSL optimization, the client-side SteelHead runs on the client machine. An attacker can redirect network traffic to their SteelHead Mobile-enabled system and obtain the client session key sent from the server-side SteelHead, thereby decrypting the client traffic.
To prevent such man-in-the-middle attacks, and to ensure that SteelHead Mobile can decrypt traffic originating on only one machine, SteelCentral Controller for SteelHead Mobile v2.0 or later provides advanced high-security SSL optimization.
Advanced High-Security SSL Optimization
This section provides an overview of advanced high-security SSL optimization. Riverbed recommends that you use advanced high-security SSL optimization to protect your system.
Advanced SSL optimization:
enables SteelHead Mobile to optimize traffic from applications on the local system but not from any other system.requires RiOS v5.5 or later. If you are running a version earlier than RiOS v5.5, SteelHead Mobile supports the traditional SteelHead SSL optimization.has specific browser requirements. For the most current requirements, see the release notes.Figure 24‑7. Advanced High-Security SSL Optimization Using a SteelHead Mobile
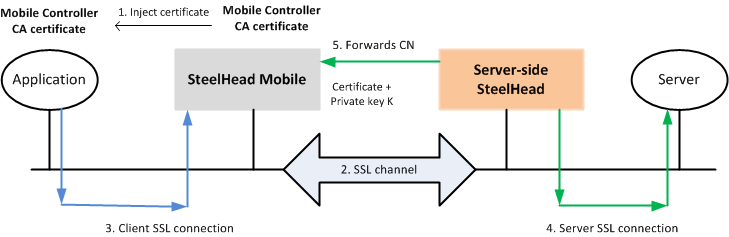
Figure 24‑7 shows the steps in the advanced high-security SSL optimization using SteelHead Mobile. The steps are as follows:
SteelHead Mobile inserts a CA certificate into the trusted CA list using Internet Explorer or Firefox. The CA certificate is local to SteelHead Mobile.
When connections are initiated for SSL optimization, either on demand or proactively, the SSL inner channel is initiated.
SteelHead Mobile intercepts the client SSL connection from the client and terminates it.
The server-side SteelHead connects to the server and extracts the common name (CN) from the server certificate. CN is the DNS name or IP address.
The server-side SteelHead forwards the CN to the SteelHead Mobile.
SteelHead Mobile takes the CN and uses the CA certificate it injected to generate a signed server certificate that it passes to the application. The application can trust this certificate because it is signed by the CA that exists in its trusted certificates list.
Configuring SteelCentral Controller for SteelHead Mobile and SSL
This section provides an overview of the basic steps required to configure SSL using SteelCentral Controller for SteelHead Mobile v4.0 or later and the SteelHead v6.0 or later.
Obtain valid Enhanced Cryptography License Keys. This is required for every SteelHead that peers with SteelHead Mobile and Mobile Controller.
Configure the server-side SteelHead for SSL optimization with the SSL servers.
Configure a trust relationship between the Mobile Controller and the server-side SteelHead.
Export the SSL certificate from the Mobile Controller.Configure a proxy certificate and private key for the SSL back-end server on the server-side SteelHead. This step enables the server-side SteelHead to act as a proxy for the back-end server, which is necessary to intercept the SSL connection and to optimize it. Import the Mobile Controller CA certificate into the server-side SteelHead.Export the server-side SteelHead peering certificate. Add the server-side SteelHead peer to the Mobile Controller. These mutual trust relationships establish secure inner channels between the Mobile Controller and the server-side SteelHead.
For information about the secure inner channel, see the SteelHead Deployment Guide - Protocols.
Create or edit the policy on the Mobile Controller so that it allows the SteelHead Mobile to intercept SSL connections.
Run a test to verify your configuration.
For information about configuring SteelCentral Controller for SteelHead Mobile and SSL, see the SteelCentral Controller for SteelHead Mobile User’s Guide.
Supported TLS Versions with SteelHead Mobile
By default, after you have completed the steps in
Configuring SteelCentral Controller for SteelHead Mobile and SSL, the SteelHead Mobile client supports SSL connections that use TLS v1.0.
SteelHead Mobile v4.7 supports TLS v1.1 or v1.2. You must enable this capability using the following CLI command on the Mobile Controller:
(config) # policy id <ID-number> ssl backend client-tls-1.2
Even though TLS v1.1 is not mentioned in the syntax of this command, using this command automatically enables support for both TLS v1.1 and v1.2.
You must make sure that the server-side SteelHead is configured to support TLS v1.2 by using the following commands on the SteelHead CLI:
(config) # protocol ssl backend server-tls-1.2
(config) # protocol ssl backend client-tls-1.2
For information about configuring SteelHeads and SSL, see the SteelHead Deployment Guide - Protocols, the SteelHead Management Console User’s Guide, and the Riverbed Command-Line Interface Reference Manual.
Multiple Mobile Controllers and SSL
An SSL configuration requires there be a trust relationship between the SteelHead Mobile and Mobile Controller. Without this trust relationship, the Mobile Controller cannot connect to and provide the SteelHead Mobile with configuration details.
Mobile Controllers in a redundant deployment or a high-availability cluster must have identical signing CA certificates. Having identical signing CA certificates is a prerequisite for a Mobile Controller to join a cluster with other Mobile Controllers. Mobile Controllers generate their own certificates. If the Mobile Controllers do not have the identical signing CA certificates, the SteelHead Mobile clients receive an untrusted certificate message.
For more information about configuring trust relationships for Mobile Controllers and SSL, see the SteelCentral Controller for SteelHead Mobile User’s Guide.


