Configuring a RADIUS Server
This section describes how to configure a RADIUS server for the SteelHead. This section includes the following topics:
Configuring a RADIUS Server with FreeRADIUSConfiguring RADIUS Authentication in the SteelHeadConfiguring RADIUS CHAP AuthenticationConfiguring a RADIUS Server with FreeRADIUS
On a per-user basis, you can specify a different local account mapping by using a vendor specific attribute. This section describes how to configure the FreeRADIUS server to return an attribute (which specifies the local user account as an ASCII string). The file paths are the default values. If the RADIUS server installation has been customized, the paths might differ.
Dictionary files are stored in the directory /usr/local/share/freeradius. You can define RADIUS attributes in this directory. Assuming the vendor does not have an established dictionary file in the FreeRADIUS distribution, begin the process by creating a file called dictionary.<vendor> in this directory.
The contents of the dictionary.<vendor> file define a vendor identifier (which should be the Structure of Management Information [SMI] Network Management Private Enterprise Code of the Vendor) and any vendor-specific attributes.
In the following example, the Vendor Enterprise Number for Riverbed is 17163 and the Enterprise Local User Name Attribute is 1. These numbers specify that a given user is an admin or monitor user in the RADIUS server (instead of using the SteelHead default for users not named admin and monitor).
These instructions assume you are running FreeRADIUS v.1.0, which is available from
http://www.freeradius.org. You can also find more details in the
SteelHead Management Console User’s Guide.
To install FreeRADIUS on a Linux computer
At your system prompt, enter the following commands:
tar xvzf freeradius-$VERSION.tar.gz
cd freeradius-$VERSION
./configure
make
make install #as root
To add acceptance requests on the RADIUS server
In a text editor, open the /usr/local/etc/raddb/clients.conf file.
To create the key for the RADIUS server, add the following text to the clients.conf file:
client 10.0.0.0/16 {
secret = testradius
shortname = main-network
nastype = other
}
The secret you specify here must also be specified in the SteelHead when you set up RADIUS server support.
In a text editor, create a /usr/local/share/freeradius/dictionary.rbt file for Riverbed.
Add the following text to the dictionary.rbt file.
VENDOR RBT 17163
ATTRIBUTE Local-User 1 string RBT
Add the following line to the /usr/local/share/freeradius/dictionary:
$INCLUDE dictionary.rbt
Add users to the RADIUS server by editing the /usr/local/etc/raddb/users file, for example:
“admin” Auth-Type := Local, User-Password == "radadmin"
Reply-Message = "Hello, %u"
"monitor" Auth-Type := Local, User-Password == "radmonitor"
Reply-Message = "Hello, %u"
"raduser" Auth-Type := Local, User-Password == "radpass"
Local-User = "monitor", Reply-Message = "Hello, %u"
Start the server using /usr/local/sbin/radiusd. Use the -X option if you want to debug the server.
The raduser is the monitor user as specified by Local, User-Password.
Configuring RADIUS Authentication in the SteelHead
This section describes the basic steps for configuring RADIUS authentication in the SteelHead. For details, see the SteelHead Installation and Configuration Guide and the SteelHead Management Console User’s Guide.
You prioritize RADIUS authentication methods for the system and set the authorization policy and default user.
Make sure to put the authentication methods in the order in which you want authentication to occur. If authorization fails on the first method, the next method is attempted, and the order is continued until all the methods have been attempted.
Perform the following basic steps to configure RADIUS support.
To configure RADIUS support
Add the IP address of the RADIUS server and specify the key used when you added the device to the ACS server:
(config)# radius-server host 192.168.1.200 key rvbd
Enable AAA.
Define the authentication method.
The following configuration attempts to use RADIUS and then local:
(config)# aaa authentication login default radius local
Configuring RADIUS CHAP Authentication
In RiOS v8.0 or later you can configure RADIUS CHAP authentication through the CLI or, in RiOS v8.5 or later, the SteelHead Management Console. Choose which method to use based on the appropriate risk mitigation strategy provided by either option. For example, CHAP transmits the password in a more secure manner, but various RADIUS servers can store the password in an unencrypted format.
radius-server host 192.168.198.136 auth-type chap timeout 3 retransmit 1 key testradius
To configure CHAP authentication in the SteelHead Management Console, configure the RADIUS server (Administration > Security: RADIUS).
Figure 22‑1. RADIUS CHAP Authentication
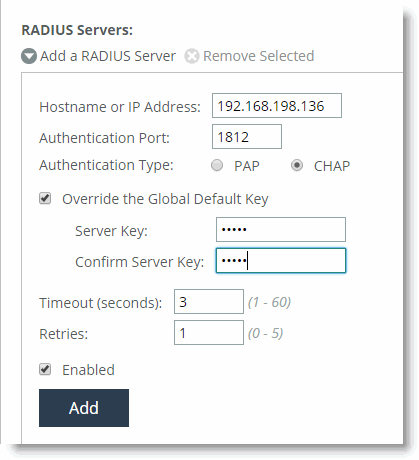
After you add the server, include RADIUS in the order of authentication methods. A best practice to ensure that you can still perform authentication in the absence of the RADIUS server is to:
Use the RADIUS server first for authentication, but Fall back to the SteelHead username and password database if the RADIUS server is unavailableFigure 22‑2. RADIUS Authentication