802.1Q Trunk Deployments
This section describes the use of virtual LANs (VLANs) and 802.1Q, which allows multiple logical networks to span a single physical link. IEEE 802.1Q is a networking standard that allows multiple bridged networks to transparently share the same physical network. IEEE 802.1Q is also referred to as VLAN Tagging, and dot1q.
This section includes the following topics:
Overview of VLAN TrunkConfiguring a SteelHead on an 802.1Q Trunk LinkCapturing Network Traces Using tcpdump The SteelHead does not support overlapping IP address spaces, even if the overlapping IPs are kept separate through VLAN tags.
For information about alternative configurations, see
VPN Routing and Forwarding.
Overview of VLAN Trunk
A SteelHead can be deployed physically in-path on an 802.1Q trunk link, and can optimize connections where packets have been tagged with an 802.1Q header. As in other physical in-path deployments, the SteelHeads in-path interface must be configured with an IP address and a default gateway. If the SteelHeads in-path IP address is in a subnet whose traffic is normally tagged when present on the in-path link, the SteelHead's in-path interface must be configured with the VLAN for that subnet. This allows the SteelHead to appropriately tag packets transmitted from the in-path interface that use the in-path IP address as the source address. The SteelHead can optimize traffic on the VLANs different from the VLAN containing the in-path IP address.
SteelHeads can be deployed across multiple 802.1Q trunk links. Each in-path interface requires:
an IP address. a default gateway.a VLAN ID (if required for the in-path IP address subnet).SteelHeads configured as connection-forwarding neighbors can be deployed on 802.1Q trunk links.
SteelHeads maintain the VLAN ID when transmitting packets for the LAN side of optimized connections. If correct addressing or port transparency is used, the SteelHead uses the configured in-path VLAN ID when transmitting packets towards the WAN. When using the full address transparency WAN visibility mode (for details, see
Full Address Transparency), SteelHeads maintain the VLAN ID (along with IP address and TCP ports) when transmitting packets on the WAN side of optimized connections. The SteelHead can maintain the VLAN IDs even if there is a difference between the packets going to the WAN and those returning from the WAN. You do not have to configure the VLAN ID on the in-path interface to match any of those seen for optimized connections.
For example, assume that SteelHead is configured for full address transparency. The SYN packet for a TCP connection traveling toward the WAN has a VLAN ID of 100, and the SYN/ACK packet returning from the WAN has a VLAN of 200. If a SteelHead optimizes this connection, then the SteelHead transmits packets toward the LAN using VLAN ID 200. The SteelHead monitors the MAC addresses associated with each VLAN.
Figure 9‑19. Example of Basic VLAN Trunk Deployment
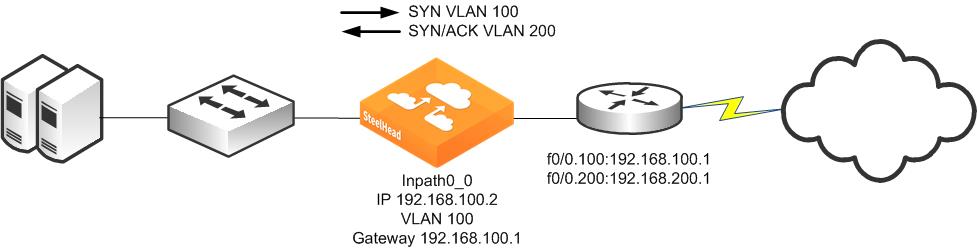
Maintaining the VLAN IDs in this manner requires using the vlan-conn-based and mac-match-vlan CLI commands, which are enabled by default in RiOS v6.0 or later, and the other commands listed in the following configuration example.
In-path rules can use VLAN tags as matching parameters. This allows you to control optimization based on VLAN tags, along with other information such as IP addresses, subnets, or TCP ports.
Configuring a SteelHead on an 802.1Q Trunk Link
Figure 9‑20 shows a SteelHead deployed physically in-path on an 802.1Q trunk link. Two VLANS are present on the in-path link: VLAN 10, which contains subnet 192.168.10.0/24, and VLAN 20, which contains subnet 192.168.20.0/24. The SteelHead is given an in-path IP address in the 192.168.10.0/24 subnet. The SteelHead is configured to use VLAN 10 for its in-path interface, and to use the routers subinterface IP address as its default gateway. Even though the SteelHead has an in-path IP address in subnet 192.168.10.0/24 and VLAN 10, it can optimize traffic in VLAN 20.
Figure 9‑20. SteelHead Deployed Physically In-Path on an 802.1Q Trunk Link
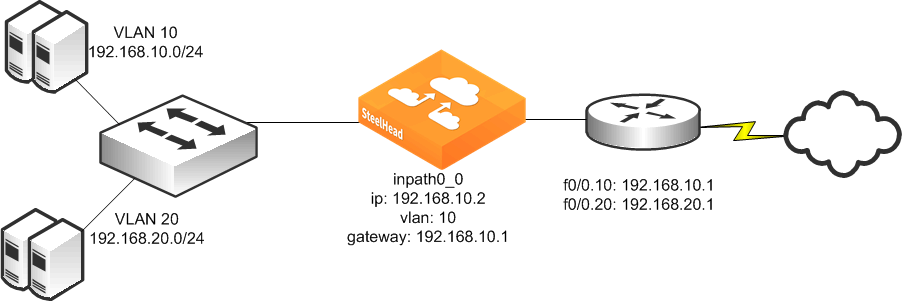
To deploy a SteelHead physically in-path on an 802.1Q trunk link
On the SteelHead, connect to the CLI and enter the following commands:
in-path enable
interface inpath0_0 ip address 192.168.10.2 /24
ip in-path-gateway inpath0_0 192.168.10.1
in-path interface inpath0_0 vlan 10
in-path simplified routing all
in-path peering auto
in-path probe-ftp-data
in-path probe-mapi-data
in-path simplified mac-def-gw-only
in-path mac-match-vlan
in-path vlan-conn-based
no in-path peer-probe-cach
no in-path probe-caching enable
in-path mac-except-locl
Capturing Network Traces Using tcpdump
Use caution when using network traces on trunk links. If you configure a TCP dump filter that restricts the captured packets to a specified set (for example, based on IP addresses or ports), by default tcpdump does not capture packets with an 802.1Q tag.
To capture packets with an 802.1Q tag, you must prefix the filter string with the keyword vlan. Enter the following CLI command:
tcpdump -i wanX_Y vlan and host
For details, see the Riverbed Command-Line Interface Reference Manual.



