About secure peering settings
Settings for secure peers are under Optimization > SSL: Secure Peering (SSL).
If you are securing encrypted MAPI, SMB-signed, or Citrix traffic, further configuration is required on the Management Console pages for those protocols.
The time setting among peers must be identical. We recommend using NTP time synchronization or manually synchronizing their clocks.
Secure peering settings
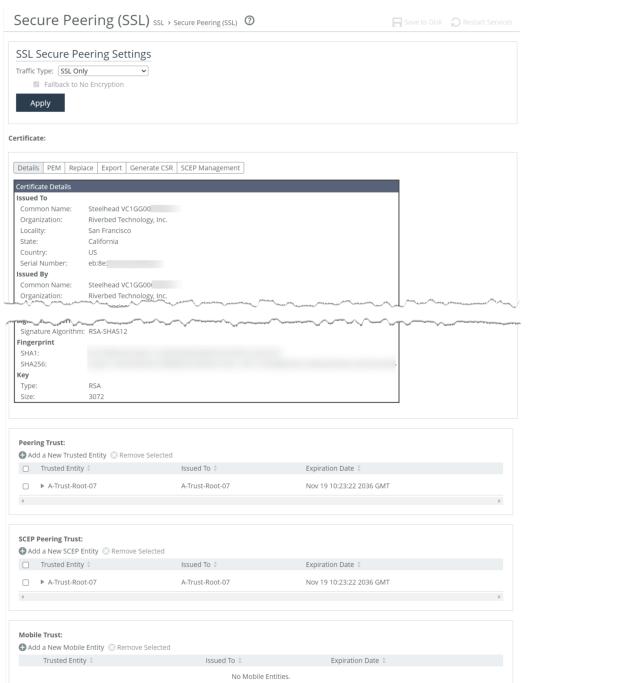
Select a traffic type. Client-side and server-side appliances authenticate each other and encrypt traffic of the selected type. Changing the traffic type requires a service restart.
SSL Only
Encrypts and optimizes all SSL traffic, such as HTTPS on port 443. This is the default value.
SSL and Secure Protocols
Encrypts and optimizes all traffic traveling over Citrix, SSL, SMB-signed, and encrypted MAPI.
All
Encrypts and optimizes all traffic, except pass-through traffic.
Selecting All can cause up to a 10-percent performance decline in higher-capacity SteelHead. Take this performance metric into account when sizing a complete, secure peering environment.
Fallback to No Encryption
Specifies that the appliance optimizes but doesn’t encrypt connections when it’s unable to negotiate a secure, encrypted inner channel connection with the peer. Disable to pass through connections that don’t have a secure encrypted inner-channel connection with the peer. This option is enabled by default. This setting requires a service restart.
Use caution when disabling this setting, as doing so specifies that you strictly don’t want traffic optimized between nonsecure appliances. Consequently, connections might be dropped. For example, when this setting is disabled and All is selected as the traffic type, the appliance will not optimize the connection when a secure channel is unavailable and might drop it.
We strongly recommend enabling this setting on client-side and server-side appliances, especially in mixed version deployments. This option applies only to non-SSL traffic and is unavailable when you select SSL Only.
About peer trust tables
Appliances maintain lists of peers in their peering trust tables. You can manually add trusted peers and accept or decline the trust relationship with any listed peer requesting a secure inner channel.
Secure peering trust tables
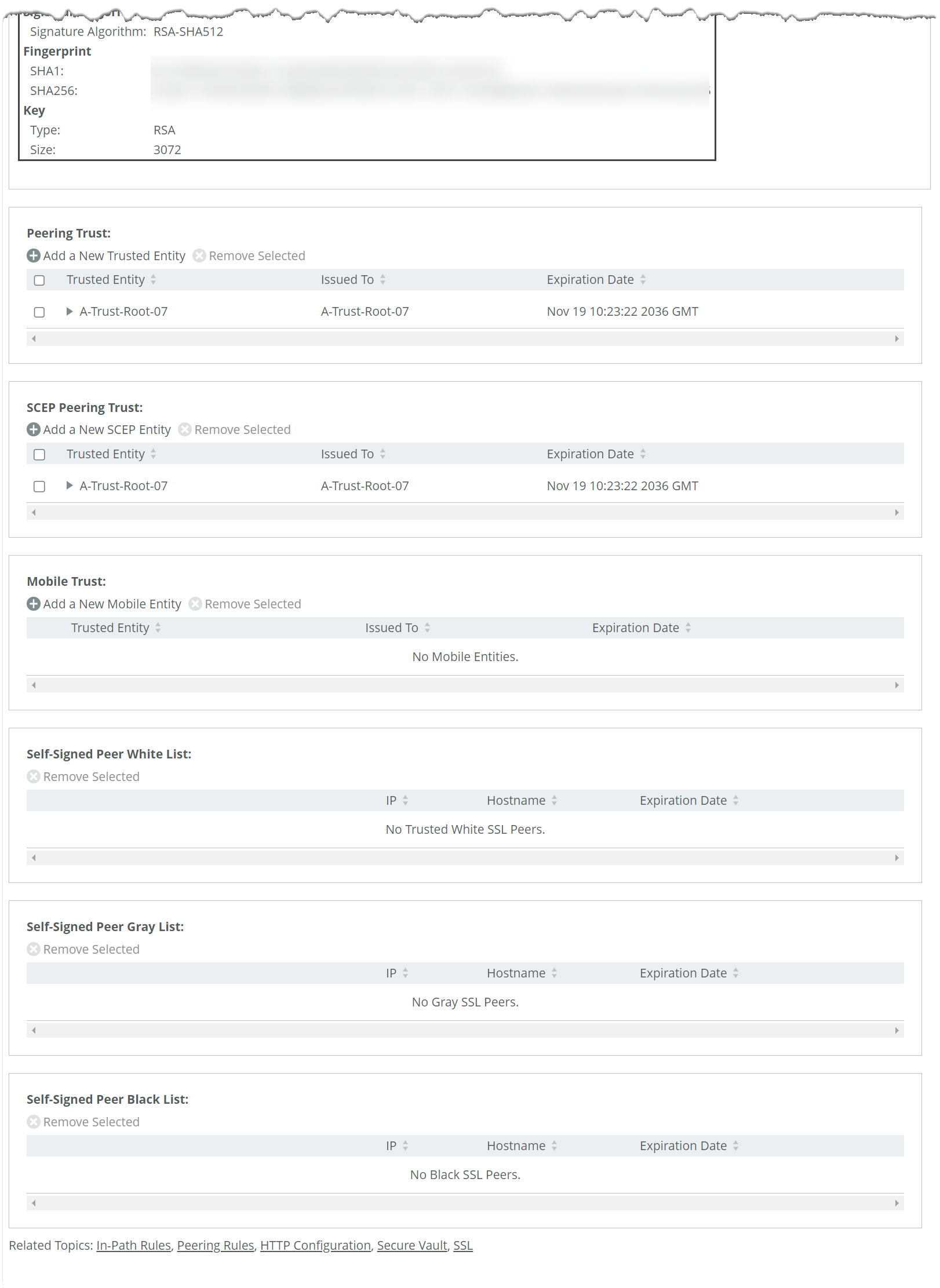
Peering trust
Lists all trusted peers. You can view any listed peer’s certificate details and certificate (PEM format).
SCEP peering trust
Lists the subset of peers that can use simple certificate enrollment protocol (SCEP) certificates:
• URL specifies the URL of the SCEP responder. Example: http://<Iip-address>/certsrv/mscep/mscep.dll
• Maximum Number of Polls specifies the maximum number of polls before the SteelHead cancels the enrollment. The peering certificate is not modified. The default value is 5. A poll is a request to the server for an enrolled certificate by the SteelHead. The SteelHead polls only if the server responds with pending. If the server responds with fail then the SteelHead doesn’t poll.
• Poll Period specifies the poll frequency in minutes. The default value is 5.
• Change Challenge Passphrase specifies the challenge password phrase.
• Enable Auto Enrollment enables automatic reenrollment of a certificate to be signed by a CA using SCEP.
• Expiration Threshold specifies the amount of time (in days) to schedule reenrollment before the certificate expires. The range is from 1 to 60 days. The default value is 30 days.
• Update SCEP Settings updates the SCEP settings.
Mobile trust
Manages trusted Client Accelerator Controller appliances, which are authorized to sign certificates for Client Accelerator endpoint software. Peer appliances are sorted into three color-coded lists based on trust status:
• White list—Trusted peers
• Black list—Untrusted peers
• Gray list—Unknown peers (typically newly discovered ones attempting to form secure connections)
Each entry in these lists may include details such as the appliance's public key, certificate, certificate expiration date, IP address, and hostname. You can change an appliance’s status manually by:
• moving a peer from the gray or black list to white means you trust it.
• moving a peer from the white or gray list to black means you do not trust it.
Before trusting a peer from the gray list, always verify the certificate fingerprint to protect against potential man-in-the-middle attacks.
If the same certificate is listed in both the trusted entity list and a self-signed peer list, deleting it from one will automatically remove it from the other.



