SteelConnect Topologies
This topic describes the supported SteelConnect topologies. It includes these sections:
Supported topologies
This section describes many, but not all, of the qualified topology designs for the branches and the data center. Because networks are not identical, the supported topologies described in this section provide a starting point for your network design.
For all topologies, configuring high availability improves the reliability of a network by replacing a single SteelConnect gateway with two gateways in the branch or three gateways in the data center. A backup gateway can maintain network traffic if another gateway fails. For details, see
How does branch high availability work? and
How does data center high availability work?.
For more topologies, including SteelHead with SteelConnect, see the SD-WAN Deployment Guide.
Branch topologies
Single router using NAT to the internet
Router using NAT

The following topologies support a single router using network address translation (NAT).
DHCP or static IP address for the uplink
A location connects to the internet using a single router or a DSL modem. You can deploy a SteelConnect gateway on the LAN side of the router with its default configuration and it will perform NAT as well. This topology works fine for most deployments. If you have port forwarding configured on the router, you’d have to configure the port forwarding on the gateway as well.
Turn off outbound NAT
Outbound NAT forwards the client’s connections with their original source IP to the router. For deployments where an upstream gateway, router, or firewall will perform NAT, you can turn off outbound NAT. When outbound NAT is off, the existing router is no longer directly connected to the IP subnets used in the LAN, but sends traffic to the gateway. The gateway performs NAT and forwards traffic to the zones.
You can’t turn off outbound NAT per gateway. You can turn off outbound NAT per zone, sites, and uplinks. For details, see
Turning off outbound NAT.
Skipping outbound NAT

Reconfigure the router to function as a DSL modem or bridge
In this deployment, you need to configure the Point-to-Point Protocol over Ethernet (PPPoE) credentials on the gateway so it can authenticate with the internet service provider. This typically means that the customer enters a user name and password provided by the ISP to use that last-mile link from the customer premises to the ISP. The gateway then connects to the internet using NAT and routes traffic between the configured zones and the internet.
This topology is not supported on SteelHead SD 570-SD, 770-SD, and 3070-SD appliances.
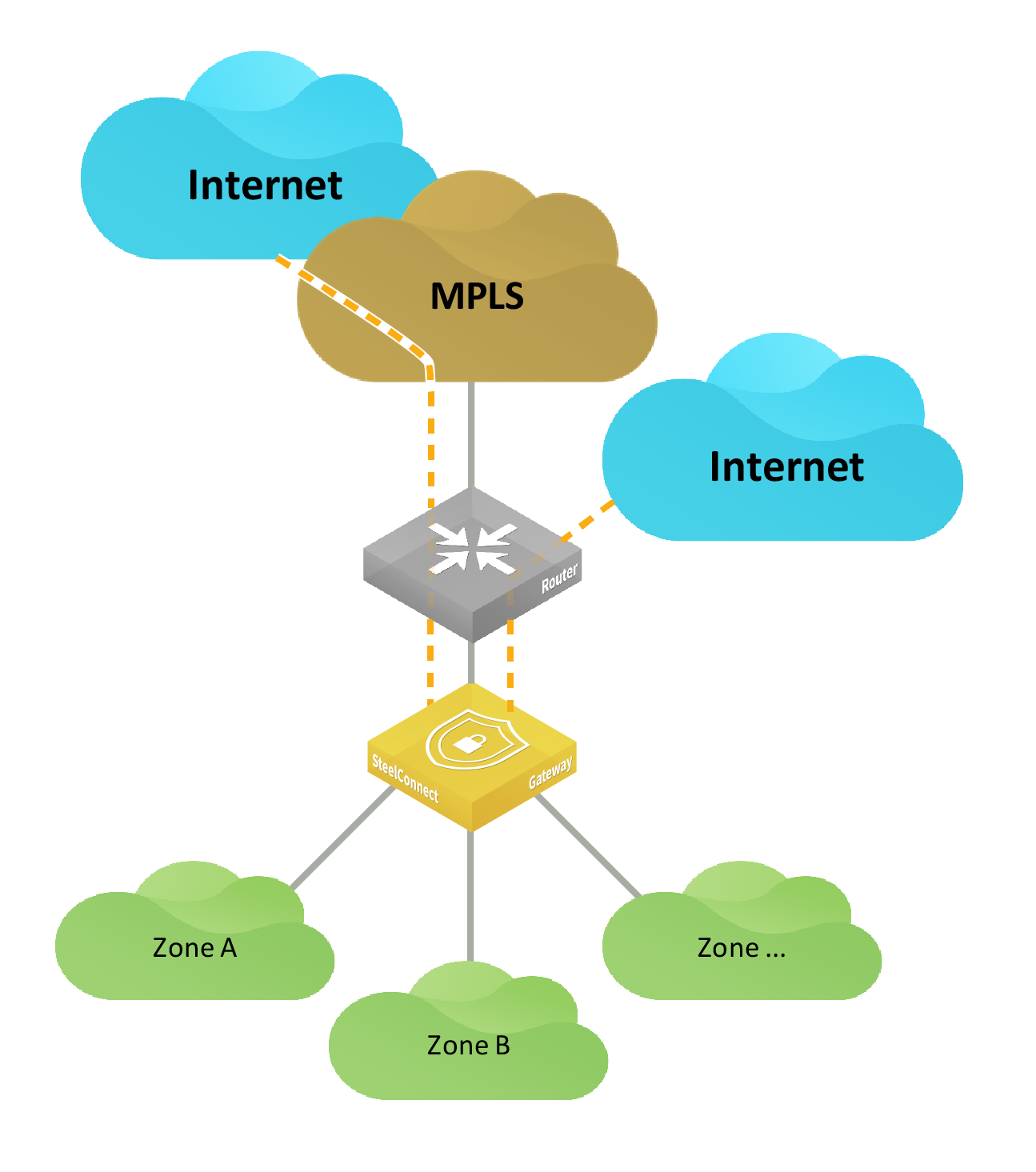
Single router to an MPLS network
This topology is similar to the previous description of a single router using NAT, except that the router connects to an MPLS network.
One router connecting to MPLS

The gateway must connect to the internet either through the MPLS network or through a local internet breakout to connect to the SteelConnect cloud service.
You must map the static IP address for the gateway’s uplink to the IP address of the LAN interface on the router. To ensure that the zones on the LAN side of the gateway can be reached, you must also configure static routes for the zone’s subnets on the router.
To set up a VPN over the MPLS network, configure the uplink of the gateway to propagate the internal IP address that the remote sites use as the endpoint target for the AutoVPN tunnel. By default, SCM uses the external IP address facing the internet. For details, see
To configure an uplink to use an internal interface.
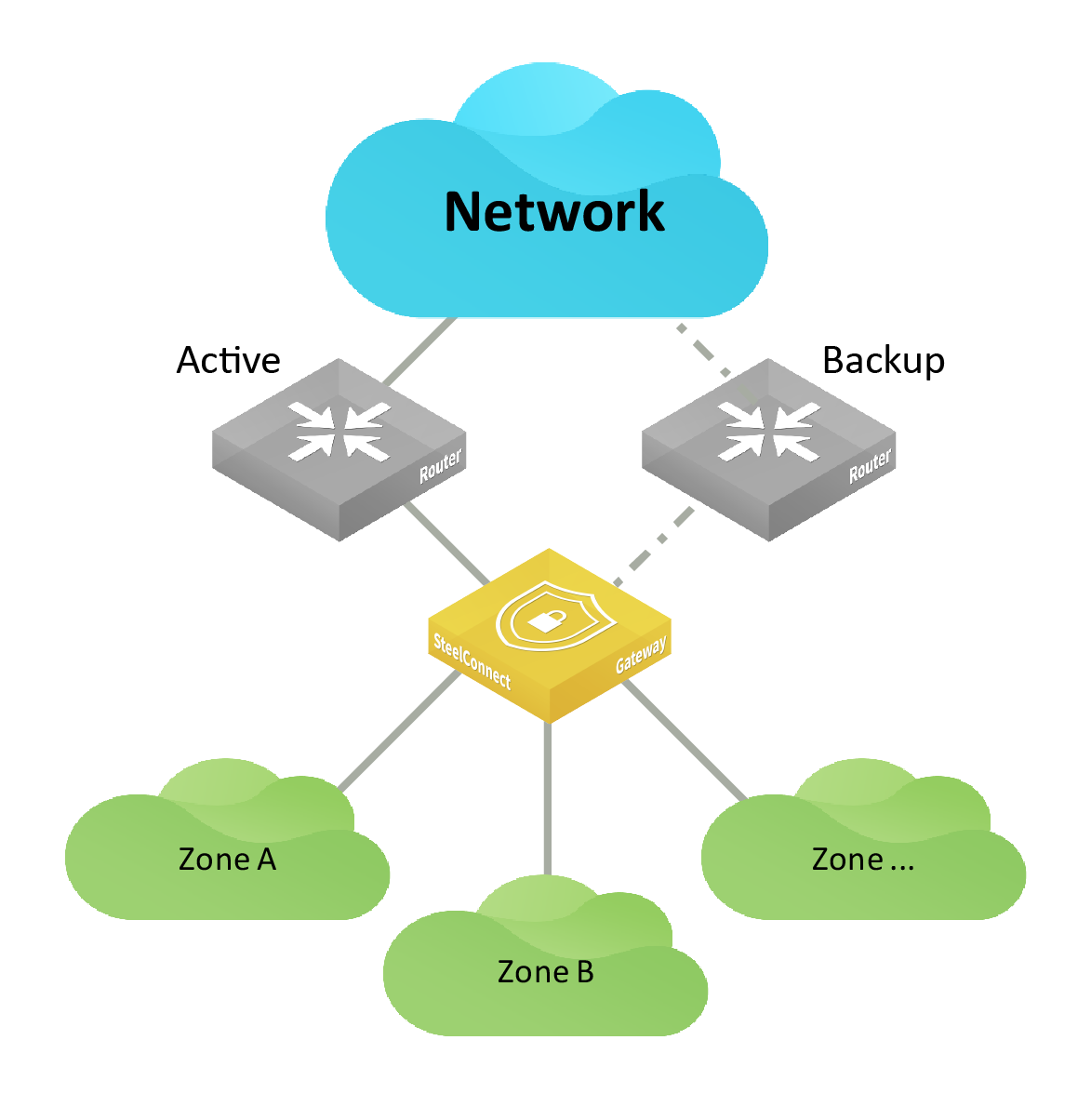
Two routers active-backup
The following topologies support two routers.
Single network: internet/MPLS
This topology deploys two routers connecting to the same network where one router is actively forwarding traffic and the second router is acting as backup for the first. In this topology, it doesn’t make a difference if the network were trying to connect to the internet or a private network such as MPLS. For a description of the challenges connecting to the internet versus connecting to a private network, see
Single router to an MPLS network.
To connect a SteelConnect gateway to two routers, you need to create two uplinks configured with different IP addresses. Then you need to configure one of the uplinks as backup only.
The SD-WAN controller establishes tunnels on both the active and backup uplinks.
For details on backup uplinks, see
Creating uplinks.
Two routers active-backup
Two routers active-active
This topology deploys two routers connecting to the same network where both routers are actively forwarding traffic. In this topology, you connect a SteelConnect gateway to the routers by creating two uplinks configured with different IP addresses. There is nothing additional to configure.
The SteelConnect gateway automatically load balances the sessions over the two uplinks based on source and destination IP addresses.
Two routers active-active

Dual internet through two ISPs
This topology has dual internet connectivity via two different Internet Service Providers (ISPs). The traffic outbound is automatically load balanced by the gateway when both uplinks connect to the same WAN (internet). The system uses the source IP to load balance internet-bound traffic, and the source and destination IP to load balance RouteVPN traffic.
You can also configure this topology as active-backup.
RouteVPN is the name for the overlay on an Internet WAN uplink (and only for that type of WAN). Overlay tunnels are called AutoVPN on SteelConnect.
Two routers connecting to the internet with different ISPs

Internet and MPLS
This topology is very similar to the previous deployment except instead of two internet connections there is one connection to the internet and one connection to a private network, typically MPLS. As in the previous topologies, you connect a SteelConnect gateway to the routers by creating two uplinks configured with different IP addresses. Next, choose to do either automatic load balancing or path selection. For path selection, the SteelConnect gateway must have a Layer 2 connection to the routers to perform MAC address rewriting.
For this topology, on the gateway uplink to the MPLS router, you also need to configure a static route to the MPLS network. For details, see
Single router to an MPLS network. You must also configure static routes to zones on the MPLS router.
One connection to the internet, one connection to MPLS

Dual MPLS
This topology has two connections to private networks, most likely MPLS. In this topology the SteelConnect gateway needs a connection to the internet to reach the cloud controller. The internet connection can’t use a proxy.
You create two uplinks with different IP addresses. Next, choose to do either automatic load balancing or path selection. For path selection, the SteelConnect gateway must have a Layer 2 connection to the routers to perform MAC address rewriting.
For this topology, on the gateway uplink to the MPLS router, you need to configure a static route to the MPLS network. For details, see
Single router to an MPLS network. You must also configure static routes to zones on the MPLS router.
Two connections to private networks

Data center topologies
The SDI-2030 and SDI-5030 gateways are the data center side of SteelConnect.
The SDI-2030 gateway can be deployed in-line mode as a 1-Gbps data center gateway and can serve large throughput requirements. The SDI-2030 gateway does not support WAN optimization capabilities. For details on the SDI-2030 gateway, see the SteelHead SD User Guide.
In contrast to the gateways that handle the in-path traffic, the SDI-5030 data center gateway sits out of path deep inside the data center’s network.
Data center, Interceptor, and branch gateway deployment

Figure: Data center, Interceptor, and branch gateway deployment shows four SteelHead Interceptor 9600s placed between the LAN switching and WAN aggregation routing layers. On the LAN side of the SteelHead Interceptors, three SteelHead CXs provide WAN optimization. On the WAN side of the SteelHead Interceptors, three SDI-5030 gateways are connected physically (or by switching) to the WAN aggregation routers.
All VPN tunnels exist between the branch gateways and the SDI-5030 gateways behind the aggregation layer. The SteelHead Interceptors always see nonencrypted traffic, enabling them to redirect the flows to the SteelHead CXs for WAN optimization.
Topology options
Local internet breakout or backhaul
When sending traffic to the internet, a SteelConnect access point or gateway uses direct internet uplinks by default for the local breakout. You can configure a backhaul site, or a local internet breakout for each network, similar to a default route. SteelConnect sends any traffic with an unknown destination network; that is, the destination is not configured in a site or a zone, to the specified site, or to the local internet breakout.
You can set the internet breakout preference to RouteVPN, which is essentially a WAN over the internet resulting from AutoVPN, or to a WAN defined for an organization. You can override the default on the network, site, or zone level. You can define multiple internet breakouts within an organization. For more information, see
Configuring a direct alternate hub.
Internet traffic breakout or backhaul
Do not select a site configured in leaf mode (either single leaf or dual hub) as a remote RouteVPN internet breakout site. Doing so will create an invalid design. Suppose that you have three sites: site A, site B, and site C. Site A is configured in leaf mode to the hub site B. Although it is possible to configure an internet breakout setting for site C by selecting site A as the remote RouteVPN breakout site, in this configuration the internet bound traffic will not break out of site A. Rather, the traffic from site C will reach site B on the overlay and then break out from site B using site B's internet breakout configuration. SteelConnect does not support multihop internet breakout as described in this example (site C to site B to site A).
Connect cloud services
The SteelConnect gateway virtual machine (VM) is available for various virtualization platforms in these image types:
• VMware
• Virtualbox
• KVM
• Hyper-V
• XENCenter
• Amazon EC2
When you deploy a gateway in your cloud or multiple clouds, the RouteVPN feature lets you connect your data center to the cloud, or even multiple clouds with each other.











