SSL simplification
RiOS 9.12 introduces a new feature that provides a simplified, modular, and automated platform for managing SSL certificates.
This feature includes these components:
• Transport Layer Security (TLS) blade–This component handles TLS/SSL optimization and manages the communication between endpoint applications and SSL agents.
• SSL agent–Similar to a hardware security module (HSM), this component provides access to certificates. The SSL agent autogenerates its own certificates or connects with the server-side SteelHead certificate repository. This component includes a transport layer that automatically peers and communicates with other SSL agents.
When fully functional, the SSL agents create and manage certificates for their respective client to use for traffic optimization.
Currently, the feature can be deployed in these ways:
• Client Accelerator is deployed on end-user systems as an SSL agent. The Client Accelerator communicates with a client-side SteelHead which in turn communicates with the server-side SteelHead. Optimization is handled by the client-side and server-side SteelHead. Certificate management is handled by the SSL Client Accelerator.
• Client Accelerator is deployed on end user systems as an optimization and SSL agent. The Client Accelerator communicates directly with the server-side SteelHead. Optimization is handled by the Client Accelerator and the server-side SteelHead, and certificate management is handled by the Client Accelerator.
Deployment options
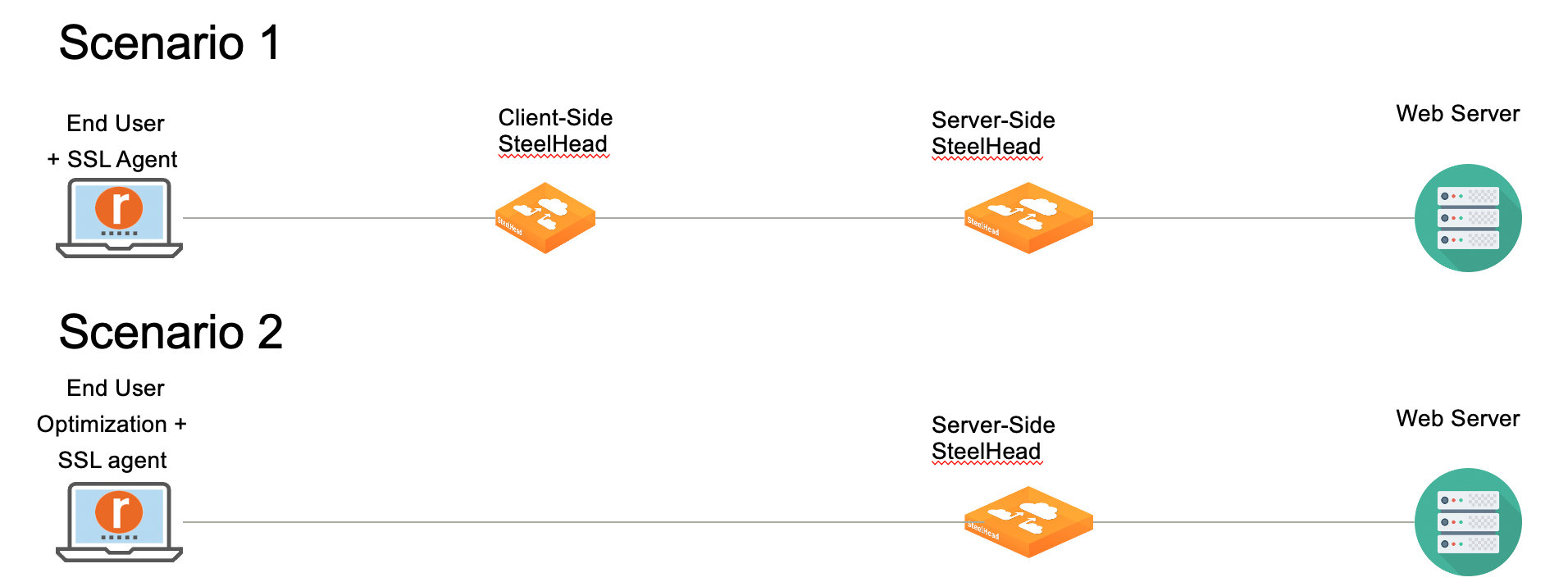
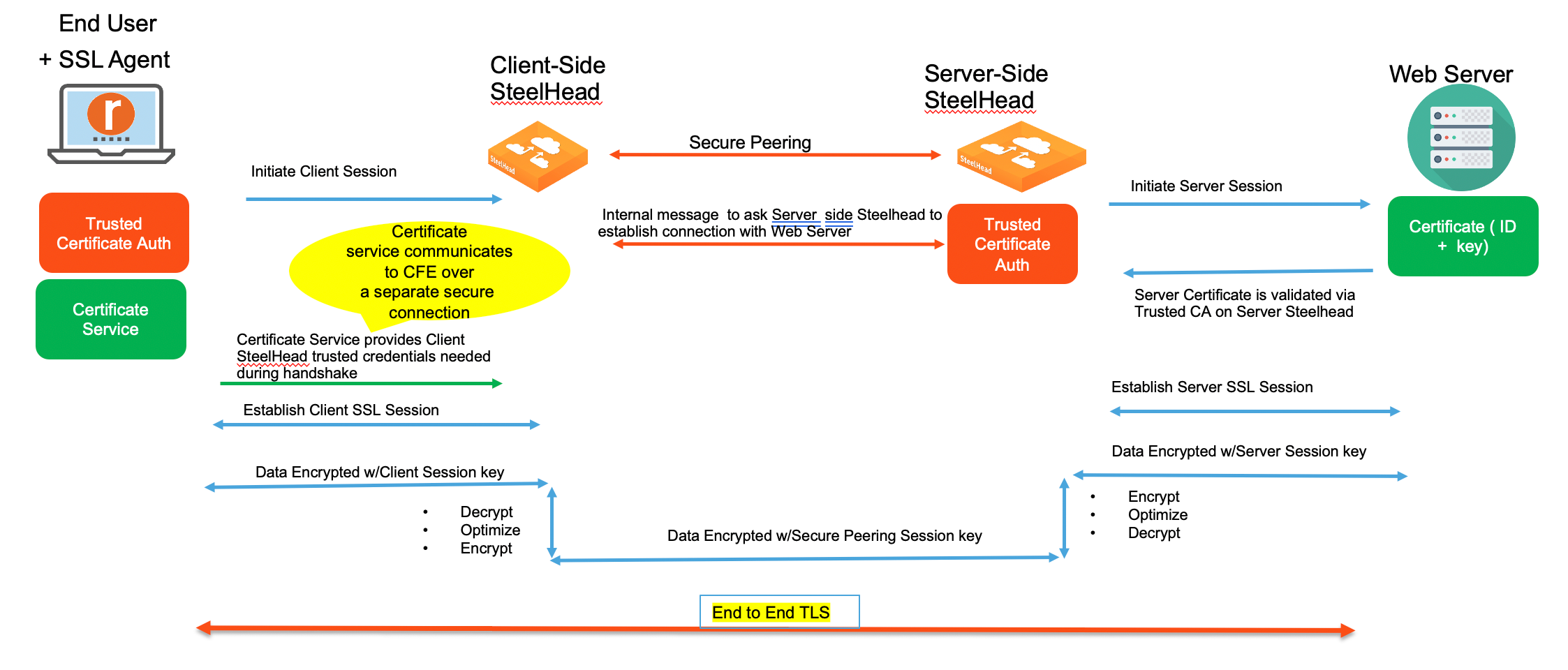
Scenario 1 illustrates Client Accelerator deployed as an SSL agent. The client endpoint device initiates a TLS/SSL connection with the client-side SteelHead, which is received through the TLS blade. The TLS blade requests a certificate from its peer-certificate services layer. This layer is aware that it is connected to a Client Accelerator that is acting as an SSL agent and fetches the appropriate certificate from the certificate services layer there, and then returns the certificate to the TLS blade. The TLS/SSL session is authenticated. Using the client session key, the system decrypts the data, optimizes it, re-encrypts it using the peering SteelHead’s secure peering session key, and then sends it to the server-side SteelHead.
Topology where the Client Accelerator is deployed in end-user devices as an SSL agent.
The feature uses one method for certificate selection: Server Name Identification (SNI). This method is an improvement over the traditional system which relies on exact matches between addresses and certificates and bypass tables when mismatches occur. Under the traditional system, mismatches would sometimes result in dropped connections. With SNI, destination domains and their certificates can be matched at the start of the connection handshake, and when there is no match, the connection is simply passed through—no dropped connections.
Requirements and compatibility
This feature requires SteelHead 9.12 or later and Client Accelerator 6.2.2 or later.
Requirements for Client Accelerator as an SSL agent
• TLS enabled on the server-side SteelHead, client-side SteelHead, and the Client Accelerator.
• Secure Peering configured between:
– the client-side SteelHead and the Client Accelerator Controller.
– the client-side SteelHead and the server-side SteelHead.
• SSL enabled on the Client Accelerator.
• Location awareness enabled on the Client Accelerator.
• In-path rules configured as auto-discovery on the Client Accelerator Controller for all SSL traffic.
Requirements for Client Accelerator as an optimization and SSL agent
• TLS enabled on the server-side SteelHead and the Client Accelerator.
• SSL enabled on the Client Accelerator.
• Secure Peering configured between the Client Accelerator Controller and the server-side SteelHead.
Configuring the feature
You must configure this feature on the Client Accelerator using the Client Accelerator Controller and on the client-side SteelHead using the SteelHead Management Console.
To configure the feature on Client Accelerator
1. Log in to the Client Accelerator Controller.
2. Choose Manage > Services: Policies and select the policy you want to modify.
3. Select the SSL tab.
4. Under TLS Optimization, select Enable TLS Optimization.
5. Click Update Policy.
6. Choose Administration > SSL Peering and add any peering trust certificates or certificate authority (CA) required by the server-side SteelHead.
– For Client Accelerator as an SSL agent, add the client-side SteelHead peering certificate.
– For Client Accelerator as an SSL and optimization agent, add the server-side SteelHead peering certificate.
7. Choose Manage > Policies, and select the policy you want to modify.
8. Select the In-Path Rules tab.
9. Select Add a New In-Path Rule.
10. Define an in-path rule for SSL optimization that is similar to an in-path rule on the SteelHead. For Client Accelerator an SSL agent, define the in-path rule as AutoDiscover only.
11. Click Update Policy.
12. Select the SSL tab:
– ensure that SSL is enabled.
– confirm that the peering trust elements are displayed in the Effective List of all the Peering Certificates. If they are not listed, update your SSL peers.
13. Select the Location Awareness tab and perform these actions:
– enable latency-based location awareness.
– increase the latency timeout to accommodate the round trip time (RTT) between the Client Accelerator and the client-side SteelHead.
– ensure Branch Warming is not enabled.
14. Click Update Policy.
15. Click Save to Disk.
To configure the feature on SteelHead
1. Log in to the Management Console.
2. Choose Optimization > SSL: Advanced Settings.
3. Scroll to the bottom of the page, under TLS Blade, select Enable TLS blade.
4. Click Apply.
5. Click Save to Disk to save your configuration.
6. Choose Administration > Maintenance: Services and click Restart.



