Figure: User Permissions Page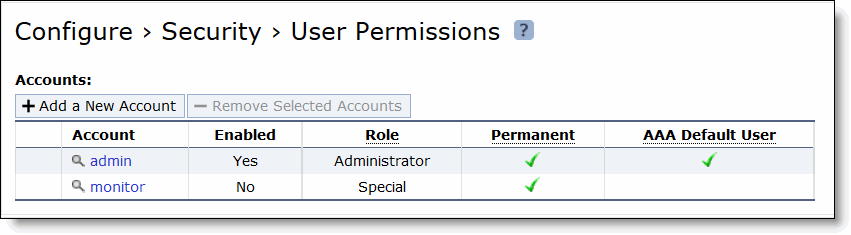


Control | Description |
admin/monitor | Click the magnifying glass icon for the user account you want to set or modify. Login failure details are displayed. |
Clear - Clears the detailed information about login failures. | |
Change Password - Enables password protection. Mobile Controller 5.0 and later includes an account control feature that allows you to select a password policy for more security. When you enable account control on the Configure > Security > Password Policy page, a user must use a password. When a user has a null password to start with, the administrator can still set the user password with account control enabled. However, once the user or administrator changes the password, it cannot be reset to null as long as account control is enabled. | |
New Password - Specify a password in the text box. | |
New Password Confirm - Retype the new administrator password. | |
Enable Account - Select the option to enable or clear to disable the administrator or monitor account. If the account is enabled, the following option is available: • Make this the AAA Default User (for RADIUS/TACACS+ logins) |
Control | Description |
Add a New Account | Click to display the controls for creating a new account. |
Account Name | Specify a name for the account. |
Password | Specify a password in the text box. |
New Password Confirm | Retype the password to confirm. |
Enable Account | Select the check box to enable the new account. If the account is enabled, the following option is available: • Make this the AAA Default User (for RADIUS/TACACS+ logins) |
Roles and Permissions | Select one of these roles: • Administrator - Specifies an administration account with full access to configuration and reports. • Role-based management (RBM) User - Select deny, read-only, or read/write access for the following settings: – General Settings - Configures the per-source IP connection limit and the maximum connection pooling size. – Network Settings - Configures host and network interface settings, including DNS cache settings and hardware assist rules. – Security Settings - Configures security settings, including RADIUS and TACACS authentication settings and the secure vault password. – Policy/Package/Assignment Settings - Configures policy, package, and assignment settings. – Diagnostic Reports Settings - Customizes system diagnostic reports, including system and user log settings. It does not include TCP dumps. – Endpoint Reports Settings - Configures endpoint client report settings. – SSL Settings - Configures SSL support and the secure inner channel. – Cluster Settings - Configures Mobile Controller cluster settings. |
Add | Adds your settings to the system. |
Remove Selected Accounts | Click to remove the selected accounts. |