Configuring general security settings
Settings to prioritize local, RADIUS, and TACACS+ authentication methods for the system and to set the authorization policy and default user for RADIUS and TACACS+ authorization systems are under Administration > Security: General Settings.
Make sure to put the authentication methods in the order in which you want authentication to occur. If authorization fails on the first method, the next method is attempted, and so on, until all of the methods are attempted.
To set TACACS+ authorization levels (admin or read-only) to allow certain members of a group to log in, add this attribute to users on the TACACS+ server:
service = rbt-exec {
local-user-name = “monitor”
}
where you replace monitor with admin for write access.
For details about setting up RADIUS and TACACS+ servers, see the SteelHead Deployment Guide.
Perform this task to set general security settings:
General Security Settings page
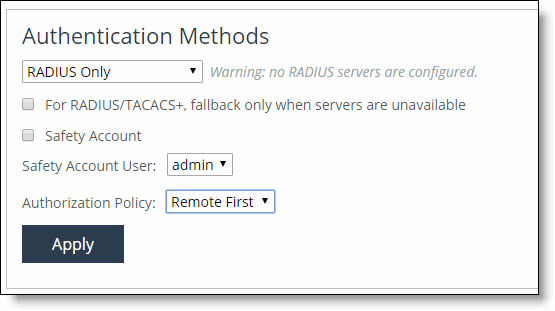
These configuration options are available under Authentication Methods:
Authentication Methods
Specifies the authentication method. Select an authentication method from the drop-down list. The methods are listed in the order in which they occur. If authorization fails on the first method, the next method is attempted, and so on, until all of the methods have been attempted.
For RADIUS/TACACS+, fallback only when servers are unavailable
Prevents local login if the RADIUS or TACACS+ server denies access, but allow local login if the RADIUS or TACACS+ server is not available.
Safety Account
Creates a safety account so that admin or sys admin users can login to the SteelHead even if remote authentication servers are unreachable. A safety account increases security and conforms to US National Institute of Standards and Technology (NIST) requirements. Only the selected safety account will be allowed to login in cases where the AAA server isn’t reachable. (Only one user can be assigned to the safety account.) Settings to create a system administrator user are under Administrator > Security: User Permissions. For details, see
Managing user permissions.Safety Account User
Selects the user from the drop-down list.
Authorization Policy
Appears only for some Authentication Methods. Optionally, select one of these policies from the drop-down list:
• Remote First checks the remote server first for an authentication policy, and only checks locally if the remote server doesn’t have one set. This is the default behavior.
• Remote Only only checks the remote server.
• Local Only only checks the local server. All remote users are mapped to the user specified. Any vendor attributes received by an authentication server are ignored.


