About log settings
Settings for local and remote logging are under Administration > System Settings: Logging.
By default, the system rotates each log file every 24 hours or if the file size reaches 1 GB uncompressed. You can change this setting to rotate every week or month, and you can rotate the files based on file size.
The automatic rotation of system logs deletes your oldest log file, labeled as Archived log #10, pushes the current log to Archived log # 1, and starts a new current-day log file.
Logging page
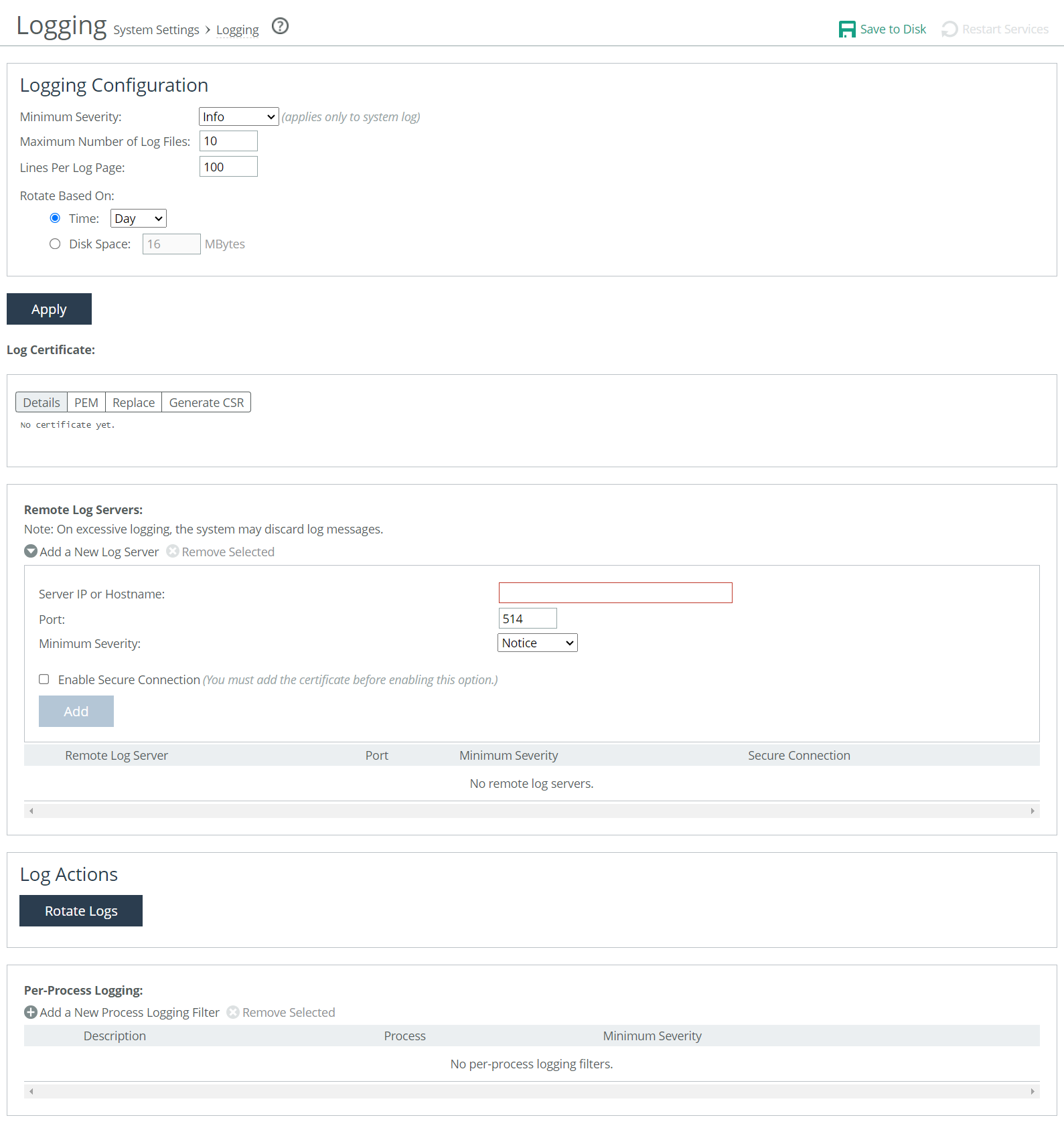
To rotate the logs manually, under Log Actions, click Rotate Logs. After the logs are rotated, this message appears:
logs successfully rotated
When you click Rotate Logs, your archived file #1 contains data for a partial day because you are writing a new log before the current 24-hour period is complete.
Under Logging Configuration, these configuration options are available:
Minimum Severity
Sets the minimum severity level for the system log messages. The log contains all messages with this severity level or higher. Select one of these levels from the drop-down list:
• Emergency indicates the system is unusable.
• Alert indicates action must be taken immediately.
• Critical indicates conditions that affect the functionality of the SteelHead.
• Error indicates conditions that probably affect the functionality of the SteelHead.
• Warning indicates conditions that could affect the functionality of the SteelHead, such as authentication failures.
• Notice indicates normal but significant conditions, such as a configuration change. This is the default setting.
• Info indicates informational messages that provide general information about system operations.
This control applies to the system log only. It doesn’t apply to the user log.
Maximum Number of Log Files
Specifies the maximum number of logs to store. The default value is 10.
Lines Per Log Page
Specifies the number of lines per log page. The default value is 100.
Rotate Based On
Specifies the rotation option:
• Time specifies Day, Week, or Month from the drop-down list. The default setting is Day.
• Disk Space specifies how much disk space, in megabytes, the log uses before it rotates. The default value is 16 MB.
The log file size is checked at 10-minute intervals. If there’s an unusually large amount of logging activity, it’s possible for a log file to grow larger than the set disk space limit in that period of time.
Adding or replacing a log certificate
To import or replace a log certificate, under Log Certificate select the Replace tab.
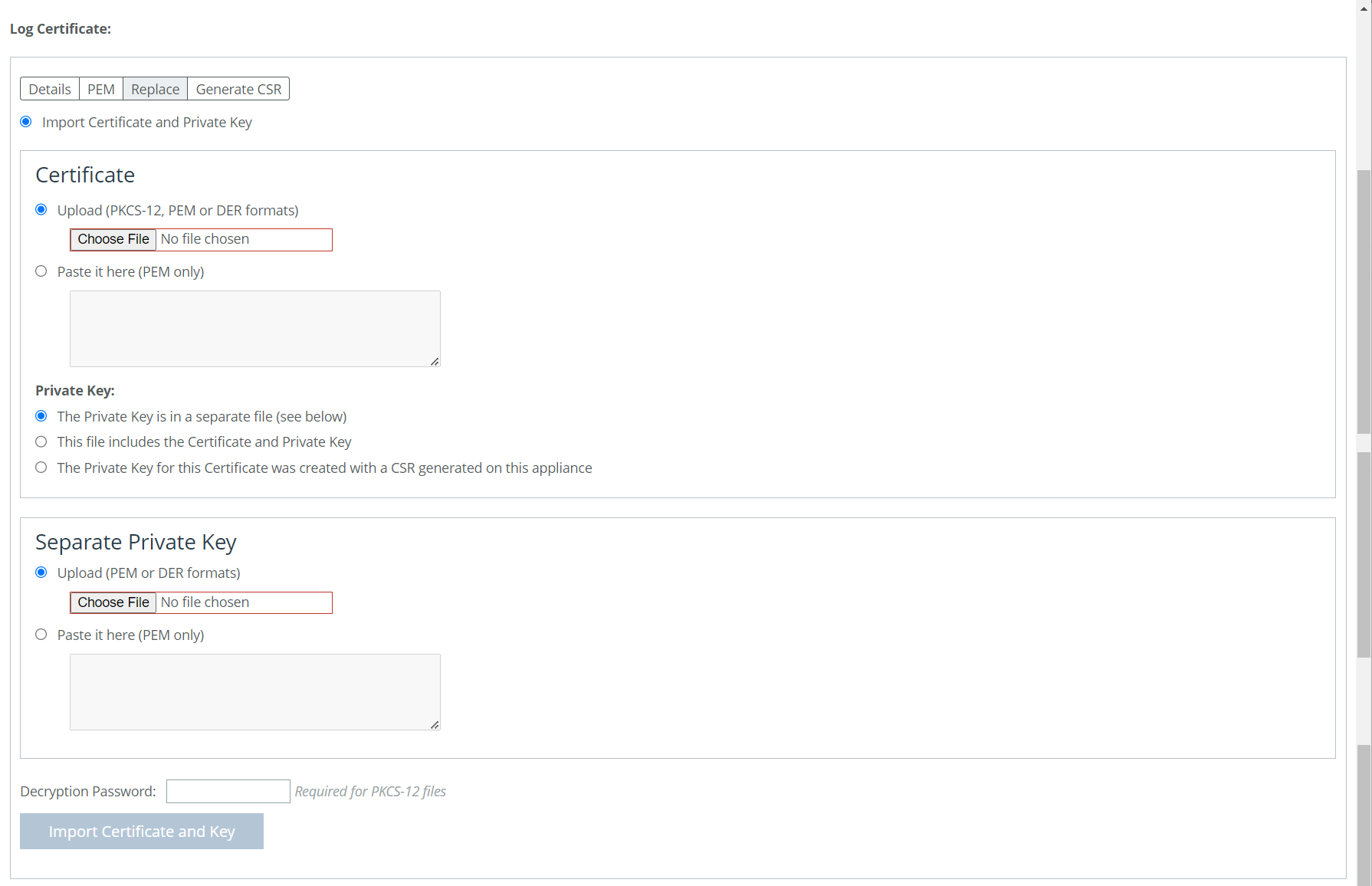
Importing or Replacing a Log Certificate
These options are available for importing a log certificate:
Import Certificate and Private Key
Imports the certificate and key. The page displays controls for browsing to and uploading the certificate and key files. You can also use the text box to copy and paste a PEM file. The private key is required regardless of whether you are adding or updating the certificate.
Under Certificate select from the following options:
Upload
Browses to the local file in PKCS-12, PEM, or DER formats.
Paste it here (PEM only)
Allows you to copy and then paste the contents of a PEM file.
Private Key
Selects the private key origin. You can choose from the following private key options:
• The Private Key is in a separate file (see below). You can either upload it or copy and paste it.
• This file includes the Certificate and Private Key.
• The Private Key for this Certificate was created with a CSR generated on this appliance.
Separate Private Key
Upload (PEM or DER formats)
Browses to the local file in PEM or DER formats.
Paste it here (PEM only)
Pastes the contents of a PEM file.
Decryption Password
Specifies the decryption password, if necessary. Passwords are required for PKCS-12 files, optional for PEM files, and never needed for DER files.
To generate a CSR, under Log Certificate select the Generate CSR tab. These configuration options are available:
Common Name
Specifies the common name (hostname).
Organization Name
Specifies the organization name (for example, the company).
Organization Unit Name
Specifies the organization unit name (for example, the section or department).
Locality
Specifies the city.
State
Specifies the state. Do not abbreviate.
Country
Specifies the country (2-letter code only).
Email Address
Specifies the email address of the contact person.
Generate CSR
Generates the Certificate Signing Request.
Adding or removing a remote log server
Remote logging supports secured and unsecured connections to remote logging servers. Secured connections are established using TLS with Reliable Event Logging Protocol (RELP). A log server certificate must be installed before a secure remote logging server can be enabled. For secure remote logging, certificates and keys are moved to the appliance’s secure vault. Ensure that the vault is unlocked before adding certificates and keys. If it is not, they will not be stored in the vault.
The default port number for secure remote logging is 514.
Remote Log Servers
adds a new remote log server from the drop-down menu.
Server IP or Hostname
specifies the server IP address or hostname of the remote log server.
Port
Specifies the port. If you are upgrading from a release that did not include a port number option, you’ll need to remove the remote log server and then add it back, specifying a port. The default is 514.
Minimum Severity
Specifies the minimum severity level for the log messages. The log contains all messages with this severity level or higher. Select one of these levels from the drop-down list:
• Emergency indicates system is unusable.
• Alert indicates action must be taken immediately.
• Critical indicates conditions that affect the functionality of the SteelHead.
• Error indicates conditions that probably affect the functionality of the SteelHead.
• Warning indicates conditions that could affect the functionality of the SteelHead, such as authentication failures.
• Notice indicates normal but significant conditions, such as a configuration change. This is the default setting.
• Info indicates informational messages that provide general information about system operations.
Enable secure connection
Enables secure remote logging. A log server certificate must be installed before a secure remote logging server can be enabled.



 Importing or Replacing a Log Certificate
Importing or Replacing a Log Certificate