Figure 4‑1 shows a monitoring configuration in which you detect traffic among all local servers. By monitoring an uplink port or VLAN, in addition to the local ports or VLANs, you can also detect traffic between all external hosts to the local hosts. The NetShark supports up to eight monitoring ports that enable you to duplicate this configuration multiple times using the same NetShark.
Figure 4‑1. SPAN Connectivity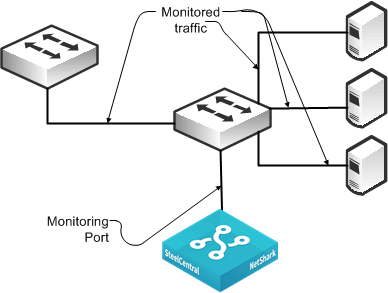

Figure 4‑2 shows a monitoring configuration in which you detect traffic to and from local servers on two different switches. The monitoring port is on an upstream switch. The NetShark and NetExpress have two or more monitoring ports that enable you to duplicate this configuration multiple times using the same NetShark or NetExpress.
Figure 4‑2. RSPAN Connectivity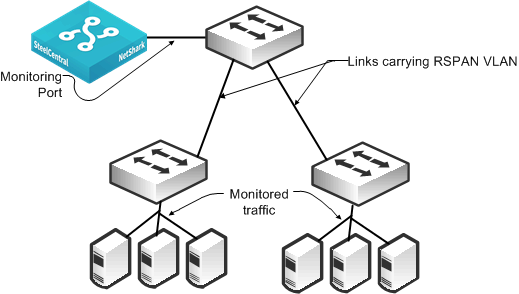

Figure 4‑3 shows a monitoring configuration that enables you to detect traffic to and from local servers on two different switches when the monitoring port is on an upstream switch over a routed network. The NetShark and NetExpress have two or more monitoring ports that enable you to duplicate this configuration multiple times using the same NetShark or NetExpress.
Figure 4‑3. ERSPAN Connectivity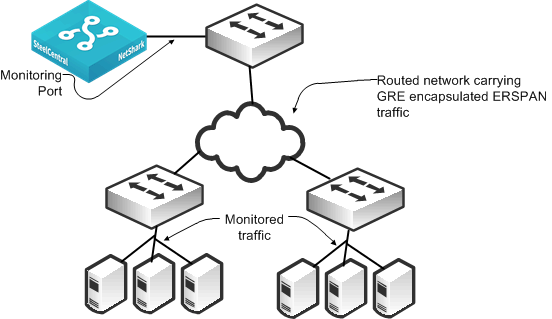

For details about Cisco switch configuration examples, go to http://www.cisco.com/en/US/products/hw/switches/ps708/products_tech_note09186a008015c612.shtml.
Figure 4‑4 shows an example Cisco Nexus v1000 virtual switch environment.
Figure 4‑4. 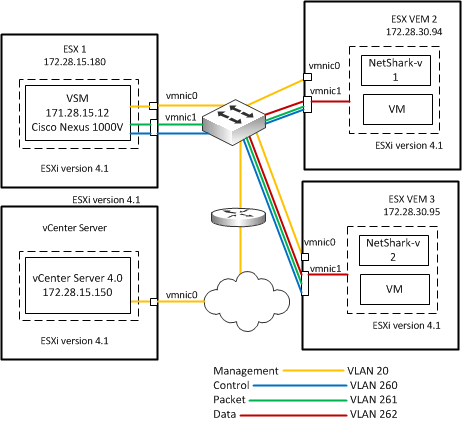 Cisco Nexus v1000 Virtual Switch SPAN
Cisco Nexus v1000 Virtual Switch SPAN
 Cisco Nexus v1000 Virtual Switch SPAN
Cisco Nexus v1000 Virtual Switch SPANFor additional information about Cisco Nexus 5000 and NetShark, see http://supportkb.riverbed.com/support/index?page=content&id=S24538.
|
1.
|
|
1.
|
