About SSL and Secure Inner Channels
This section provides an overview of Secure Sockets Layer (SSL) support and describes how to configure SSL server certificates and certificate authorities. SSL is a cryptographic protocol that provides secure communications between two parties over the internet.
Typically in a web-based application, it is the client that authenticates the server. To identify itself, an SSL certificate is installed on a web server and the client checks the credentials of the certificate to make sure it is valid and signed by a trusted third party. Trusted third parties that sign SSL certificates are called certificate authorities (CA).
With Riverbed SSL, appliances are configured to have a trust relationship, so they can exchange information securely over an SSL connection. SSL clients and servers communicate with each other exactly as they do without Riverbed appliances; no changes are required for the client and server application, nor are they required for the configuration of proxies. RiOS splits up the SSL handshake, the sequence of message exchanges at the start of an SSL connection.
In an ordinary SSL handshake, the client and server first establish identity using public-key cryptography, and then negotiate a symmetric session key to be used for data transfer. With Riverbed SSL acceleration, the initial SSL message exchanges take place between the client-side appliance and the server-side SteelHead.
Riverbed SSL
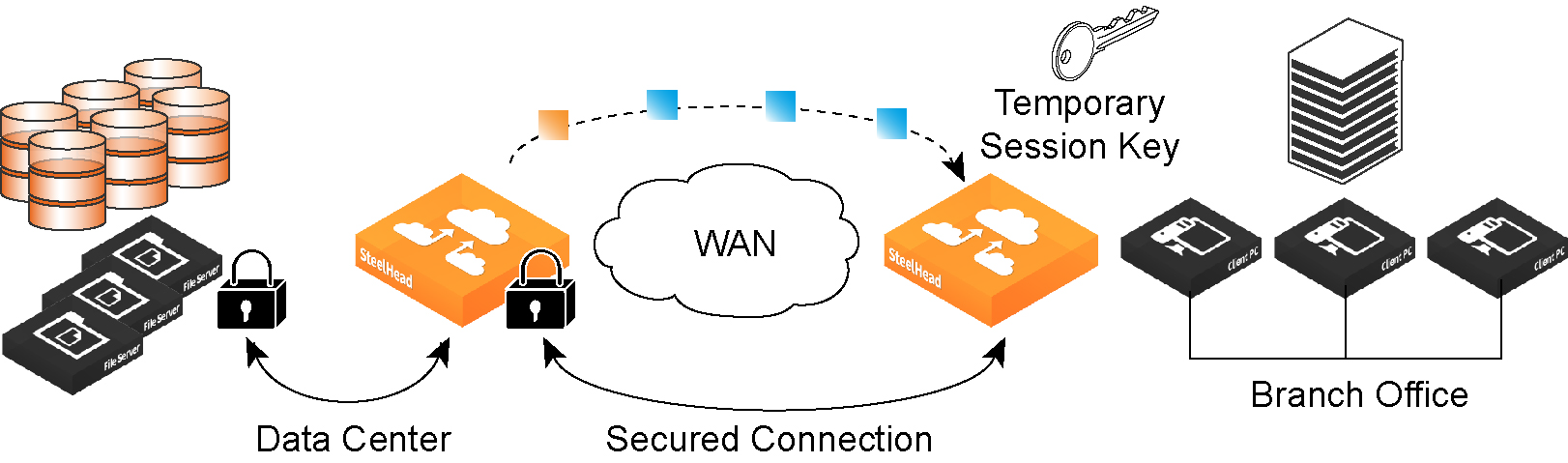
RiOS provides an alternative handshake, called distributed termination, which terminates full handshakes on the client-side appliance. The master secret containing information that allows the computation of the session key for reusing the session is transported to the session cache of the client-side appliance. The subsequent handshakes are reused and the client’s SSL connection is physically and logically terminated on the client-side appliance.
Distributed termination improves performance by lessening the CPU load because it eliminates expensive asymmetric key operations. It also shortens the key negotiation process by avoiding WAN roundtrips to the server. You can find the setting to reuse a client-side session for distributed termination under Optimization > SSL: Advanced Settings. See
Setting advanced SSL options.
RiOS provides client-side authentication, used to optimize SSL connections where the SSL server challenges the SSL client to present its own certificate, in addition to authenticating servers using SSL certificates.
The appliance also contains a secure vault that stores all SSL server settings, other certificates (that is, the CA, peering trusts, and peering certificates), and the peering private key. The secure vault protects your SSL private keys and certificates when the appliance is not powered on. You set a password for the secure vault that is used to unlock it when the appliance is powered on. After rebooting the appliance, SSL traffic is not optimized until the secure vault is unlocked with the correct password.


