Viewing user logs
You view user logs under Reports > Diagnostics: User Logs. The user log filters messages from the system log to display messages that are of immediate use to the system administrator.
View user logs to monitor system activity and to troubleshoot problems. For example, you can monitor who logged in, who logged out, and who entered particular CLI commands, alarms, and errors. The most recent log events are listed first.
Viewing and customizing user logs
You view and customize user logs under Reports > Diagnostics: User Logs.
User Logs page
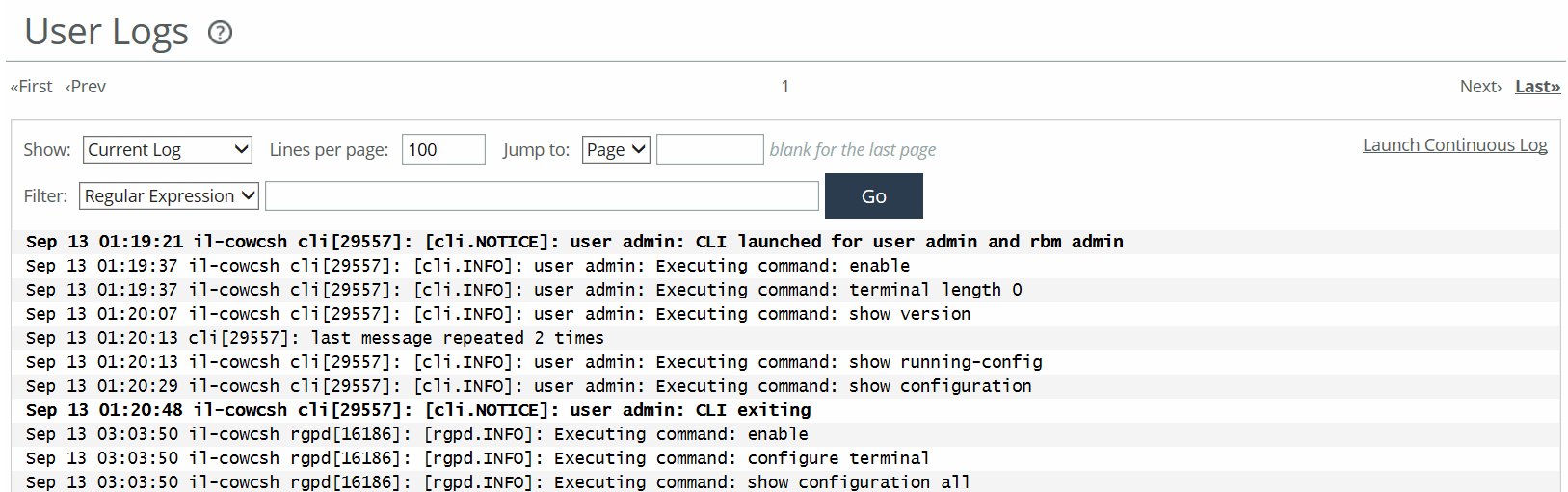
Use these controls to customize the log:
Show
Specifies one of the archived logs or Current Log from the drop-down list.
Lines per Page
Specifies the number of lines you want to display in the page.
Jump to
Specifies one of these options from the drop-down list:
• Page specifies the number of pages you want to display.
• Time specifies the time for the log you want to display.
Filter
Specifies one of these filtering options from the drop-down list:
• Regular expression specifies a regular expression on which to filter the log.
• Error or higher displays Error level logs or higher.
• Warning or higher displays Warning level logs or higher.
• Notice or higher displays Notice level logs or higher.
• Info or higher displays Info level logs or higher.
Go
Displays the report.
To print the report, choose File > Print in your web browser to open the Print dialog box.
You can continuously display new lines as the log grows and appends new data.
Viewing a continuous log
You view continuous logs under Reports > Diagnostics: User Logs.
Click Launch Continuous Log in the upper-right corner of the page.
If the continuous log does not appear after clicking Launch Continuous Log, a pair of appliances might be optimizing HTTP traffic between the user's web browser and the primary or auxiliary interface of the appliance for which the user is viewing the log, and they are buffering the HTTP response.
To display the continuous log, you can switch to HTTPS because the appliances will not optimize HTTPS traffic. Alternatively, you can configure the other appliances to pass-through traffic on the primary or auxiliary interfaces for port 80.


