Configuring security groups
Correctly configured security groups are critical for a node in an optimization group to contact its peers during discovery and for optimization to work. The Riverbed Cloud Portal automates many steps in the security group configuration.
Note: This feature is available to appliances provisioned through the portal to the AWS cloud platform.
For example, consider a configuration in which SteelHead-c 1, SteelHead-c 2, and Cloud Server A are members (nodes) of the same optimization group. The Riverbed Cloud Portal automatically creates a security group (Security Group 1) when SteelHead-c 1 is provisioned.
Figure: Security groups example
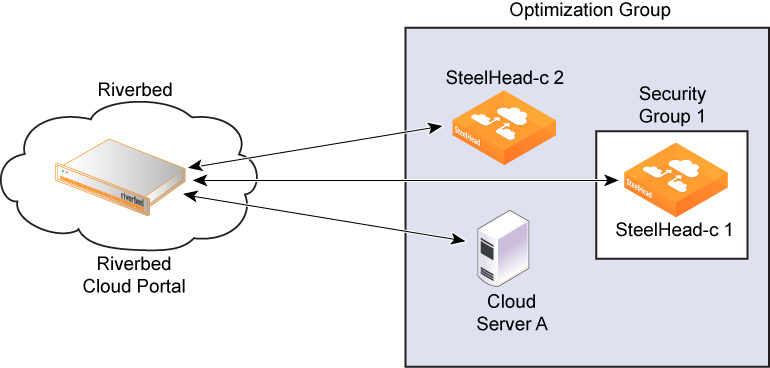
Initially, Security Group 1 does not let SteelHead-c 2 or Cloud Server A access SteelHead-c 1. However, after each node in the optimization group communicates with the Riverbed Cloud Portal and transmits its IP address, the portal automatically adds rules, called discovery service rules, to Security Group 1 so that the group allows access to SteelHead-c 1 from the node.
To complete the configuration, you must also add your own rules, called custom rules, because:
• You can configure and manage a SteelHead-c only if its security group allows connections from outside AWS on ports 22, 80, and 443.
• SteelHeads outside the AWS cloud must access ports 7800 and 7810 of the SteelHead-c for optimizing the connections.
Custom rules are not added to the security group for the Discovery Service and are not tracked by the Riverbed Cloud Portal.
The Riverbed Cloud Portal ensures that discovery service rules are automatically added to the security group whenever you restart the appliance. Even if you delete a Discovery Service Rule using a third-party tool such as the AWS user interface, the portal adds it back when you restart the appliance.
To remove a Discovery Service Rule, you must delete it from the Riverbed Cloud Portal by clicking delete in the Discovery Service Rule table.
You can add or delete custom rules through the Riverbed Cloud Portal, which adds or deletes the rules from the security group immediately. But if you subsequently delete a Custom Rule from the security group using a third-party tool, the Riverbed Cloud Portal does not ensure that the rule is reapplied when you start the appliance. The custom rules table simply reflects what is currently configured for the security group in the Amazon cloud at the time you visit the page on the Riverbed Cloud Portal.
For optimization to work, you must add rules to the Cloud Server security group to allow traffic from the SteelHead-c to reach the server TCP ports used by the application you want to optimize.
When the Discovery Agent is installed on the server, you must enable access to the UDP source port 7801 and destination port 7801 from the SteelHead-c on the server’s security group.


