About IPsec encryption
IPsec encryption settings to allow data to be communicated securely between peer SteelHeads are under Optimization > SSL: Secure Peering (IPSEC).
IPsec secure peering settings
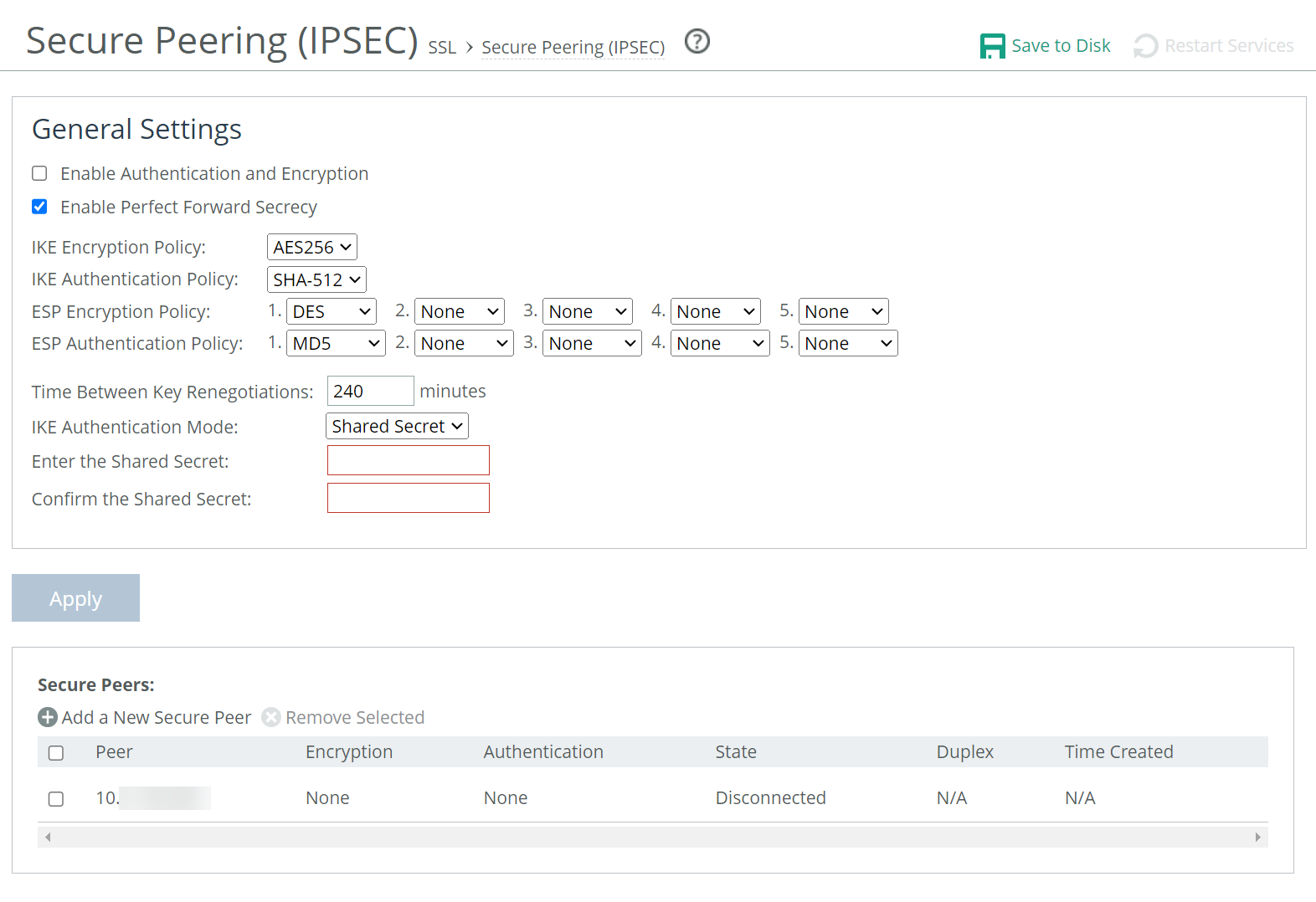
Enabling IPsec encryption makes it difficult for a third party to view your data or pose as a computer you expect to receive data from. To enable IPsec, you must specify at least one encryption and authentication algorithm. Only optimized data is protected, pass-through traffic isn’t.
Enabling IPsec support is optional.
RiOS doesn’t support IPsec over IPv6.
In RiOS 9.0 and later, IPsec secure peering and the secure transport service are mutually exclusive. The secure transport service is enabled by default. Before you enable IPsec secure peering, you must disable the secure transport service by entering the no stp-client enable command at the system prompt.
RiOS provides support for SSL peering beyond traditional HTTPS traffic. For details, see
About secure peers.
You must set IPsec support on each peer SteelHead in your network for which you want to establish a secure connection. You must also specify a shared secret on each peer SteelHead.
If you NAT traffic between SteelHeads, you can’t use the IPsec channel between the SteelHeads because the NAT changes the packet headers, causing IPsec to reject them.


