Management ACL page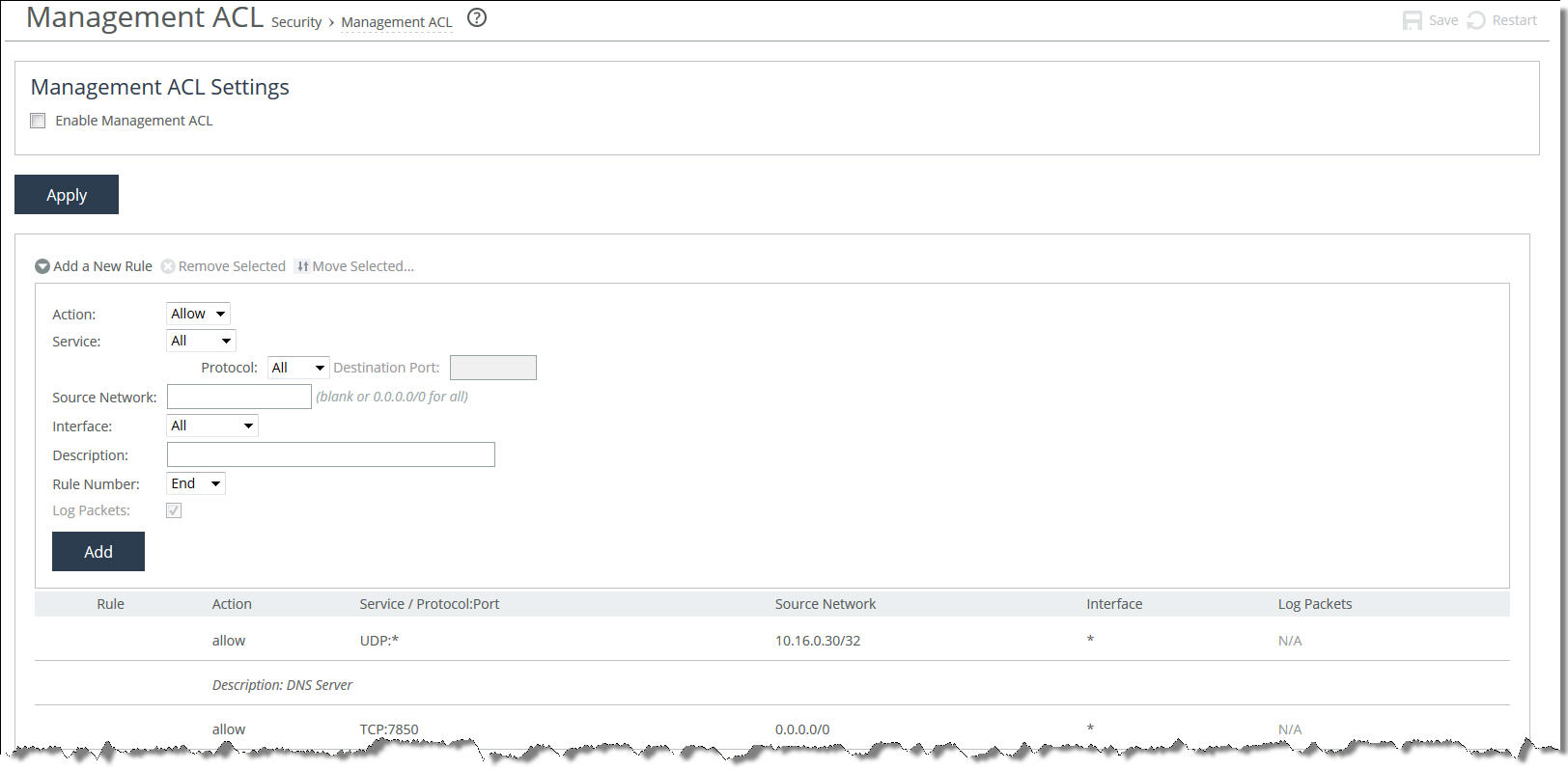


Control | Description |
Enable Management ACL | Secures access to a SteelHead Interceptor using a management ACL. |
Control | Description |
Add a New Rule | Displays the controls for adding a new rule. |
Action | Select one of these rule types from the drop-down list: • Allow—Allows a matching packet access to the SteelHead Interceptor. This is the default action. • Deny—Denies access to any matching packets. |
Service | Select All, or select a specific protocol (such as HTTP, HTTPS, SOAP, SNMP, SSH or Telnet) from the drop-down list. When a specific protocol is selected, the Protocol and Destination Port fields are unavailable. |
Protocol | (Appears only when Service is set to All.) Select All, TCP, UDP, or ICMP from the drop-down list. The default setting is All. When set to All or ICMP, the Destination Port is unavailable. |
Destination Port | (Appears only when the Protocol is set to UDP or TCP.) Specify the destination port of the inbound packet, either a single port value or a port range of port1-port2, where port1 must be less than port2. Leave it blank to specify all ports. |
Source Network | Optionally, specify the source subnet of the inbound packet: for example, 1.2.3.0/24. |
Interface | Optionally, select an interface type from the drop-down list. Select All to specify all interfaces. |
Description | Optionally, describe the rule to facilitate administration. |
Rule Number | Optionally, select a rule number from the drop-down list (Start, 1, or End). By default, the rule goes to the end of the table (just above the default rule). SteelHeads evaluate rules in numerical order starting with rule 1. If the conditions set in the rule match, then the rule is applied, and the system moves on to the next packet. If the conditions set in the rule do not match, the system consults the next rule; for example, if the conditions of rule 1 do not match, rule 2 is consulted. If rule 2 matches the conditions, it is applied, and no further rules are consulted. The default rule, Allow, which allows all remaining traffic from everywhere that has not been selected by another rule, cannot be removed and is always listed last. |
Log Packets | Tracks denied packets in the log. By default, packet logging is enabled. |
Add | Adds the rule to the list. The Management Console displays the Rules table and applies your modifications to the running configuration, which is stored in memory. |
Remove Selected | Select the check box next to the name and click Remove Selected. |
Move Selected | Moves the selected rules. Click the arrow next to the desired rule position; the rule moves to the new position. |