The Riverbed SSL Solution
The Riverbed SSL solution optimizes data transfers that are encrypted using SSL, provided that SteelHeads are deployed locally to both the client-side and server-side of the network. All of the same optimized connections that are applied to normal nonencrypted TCP traffic, you can also apply to encrypted SSL traffic. SteelHeads accomplish this without compromising end-to-end security and the established trust model. Your private keys remain in the data center and are not exposed in the remote branch office location where they might be compromised.
The Riverbed SSL solution starts with SteelHeads that have a configured trust relationship, enabling them to exchange information securely over their own dedicated SSL connection. Each client uses unchanged server addresses and each server uses unchanged client addresses; no application changes or explicit proxy configuration is required. Riverbed uses a unique technique to split the SSL handshake.
The handshake is the sequence of message exchanges at the start of an SSL connection. In an ordinary SSL handshake, the client and server first establish identity using public-key cryptography, and then negotiate a symmetric session key to use for data transfer. When you use Riverbed's SSL optimization, the initial SSL message exchanges take place between the client application (for example, a Web browser) and the server-side SteelHead.
Prior to RiOS v6.0, the SSL handshakes from the client are always handled by the server-side SteelHead, including session reuse handshakes.
RiOS v6.0 or later provides an alternative strategy, called distributed termination, in which initial full handshakes are terminated on the server-side SteelHead, while subsequent reuse handshakes are terminated by the client-side SteelHead.
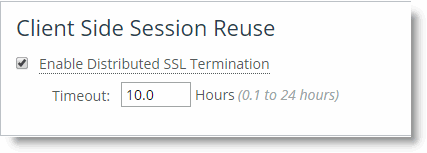
Distributed termination is enabled by default and is on the Optimization > SSL: Advanced Settings page. The time-out value specifies the amount of time the client can reuse a session with an SSL server after the initial connection ends. The range is 6 minutes to 24 hours. The default value is 10 hours.
Figure 11‑1. Distributed Termination Setting on the Advanced Settings Page
Distributed termination improves performance by reducing the CPU load on the server-side SteelHead and shortens the key negotiation process by avoiding WAN round trips to the server. Distributed termination also shortens the key negotiation process by avoiding WAN round trips to the server. You can configure reuse of a client-side session for distributed termination on the Optimization > SSL: Advanced Settings page in the Management Console. For more information about distributed termination, see
How SteelHeads Terminate an Optimized SSL Connection.
Riverbed has worked with large enterprise design partners to ensure that SSL optimization delivers real world benefits in real-world deployments, specifically:
sensitive cryptographic information is kept in the secure vault—a separate, encrypted store on the disk.built-in support for popular Certificate Authorities (CAs) such as VeriSign, Thawte, Entrust, and GlobalSign. In addition, SteelHeads allow the installation of other commercial or privately operated CAs.import of server proxy certificates and keys in PEM, PKCS12, or DER formats. SteelHeads also support the generation of new keys and self-signed certificates. If your certificates and keys are in another format, you must first convert them to a supported format before you can import them into the SteelHead. For details, see SSL Optimization Required Components.separate control of cipher suites for client connections, server connections, and peer connections. bulk export or bulk import server configurations (including keys and certificates) from or to, respectively, the server-side SteelHead.that you can use the SCC to streamline setup of SteelHead trust relationships.For more information, see the SteelHead Management Console User’s Guide and SteelCentral Controller for SteelHead User’s Guide.
The SteelHead has a secure vault that stores all SSL server settings, other certificates (that is, the CA, peering trusts, and peering certificates), and the peering private key. The secure vault protects your SSL private keys and certificates when the SteelHead is not powered on.
Initially the secure vault is keyed with a default password known only to the RiOS software. This allows the SteelHead to automatically unlock the vault during system start up. You can change the password, but the secure vault does not automatically unlock on start up. To optimize SSL connections, the secure vault must be unlocked.


