Back-hauled internet deployment
In this topology, the branch does not have its own connection to the internet. All traffic directed to the internet is back-hauled over a private WAN or VPN to the organization’s data center.
Figure: Back-hauled internet deployment
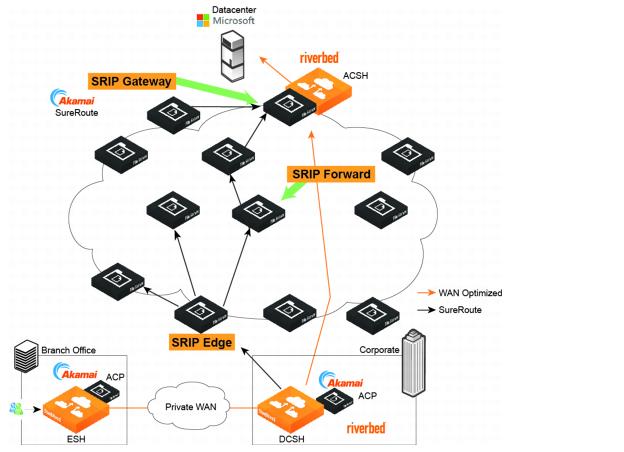
In this mode, the branch SteelHead appliance adds special information to the inner channel packets to indicate that this is traffic directed to the SaaS provider. When the data center SteelHead appliance receives the traffic with this special information, it redirects the traffic into a UDP tunnel and sends it to the Akamai network to be SureRoute routed to the SaaS application provider. For traffic coming back from Akamai, the data center SteelHead appliance unwraps the inner channel traffic from the tunnel before sending it across the WAN to the branch SteelHead appliance.
Although the data center SteelHead appliance encapsulates the traffic, it plays no role in the SSL optimization process. SSL optimization still takes place between the branch SteelHead appliance and the ACSH. Ensure that you establish the SSL peering trust between them.
In the back-hauled mode, you can configure the branch SteelHead appliance with full transparency and maintain existing QoS policies on the WAN.
If there is another branch with a SteelHead appliance that is not running a version of RiOS that supports SteelHead SaaS, then traffic from that branch appliance directed to the SaaS provider is passed through.
Note: If there is a firewall in the data center, you must configure it to allow the UDP traffic between the data center SteelHead appliance and the Simple Routing Information Protocol (SRIP) network.
Note: Ensure that you register both the branch SteelHead appliance and the data center SteelHead appliance with the Riverbed Cloud Portal and that they are granted access to the SRIP network. Also, ensure that the RiOS software running on both the branch appliance and the data center SteelHead appliance support SteelHead SaaS.


