Overview
Most enterprises today require that internet traffic go through a web proxy server for performance and security. The proxy server is typically deployed as an out-of-path server in the enterprise network.
You can configure the proxy server to intercept the traffic in these deployments:
• Transparent proxy deployment - This method uses packet redirection mechanisms, such as Layer-4 switch, WCCP, or policy-based routing (PBR) for packet redirection.
• Explicit proxy deployment - In this method, you configure browsers to communicate with the proxy server for internet traffic using an automatic script or hard-coded configuration. When you access a secure web server through an HTTPS connection, the browser tunnels HTTPS requests to the proxy server by sending HTTP CONNECT requests. If you are deploying an explicit proxy server, it might not terminate the SSL connections. Use the configuration described in the section
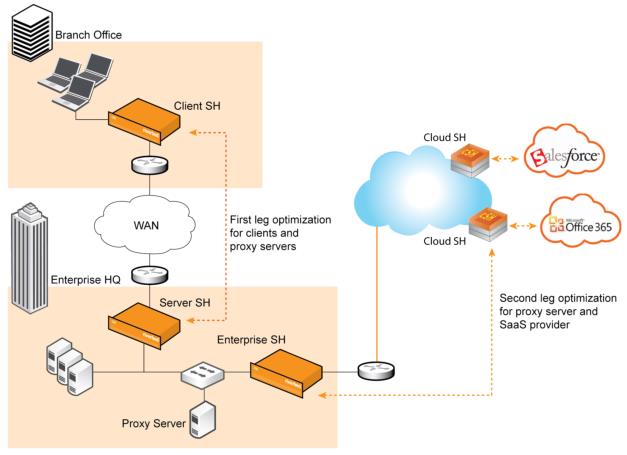
Configuring the first optimization phase. To deploy SaaS Accelerator in a network with a proxy server, you must set up chained optimization to obtain maximum performance. In chained optimization, a single request is optimized by two separate pairs of SteelHead appliances. The first SteelHead appliance pair optimizes the front-end proxy requests. The second pair intercepts the proxy server requests from the ESH to the Cloud SteelHead appliance.
To deploy the chained optimization, set up the first pair of SteelHead appliances to optimize SSL proxy requests from the client to the proxy server and then set up the second pair of SteelHead appliances to optimize the HTTPS request from the proxy server to the SaaS server.
Network topology with a proxy server
Test and verify one pair of SteelHead appliances to optimize the traffic before you set up the second pair.


