In-Path Rules page (standard mode)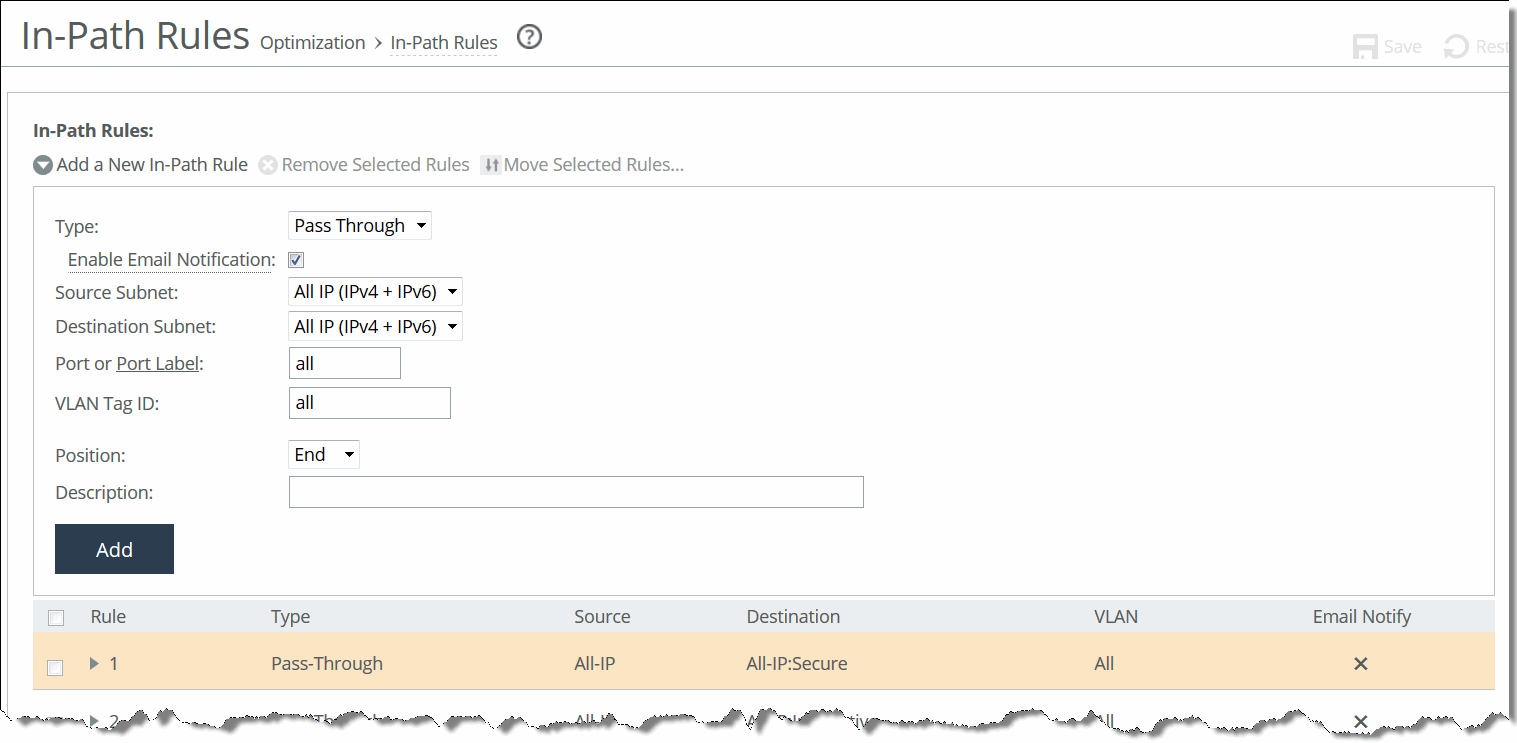


Control | Description |
Add a New In-Path Rule | Displays the controls to add a new rule. |
Type | Select one of these rule types: When traffic matches the pass-through rules, the traffic will also be matched to service rules if path selection is enabled. • Redirect—Redirect rules select traffic that might be redirected. Typically, you configure a redirect rule for source and destination addresses and ports you want to optimize with the Riverbed system. A separate set of load-balancing rules determines the SteelHead Interceptor to which the connection is to be redirected. • Pass Through—Pass-through rules identify traffic that is passed through the network unoptimized. For example, you might choose to pass through traffic on interactive or secure ports. • Discard—Packets for connections that match the rule are dropped silently. Essentially, the SteelHead Interceptor filters out traffic that matches the discard rules. For example, you might choose to drop connections from an unauthorized source or to an unauthorized target subnet. • Deny—If packets for connections match the deny rule, the SteelHead Interceptor actively tries to reset the connection. For example, you might choose to deny connections from an unauthorized source or to an unauthorized target subnet. |
Enable Email Notification | This option enables email notification of pass-through rules every 15 days. In addition to selecting this check box, you must also select the Report Events via Email check box and specify an email address in the Email > System Settings: Email page. You can select or more pass-through rules for notification. However, notifications are sent only for those rules that have this check box selected. This option is available for pass-through rules only and is enabled by default. This option is disabled for the other rule types. To change the frequency of reminder emails, enter the email notify passthrough rule notify-timer command. To disable reminder emails for pass-through rules, clear this check box or enter the no email notify passthrough rule command. For more information, see the Riverbed Command-Line Interface Reference Manual. |
Source Subnet | Specify the subnet IP address and netmask for the source network. • All IP (IPv4 + IPv6)—Maps to all IPv4 and IPv6 networks. • All IPv4—Maps to 0.0.0.0/0. • All IPv6—Maps to ::/0. • IPv4—Prompts you for a specific IPv4 subnet address. Use this format for an individual subnet IP address and netmask: xxx.xxx.xxx.xxx/xx • IPv6—Prompts you for a specific IPv6 subnet address. Use this format for an individual subnet IP address and netmask: x:x:x::x/xxx |
Destination Subnet | Specify the subnet IP address and netmask for the destination network. • All IP (IPv4 + IPv6)—Maps to all IPv4 and IPv6 networks. • All IPv4—Maps to 0.0.0.0/0. • All IPv6—Maps to ::/0. • IPv4—Prompts you for a specific IPv4 subnet address. Use this format for an individual subnet IP address and netmask: xxx.xxx.xxx.xxx/xx • IPv6—Prompts you for a specific IPv6 subnet address. Use this format for an individual subnet IP address and netmask: x:x:x::x/xxx |
Port or Port Label | Specify the destination port number, port label, or All. Click Port Label to go to the Networking > Network Services: Port Labels page for reference. For details about managing port labels, see
Setting port labels. If you order rules so that traffic that is passed through, discarded, or denied is filtered first, All represents all remaining ports. |
VLAN Tag ID | Specify a VLAN identification number from 0 to 4094, enter all to apply the rule to all VLANs, or enter untagged to apply the rule to nontagged connections. Pass-through traffic maintains any preexisting VLAN tagging between the LAN and WAN interfaces. To complete the implementation of VLAN tagging, you must set the VLAN tag IDs for the in‑path interfaces that the SteelHead Interceptor uses to communicate with other SteelHead Interceptors. |
Position | Select Start, End, or a rule number from the drop-down list. SteelHead Interceptors evaluate rules in numerical order starting with rule 1. If the conditions set in the rule match, then the rule is applied, and the system moves on to the next packet. If the conditions set in the rule do not match, the system consults the next rule: for example, if the conditions of rule 1 do not match, rule 2 is consulted. If rule 2 matches the conditions, it is applied, and no further rules are consulted. In general, list rules in this order: 1. Deny 2. Discard 3. Pass-through 4. Redirect |
Description | Describe the rule. |
Add | Adds the newly defined rule to the list and applies the settings to the running configuration. |
Remove Selected Rules | Select the check box next to the name and click Remove Selected Rules. This action applies the settings to the running configuration. The default rule cannot be removed and is always listed last. |
Move Selected Rules | Click the arrow next to the desired rule position; the rule moves to the new position. The default rule cannot be reordered and is always listed last. |