Client authentication is also supported as part of a Mobile Controller deployment. You must have SteelHead Mobile v4.6 or later. For more information specific to the Mobile Controller, see the SteelHead Deployment Guide.
|
1.
|
|
3.
|
Choose Optimization> SSL: SSL Main Settings, import the SSL server private key and certificate, and click Save to save the configuration. You do not need to restart the optimization service.
|
To verify client authentication, on the server-side SteelHead, check the Discovered Server (Optimizable) table on the SSL Main Settings page. Optimizable servers that are using client authentication appear as optimizable streams. For servers that are not using client authentication, the server appears in the Discovered Server (bypassed, not optimizable streams) table with the reason No proxy certificate configured for the server.
For more information, including a configuration example, see Configuring HTTP SSL Proxy Interception.
An example mid-session SSL is START Transport Layer Security (TLS) during SMTP sessions. The client starts an unencrypted SMTP session on port 25, to the server. The server accepts the unencrypted session and indicates to the client that it supports STARTTLS. In the middle of session, the client initiates STARTTLS. Normal TLS negotiations resume and the rest of the conversation is encrypted. For more details, see http://en.wikipedia.org/wiki/STARTTLS.
Figure 11‑18. Example STARTTLS During SMTP Session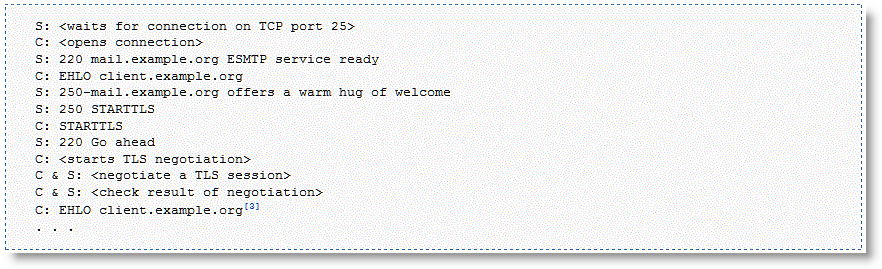
Source: http://en.wikipedia.org/wiki/STARTTLS (May 3, 2012)
|
3.
|
Click Apply.
|
