About SteelCentral Controller for SteelHead
The SCC enables you to manage, configure, and monitor Riverbed products. The SCC also acts as an enterprise management and reporting tool for Riverbed products enabling greater control for global network deployments.
This chapter assumes you have installed and performed the initial configuration of the SCC. For details, including system requirements and cross-product compatibility, see the SteelCentral Controller for SteelHead Installation Guide.
This chapter also assumes that you’re familiar with the various deployment options available to you. For details, see the SteelHead Deployment Guide and the SteelCentral Controller for SteelHead Deployment Guide.
We recommend that you don’t use the Riverbed CLI to configure the SCC.
About migration procedures
For detailed information about SCC migration best practices, see
SCC Best Practices.About SteelHead autoregistration
SteelHeads must be registered with the SCC so that you can monitor and manage them with the SCC.
SteelHeads are designed to send a registration request periodically to the SCC—either to an IP address or hostname you specify when you run the SteelHead configuration wizard, or to a default SCC hostname. For autoregistration with the default hostname to work, you must configure your DNS server to map to the hostname riverbedcmc and the IP address of the SCC either as a CNAME or as an A record.
During autoregistration, the SteelHeads don’t send passwords to the SCC. Unless the password value has been modified in the Manage Appliances page, the SCC assumes that the default password is password. For details, see
Adding appliances.After a SteelHead is registered, you can set autoconfiguration to automatically push the current configuration when the SteelHead connects.
About scaling best practices
The model 1000 SCC can manage up to 2500 appliances. The SCC-v configuration must be equivalent, or better, to the model 1000 to support 2500 appliances.
Adhere to these guidelines for deployments with 1500 or more appliances:
• Legacy policy pushes must be limited to 200 appliance at a time. This process may take several minutes for a larger set of appliances.
• Hybrid network policy pushes are limited to 500 appliances at a time. This process may take several minutes for a larger set of appliances.
• If a legacy and hybrid networking policy push must be performed together, then the push is limited to 200 appliances at a time. This process may take several minutes for a larger set of appliances.
• When upgrading large deployments, the initial upgrade may take several hours.
• If your deployment contains more than 1000 appliances, backups will take more than three hours.
About HTTPS communication channel
Traditionally, appliances communicated with the SCC through an SSH channel. Now, an HTTPS (on TCP port 9443) communication channel is also available. This channel is used to push and pull the new hybrid networking features supported in the SCC (for example, path selection, QoS, and secure transport).
For managed appliances both the SSH and the HTTPS channels must be in a connected state. If either one of these channels is down, then a push from the SCC to the appliance will fail. For instance, if the HTTPS connection is down, pushing the hybrid network configuration from the SCC to appliances will fail.
For detailed information about troubleshooting, see
HTTPS communication channel. Connecting SteelHeads when the SCC is behind a firewall
The SCC provides you with the ability to configure an SSL authentication port for SteelHeads when the SCC is behind a firewall with restricted access to ports 443 and 80. This feature enables SteelHeads to communicate with SCC. You configure the SSL authentication port using the SCC CLI.
This diagram shows a SteelHead (SH-1) connected to the SCC that’s listening on port 443 without a firewall. The second SteelHead (SH-2) is connected to the SCC through a firewall that has restricted access to ports 443 and 80. On the SCC for SH-2, you can configure an SSL authentication port (for example, 7443) using a CLI command enabling you to communicate with SH-2.
SCC with custom authorized port 7443
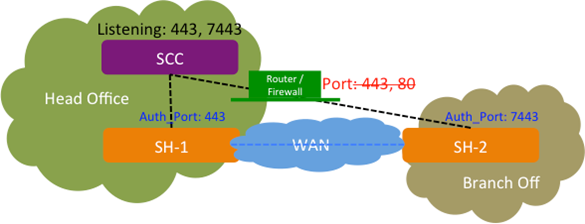
You can configure one additional authentication port in addition to the existing port 443.
The SSL authentication port feature is only available via the CLI; it isn’t available in the SCC Management Console.
For detailed information about connecting and using the Riverbed CLI, see the Riverbed Command-Line Interface Reference Manual.
To enable communication to SteelHeads with restricted access
1. On the SCC, connect to the CLI in configuration mode. For detailed information about connecting and using the Riverbed CLI, see the Riverbed Command-Line Interface Reference Manual.
2. To configure SSL authentication port access, at the system prompt enter:
amnesiac (config) # ocs authport port <port-number>
where <port-number> is the authentication port number on which you want to establish communication with the SCC.
3. On the SteelHead, connect to the CLI in configuration mode and enter this command at the system prompt:
ocd connection cmc csr_auth auth_port <port-number>
where <port-number> is the authorized port number on which you want to establish communication with the SCC. Make sure this is the same port you configured on the SCC.
Troubleshooting
On the SCC:
• The port number should have an appropriate entry when you run the netstat command. On the SCC, via the shell, at the system prompt enter:
netstat -an |grep <port-number>
• The port number should be listed in the Apache /etc/httpd/http.conf file:
Listen <port-number>
If the port number doesn’t appear, restart the HTTP service on the SCC:
pm process httpd restart
On the SteelHead:
• Enter the show ocd connections command. It should list the port number as Auth Port and Status “Connected.”
• To ensure registration is successful, enter these commands:
amnesiac # show scc
amnesiac # show cmc
Connecting to the SCC Management Console
To connect to the Management Console, you must know the host, domain, and administrator password that you assigned in the configuration wizard.
Cookies and JavaScript must be enabled in your web browser.
Before you begin, clear your browser cache and cookies to ensure the user interface displays correctly.
To connect to the SCC Management Console
1. Enter the URL for the SCC in the location box of your browser:
<protocol>://<host>.<domain>
<protocol> is http or https. The secure HTTPS uses the SSL protocol to ensure a secure environment. When you connect using HTTPS, you’re prompted to inspect and verify the SSL certificate. This is a self-signed certificate used to provide encrypted web connections to the SCC.
<host> is the IP address or hostname you assigned the SCC during initial configuration. If your DNS server maps the IP address to a name, you can specify the DNS name.
<domain> is the full domain name for the SCC.
The SCC Sign In page appears.
2. In the text box, specify the user login: admin, monitor, a login from a RADIUS or a TACACS+ database, or a previously configured role-based management (RBM) account.
The default login is admin. Users with administrator privileges can configure and administer the SCC. Users with monitor privileges can view SCC reports but they can’t configure the system.
3. In the Password text box, specify the password you assigned in the configuration wizard of the SCC.
The SCC is shipped with password as the default password.
4. Click Log In to log in to display the dashboard.


