About SAML authentication
Settings for SAML are under Administration > Security: SAML.
Security Assertion Markup Language (SAML) is an XML standard that acts as an authentication interface between a appliance and an identity provider (IdP). You can use the IdP to provide additional requirements for authentication, such as a multifactor authentication based on a common access card (CAC) or personal identity verification (PIV).
When an appliance receives a login request, it determines if SAML is enabled. If SAML is enabled, user authentication through AAA is disabled and the appliance redirects the authentication request to the IdP. The IdP authenticates the user and redirects the user to the SteelHead, which allows access.
SAML authentication process
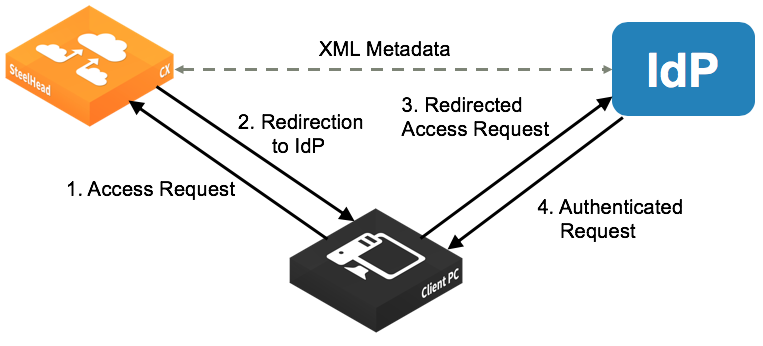
To enable IdP authentication, you configure the appliance and the IdP with XML metadata that provides detailed appliance identification. The metadata also establishes a trust relationship between the appliance and the IdP.
Administrators must add users to the IdP server to provide them login access, and those users need to correspond to users on the appliance. You can have one-to-one mapping of users between IdP and the appliance, or you can have multiple users on IdP map to single account on the appliance, such as the admin account. (You have to create individual user accounts on the appliance for one-to-one mapping as the user accounts determine the access permissions.)
If a user who has not been set up in the IdP tries to log in to the appliance, the login fails on the IdP login page. (This failed login is not tracked in the appliance logs.) If the user has been set up but their user mapping has not been defined in the IdP, the login succeeds but the appliance displays an error page (instead of the dashboard).
SAML authentications are only available in the Management Console web interface; they are not available through the CLI. Users can log in to a SAML-enabled appliance through the CLI but they are authenticated using the local, RADIUS, or TACACS+ authentication methods.
If you cannot log in using SAML (for example, if the IdP server is unavailable), you can log in through the CLI and disable SAML using the no aaa saml command. Once SAML is disabled, you revert to the previously configured authentication method for the web interface.
You must be logged in as the administrator to enable or disable SAML.
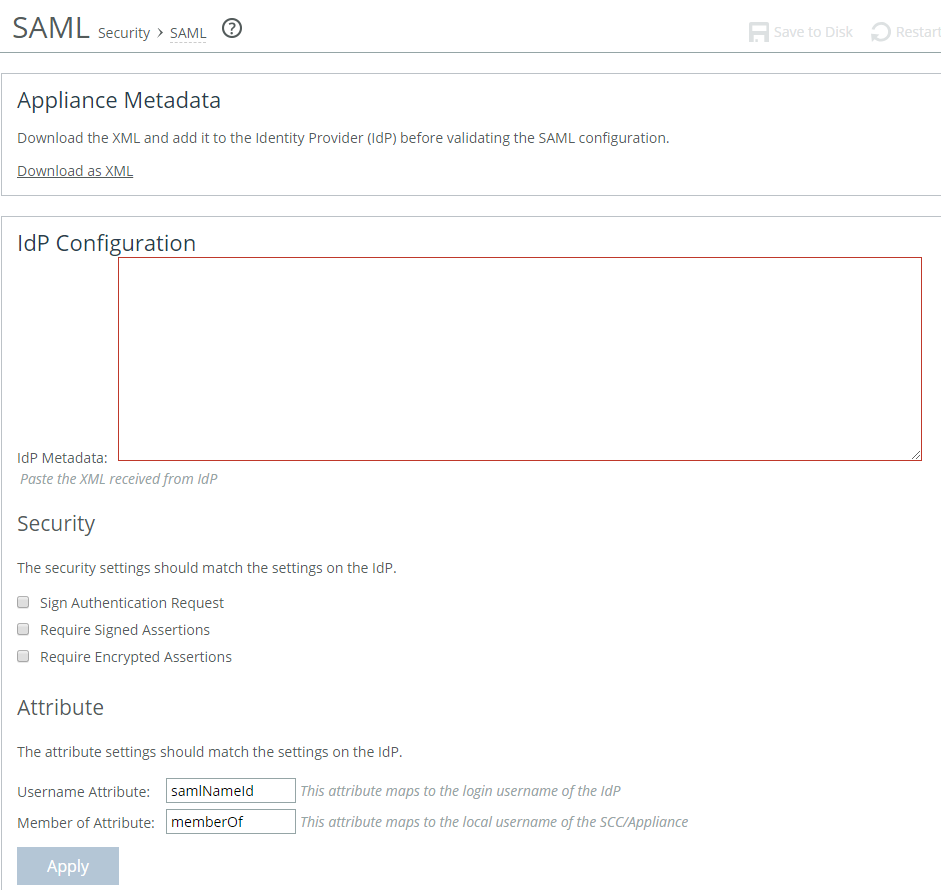
IdP Configuration section of the SAML page