Configuring SAML
You set up SAML in the Administration > Security: SAML page.
Security Assertion Markup Language (SAML) 2.0 is an XML standard that acts as an authentication interface between a SCC and an identity provider (IdP). You can use the IdP to provide additional requirements for authentication, which can be multi-factor authentication methods such as common access card (CAC) or personal identity verification (PIV).
When an SCC receives a login request, it determines if there is a local login available, and if so, the SCC provides access with the local credential. If SAML is enabled, user authentication through AAA is disabled and the SCC redirects the authentication request to the IdP. The IdP authenticates the user, informs the SCC of the verified identify, and redirects the user to the SCC, which allows access.
Figure: SAML authentication process
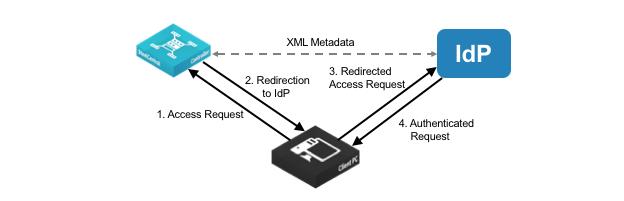
To enable IdP authentication, you configure the SCC and the IdP with XML metadata that provides detailed appliance identification. The metadata also establishes a trust relationship between the SCC and the IdP.
Administrators must add users to the IdP server to provide them login access, and those users need to correspond to SCC users. You can have one-to-one mapping of users between IdP and SCC, or you can have multiple users on IdP map to a single account on the SCC, such as the admin account. (You have to create individual user accounts on the SCC for one-to-one mapping as the user accounts determine the access permissions.)
You can enable SAML on a single appliance using the SAML page of that appliance (this procedure is an example of how to enable SAML in an SCC), or you can configure SAML in a policy and then push the policy across multiple appliances. For more details on how to configure SAML in a policy, see
Managing SAML.Note: Before you enable SAML on a single appliance or on multiple appliances, you must configure IdP individually for each appliance because the IdP metadata required to enable SAML is unique for each appliance.
You must be logged in as the administrator to enable SAML.SCC
To enable SAML in SCC
1. Choose Administration > Security: SAML to display the SAML page.
2. Under Download SteelCentral Controller Metadata, select Download XML to download the SCC metadata in XML format.
The sp_metadata.xml file downloads to your local machine.
3. Configure SCC in your IdP.
Refer to the documentation for your IdP for specific instructions. In general, you complete these steps:
– Log in to the IdP website.
– Upload the metadata from the sp_metadata.xml file and provide any other required details.
– When the configuration is complete, download the IdP metadata.
4. In the SCC Management console, under SAML > IdP Configuration, configure the SAML request and response settings as described in this table.
Control | Description |
IdP Metadata | Paste the IdP metadata you copied or received from the IdP website. |
Security Settings | Sign Authentication Request - Select this option to have SCC sign the SAML authentication request sent to the identity provider. Signing the initial login request sent by SCC allows the identity provider to verify that all login requests originate from a trusted service provider. |
Requires Signed Assertions - Select if SAML assertions must be signed. Some SAML configurations require signed assertions to improve security. |
Requires Encrypted Assertions - Select this option to indicate to the SAML identity provider that SCC requires encrypted SAML assertion responses. When this option is selected, the identity provider encrypts the assertion section of the SAML responses. Even though all SAML traffic to and from SCC is already encrypted by the use of HTTPS, this option adds another layer of encryption. |
Attribute | User Name Attribute - Enter the name of the IdP variable that carries the username of the user. The user name attribute is mandatory and must be sent by your identify provider in the SAML response to align the login with a configured SteelHead account. Default value is samlNameId. |
Member of Attribute - Enter the name of the IdP variable that carries the role of the user. Default value is memberOf. |
5. Click Apply to save your configuration settings.
6. Under Validate the IdP Configuration, click Validate.
The IdP Validation window appears.
7. Click Go to IdP.
The IdP login page opens.
8. Log in to the IdP website.
The page indicates if your IdP configuration was successful.
9. After successful validation, return to the SAML page in the management console and select the Enable SAML check box and click Apply.
Tip: If the validation status on the SCC page does not update after a successful validation, reload the page to refresh the status.
With SAML enabled, all web login requests are redirected to the IdP.
10. Click Save to Disk to save your settings permanently.
If you make changes to the SAML settings after you validate the IdP configuration, you need to validate again with the new settings and enable SAML again.
Usage Notes
SAML authentications are only available in the Management Console web interface; they are not available through the CLI. Users can log in to a SAML-enabled SCC through the CLI but they are authenticated using the local, RADIUS, or TACACS+ authentication methods. We recommend that you set strong passwords for Riverbed appliances.
Troubleshooting
• If a user who has not been set up in the IdP tries to log in to the SCC, the login fails on the IdP login page. (This failed login is not tracked in the SCC logs.) Log in to SCC through CLI.
• If the user has been set up but their user role has not been defined in the IdP, the login succeeds but the SCC displays an error page (instead of the dashboard). Log in to SCC through CLI.
• If you cannot log in using SAML (for example, if the IdP server is unavailable), you can log in through the CLI and disable SAML using the no aaa saml enable command. Once SAML is disabled, you revert to the previously configured authentication method for the web interface. For command details, see the Riverbed Command-Line Interface Reference Manual.
• If SAML stopped working, in the Administration > Security: SAML page, click Apply. SAML authentication will be disabled for SCC. Then click Validate. The error message displayed can help you identify and fix the problem.


