Deployment configurations
There are two types of deployment configurations defined by how the branch offices access the internet. In direct branch internet deployment mode, branch offices access the internet directly without passing through a data center. In back-hauled internet deployment configurations, branch offices connect to the internet over an internal WAN or VPN connection to a centralized data center that controls all internet access.
Note: SteelHead SaaS does not support SteelHead Mobile.
Figure: SteelHead SaaS configurations
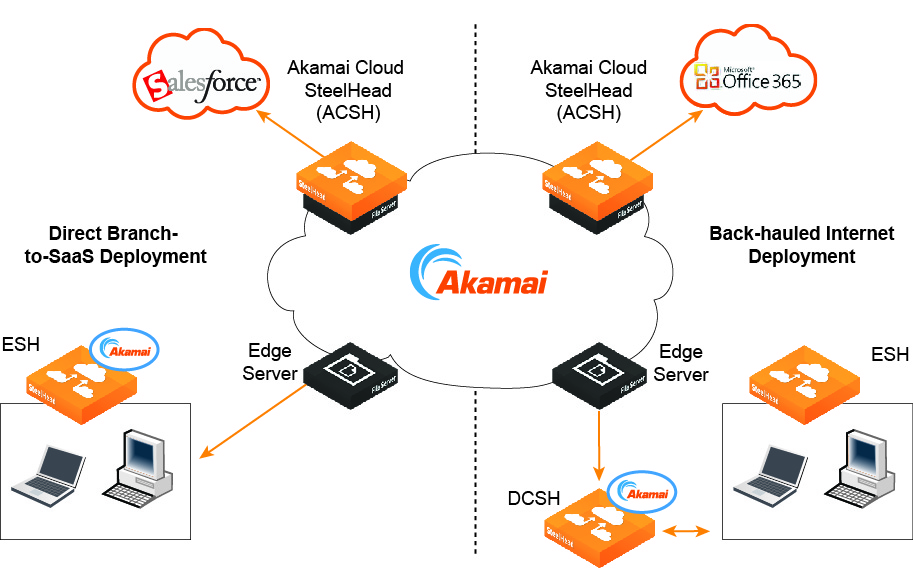
Direct branch internet deployment
In direct mode, the branch SteelHead appliance encapsulates the traffic and sends it directly to a server in the Akamai network. Akamai SureRoute optimization technology ensures that the traffic is forwarded through the Akamai network along the fastest path toward its destination at the data center hosting the SaaS application.
Figure: Direct branch internet deployment
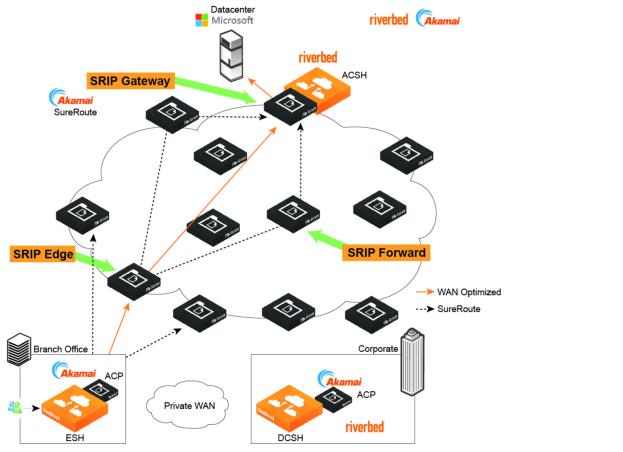
After the branch SteelHead appliance is licensed and registered on the Riverbed Cloud Portal, it downloads a set of rules from the portal and obtains the IP addresses for all of the servers for the SaaS applications to which you are subscribed.
This topology does not involve an intermediary SteelHead appliance. All SSL optimization and peering trusts are established directly between the branch SteelHead appliance and the ACSH.
Back-hauled internet deployment
In this topology, the branch does not have its own connection to the internet. All traffic directed to the internet is back-hauled over a private WAN or VPN to the organization’s data center.
Figure: Back-hauled internet deployment
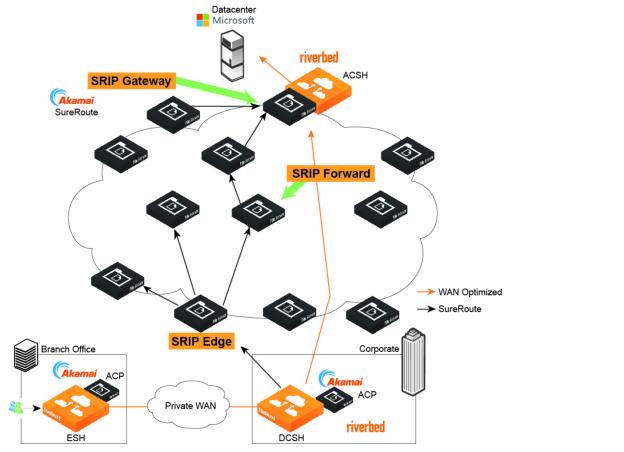
In this mode, the branch SteelHead appliance adds special information to the inner channel packets to indicate that this is traffic directed to the SaaS provider. When the data center SteelHead appliance receives the traffic with this special information, it redirects the traffic into a UDP tunnel and sends it to the Akamai network to be SureRoute routed to the SaaS application provider. For traffic coming back from Akamai, the data center SteelHead appliance unwraps the inner channel traffic from the tunnel before sending it across the WAN to the branch SteelHead appliance.
Although the data center SteelHead appliance encapsulates the traffic, it plays no role in the SSL optimization process. SSL optimization still takes place between the branch SteelHead appliance and the ACSH. Ensure that you establish the SSL peering trust between them.
In the back-hauled mode, you can configure the branch SteelHead appliance with full transparency and maintain existing QoS policies on the WAN.
If there is another branch with a SteelHead appliance that is not running a version of RiOS that supports SteelHead SaaS, then traffic from that branch appliance directed to the SaaS provider is passed through.
Note: If there is a firewall in the data center, you must configure it to allow the UDP traffic between the data center SteelHead appliance and the Simple Routing Information Protocol (SRIP) network.
Note: Ensure that you register both the branch SteelHead appliance and the data center SteelHead appliance with the Riverbed Cloud Portal and that they are granted access to the SRIP network. Also, ensure that the RiOS software running on both the branch appliance and the data center SteelHead appliance support SteelHead SaaS.
Deciding on a deployment configuration
The key deciding factor to choosing a deployment configuration is whether or not your network requires QoS or NetFlow reporting on the WAN between the data center and the branch. This is because in a back-hauled configuration traffic directed to the SaaS provider is encapsulated within a UDP tunnel and is no longer visible on the WAN.
If your network does not need QoS or NetFlow reporting on the link between the data center and the branch, then use a direct mode deployment. Otherwise, use a back-hauled deployment. In a back-hauled deployment, the data center SteelHead appliance redirects the traffic to the Akamai network, but the branch SteelHead appliance performs the optimization. Traffic from the branch SteelHead appliance to the ACSH uses TCP on ports 7800 through 7899 as visible on the network. When traffic arrives at the data center SteelHead appliance, the appliance redirects the traffic using UDP on port 9545.
Note: If the data center has a firewall, ensure that it allows UDP access from the in-path IP address of the branch SteelHead appliance.




